My PC ROS has 3 NICs: PUBLIC, LOCAL (192.168.1.0/24), and PRIVATE (192.168.2.0/24, for my personal use). Earlier today, my LOCAL network suddenly started acting up. VERY frequent connection drops & RTOs, high latency, and it took forever to reconnect. The PRIVATE network is fine, even now.
I then looked up the LOCAL interface traffic, and it shows 2.4Mbps Tx and 7.1Mbps Rx (holy smokes!!
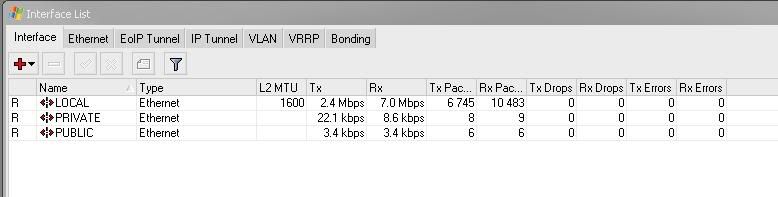
After I torched it, I see this:
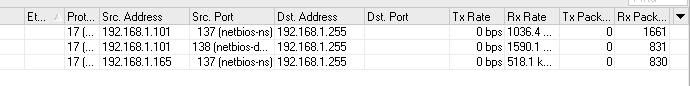
Here's what I put in my firewall rules:
Code: Select all
Flags: X - disabled, I - invalid, D - dynamic
0 ;;; Allow established connections
chain=input action=accept connection-state=established
1 ;;; Allow related connections
chain=input action=accept connection-state=related
2 ;;; Drop invalid connections
chain=input action=drop connection-state=invalid
3 ;;; Blocking outside relay
chain=input action=drop protocol=tcp src-address=0.0.0.0/0 in-interface=PUBLIC dst-port=8080
4 ;;; Allow UDP
chain=input action=accept protocol=udp
5 ;;; Allow limited ICMP
chain=input action=accept protocol=icmp limit=50/5s,2
6 ;;; Drop excess pings
chain=input action=drop protocol=icmp
7 ;;; Allow access from local network
chain=input action=accept in-interface=!PUBLIC
8 ;;; Blocking telnet access method
chain=input action=drop protocol=tcp dst-port=23
9 ;;; Log everything else
chain=input action=log log-prefix="DROP INPUT"
10 ;;; Drop everything else
chain=input action=drop
11 ;;; allow established connections
chain=forward action=accept connection-state=established
12 ;;; allow related connections
chain=forward action=accept connection-state=related
13 ;;; drop invalid connections
chain=forward action=drop connection-state=invalid
14 chain=forward action=drop src-address=0.0.0.0/8
15 chain=forward action=drop dst-address=0.0.0.0/8
16 chain=forward action=drop src-address=127.0.0.0/8
17 chain=forward action=drop dst-address=127.0.0.0/8
18 chain=forward action=drop src-address=224.0.0.0/3
19 chain=forward action=drop dst-address=224.0.0.0/3
20 chain=forward action=drop protocol=tcp dst-port=135
21 chain=forward action=drop tcp-flags=syn protocol=tcp connection-limit=6,32
22 ;;; jump to the tcp chain
chain=forward action=jump jump-target=tcp protocol=tcp
23 ;;; jump to the udp chain
chain=forward action=jump jump-target=udp protocol=udp
24 ;;; jump to the icmp chain
chain=forward action=jump jump-target=icmp protocol=icmp
25 ;;; Log dropped connections
chain=forward action=log log-prefix="DROP FORWARD"
26 ;;; Drop and log everything else
chain=forward action=drop protocol=!tcp
27 ;;; deny TFTP
chain=tcp action=drop protocol=tcp dst-port=69
28 ;;; deny RPC portmapper
chain=tcp action=drop protocol=tcp dst-port=111
29 ;;; deny RPC portmapper & NBT
chain=tcp action=drop protocol=tcp dst-port=135-139
30 ;;; deny cifs
chain=tcp action=drop protocol=tcp dst-port=445
31 ;;; deny NFS
chain=tcp action=drop protocol=tcp dst-port=2049
32 ;;; deny NetBus
chain=tcp action=drop protocol=tcp dst-port=12345-12346
33 ;;; deny NetBus
chain=tcp action=drop protocol=tcp dst-port=20034
34 ;;; deny BackOriffice
chain=tcp action=drop protocol=tcp dst-port=3133
35 ;;; deny DHCP
chain=tcp action=drop protocol=tcp dst-port=67-68
36 ;;; deny TFTP
chain=udp action=drop protocol=udp dst-port=69
37 ;;; deny PRC portmapper
chain=udp action=drop protocol=udp dst-port=111
38 ;;; deny PRC portmapper & NBT
chain=udp action=drop protocol=udp dst-port=135-139
39 ;;; deny NFS
chain=udp action=drop protocol=udp dst-port=2049
40 ;;; deny BackOriffice
chain=udp action=drop protocol=udp dst-port=3133
41 ;;; drop invalid connections
chain=icmp action=accept protocol=icmp icmp-options=0:0
42 ;;; allow established connections
chain=icmp action=accept protocol=icmp icmp-options=3:0
43 ;;; allow already established connections
chain=icmp action=accept protocol=icmp icmp-options=3:1
44 ;;; allow source quench
chain=icmp action=accept protocol=icmp icmp-options=4:0
45 ;;; allow echo request
chain=icmp action=accept protocol=icmp icmp-options=8:0
46 ;;; allow time exceed
chain=icmp action=accept protocol=icmp icmp-options=11:0
47 ;;; allow parameter bad
chain=icmp action=accept protocol=icmp icmp-options=12:0
48 ;;; deny all other types
chain=icmp action=drop Oh, by the way, that computer in the 2nd picture (192.168.1.165) is not powered on when I took the picture. I turned it off about an hour before the picture was taken, but it's still there! GAAAHHH!!!
I really don't think it's virus/trojan/worm/the like, because I keep the AV definitions updated with the latest version (well, it auto-updates, but meh...). And EVEN IF IT IS, the firewall should've blocked it, no?
Please, please, please help.
I've been working on this for 10 hours, been reading documentations, manuals, and tutorials till my eyes bleed, and I still can't figure out what's wrong. Plus, I only have several hours before my boss comes in and starts yelling at me.
Thanks a gazillion
-Ted-




