Scenario :
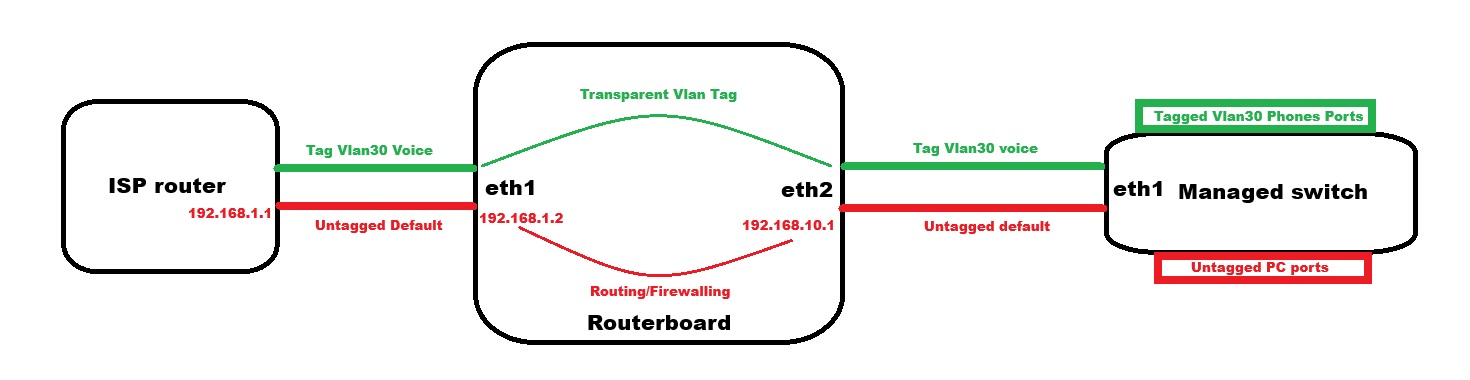
Single eth port connection between devices.
How can I run voice vlan transparently over RB while internet connectivity is routed ?
Thanks.
Scenario :

Single eth port connection between devices.
How can I run voice vlan transparently over RB while internet connectivity is routed ?
Thanks.
What is the model of your MikroTik router? Depending on the hardware you might want to use ports other than ether1 and ether2 to make use of hardware offload. Also, depending on the hardware, the configuration might be done with Bridge VLAN Filtering or over the old /interface ethernet switch menu.
The general idea is to put the two ports in a single bridge (that can also have other ports) and configure VLAN on that bridge (Bridge VLAN Filtering or /interface ethernet switch depending on the hardware). The two ports will be hybrid ports. The port towards the ISP router has VLAN30 tagged and VLAN1000 (or any other number) untagged. The port towards the switch has VLAN30 tagged and VLAN2000 untagged (but because your switch is a managed switch, this VLAN2000 can be a tagged VLAN too if you want, so that the 2nd port is a normal trunk port instead of a hybrid port).
VLAN1000 is the WAN interface with 192.168.1.2/24 and NAT configured. VLAN2000 is the LAN interface with 192.168.10.1/24 and DHCP Server configured.
Regarding “any other number”: range for VLAN number is 0-4095 (a 12-bit unsigned integer). However, to avoid problems, usable range is from 2 to 4094 (both included). Syntactically it is correct also to use 1 but since it’s used in default config by many vendors (some actually treat it specially) it’s best not to use it unless it’s mandatory. Number 4095 is reserved and 0 is not permitted (it’s used on frames which only carry QoS bits but are otherwise untagged).
It is not clear what is coming from ISP.
One cable with two streams of data one untaggged and one tagged
One cable with two streams of data tagged
Two cables one an untagged internet traffic for termination, and one tagged VOIP traffic for termination
A picture is worth a thousand words…
Always… ![]()
![]()
Anav:
One cable with two streams of data one untaggged and one tagged
ISP provides a bunch of IP phones working on a tagged Vlan with their own ip subnet (I don’t know wich one yet and I shouldn’t care of) but just a one port router with both Vlans/subnets to be managed.
The first suggestion is indeed simpler to do than to explain…
Declaring the single Vlan30 tagged on both ports of the same bridge actually connect them both at L2, while assigning a second and a third Vlan one on each port makes the routing happen.
I used the “trunk” (tagged) way between RB and switch succesfully.
Makes no sense to me,
If one stream has no vlan you can assign it a vlan ( as an untagged port ).
It would be wrong to call the MT port type: trunk.
Its a hybrid port!
/interface vlan
add interface=bridge name=vlan-isp vlan-id=10
add interface=bridge name=vlan-voip vlan-id=30
add interface=bridge name=vlan-home vlan-id=20 { need pool, ip address etc… }
add interface=bridge name=vlan-mgmt vlan-id=99 { need pool, ip address etc… }
/interface bridge port
add bridge=bridge ingress-filtering=no interface=ether1 pvid=10
add bridge=bridge ingress-filtering=yes frame-types-admit-only interface=ether2 comment=“trunk port to switch”
/interface bridge vlan
add bridge=bridge tagged=bridge untagged=ether1 vlan-id=10
add bridge=bridge tagged=bridge,ether1,ether2 vlan-id=30
add bridge=bridge tagged=bridge,ether2 vlan-id=20,99
EITHER
/ip dhcp client
add interface=vlan10-isp
OR
/ip dhcp client
add disabled=yes
/ip address
add address=192.168.1.2/24 interface=vlan10 network=192.168.1.0
The managed switch is fed a trunk port from the MT and should get an IP address on the vlan99 subnet.
In fact, actually that’s the configuration…
I said: “I used the “trunk” (tagged) way between RB and switch succesfully.”
Of course the port facing ISP is hybrid.
eth1_to_isp = hybrid port (Vlan 30 tagged, Vlan “X” untagged)
eth2_to_switch = “trunk” port (Vlan30 + Vlan “Y” both tagged).
I have a separate management vlan, but it is not required if your home vlan is trusted enough.