Have a read overhere on that: http://forum.mikrotik.com/t/nordvpn-ipsec-ikev2-killswitch-for-ros6/144817/1
My contribution: http://forum.mikrotik.com/t/nordvpn-ipsec-ikev2-killswitch-for-ros6/144817/1 usin IPSEC Policies.
Look where Forward is the flow, before deciding of IPSEC out. So policy is not set then.
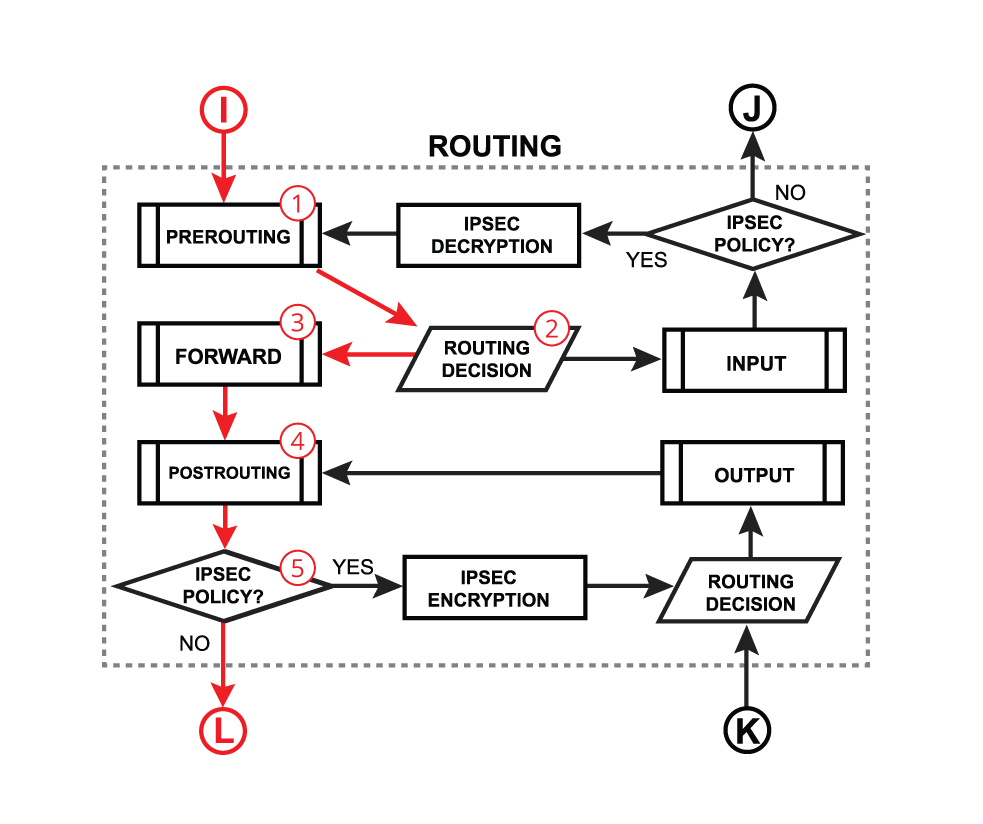
https://help.mikrotik.com/docs/display/ROS/Packet+Flow+in+RouterOS#PacketFlowinRouterOS-Forward
Postrouting (Mangle) see every forwarded packet, Output (Mangle) sees only the packets generated by the router self and in this case your outgoing encrypted traffic.
To set MSS you have to use Postrouting as then the outgoing packet is still unencrypted. But then you still can’t use ipsec-out because it is still before that is set. And once encrypted your can’t use MSS. You can’t so filter on that and you have to use the connection-mark “Mark” to recognize that traffic.
chain=postrouting action=change-mss new-mss=1382 passthrough=yes tcp-flags=syn protocol=tcp connection-mark=MARK log=yes log-prefix="MANGLE_SET_TCP_MSS_IPSEC"
Optimized to only handle packets bigger than 1383 (in your case) and because it Postrouting (end of the line) you can mark passthrough=no so that the rest of rules in Mangle are ignored
chain=postrouting action=change-mss new-mss=1382 passthrough=no tcp-flags=syn protocol=tcp connection-mark=Mark tcp-mss=1383-65535 log=yes log-prefix="MANGLE_SET_TCP_MSS_IPSEC_OUT"