Hello All
Thanks a lot for the various replies & ideas.
After 3 more waves of suspicious scans from various Windows destops & laptops in my house, and after starting to get really worried, I played with a combinations of Wireshark and Process Explorer and managed to narrow it down to the AVG Antivirus !! ![]() (that is indeed installed on all my Windows devices).
(that is indeed installed on all my Windows devices).
Indeed, it seems that during a full scan (either planned or the ones that occur by themselves after a year without a scan having being executed, there is a new ‘feature’ in the Network Inspector module called Test network devices for weak passwords ; and that’s exactly what AVG does, it performs a port scan on all devices on your network and tries to login using known default users/passwords combinations.
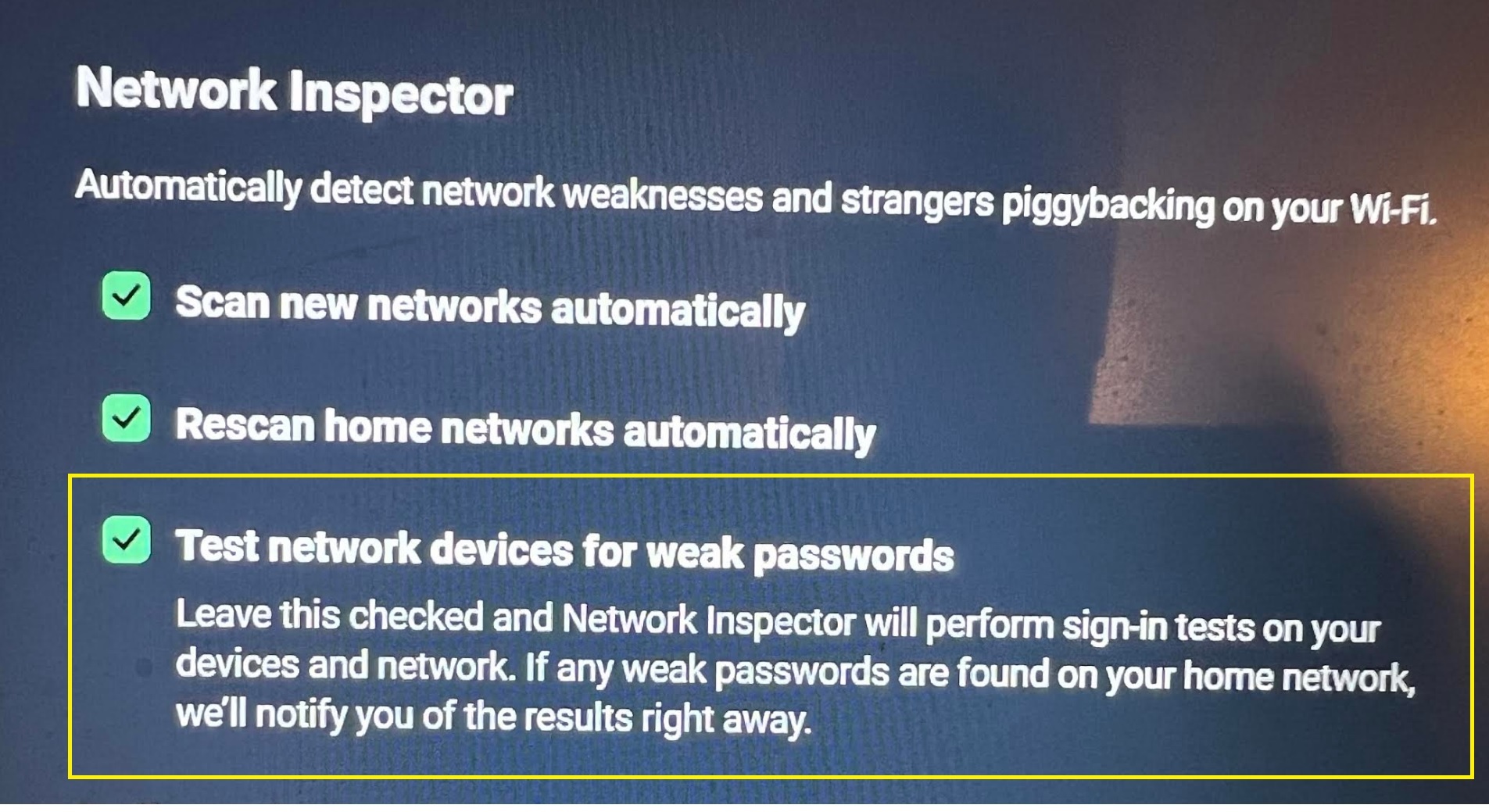
Disabling it stops the brute force from happening ![]()
So not a real malware as such, but definitly something I have now turned off; hope this can helps others identify and disable what could be seen by many as a malware
Thanks again to all for your help