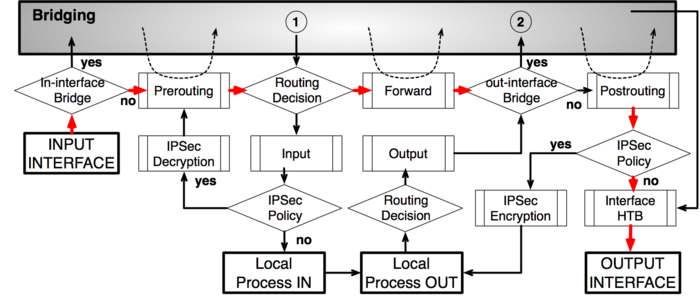
can anybody explain to me, why my firewall rules and chains do not behave as expected?
I have numerous rules setup under /ip firewall filter, but some of them seems to have no effect.
for example:
PING seems to be enabled in rule #3, but if I ping, and disable this rule...nothing happens, I can still ping the server behind firewall.
Open SSH PORT 22...I cannot open it no mater what. Took me 1 hour to test all possible combinations, put it into INPUT, FORWARD rule, setup IP, or without IP, tried NEW connection or empty.... but no, I cannot open port 22 to server behind firewall:
Code: Select all
3 chain=input action=accept connection-state=new protocol=tcp dst-port=22
Any advice welcome!
Code: Select all
0 ;;; Allow Established Connections
chain=input action=accept connection-state=established
1 chain=input action=accept protocol=icmp
2 chain=input action=accept src-address=192.168.1.0/24 in-interface=!ether2
3 chain=input action=drop connection-state=invalid
4 chain=input action=drop
5 chain=forward action=accept connection-state=established
6 chain=forward action=accept connection-state=related
7 chain=forward action=drop connection-state=invalid protocol=tcp
8 chain=forward action=drop src-address=0.0.0.0/8
9 chain=forward action=drop dst-address=0.0.0.0/8
10 chain=forward action=drop src-address=127.0.0.0/8
11 chain=forward action=drop dst-address=127.0.0.0/8
12 chain=forward action=drop src-address=224.0.0.0/3
13 chain=forward action=drop dst-address=224.0.0.0/3
14 chain=forward action=jump jump-target=tcp protocol=tcp
15 chain=forward action=jump jump-target=udp protocol=udp
16 chain=forward action=jump jump-target=icmp protocol=icmp
17 ;;; deny TFTP
chain=tcp action=drop protocol=tcp dst-port=69
18 ;;; deny RPC pocp action=drop protocol=tcp dst-port=111
19 ;;; deny RPC porter
chain=tcp action=drop protocol=tcp dst-port=135
20 ;;; deny NBT
chain=tcp action=drop protocol=tcp dst-port=137-139
21 ;;; deny cifs
chain=tcp action=drop protocol=tcp dst-port=445
22 ;;; deny NFS
chain=tcp action=drop protocol=tcp dst-port=2049
23 ;;; deny NetBus
chain=tcp action=drop protocol=tcp dst-port=12345-12346
24 ;;; deny NetBus
chain=tcp action=drop protocol=tcp dst-port=20034
25 ;;; deny BackOriffice
chain=tcp action=drop protocol=tcp dst-port=3133
26 ;;; deny DHCP
chain=tcp action=drop protocol=tcp dst-port=67-68
27 ;;; deny TFTP
chain=udp action=drop protocol=udp dst-port=69
28 ;;; deny PRC portmapper
chain=udp action=drop protocol=udp dst-port=111
29 ;;; deny PRC portmapper
chain=udp action=drop protocol=udp dst-port=135
30 ;;; deny NBT
chain=udp action=drop protocol=udp dst-port=137-139
31 ;;; deny NFS
chain=udp action=drop protocol=udp dst-port=2049
32 ;;; deny BackOriffice
chain=udp action=drop protocol=udp dst-port=3133
33 ;;; echo reply
chain=icmp action=accept protocol=icmp icmp-options=0:0
34 ;;; net unreachable
chain=icmp action=accept protocol=icmp icmp-options=3:0
35 ;;; host unreachable
chain=icmp action=accept protocol=icmp icmp-options=3:1
36 ;;; host unreachable fragmentation required
chain=icmp action=accept protocol=icmp icmp-options=3:4
37 ;;; allow source quench
chain=icmp action=accept protocol=icmp icmp-options=4:0
38 ;;; allow echo request
chain=icmp action=accept protocol=icmp icmp-options=8:0
39 ;;; allow time exceed
chain=icmp action=accept protocol=icmp icmp-options=11:0
40 chain=icmp action=accept protocol=icmp icmp-options=12:0
41 ;;; deny all other types
chain=icmp action=drop
42 ;;; drop ftp brute forcers
chain=input action=drop protocol=tcp src-address-list=ftp_blacklist dst-port=21
43 chain=output action=accept protocol=tcp content=530 Login incorrect dst-limit=1/1m,9,dst-address/1m
44 chain=output action=add-dst-to-address-list protocol=tcp address-list=ftp_blacklist address-list-timeout=3h
content=530 Login incorrect
45 ;;; drop ssh brute forcers
chain=input action=drop protocol=tcp src-address-list=ssh_blacklist dst-port=22
46 chain=input action=add-src-to-address-list connection-state=new protocol=tcp src-address-list=ssh_stage3
address-list=ssh_blacklist address-list-timeout=1w3d dst-port=22
47 chain=input action=add-src-to-address-list connection-state=new protocol=tcp src-address-list=ssh_stage2
address-list=ssh_stage3 address-list-timeout=1m dst-port=22
48 chain=input action=add-src-to-address-list connection-state=new protocol=tcp src-address-list=ssh_stage1
address-list=ssh_stage2 address-list-timeout=1m dst-port=22
49 chain=input action=add-src-to-address-list connection-state=new protocol=tcp address-list=ssh_stage1
address-list-timeout=1m dst-port=22
50 ;;; Port scanners to list
chain=input action=add-src-to-address-list protocol=tcp psd=21,3s,3,1 address-list=port scanners
address-list-timeout=2w
51 ;;; NMAP FIN Stealth scan
chain=input action=add-src-to-address-list tcp-flags=fin,!syn,!rst,!psh,!ack,!urg protocol=tcp
address-list=port scanners address-list-timeout=2w
52 ;;; SYN/FIN scan
chain=input action=add-src-to-address-list tcp-flags=fin,syn protocol=tcp address-list=port scanners
address-list-timeout=2w
53 ;;; SYN/RST scan
chain=input action=add-src-to-address-list tcp-flags=syn,rst protocol=tcp address-list=port scanners
address-list-timeout=2w
54 ;;; FIN/PSH/URG scan
chain=input action=add-src-to-address-list tcp-flags=fin,psh,urg,!syn,!rst,!ack protocol=tcp
address-list=port scanners address-list-timeout=2w
55 ;;; ALL/ALL scan
chain=input action=add-src-to-address-list tcp-flags=fin,syn,rst,psh,ack,urg protocol=tcp
address-list=port scanners address-list-timeout=2w
56 ;;; NMAP NULL scan
chain=input action=add-src-to-address-list tcp-flags=!fin,!syn,!rst,!psh,!ack,!urg protocol=tcp
address-list=port scanners address-list-timeout=2w
57 ;;; dropping port scanners
chain=input action=drop src-address-list=port scanners