Good afternoon! Can you tell me where the problem is?
Network diagram: Router R2 is with a routable IP and domain name, followed by a NAS (which acts as a central hub for IP cameras) and an IP camera.
R1, R3 with private IP, followed by IP cameras.
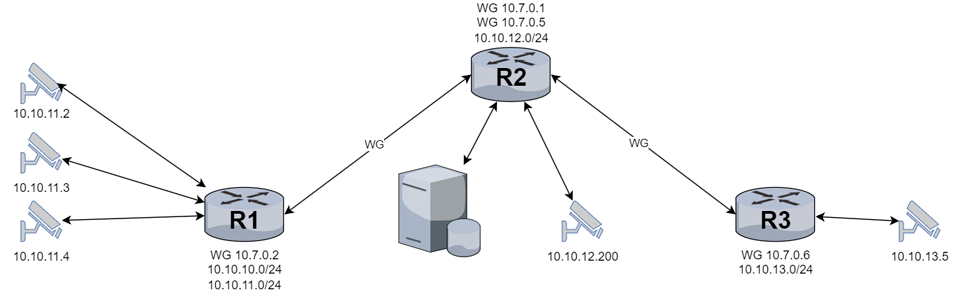
Currently, R2 users have access to the network on 10.10.10.0/24, 10.10.11.0/24 and 10.10.13.0/24.
The goal is to be behind any router to have access to other routers and equipment behind them.
Config Router R2 10.10.12.0/24:
/interface wireguard add comment="WG-own-VPN RB5009" listen-port=51819 mtu=1420 name=WG1-RB5009
/interface wireguard add comment="WG-own-VPN hAP aX2" listen-port=51818 mtu=1420 name=WG2-AX2
/interface list member add interface=WG1-RB5009 list=LAN
/interface list member add interface=WG2-AX2 list=LAN
/ip address add address=10.7.0.1/30 interface=WG1-RB5009 network=10.7.0.0
/ip address add address=10.7.0.5/30 interface=WG2-AX2 network=10.7.0.4
/interface wireguard peers add allowed-address=10.7.0.2/32,10.10.10.0/24,10.10.11.0/24 comment=RB5009 interface=WG1-RB5009 persistent-keepalive=1m public-key="xxxx"
/interface wireguard peers add allowed-address=10.7.0.6/32,10.10.13.0/24 comment="hAP aX2" interface=WG2-AX2 persistent-keepalive=1m public-key="xxxx"
/ip firewall filter add action=accept chain=input comment="WireGuard VPN" connection-state=established,related,new dst-port=51818-51820 in-interface-list=WANs protocol=udp
/routing bgp connection add as=65000 connect=yes disabled=no listen=yes local.address=10.7.0.1 .role=ibgp-rr name=TO-RB5009 nexthop-choice=force-self output.network=LAN_IP .redistribute=bgp remote.address=10.7.0.2/32 .as=65000 router-id=10.10.12.1 routing-table=main
/routing bgp connection add as=65000 connect=yes disabled=no listen=yes local.address=10.7.0.5 .role=ibgp-rr name=TO-AX2 nexthop-choice=force-self output.network=LAN_IP .redistribute=bgp remote.address=10.7.0.6/32 .as=65000 router-id=10.10.12.1 routing-table=main
Config Router R1 10.10.10(11).0/24:
/interface wireguard add comment=WG-Own-VPN listen-port=51819 mtu=1420 name=WG1-AX3
/interface wireguard peers add allowed-address=10.7.0.0/24,10.10.12.0/24,10.10.13.0/24 comment="Own-VPN hAP aX3" endpoint-address=xxxx.xx endpoint-port=51819 interface=WG1-AX3 persistent-keepalive=1m public-key="xxxx"
/interface list member add interface=WG1-AX3 list=LAN
/ip address add address=10.7.0.2/30 interface=WG1-AX3 network=10.7.0.0
/ip firewall filter add action=accept chain=input comment="WireGuard VPN" connection-state=established,related,new dst-port=51819-51820 in-interface-list=WANs protocol=udp
/routing bgp connection add as=65000 connect=yes disabled=no listen=yes local.address=10.7.0.2 .role=ibgp-rr-client name=TO-AX3 output.network=LAN_IP .redistribute=static remote.address=10.7.0.1/32 .as=65000 router-id=10.10.10.1 routing-table=main
Config Router R3 10.10.13.0/24:
/interface wireguard add comment=WG-Own-VPN listen-port=51818 mtu=1420 name=WG2-AX3
/interface wireguard peers add allowed-address=10.7.0.0/24,10.10.10.0/24,10.10.11.0/24,10.10.12.0/24 comment="to WG-Own-VPN" endpoint-address=xxxx.xx endpoint-port=51818 interface=WG2-AX3 persistent-keepalive=1m public-key="zzzz"
/interface list member add interface=WG2-AX3 list=LAN
/ip address add address=10.7.0.6/30 interface=WG2-AX3 network=10.7.0.4
/ip firewall filter add action=accept chain=input connection-state=established,related,new dst-port=51818,51820 in-interface-list=WAN protocol=udp
/routing bgp connection add as=65000 connect=yes disabled=no listen=yes local.address=10.7.0.6 .role=ibgp-rr-client name=TO-AX3 output.network=LAN_IP remote.address=10.7.0.5/32 .as=65000 router-id=10.10.13.1 routing-table=main
After everything was connected, I configured routing via BGP and dynamic routes appeared on all routers.
R1
/ip/route/ print
Flags: D - DYNAMIC; A - ACTIVE; c - CONNECT, s - STATIC, b - BGP, v - VPN
Columns: DST-ADDRESS, GATEWAY, DISTANCE
# DST-ADDRESS GATEWAY DISTANCE
DAv 0.0.0.0/0 ISP1-PPPoE 2
DAc 10.7.0.0/30 WG1-AX3 0
DAc 10.10.10.0/24 Bridge.10 0
DAc 10.10.11.0/24 VBridge.11 0
DAb 10.10.12.0/24 10.7.0.1 200
DAb 10.10.13.0/24 10.7.0.6 200
DAc 10.110.54.1/32 ISP1-PPPoE 0
;;; Acceess to SFP module
0 As 192.168.1.0/24 SFP 1
DAc 192.168.1.0/32 SFP 0
R2
/ip/route> print
Flags: D - DYNAMIC; A - ACTIVE; c - CONNECT, s - STATIC, b - BGP, d - DHCP
Columns: DST-ADDRESS, GATEWAY, DISTANCE
# DST-ADDRESS GATEWAY DISTANCE
DAc 10.7.0.0/30 WG1-RB5009 0
DAc 10.7.0.4/30 WG2-AX2 0
DAb 10.10.10.0/24 10.7.0.2 200
DAb 10.10.11.0/24 10.7.0.2 200
DAc 10.10.12.0/24 Bridge 0
DAb 10.10.13.0/24 10.7.0.6 200
DAc 81.163.176.0/22 WAN 0
DAb 192.168.1.0/24 10.7.0.2 200
R3
/ip/route> print
Flags: D - DYNAMIC; X - DISABLED, I - INACTIVE, A - ACTIVE; c - CONNECT, s - STATIC, b - BGP, d - DHCP
Columns: DST-ADDRESS, GATEWAY, DISTANCE
# DST-ADDRESS GATEWAY DISTANCE
DAd 0.0.0.0/0 192.168.64.254 1
DAc 10.7.0.4/30 WG2-AX3 0
DAb 10.10.10.0/24 10.7.0.2 200
DAb 10.10.11.0/24 10.7.0.2 200
DAb 10.10.12.0/24 10.7.0.5 200
DAc 10.10.13.0/24 Bridge 0
DAb 192.168.1.0/24 10.7.0.2 200
DAc 192.168.64.0/24 WAN 0
But when tracing from R1 to R3, it does not pass through R2.
/tool> traceroute 10.10.13.1
Columns: ADDRESS, LOSS, SENT, LAST, AVG, BEST, WORST, STD-DEV
# ADDRESS LOSS SENT LAST AVG BEST WORST STD-DEV
1 10.110.54.1 0% 1 1.5ms 1.5 1.5 1.5 0
2 172.10.0.202 0% 1 2.3ms 2.3 2.3 2.3 0
3 5.181.211.13 0% 1 1.2ms 1.2 1.2 1.2 0
4 100.105.103.157 0% 1 2.2ms 2.2 2.2 2.2 0
5 194.187.204.9 0% 1 3.2ms 3.2 3.2 3.2 0
6 100% 1 timeout
As well as in the opposite direction from R3 to R1.
/tool> traceroute 10.10.10.1
Columns: ADDRESS, LOSS, SENT, LAST, AVG, BEST, WORST, STD-DEV
# ADDRESS LOSS SENT LAST AVG BEST WORST STD-DEV
1 192.168.64.254 0% 2 0.4ms 0.5 0.4 0.5 0.1
2 85.117.68.16 0% 2 2.4ms 2.5 2.4 2.6 0.1
3 85.117.68.17 0% 2 2.2ms 2.1 2 2.2 0.1
4 85.117.68.101 0% 2 3ms 2.9 2.7 3 0.2
5 10.220.191.125 0% 2 2.6ms 2.6 2.6 2.6 0
6 212.188.16.238 0% 2 2.2ms 2.3 2.2 2.3 0.1
7 212.188.56.41 0% 2 12.3ms 12.3 12.3 12.3 0
8 212.188.29.145 0% 2 22.7ms 22.7 22.6 22.7 0.1
9 212.188.56.37 0% 2 34.3ms 34.3 34.3 34.3 0
10 212.188.29.85 0% 2 50.3ms 50.3 50.2 50.3 0.1
11 195.34.50.161 0% 2 62.2ms 62.1 62 62.2 0.1
12 100% 2 timeout