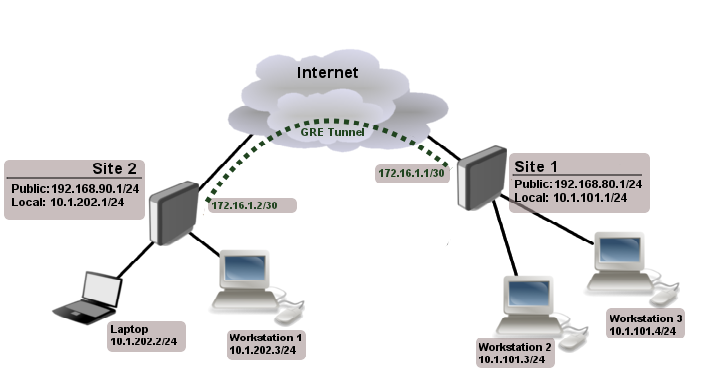
This is my network: (example)
My REAL Configuration:
Code: Select all
/interface bridge
add arp=proxy-arp fast-forward=no name=LOCAL
add disabled=yes fast-forward=no name=WAN
/interface gre
add allow-fast-path=no comment=GREIZI1 ipsec-secret=XXXXXXXXXXXXXXXX !keepalive local-address=83.XXX.ХХХ.XXX name=gre-izi-ЧЧЧ remote-address=185.ЧЧЧ.255.ЧЧЧ
add allow-fast-path=no comment=GREIZI2 disabled=yes !keepalive local-address=83.XXX.ХХХ.XXX name=gre-izi-ЧЧЧ2 remote-address=185.ЧЧЧ.255.ЧЧЧ
add allow-fast-path=no ipsec-secret=XXXXXXXXXXXXXXXX !keepalive local-address=83.XXX.ХХХ.XXX name=gre-ГГГz-ЧЧЧ remote-address=91.211.ЧЧ.ЧЧЧ
/interface vlan
add interface=LOCAL name=vlan10-СССvlan-id=10
add interface=LOCAL name=vlan20-ГГГ vlan-id=20
add interface=LOCAL name=vlan24-МММ vlan-id=24
add interface=LOCAL name=vlan30-TEL vlan-id=30
add interface=LOCAL name=vlan40-CAMERA vlan-id=40
add interface=LOCAL name=vlan88-GUEST vlan-id=88
add interface=LOCAL name=vlan99-VPN vlan-id=99
add interface=LOCAL name=vlan100-USER vlan-id=100
/interface list
add name=WAN1
/ip ipsec proposal
set [ find default=yes ] auth-algorithms=md5
/routing ospf area
add area-id=192.168.213.0 name=home
/routing ospf instance
set [ find default=yes ] router-id=192.168.200.1
/tool user-manager customer
set admin access=own-routers,own-users,own-profiles,own-limits,config-payment-gw
/interface bridge port
add bridge=LOCAL interface=ether3
add bridge=LOCAL interface=ether4
add bridge=LOCAL interface=ether5
add bridge=WAN hw=no interface=sfp-sfpplus2
add bridge=WAN interface=ether1
add bridge=LOCAL interface=ether8
add bridge=WAN hw=no interface=sfp-sfpplus1
add bridge=LOCAL interface=ether6
add bridge=LOCAL interface=ether7
/ip address
add address=192.168.40.1/24 comment=Vlan40 interface=vlan40-CAMERA network=192.168.40.0
add address=83.XXX.ХХХ.XXX/24 comment=NEO_old interface=ether1 network=83.XXX.ХХХ.0
add address=192.168.24.1/24 comment=Vlan24 interface=vlan24-МММ network=192.168.24.0
add address=192.168.10.1/24 comment=Vlan10 interface=vlan10-СССnetwork=192.168.10.0
add address=192.168.20.1/24 comment=Vlan20 interface=vlan20-ГГГ network=192.168.20.0
add address=192.168.88.1/24 comment=Vlan88 interface=vlan88-GUEST network=192.168.88.0
add address=192.168.100.1/24 comment=Vlan100 interface=vlan100-USER network=192.168.100.0
add address=192.168.200.1/24 comment=admin interface=LOCAL network=192.168.200.0
add address=172.22.2.33/30 comment=shar interface=shar network=172.22.2.32
add address=172.22.252.9/30 comment=gre-ГГГz-ЧЧЧ interface=gre-ГГГz-ЧЧЧ network=172.22.252.8
add address=172.22.2.29/30 comment=gre-МММ-ЧЧЧ1 interface=gre-izi-ЧЧЧ network=172.22.2.28
add address=83.XXX.ХХХ.72/24 comment=NEO_СССinterface=ether1 network=83.XXX.ХХХ.0
add address=83.XXX.ХХХ.73/24 comment=NEO_МММ interface=ether1 network=83.XXX.ХХХ.0
add address=83.XXX.ХХХ.74/24 comment=NEO_ГГГ interface=ether1 network=83.XXX.ХХХ.0
add address=192.168.30.1/24 comment=Vlan30 interface=vlan30-TEL network=192.168.30.0
add address=89.ХХХ.ХХХ.217/26 disabled=yes interface=ether2 network=89.ХХХ.ХХХ.192
add address=192.168.99.1/24 interface=vlan99-VPN network=192.168.99.0
add address=172.22.4.29/30 comment=gre-МММ-ЧЧЧ2 disabled=yes interface=gre-izi-ЧЧЧ2 network=172.22.4.28
/ip dhcp-server network
add address=192.168.10.0/24 dns-server=192.168.10.20,192.168.24.20,192.168.20.20 gateway=192.168.10.1
add address=192.168.20.0/24 dns-server=192.168.20.20,192.168.24.20,192.168.10.20 gateway=192.168.20.1
add address=192.168.24.0/24 dns-server=192.168.24.20,192.168.24.1 gateway=192.168.24.1
add address=192.168.30.0/24 dns-server=192.168.10.20,192.168.24.20 gateway=192.168.30.1
add address=192.168.40.0/24 dns-server=192.168.40.1,8.8.8.8 gateway=192.168.40.1
add address=192.168.88.0/24 dns-server=192.168.88.1,8.8.8.8 gateway=192.168.88.1
add address=192.168.100.0/24 dns-server=192.168.100.1,192.168.10.20,192.168.20.20,192.168.24.20 gateway=192.168.100.1
add address=192.168.200.0/24 dns-server=192.168.10.20,192.168.24.20,192.168.20.20,192.168.100.1 gateway=192.168.200.1
/ip dns
set allow-remote-requests=yes servers=217.150.ххх.ххх,217.150.1ЧЧЧ.ххх
/ip firewall nat
add action=src-nat chain=srcnat out-interface=ether1 src-address=192.168.10.0/24 to-addresses=83.XXX.ХХХ.72
add action=src-nat chain=srcnat out-interface=ether1 src-address=192.168.24.0/24 to-addresses=83.XXX.ХХХ.73
add action=src-nat chain=srcnat out-interface=ether1 src-address=192.168.20.0/24 to-addresses=83.XXX.ХХХ.74
add action=masquerade chain=srcnat out-interface=ovpn-ProxMox
add action=masquerade chain=srcnat out-interface=ether1
add action=dst-nat chain=dstnat dst-address=83.XXX.ХХХ.72 dst-port=1720 protocol=tcp to-addresses=192.168.10.60 to-ports=1720
add action=dst-nat chain=dstnat dst-address=83.XXX.ХХХ.72 dst-port=1720 protocol=tcp to-addresses=192.168.10.60 to-ports=1720
add action=dst-nat chain=dstnat dst-address=83.XXX.ХХХ.72 dst-port=50000-50499 protocol=udp to-addresses=192.168.10.60 to-ports=50000-50499
add action=dst-nat chain=dstnat dst-address=83.XXX.ХХХ.72 dst-port=50000-50499 protocol=tcp to-addresses=192.168.10.60 to-ports=50000-50499
add action=dst-nat chain=dstnat dst-address=83.XXX.ХХХ.XXX dst-port=50000-50499 protocol=udp to-addresses=192.168.10.60 to-ports=50000-50499
add action=dst-nat chain=dstnat dst-address=83.XXX.ХХХ.XXX dst-port=34567 protocol=tcp to-addresses=192.168.40.200 to-ports=34567
add action=dst-nat chain=dstnat disabled=yes dst-address=83.XXX.ХХХ.XXX dst-port=80 protocol=tcp to-addresses=192.168.40.238 to-ports=80
add action=dst-nat chain=dstnat disabled=yes dst-address=83.XXX.ХХХ.72 dst-port=25 protocol=tcp src-address=138.ЧЧЧ.ЧЧЧ.94 to-addresses=192.168.10.26 to-ports=25
add action=dst-nat chain=dstnat disabled=yes dst-address=83.XXX.ХХХ.72 dst-port=25 protocol=tcp src-address=185.ЧЧЧ.ЧЧЧ.5 to-addresses=192.168.10.26 to-ports=25
/ip firewall service-port
set sip disabled=yes
/ip route
add check-gateway=ping disabled=yes distance=1 gateway=83.XXX.ХХХ.1 pref-src=83.XXX.ХХХ.72 routing-mark=mail_sph
add distance=1 gateway=83.XXX.ХХХ.1
add disabled=yes distance=1 gateway=89.ХХХ.ХХХ.1ЧЧЧ
add distance=220 dst-address=10.1.1.0/24 gateway=gre-izi-xxx2 scope=20
add disabled=yes distance=1 dst-address=192.168.19.0/24 gateway=172.22.252.10
/routing igmp-proxy
set quick-leave=yes
/routing igmp-proxy interface
add alternative-subnets=0.0.0.0/0 interface=ether1 upstream=yes
add interface=LOCAL
/routing ospf network
add area=backbone network=172.22.2.32/30
add area=backbone network=172.22.252.8/30
add area=backbone network=192.168.100.0/24
add area=backbone network=192.168.24.0/24
add area=backbone network=192.168.20.0/24
add area=backbone network=172.22.2.28/30
add area=backbone network=192.168.200.0/24
add area=backbone network=192.168.10.0/24
add area=backbone network=192.168.19.0/24
add area=backbone network=192.168.99.0/24
add area=backbone network=172.22.4.28/30Why is the connection IP 172.16.1.1 (IP my tunnel) ?
https://ibb.co/fBW30K

