I am trying to create a L2TP VPN for an iphone to connect back, and I am getting this error:

Here is how the proposals are setup:
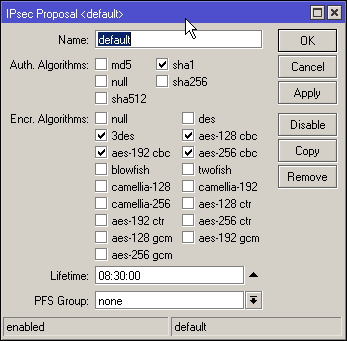
Anyone know how to fix this?


Same, still error.Check and aes-128-cbc
Code: Select all
[admin@FMT-ROUTER] > /ip ipsec policy print
Flags: T - template, X - disabled, D - dynamic, I - invalid, A - active,
* - default
0 T * group=default src-address=::/0 dst-address=::/0 protocol=all
proposal=default template=yes
[admin@FMT-ROUTER] >
Sorry, same issue.You might try setting PFS Group=modp1024. That fixed mine when I had an error the other day.
encmode mismatched: my:Tunnel peer:TransportMikrotik is directly on the internet.A blind shot - is the public IP address to which you point your iPhone directly at the Mikrotik or is it up at some equipment between the Mikrotik and the internet and UDP ports 500 and 4500 are forwarded to the Mikrotik from there?
Sorry, it was too late yesterday and haven't realized that you actually use L2TP over IPsec, not just IPsec. In this case, the transport mode is used at IPsec level and the tunnelling functionality is provided by L2TP, so there is most likely something wrong in your Mikrotik configuration.I am actually wanting the iphone to access the LAN and tunnel all internet traffic, but I will be fine with either.
/export hide-sensitivepub.lic.ip.1pub.lic.ip.2[admin@FMT-ROUTER] > /export hide-sensitive
# mar/19/2018 12:21:20 by RouterOS 6.42rc35
# software id = S6JE-ES6Y
#
# model = RouterBOARD 3011UiAS
/interface bridge
add admin-mac=CC:2D:E0:40:25:0F arp=proxy-arp auto-mac=no comment=defconf name=\
LAN
/interface ethernet
set [ find default-name=ether1 ] arp=proxy-arp name=INTERNET
set [ find default-name=ether2 ] name=ether2-master
set [ find default-name=ether6 ] name=ether6-master
/interface list
add exclude=dynamic name=discover
add name=mactel
add name=mac-winbox
add name=WAN
/interface wireless security-profiles
set [ find default=yes ] supplicant-identity=MikroTik
/ip ipsec proposal
set [ find default=yes ] enc-algorithms=\
aes-256-cbc,aes-192-cbc,aes-128-cbc,3des lifetime=8h30m
/ip pool
add name=dhcp ranges=192.168.2.10-192.168.2.254
add name=pool-ovpn ranges=10.255.255.2-10.255.255.254
/ip dhcp-server
add address-pool=dhcp disabled=no interface=LAN name=defconf
/ppp profile
add local-address=10.255.255.1 name=Openvpn remote-address=pool-ovpn
set *FFFFFFFE local-address=192.168.2.1 remote-address=dhcp use-compression=yes
/routing ospf area
add area-id=0.0.0.255 name=area255
/interface bridge port
add bridge=LAN comment=defconf interface=ether2-master
add bridge=LAN comment=defconf interface=ether6-master
add bridge=LAN comment=defconf hw=no interface=sfp1
add bridge=LAN interface=ether3
add bridge=LAN interface=ether4
add bridge=LAN interface=ether5
add bridge=LAN interface=ether7
add bridge=LAN interface=ether8
add bridge=LAN interface=ether9
add bridge=LAN interface=ether10
/ip neighbor discovery-settings
set discover-interface-list=discover
/interface l2tp-server server
set allow-fast-path=yes authentication=chap,mschap2 enabled=yes use-ipsec=yes
/interface list member
add interface=ether2-master list=discover
add interface=ether3 list=discover
add interface=ether4 list=discover
add interface=ether5 list=discover
add interface=sfp1 list=discover
add interface=ether6-master list=discover
add interface=ether7 list=discover
add interface=ether8 list=discover
add interface=ether9 list=discover
add interface=ether10 list=discover
add interface=LAN list=discover
add interface=LAN list=mactel
add interface=LAN list=mac-winbox
add interface=INTERNET list=WAN
/interface ovpn-server server
set certificate=myCa cipher=aes256 default-profile=Openvpn enabled=yes netmask=\
32 port=8080
/interface pptp-server server
set authentication=chap,mschap2 enabled=yes
/interface sstp-server server
set default-profile=default-encryption enabled=yes
/ip address
add address=192.168.2.1/24 comment=defconf interface=ether2-master network=\
192.168.2.0
add address=x.x.x.x/25 interface=INTERNET network=x.x.x.x
/ip cloud
set ddns-enabled=yes
/ip dhcp-client
add comment=defconf dhcp-options=hostname,clientid interface=INTERNET
/ip dhcp-server network
add address=192.168.2.0/24 comment=defconf dns-server=8.8.8.8 gateway=\
192.168.2.1 netmask=24
/ip dns
set allow-remote-requests=yes servers=8.8.8.8,4.2.2.2
/ip dns static
add address=192.168.2.1 name=router
/ip firewall filter
add action=accept chain=input dst-port=8291 protocol=tcp
add action=accept chain=input dst-port=8080 protocol=tcp
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=accept chain=input comment="defconf: accept established,related" \
connection-state=established,related
add action=accept chain=input comment="allow IPsec NAT" dst-port=4500 protocol=\
udp
add action=accept chain=input comment="allow IKE" dst-port=500 protocol=udp
add action=accept chain=input comment="allow l2tp" dst-port=1701 protocol=udp
add action=accept chain=input comment="allow pptp" dst-port=1723 protocol=tcp
add action=accept chain=input comment="allow sstp" dst-port=443 protocol=tcp
add action=drop chain=input comment="defconf: drop all from WAN" in-interface=\
INTERNET
add action=accept chain=forward comment="defconf: accept established,related" \
connection-state=established,related
add action=drop chain=forward comment="defconf: drop invalid" connection-state=\
invalid
add action=drop chain=forward comment=\
"defconf: drop all from WAN not DSTNATed" connection-nat-state=!dstnat \
connection-state=new in-interface=INTERNET
add action=accept chain=forward connection-state=established,related
add action=accept chain=forward connection-state=established,related
add action=drop chain=forward connection-state=invalid
/ip firewall nat
add action=masquerade chain=srcnat comment="defconf: masquerade" out-interface=\
INTERNET
add action=accept chain=dstnat dst-port=8291 protocol=tcp
add action=masquerade chain=srcnat comment="masq. vpn traffic" src-address=\
192.168.89.0/24
/ip ipsec peer
add address=0.0.0.0/0 dh-group=modp1024 dpd-interval=disable-dpd enc-algorithm=\
aes-256,aes-192,aes-128 exchange-mode=main-l2tp generate-policy=\
port-override hash-algorithm=md5 send-initial-contact=no
/ip route
add distance=1 gateway=x.x.x.x
add distance=1 dst-address=192.168.0.0/24 gateway=10.255.255.4
add distance=1 dst-address=192.168.1.0/24 gateway=10.255.255.3
add distance=1 dst-address=192.168.5.0/24 gateway=10.255.255.2
/ip service
set www address=0.0.0.0/0
set winbox address=0.0.0.0/0
/ppp secret
add name=vpn
add name=Openvpn-MLM profile=Openvpn remote-address=10.255.255.2
add name=Openvpn-WYN profile=Openvpn remote-address=10.255.255.3
add name=Openvpn-INS profile=Openvpn remote-address=10.255.255.4
/routing ospf network
add area=area255 network=10.255.255.0/24
add area=area255 network=192.168.5.0/24
/system clock
set time-zone-name=America/Chicago
/system identity
set name=FMT-ROUTER
/system ntp client
set enabled=yes primary-ntp=129.6.15.28 secondary-ntp=129.6.15.30
/system package update
set channel=release-candidate
/system routerboard settings
set boot-protocol=dhcp silent-boot=no
/tool mac-server
set allowed-interface-list=mactel
/tool mac-server mac-winbox
set allowed-interface-list=mac-winbox
[admin@FMT-ROUTER] >
/ip ipsec peer printaddress=0.0.0.0/0/ip ipsec peer add address=0.0.0.0/0 dh-group=modp1024 dpd-interval=disable-dpd enc-algorithm=\
aes-256,aes-192,aes-128 exchange-mode=main-l2tp generate-policy=\
port-override hash-algorithm=md5 send-initial-contact=no
/ip ipsec peer print/log print where topics~"ipsec"Nevertheless, the one with IPv6 match pattern "any address" (These are not same peers. The first one is IPv4, the second one is IPv6.
::/0[admin@FMT-ROUTER] > /log print where topics~"ipsec"
14:57:28 ipsec,info ISAKMP-SA established x.x.x.x[4500]-x.x.x.x[4500] sp
i:da3b627eef31d9a3:637c812fece3bf78
14:57:28 ipsec,error no suitable proposal found.
14:57:28 ipsec,error x.x.x.x failed to pre-process ph2 packet.
14:57:31 ipsec,error x.x.x.x peer sent packet for dead phase2
14:57:34 ipsec,error x.x.x.x peer sent packet for dead phase2
14:57:38 ipsec,error x.x.x.x peer sent packet for dead phase2
14:57:41 ipsec,error x.x.x.x peer sent packet for dead phase2
14:57:44 ipsec,error x.x.x.x peer sent packet for dead phase2/system logging add topics=ipsec,debug action=memory/log print where topics~"ipsec"15:16:08 ipsec,debug dh(modp1536)
15:16:08 ipsec,debug transform #7 len=36
15:16:08 ipsec,debug type=Life Type, flag=0x8000, lorv=seconds
15:16:08 ipsec,debug type=Life Duration, flag=0x8000, lorv=3600
15:16:08 ipsec,debug type=Encryption Algorithm, flag=0x8000, lorv=AES-CBC
15:16:08 ipsec,debug encryption(aes)
15:16:08 ipsec,debug type=Key Length, flag=0x8000, lorv=256
15:16:08 ipsec,debug type=Authentication Method, flag=0x8000, lorv=pre-shared key
15:16:08 ipsec,debug type=Hash Algorithm, flag=0x8000, lorv=MD5
15:16:08 ipsec,debug hash(md5)
15:16:08 ipsec,debug type=Group Description, flag=0x8000, lorv=1536-bit MODP group
15:16:08 ipsec,debug dh(modp1536)
15:16:08 ipsec,debug transform #8 len=36
15:16:08 ipsec,debug type=Life Type, flag=0x8000, lorv=seconds
15:16:08 ipsec,debug type=Life Duration, flag=0x8000, lorv=3600
15:16:08 ipsec,debug type=Encryption Algorithm, flag=0x8000, lorv=AES-CBC
15:16:08 ipsec,debug encryption(aes)
15:16:08 ipsec,debug type=Key Length, flag=0x8000, lorv=256
15:16:08 ipsec,debug type=Authentication Method, flag=0x8000, lorv=pre-shared key
15:16:08 ipsec,debug type=Hash Algorithm, flag=0x8000, lorv=4
15:16:08 ipsec,debug hash(sha2_256)
15:16:08 ipsec,debug type=Group Description, flag=0x8000, lorv=1024-bit MODP group
15:16:08 ipsec,debug dh(modp1024)
15:16:08 ipsec,debug transform #9 len=36
15:16:08 ipsec,debug type=Life Type, flag=0x8000, lorv=seconds
15:16:08 ipsec,debug type=Life Duration, flag=0x8000, lorv=3600
15:16:08 ipsec,debug type=Encryption Algorithm, flag=0x8000, lorv=AES-CBC
15:16:08 ipsec,debug encryption(aes)
15:16:08 ipsec,debug type=Key Length, flag=0x8000, lorv=256
15:16:08 ipsec,debug type=Authentication Method, flag=0x8000, lorv=pre-shared key
15:16:08 ipsec,debug type=Hash Algorithm, flag=0x8000, lorv=SHA
15:16:08 ipsec,debug hash(sha1)
15:16:08 ipsec,debug type=Group Description, flag=0x8000, lorv=1024-bit MODP group
15:16:08 ipsec,debug dh(modp1024)
15:16:08 ipsec,debug transform #10 len=36
15:16:08 ipsec,debug type=Life Type, flag=0x8000, lorv=seconds
15:16:08 ipsec,debug type=Life Duration, flag=0x8000, lorv=3600
15:16:08 ipsec,debug type=Encryption Algorithm, flag=0x8000, lorv=AES-CBC
15:16:08 ipsec,debug encryption(aes)
15:16:08 ipsec,debug type=Key Length, flag=0x8000, lorv=256
15:16:08 ipsec,debug type=Authentication Method, flag=0x8000, lorv=pre-shared key
15:16:08 ipsec,debug type=Hash Algorithm, flag=0x8000, lorv=MD5
15:16:08 ipsec,debug hash(md5)
15:16:08 ipsec,debug type=Group Description, flag=0x8000, lorv=1024-bit MODP group
15:16:08 ipsec,debug dh(modp1024)
15:16:08 ipsec,debug transform #11 len=36
15:16:08 ipsec,debug type=Life Type, flag=0x8000, lorv=seconds
15:16:08 ipsec,debug type=Life Duration, flag=0x8000, lorv=3600
15:16:08 ipsec,debug type=Encryption Algorithm, flag=0x8000, lorv=AES-CBC
15:16:08 ipsec,debug encryption(aes)
15:16:08 ipsec,debug type=Key Length, flag=0x8000, lorv=128
15:16:08 ipsec,debug type=Authentication Method, flag=0x8000, lorv=pre-shared key
15:16:08 ipsec,debug type=Hash Algorithm, flag=0x8000, lorv=SHA
15:16:08 ipsec,debug hash(sha1)
15:16:08 ipsec,debug type=Group Description, flag=0x8000, lorv=1024-bit MODP group
15:16:08 ipsec,debug dh(modp1024)
15:16:08 ipsec,debug transform #12 len=36
15:16:08 ipsec,debug type=Life Type, flag=0x8000, lorv=seconds
15:16:08 ipsec,debug type=Life Duration, flag=0x8000, lorv=3600
15:16:08 ipsec,debug type=Encryption Algorithm, flag=0x8000, lorv=AES-CBC
15:16:08 ipsec,debug encryption(aes)
15:16:08 ipsec,debug type=Key Length, flag=0x8000, lorv=128
15:16:08 ipsec,debug type=Authentication Method, flag=0x8000, lorv=pre-shared key
15:16:08 ipsec,debug type=Hash Algorithm, flag=0x8000, lorv=MD5
15:16:08 ipsec,debug hash(md5)
15:16:08 ipsec,debug type=Group Description, flag=0x8000, lorv=1024-bit MODP group
15:16:08 ipsec,debug dh(modp1024)
15:16:08 ipsec,debug transform #13 len=32
15:16:08 ipsec,debug type=Life Type, flag=0x8000, lorv=seconds
15:16:08 ipsec,debug type=Life Duration, flag=0x8000, lorv=3600
15:16:08 ipsec,debug type=Encryption Algorithm, flag=0x8000, lorv=3DES-CBC
15:16:08 ipsec,debug encryption(3des)
15:16:08 ipsec,debug type=Authentication Method, flag=0x8000, lorv=pre-shared key
15:16:08 ipsec,debug type=Hash Algorithm, flag=0x8000, lorv=SHA
15:16:08 ipsec,debug hash(sha1)
15:16:08 ipsec,debug type=Group Description, flag=0x8000, lorv=1024-bit MODP group
15:16:08 ipsec,debug dh(modp1024)
15:16:08 ipsec,debug transform #14 len=32
15:16:08 ipsec,debug type=Life Type, flag=0x8000, lorv=seconds
15:16:08 ipsec,debug type=Life Duration, flag=0x8000, lorv=3600
15:16:08 ipsec,debug type=Encryption Algorithm, flag=0x8000, lorv=3DES-CBC
15:16:08 ipsec,debug encryption(3des)
15:16:08 ipsec,debug type=Authentication Method, flag=0x8000, lorv=pre-shared key
15:16:08 ipsec,debug type=Hash Algorithm, flag=0x8000, lorv=MD5
15:16:08 ipsec,debug hash(md5)
15:16:08 ipsec,debug type=Group Description, flag=0x8000, lorv=1024-bit MODP group
15:16:08 ipsec,debug dh(modp1024)
15:16:08 ipsec,debug pair 1:
15:16:08 ipsec,debug 0x73c90: next=(nil) tnext=0x739e8
15:16:08 ipsec,debug 0x739e8: next=(nil) tnext=0x76720
15:16:08 ipsec,debug 0x76720: next=(nil) tnext=0x78230
15:16:08 ipsec,debug 0x78230: next=(nil) tnext=0x78248
15:16:08 ipsec,debug 0x78248: next=(nil) tnext=0x785e8
15:16:08 ipsec,debug 0x785e8: next=(nil) tnext=0x78600
15:16:08 ipsec,debug 0x78600: next=(nil) tnext=0x799c8
15:16:08 ipsec,debug 0x799c8: next=(nil) tnext=0x799e0
15:16:08 ipsec,debug 0x799e0: next=(nil) tnext=0x780f8
15:16:08 ipsec,debug 0x780f8: next=(nil) tnext=0x78110
15:16:08 ipsec,debug 0x78110: next=(nil) tnext=0x79758
15:16:08 ipsec,debug 0x79758: next=(nil) tnext=0x79770
15:16:08 ipsec,debug 0x79770: next=(nil) tnext=0x73c30
15:16:08 ipsec,debug 0x73c30: next=(nil) tnext=(nil)
15:16:08 ipsec,debug proposal #1: 14 transform
15:16:08 ipsec,debug prop#=1, prot-id=ISAKMP, spi-size=0, #trns=14
15:16:08 ipsec,debug trns#=1, trns-id=IKE
15:16:08 ipsec,debug type=Life Type, flag=0x8000, lorv=seconds
15:16:08 ipsec,debug type=Life Duration, flag=0x8000, lorv=3600
15:16:08 ipsec,debug type=Encryption Algorithm, flag=0x8000, lorv=AES-CBC
15:16:08 ipsec,debug type=Key Length, flag=0x8000, lorv=256
15:16:08 ipsec,debug type=Authentication Method, flag=0x8000, lorv=pre-shared key
15:16:08 ipsec,debug type=Hash Algorithm, flag=0x8000, lorv=4
15:16:08 ipsec,debug type=Group Description, flag=0x8000, lorv=2048-bit MODP group
15:16:08 ipsec,debug Compared: Local:Peer
15:16:08 ipsec,debug (lifetime = 86400:3600)
15:16:08 ipsec,debug (lifebyte = 0:0)
15:16:08 ipsec,debug enctype = AES-CBC:AES-CBC
15:16:08 ipsec,debug (encklen = 256:256)
15:16:08 ipsec,debug hashtype = SHA:4
15:16:08 ipsec,debug authmethod = pre-shared key:pre-shared key
15:16:08 ipsec,debug dh_group = 2048-bit MODP group:2048-bit MODP group
15:16:08 ipsec,debug Compared: Local:Peer
15:16:08 ipsec,debug (lifetime = 86400:3600)
15:16:08 ipsec,debug (lifebyte = 0:0)
15:16:08 ipsec,debug enctype = AES-CBC:AES-CBC
15:16:08 ipsec,debug (encklen = 256:256)
15:16:08 ipsec,debug hashtype = SHA:4
15:16:08 ipsec,debug authmethod = pre-shared key:pre-shared key
15:16:08 ipsec,debug dh_group = 1024-bit MODP group:2048-bit MODP group
15:16:08 ipsec,debug Compared: Local:Peer
15:16:08 ipsec,debug (lifetime = 86400:3600)
15:16:08 ipsec,debug (lifebyte = 0:0)
15:16:08 ipsec,debug enctype = AES-CBC:AES-CBC
15:16:08 ipsec,debug (encklen = 192:256)
15:16:08 ipsec,debug hashtype = SHA:4
15:16:08 ipsec,debug authmethod = pre-shared key:pre-shared key
15:16:08 ipsec,debug dh_group = 2048-bit MODP group:2048-bit MODP group
15:16:08 ipsec,debug Compared: Local:Peer
15:16:08 ipsec,debug (lifetime = 86400:3600)
15:16:08 ipsec,debug (lifebyte = 0:0)
15:16:08 ipsec,debug enctype = AES-CBC:AES-CBC
15:16:08 ipsec,debug (encklen = 192:256)
15:16:08 ipsec,debug hashtype = SHA:4
15:16:08 ipsec,debug authmethod = pre-shared key:pre-shared key
15:16:08 ipsec,debug dh_group = 1024-bit MODP group:2048-bit MODP group
15:16:08 ipsec,debug Compared: Local:Peer
15:16:08 ipsec,debug (lifetime = 86400:3600)
15:16:08 ipsec,debug (lifebyte = 0:0)
15:16:08 ipsec,debug enctype = AES-CBC:AES-CBC
15:16:08 ipsec,debug (encklen = 128:256)
15:16:08 ipsec,debug hashtype = SHA:4
15:16:08 ipsec,debug authmethod = pre-shared key:pre-shared key
15:16:08 ipsec,debug dh_group = 2048-bit MODP group:2048-bit MODP group
15:16:08 ipsec,debug Compared: Local:Peer
15:16:08 ipsec,debug (lifetime = 86400:3600)
15:16:08 ipsec,debug (lifebyte = 0:0)
15:16:08 ipsec,debug enctype = AES-CBC:AES-CBC
15:16:08 ipsec,debug (encklen = 128:256)
15:16:08 ipsec,debug hashtype = SHA:4
15:16:08 ipsec,debug authmethod = pre-shared key:pre-shared key
15:16:08 ipsec,debug dh_group = 1024-bit MODP group:2048-bit MODP group
15:16:08 ipsec,debug Compared: Local:Peer
15:16:08 ipsec,debug (lifetime = 86400:3600)
15:16:08 ipsec,debug (lifebyte = 0:0)
15:16:08 ipsec,debug enctype = 3DES-CBC:AES-CBC
15:16:08 ipsec,debug (encklen = 0:256)
15:16:08 ipsec,debug hashtype = SHA:4
15:16:08 ipsec,debug authmethod = pre-shared key:pre-shared key
15:16:08 ipsec,debug dh_group = 2048-bit MODP group:2048-bit MODP group
15:16:08 ipsec,debug Compared: Local:Peer
15:16:08 ipsec,debug (lifetime = 86400:3600)
15:16:08 ipsec,debug (lifebyte = 0:0)
15:16:08 ipsec,debug enctype = 3DES-CBC:AES-CBC
15:16:08 ipsec,debug (encklen = 0:256)
15:16:08 ipsec,debug hashtype = SHA:4
15:16:08 ipsec,debug authmethod = pre-shared key:pre-shared key
15:16:08 ipsec,debug dh_group = 1024-bit MODP group:2048-bit MODP group
15:16:08 ipsec,debug prop#=1, prot-id=ISAKMP, spi-size=0, #trns=14
15:16:08 ipsec,debug trns#=2, trns-id=IKE
15:16:08 ipsec,debug type=Life Type, flag=0x8000, lorv=seconds
15:16:08 ipsec,debug type=Life Duration, flag=0x8000, lorv=3600
15:16:08 ipsec,debug type=Encryption Algorithm, flag=0x8000, lorv=AES-CBC
15:16:08 ipsec,debug type=Key Length, flag=0x8000, lorv=256
15:16:08 ipsec,debug type=Authentication Method, flag=0x8000, lorv=pre-shared key
15:16:08 ipsec,debug type=Hash Algorithm, flag=0x8000, lorv=SHA
15:16:08 ipsec,debug type=Group Description, flag=0x8000, lorv=2048-bit MODP group
15:16:08 ipsec,debug Compared: Local:Peer
15:16:08 ipsec,debug (lifetime = 86400:3600)
15:16:08 ipsec,debug (lifebyte = 0:0)
15:16:08 ipsec,debug enctype = AES-CBC:AES-CBC
15:16:08 ipsec,debug (encklen = 256:256)
15:16:08 ipsec,debug hashtype = SHA:SHA
15:16:08 ipsec,debug authmethod = pre-shared key:pre-shared key
15:16:08 ipsec,debug dh_group = 2048-bit MODP group:2048-bit MODP group
15:16:08 ipsec,debug an acceptable proposal found.
15:16:08 ipsec,debug dh(modp2048)
15:16:08 ipsec,debug agreed on pre-shared key auth.
15:16:08 ipsec,debug ===
15:16:08 ipsec,debug new cookie:
15:16:08 ipsec,debug 318768342374a315\18
15:16:08 ipsec,debug add payload of len 52, next type 13
15:16:08 ipsec,debug add payload of len 16, next type 13
15:16:08 ipsec,debug add payload of len 16, next type 13
15:16:08 ipsec,debug add payload of len 20, next type 0
15:16:08 ipsec,debug 148 bytes from x.x.x.x[500] to x.x.x.x[500]
15:16:08 ipsec,debug 1 times of 148 bytes message will be sent to x.x.x.x[500
]
15:16:08 ipsec,debug,packet 0ca0ebeb 85ce3373 31876834 2374a315 01100200 00000000
00000094 0d000038
15:16:08 ipsec,debug,packet 00000001 00000001 0000002c 01010001 00000024 02010000
800b0001 800c0e10
15:16:08 ipsec,debug,packet 80010007 800e0100 80030001 80020002 8004000e 0d000014
4a131c81 07035845
15:16:08 ipsec,debug,packet 5c5728f2 0e95452f 0d000014 afcad713 68a1f1c9 6b8696fc
77570100 00000018
15:16:08 ipsec,debug,packet 4048b7d5 6ebce885 25e7de7f 00d6c2d3 80000000
15:16:08 ipsec,debug ===== received 356 bytes from x.x.x.x[500] to 74.82.59.1
30[500]
15:16:08 ipsec,debug,packet 0ca0ebeb 85ce3373 31876834 2374a315 04100200 00000000
00000164 0a000104
15:16:08 ipsec,debug,packet 7ea81187 181ea2f6 0c11db9a 0e4a9789 faa3f814 98867252
2d7dc164 484729c3
15:16:08 ipsec,debug,packet 4c512aed 2997821c 01e6fe7e 5849f62f 89fd8196 613673ae
c9a75462 32161992
15:16:08 ipsec,debug,packet 48a10fd1 182310a0 e1941e7a e913c13a 614f593a ecc7a4f9
6b483707 cd3feb4c
15:16:08 ipsec,debug,packet 8096269e 843ce5db 1801565a 4be3088b d30d6dd9 fc810906
7971486d 1487b400
15:16:08 ipsec,debug,packet a8a56e2c 7dfb999f 2fdfa314 e942461a deb9f037 3ee5064d
4d197ab7 4ff9b99d
15:16:08 ipsec,debug,packet a540068f dc446ebf 2a7bb729 e73337ef 9622e1e8 52b978bc
26435db6 13e3a4f9
15:16:08 ipsec,debug,packet 57ba9edf afd6ec22 9c3d8d5d d7b8a009 697317dd 0207c5ba
eb41c11e 5f9fe5a9
15:16:08 ipsec,debug,packet b543eef9 2667e041 a68f5bd5 dfc1f7b8 321087d6 ae3037a8
8b1948dd e2ab1e8d
15:16:08 ipsec,debug,packet 14000014 7527c45c d950e1b1 17c61a60 0edc5dcf 14000018
53ebca61 b5d9a377
15:16:08 ipsec,debug,packet d2d90069 890f2edb 7fd13b20 00000018 78de24e0 e0937b58
e803510c a0ec39bd
15:16:08 ipsec,debug,packet a89dced4
15:16:08 ipsec,debug begin.
15:16:08 ipsec,debug seen nptype=4(ke) len=260
15:16:08 ipsec,debug seen nptype=10(nonce) len=20
15:16:08 ipsec,debug seen nptype=20(nat-d) len=24
15:16:08 ipsec,debug seen nptype=20(nat-d) len=24
15:16:08 ipsec,debug succeed.
15:16:08 ipsec,debug hash(sha1)
15:16:08 ipsec,debug hash(sha1)
15:16:08 ipsec,debug ===
15:16:08 ipsec,debug dh(modp2048)
15:16:08 ipsec,debug compute DH's private.
15:16:08 ipsec,debug 654474fc 196e98ae 37609641 9aa6e6ea 34ec46fb dbb972dc 331b5fe
8 56529083
15:16:08 ipsec,debug 5d5f72c0 df75c4b5 2e4af609 4ef90d23 7b79af6b 61f38fa0 4ec47af
2 aa39a206
15:16:08 ipsec,debug 9627a948 efede9b0 4b84e35a fa569fac 1063722f 93a6cf18 e421812
1 8427f78d
15:16:08 ipsec,debug c5ee682d 4bdb30a7 4bf680f3 82c53db1 790f7a17 ff64f41e 932ab1a
b 8f6486bb
15:16:08 ipsec,debug 688d523e bb89024d c20f495b 19f35492 e4d7a846 509a48ec bf39f36
6 7114ff74
15:16:08 ipsec,debug 0e9f1380 cfc107b2 211189be e71d10be 9d979eab 5128dbeb 63a86f9
b 64dc7c3f
15:16:08 ipsec,debug d570dc51 767eb630 425e42db 3cb0ba09 a9439cac 256f740f bf24076
5 05611d1d
15:16:08 ipsec,debug e1fa1a1d 5a472849 5fc26201 4bfed45b 0046b333 4e3bda6f dec510c
6 e5e47a73
15:16:08 ipsec,debug compute DH's public.
15:16:08 ipsec,debug 43b6770c bbd18b18 bbfdb8c9 180f76b1 6532600f 0ae47c60 0630550
8 6f829d27
15:16:08 ipsec,debug 8df0b8e7 edeb4270 9525c1f6 d05f3792 415dd8e9 41360acc 8dd57db
c 30a6d0de
15:16:08 ipsec,debug 1e42e21d ce91c539 1b28cb4a 033a64fb 8a751543 730648fd da10a3f
b 7cd6fb76
15:16:08 ipsec,debug eec773a3 058091d4 2681e458 8d3db6b8 4927ed48 b825728e f69521d
4 ab544c0a
15:16:08 ipsec,debug cf6cf047 3726b36c 56df86e4 de5a6568 4ee9ee73 5a81f592 1f64fef
c 9be88086
15:16:08 ipsec,debug eb426033 4fd446b8 cdc121e1 0e170522 1345ada1 87792d56 66b4d63
f c863f3d7
15:16:08 ipsec,debug ae7d9740 f64a722f 4e1227bb 8b46045b 36cf8de9 ca8cbcf1 befdb60
4 48da7146
15:16:08 ipsec,debug 6891fdbe 7760883d fb5d1671 5772b8fc 5e81fb12 251406f3 d70016c
3 3d4eb04f
15:16:08 ipsec,debug hash(sha1)
15:16:08 ipsec,debug hash(sha1)
15:16:08 ipsec,debug add payload of len 256, next type 10
15:16:08 ipsec,debug add payload of len 24, next type 20
15:16:08 ipsec,debug add payload of len 20, next type 20
15:16:08 ipsec,debug add payload of len 20, next type 0
15:16:08 ipsec,debug 364 bytes from x.x.x.x[500] to x.x.x.x[500]
15:16:08 ipsec,debug 1 times of 364 bytes message will be sent to x.x.x.x[500
]
15:16:08 ipsec,debug,packet 0ca0ebeb 85ce3373 31876834 2374a315 04100200 00000000
0000016c 0a000104
15:16:08 ipsec,debug,packet 43b6770c bbd18b18 bbfdb8c9 180f76b1 6532600f 0ae47c60
06305508 6f829d27
15:16:08 ipsec,debug,packet 8df0b8e7 edeb4270 9525c1f6 d05f3792 415dd8e9 41360acc
8dd57dbc 30a6d0de
15:16:08 ipsec,debug,packet 1e42e21d ce91c539 1b28cb4a 033a64fb 8a751543 730648fd
da10a3fb 7cd6fb76
15:16:08 ipsec,debug,packet eec773a3 058091d4 2681e458 8d3db6b8 4927ed48 b825728e
f69521d4 ab544c0a
15:16:08 ipsec,debug,packet cf6cf047 3726b36c 56df86e4 de5a6568 4ee9ee73 5a81f592
1f64fefc 9be88086
15:16:08 ipsec,debug,packet eb426033 4fd446b8 cdc121e1 0e170522 1345ada1 87792d56
66b4d63f c863f3d7
15:16:08 ipsec,debug,packet ae7d9740 f64a722f 4e1227bb 8b46045b 36cf8de9 ca8cbcf1
befdb604 48da7146
15:16:08 ipsec,debug,packet 6891fdbe 7760883d fb5d1671 5772b8fc 5e81fb12 251406f3
d70016c3 3d4eb04f
15:16:08 ipsec,debug,packet 1400001c bd5d47a4 f8f47c6f c08a2d54 5316ab4d ae53c0af
a28116b5 14000018
15:16:08 ipsec,debug,packet c014d3c4 dd4ee791 d6e7a4e1 90db771a 501204b2 00000018
53ebca61 b5d9a377
15:16:08 ipsec,debug,packet d2d90069 890f2edb 7fd13b20
15:16:08 ipsec,debug dh(modp2048)
15:16:08 ipsec,debug compute DH's shared.
15:16:08 ipsec,debug
15:16:08 ipsec,debug cba9eb18 ec05392e ef5a44a8 f716dae1 dcc377bb 0eef518d 8a78590
8 e62c7ecc
15:16:08 ipsec,debug 24176a69 4a45a390 d2634f74 29f34c04 73a93125 5f422cd1 eed0e70
c 30af2f14
15:16:08 ipsec,debug 8e20e91b 92694546 fc00eba2 9470ade5 7151d35e c2f229a2 eb263be
a 8928f751
15:16:08 ipsec,debug 222390ad 12dcf09b c426ce13 effad9b6 65a500ad 085a8c6f 606464b
5 17bd00e8
15:16:08 ipsec,debug 359b4581 da7032df cf799ac2 bcc5b94c 2a71ad8c e45ccb40 9369d15
d 296b7241
15:16:08 ipsec,debug 29c3a36e 1007b332 b3d35a4c 27e538a5 e6888ed5 c43a2dcd b0aa810
9 652e0b15
15:16:08 ipsec,debug 881a7ae5 b69a303b c26d9120 4d4457dc 9d64ea6f 3cf57a87 f34a58c
6 c38fe7b9
15:16:08 ipsec,debug 8a62f2f0 28b48244 5f0ab100 aeeaed1a 2e4a6872 cf260aa3 b73565c
5 93b3d289
15:16:08 ipsec,debug nonce 1:
15:16:08 ipsec,debug 7527c45c d950e1b1 17c61a60 0edc5dcf
15:16:08 ipsec,debug nonce 2:
15:16:08 ipsec,debug bd5d47a4 f8f47c6f c08a2d54 5316ab4d ae53c0af a28116b5
15:16:08 ipsec,debug hmac(hmac_sha1)
15:16:08 ipsec,debug SKEYID computed:
15:16:08 ipsec,debug fd0fca52 5b178899 d9bf0607 10dad655 cd348e80
15:16:08 ipsec,debug hmac(hmac_sha1)
15:16:08 ipsec,debug SKEYID_d computed:
15:16:08 ipsec,debug 863b66b5 0922f998 67c6044c 9956af7c 13ca190b
15:16:08 ipsec,debug hmac(hmac_sha1)
15:16:08 ipsec,debug SKEYID_a computed:
15:16:08 ipsec,debug 12004620 49b7bff0 530a6a9c b35a76cb b0101b0e
15:16:08 ipsec,debug hmac(hmac_sha1)
15:16:08 ipsec,debug SKEYID_e computed:
15:16:08 ipsec,debug 40c9541f 3b2cb84e aaa1e566 9971d7d4 7c961240
15:16:08 ipsec,debug encryption(aes)
15:16:08 ipsec,debug hash(sha1)
15:16:08 ipsec,debug len(SKEYID_e) < len(Ka) (20 < 32), generating long key (Ka =
K1 | K2 | ...)
15:16:08 ipsec,debug hmac(hmac_sha1)
15:16:08 ipsec,debug compute intermediate encryption key K1
15:16:08 ipsec,debug 00
15:16:08 ipsec,debug b1d7c185 aca220ff 96a3fc61 31155926 33cce459
15:16:08 ipsec,debug hmac(hmac_sha1)
15:16:08 ipsec,debug compute intermediate encryption key K2
15:16:08 ipsec,debug b1d7c185 aca220ff 96a3fc61 31155926 33cce459
15:16:08 ipsec,debug 861802b4 24e99c2c 458d70b6 8a032b08 fd54b43f
15:16:08 ipsec,debug final encryption key computed:
15:16:08 ipsec,debug b1d7c185 aca220ff 96a3fc61 31155926 33cce459 861802b4 24e99c2
c 458d70b6
15:16:08 ipsec,debug hash(sha1)
15:16:08 ipsec,debug encryption(aes)
15:16:08 ipsec,debug IV computed:
15:16:08 ipsec,debug 49363604 3be53d06 27cd624d 758a3e39
15:16:09 ipsec,debug ===== received 108 bytes from x.x.x.x[4500] to 74.82.59.
130[4500]
15:16:09 ipsec,debug,packet 0ca0ebeb 85ce3373 31876834 2374a315 05100201 00000000
0000006c 3e590629
15:16:09 ipsec,debug,packet 78dde780 66be6469 0fcad983 f9ddd7a4 78ce27f7 c2f6a00f
bb9c7350 5bc9fff1
15:16:09 ipsec,debug,packet 763838c2 26744d8b 491b6435 ccf20769 32c2a3bd 78a3fd02
e4204474 cf5234ef
15:16:09 ipsec,debug,packet 9ea94814 91c3f22a 33980c41
15:16:09 ipsec,debug encryption(aes)
15:16:09 ipsec,debug IV was saved for next processing:
15:16:09 ipsec,debug cf5234ef 9ea94814 91c3f22a 33980c41
15:16:09 ipsec,debug encryption(aes)
15:16:09 ipsec,debug with key:
15:16:09 ipsec,debug b1d7c185 aca220ff 96a3fc61 31155926 33cce459 861802b4 24e99c2
c 458d70b6
15:16:09 ipsec,debug decrypted payload by IV:
15:16:09 ipsec,debug 49363604 3be53d06 27cd624d 758a3e39
15:16:09 ipsec,debug decrypted payload, but not trimed.
15:16:09 ipsec,debug 0800000c 011101f4 c0a80527 0b000018 aad36bd9 32b64632 98cb8b3
4 662952c8
15:16:09 ipsec,debug e542cef4 0000001c 00000001 01106002 0ca0ebeb 85ce3373 3187683
4 2374a315
15:16:09 ipsec,debug 00000000 00000000 00000000 00000010
15:16:09 ipsec,debug padding len=17
15:16:09 ipsec,debug skip to trim padding.
15:16:09 ipsec,debug decrypted.
15:16:09 ipsec,debug 0ca0ebeb 85ce3373 31876834 2374a315 05100201 00000000 0000006
c 0800000c
15:16:09 ipsec,debug 011101f4 c0a80527 0b000018 aad36bd9 32b64632 98cb8b34 662952c
8 e542cef4
15:16:09 ipsec,debug 0000001c 00000001 01106002 0ca0ebeb 85ce3373 31876834 2374a31
5 00000000
15:16:09 ipsec,debug 00000000 00000000 00000010
15:16:09 ipsec,debug begin.
15:16:09 ipsec,debug seen nptype=5(id) len=12
15:16:09 ipsec,debug seen nptype=8(hash) len=24
15:16:09 ipsec,debug seen nptype=11(notify) len=28
15:16:09 ipsec,debug succeed.
15:16:09 ipsec,debug x.x.x.x Notify Message received
15:16:09 ipsec,debug HASH received:
15:16:09 ipsec,debug aad36bd9 32b64632 98cb8b34 662952c8 e542cef4
15:16:09 ipsec,debug HASH with:
15:16:09 ipsec,debug 7ea81187 181ea2f6 0c11db9a 0e4a9789 faa3f814 98867252 2d7dc16
4 484729c3
15:16:09 ipsec,debug 4c512aed 2997821c 01e6fe7e 5849f62f 89fd8196 613673ae c9a7546
2 32161992
15:16:09 ipsec,debug 48a10fd1 182310a0 e1941e7a e913c13a 614f593a ecc7a4f9 6b48370
7 cd3feb4c
15:16:09 ipsec,debug 8096269e 843ce5db 1801565a 4be3088b d30d6dd9 fc810906 7971486
d 1487b400
15:16:09 ipsec,debug a8a56e2c 7dfb999f 2fdfa314 e942461a deb9f037 3ee5064d 4d197ab
7 4ff9b99d
15:16:09 ipsec,debug a540068f dc446ebf 2a7bb729 e73337ef 9622e1e8 52b978bc 26435db
6 13e3a4f9
15:16:09 ipsec,debug 57ba9edf afd6ec22 9c3d8d5d d7b8a009 697317dd 0207c5ba eb41c11
e 5f9fe5a9
15:16:09 ipsec,debug b543eef9 2667e041 a68f5bd5 dfc1f7b8 321087d6 ae3037a8 8b1948d
d e2ab1e8d
15:16:09 ipsec,debug 43b6770c bbd18b18 bbfdb8c9 180f76b1 6532600f 0ae47c60 0630550
8 6f829d27
15:16:09 ipsec,debug 8df0b8e7 edeb4270 9525c1f6 d05f3792 415dd8e9 41360acc 8dd57db
c 30a6d0de
15:16:09 ipsec,debug 1e42e21d ce91c539 1b28cb4a 033a64fb 8a751543 730648fd da10a3f
b 7cd6fb76
15:16:09 ipsec,debug eec773a3 058091d4 2681e458 8d3db6b8 4927ed48 b825728e f69521d
4 ab544c0a
15:16:09 ipsec,debug cf6cf047 3726b36c 56df86e4 de5a6568 4ee9ee73 5a81f592 1f64fef
c 9be88086
15:16:09 ipsec,debug eb426033 4fd446b8 cdc121e1 0e170522 1345ada1 87792d56 66b4d63
f c863f3d7
15:16:09 ipsec,debug ae7d9740 f64a722f 4e1227bb 8b46045b 36cf8de9 ca8cbcf1 befdb60
4 48da7146
15:16:09 ipsec,debug 6891fdbe 7760883d fb5d1671 5772b8fc 5e81fb12 251406f3 d70016c
3 3d4eb04f
15:16:09 ipsec,debug 0ca0ebeb 85ce3373 31876834 2374a315 00000001 00000001 000001f
8 0101000e
15:16:09 ipsec,debug 03000024 01010000 800b0001 800c0e10 80010007 800e0100 8003000
1 80020004
15:16:09 ipsec,debug 8004000e 03000024 02010000 800b0001 800c0e10 80010007 800e010
0 80030001
15:16:09 ipsec,debug 80020002 8004000e 03000024 03010000 800b0001 800c0e10 8001000
7 800e0100
15:16:09 ipsec,debug 80030001 80020001 8004000e 03000024 04010000 800b0001 800c0e1
0 80010007
15:16:09 ipsec,debug 800e0100 80030001 80020006 8004000e 03000024 05010000 800b000
1 800c0e10
15:16:09 ipsec,debug 80010007 800e0100 80030001 80020004 80040005 03000024 0601000
0 800b0001
15:16:09 ipsec,debug 800c0e10 80010007 800e0100 80030001 80020002 80040005 0300002
4 07010000
15:16:09 ipsec,debug 800b0001 800c0e10 80010007 800e0100 80030001 80020001 8004000
5 03000024
15:16:09 ipsec,debug 08010000 800b0001 800c0e10 80010007 800e0100 80030001 8002000
4 80040002
15:16:09 ipsec,debug 03000024 09010000 800b0001 800c0e10 80010007 800e0100 8003000
1 80020002
15:16:09 ipsec,debug 80040002 03000024 0a010000 800b0001 800c0e10 80010007 800e010
0 80030001
15:16:09 ipsec,debug 80020001 80040002 03000024 0b010000 800b0001 800c0e10 8001000
7 800e0080
15:16:09 ipsec,debug 80030001 80020002 80040002 03000024 0c010000 800b0001 800c0e1
0 80010007
15:16:09 ipsec,debug 800e0080 80030001 80020001 80040002 03000020 0d010000 800b000
1 800c0e10
15:16:09 ipsec,debug 80010005 80030001 80020002 80040002 00000020 0e010000 800b000
1 800c0e10
15:16:09 ipsec,debug 80010005 80030001 80020001 80040002 011101f4 c0a80527
15:16:09 ipsec,debug hmac(hmac_sha1)
15:16:09 ipsec,debug HASH computed:
15:16:09 ipsec,debug aad36bd9 32b64632 98cb8b34 662952c8 e542cef4
15:16:09 ipsec,debug HASH for PSK validated.
15:16:09 ipsec,debug x.x.x.x peer's ID
15:16:09 ipsec,debug 011101f4 c0a80527
15:16:09 ipsec,debug ===
15:16:09 ipsec,debug use ID type of IPv4_address
15:16:09 ipsec,debug generate HASH_R
15:16:09 ipsec,debug HASH with:
15:16:09 ipsec,debug 43b6770c bbd18b18 bbfdb8c9 180f76b1 6532600f 0ae47c60 0630550
8 6f829d27
15:16:09 ipsec,debug 8df0b8e7 edeb4270 9525c1f6 d05f3792 415dd8e9 41360acc 8dd57db
c 30a6d0de
15:16:09 ipsec,debug 1e42e21d ce91c539 1b28cb4a 033a64fb 8a751543 730648fd da10a3f
b 7cd6fb76
15:16:09 ipsec,debug eec773a3 058091d4 2681e458 8d3db6b8 4927ed48 b825728e f69521d
4 ab544c0a
15:16:09 ipsec,debug cf6cf047 3726b36c 56df86e4 de5a6568 4ee9ee73 5a81f592 1f64fef
c 9be88086
15:16:09 ipsec,debug eb426033 4fd446b8 cdc121e1 0e170522 1345ada1 87792d56 66b4d63
f c863f3d7
15:16:09 ipsec,debug ae7d9740 f64a722f 4e1227bb 8b46045b 36cf8de9 ca8cbcf1 befdb60
4 48da7146
15:16:09 ipsec,debug 6891fdbe 7760883d fb5d1671 5772b8fc 5e81fb12 251406f3 d70016c
3 3d4eb04f
15:16:09 ipsec,debug 7ea81187 181ea2f6 0c11db9a 0e4a9789 faa3f814 98867252 2d7dc16
4 484729c3
15:16:09 ipsec,debug 4c512aed 2997821c 01e6fe7e 5849f62f 89fd8196 613673ae c9a7546
2 32161992
15:16:09 ipsec,debug 48a10fd1 182310a0 e1941e7a e913c13a 614f593a ecc7a4f9 6b48370
7 cd3feb4c
15:16:09 ipsec,debug 8096269e 843ce5db 1801565a 4be3088b d30d6dd9 fc810906 7971486
d 1487b400
15:16:09 ipsec,debug a8a56e2c 7dfb999f 2fdfa314 e942461a deb9f037 3ee5064d 4d197ab
7 4ff9b99d
15:16:09 ipsec,debug a540068f dc446ebf 2a7bb729 e73337ef 9622e1e8 52b978bc 26435db
6 13e3a4f9
15:16:09 ipsec,debug 57ba9edf afd6ec22 9c3d8d5d d7b8a009 697317dd 0207c5ba eb41c11
e 5f9fe5a9
15:16:09 ipsec,debug b543eef9 2667e041 a68f5bd5 dfc1f7b8 321087d6 ae3037a8 8b1948d
d e2ab1e8d
15:16:09 ipsec,debug 31876834 2374a315 0ca0ebeb 85ce3373 00000001 00000001 000001f
8 0101000e
15:16:09 ipsec,debug 03000024 01010000 800b0001 800c0e10 80010007 800e0100 8003000
1 80020004
15:16:09 ipsec,debug 8004000e 03000024 02010000 800b0001 800c0e10 80010007 800e010
0 80030001
15:16:09 ipsec,debug 80020002 8004000e 03000024 03010000 800b0001 800c0e10 8001000
7 800e0100
15:16:09 ipsec,debug 80030001 80020001 8004000e 03000024 04010000 800b0001 800c0e1
0 80010007
15:16:09 ipsec,debug 800e0100 80030001 80020006 8004000e 03000024 05010000 800b000
1 800c0e10
15:16:09 ipsec,debug 80010007 800e0100 80030001 80020004 80040005 03000024 0601000
0 800b0001
15:16:09 ipsec,debug 800c0e10 80010007 800e0100 80030001 80020002 80040005 0300002
4 07010000
15:16:09 ipsec,debug 800b0001 800c0e10 80010007 800e0100 80030001 80020001 8004000
5 03000024
15:16:09 ipsec,debug 08010000 800b0001 800c0e10 80010007 800e0100 80030001 8002000
4 80040002
15:16:09 ipsec,debug 03000024 09010000 800b0001 800c0e10 80010007 800e0100 8003000
1 80020002
15:16:09 ipsec,debug 80040002 03000024 0a010000 800b0001 800c0e10 80010007 800e010
0 80030001
15:16:09 ipsec,debug 80020001 80040002 03000024 0b010000 800b0001 800c0e10 8001000
7 800e0080
15:16:09 ipsec,debug 80030001 80020002 80040002 03000024 0c010000 800b0001 800c0e1
0 80010007
15:16:09 ipsec,debug 800e0080 80030001 80020001 80040002 03000020 0d010000 800b000
1 800c0e10
15:16:09 ipsec,debug 80010005 80030001 80020002 80040002 00000020 0e010000 800b000
1 800c0e10
15:16:09 ipsec,debug 80010005 80030001 80020001 80040002 011101f4 4a523b82
15:16:09 ipsec,debug hmac(hmac_sha1)
15:16:09 ipsec,debug HASH computed:
15:16:09 ipsec,debug d2f4de27 5f0a8d77 eb3d8a52 a1e76a08 c8aab7cb
15:16:09 ipsec,debug add payload of len 8, next type 8
15:16:09 ipsec,debug add payload of len 20, next type 0
15:16:09 ipsec,debug begin encryption.
15:16:09 ipsec,debug encryption(aes)
15:16:09 ipsec,debug pad length = 12
15:16:09 ipsec,debug 0800000c 011101f4 4a523b82 00000018 d2f4de27 5f0a8d77 eb3d8a5
2 a1e76a08
15:16:09 ipsec,debug c8aab7cb b0b0a29c fbe98089 ec95de0b
15:16:09 ipsec,debug encryption(aes)
15:16:09 ipsec,debug with key:
15:16:09 ipsec,debug b1d7c185 aca220ff 96a3fc61 31155926 33cce459 861802b4 24e99c2
c 458d70b6
15:16:09 ipsec,debug encrypted payload by IV:
15:16:09 ipsec,debug cf5234ef 9ea94814 91c3f22a 33980c41
15:16:09 ipsec,debug save IV for next:
15:16:09 ipsec,debug bc0dbf76 f15e2a27 cc6e4816 46d4da83
15:16:09 ipsec,debug encrypted.
15:16:09 ipsec,debug 76 bytes from x.x.x.x[4500] to x.x.x.x[4500]
15:16:09 ipsec,debug 1 times of 80 bytes message will be sent to x.x.x.x[4500
]
15:16:09 ipsec,debug,packet 0ca0ebeb 85ce3373 31876834 2374a315 05100201 00000000
0000004c 53806344
15:16:09 ipsec,debug,packet 15d0a5bd ac66c4e5 07790182 05383ecc 5f783175 cbe2db20
98ba561d bc0dbf76
15:16:09 ipsec,debug,packet f15e2a27 cc6e4816 46d4da83
15:16:09 ipsec,info ISAKMP-SA established x.x.x.x[4500]-x.x.x.x[4500] sp
i:0ca0ebeb85ce3373:318768342374a315
15:16:09 ipsec,debug ===
15:16:09 ipsec,debug ===== received 316 bytes from x.x.x.x[4500] to 74.82.59.
130[4500]
15:16:09 ipsec,debug,packet 0ca0ebeb 85ce3373 31876834 2374a315 08102001 9db55d38
0000013c 41118418
15:16:09 ipsec,debug,packet 64aed3df 721bb55e 9359905d 82d939a8 d9972f19 e01d2d25
b24c670c 510c746e
15:16:09 ipsec,debug,packet af9c9f41 4407b600 f39f2539 163279b9 6ad2130d 765c1f3b
af913ef4 c1f397f6
15:16:09 ipsec,debug,packet 7584524e 3cd4ce60 33a4e038 c54b343d d54ae1fb 666e5fb1
346f6f87 4adf9351
15:16:09 ipsec,debug,packet 96dac517 3d72cf0e beb8346d 690c9735 ee29d3ee d4b067e0
bdd8838b 9573150d
15:16:09 ipsec,debug,packet 54620d73 872861c4 98e15e8e 3c6d1144 7d7758c4 35b3fc81
a49d0aee f89aa7ba
15:16:09 ipsec,debug,packet d9915d1e 01700709 a2a5197f a5301dca 1669d9a3 e0f34882
569900a7 a53b6004
15:16:09 ipsec,debug,packet f2e14dd3 1f1211c0 1ac0c3b3 00af3220 9981ca6e f7c38662
530c487e 62f25637
15:16:09 ipsec,debug,packet 04dafd29 4eceb4f7 ce96259e 26eb9893 f633e93f 5cc4ca88
f59daccb 0ae0e17c
15:16:09 ipsec,debug,packet 28ca3552 ec8ffedc 60aa393d b1fbe1b7 4893cea9 19c1071f
1c36e19b
15:16:09 ipsec,debug compute IV for phase2
15:16:09 ipsec,debug phase1 last IV:
15:16:09 ipsec,debug bc0dbf76 f15e2a27 cc6e4816 46d4da83 9db55d38
15:16:09 ipsec,debug hash(sha1)
15:16:09 ipsec,debug encryption(aes)
15:16:09 ipsec,debug phase2 IV computed:
15:16:09 ipsec,debug a880eeac cba555c2 f3cbd601 b51533bc
15:16:09 ipsec,debug ===
15:16:09 ipsec,debug encryption(aes)
15:16:09 ipsec,debug IV was saved for next processing:
15:16:09 ipsec,debug b1fbe1b7 4893cea9 19c1071f 1c36e19b
15:16:09 ipsec,debug encryption(aes)
15:16:09 ipsec,debug with key:
15:16:09 ipsec,debug b1d7c185 aca220ff 96a3fc61 31155926 33cce459 861802b4 24e99c2
c 458d70b6
15:16:09 ipsec,debug decrypted payload by IV:
15:16:09 ipsec,debug a880eeac cba555c2 f3cbd601 b51533bc
15:16:09 ipsec,debug decrypted payload, but not trimed.
15:16:09 ipsec,debug 01000018 2f34201e af427911 d056c48f ec0ee4be 46f17ceb 0a0000b
8 00000001
15:16:09 ipsec,debug 00000001 000000ac 01030406 07e4e7bc 0300001c 010c0000 8001000
1 80020e10
15:16:09 ipsec,debug 80040004 80060100 80050002 0300001c 020c0000 80010001 80020e1
0 80040004
15:16:09 ipsec,debug 80060100 80050001 0300001c 030c0000 80010001 80020e10 8004000
4 80060080
15:16:09 ipsec,debug 80050002 0300001c 040c0000 80010001 80020e10 80040004 8006008
0 80050001
15:16:09 ipsec,debug 03000018 05030000 80010001 80020e10 80040004 80050002 0000001
8 06030000
15:16:09 ipsec,debug 80010001 80020e10 80040004 80050001 05000014 ce8baa1e 11d72d9
4 1ed1a35d
15:16:09 ipsec,debug 2c9e825a 0500000c 0111cef5 c0a80527 1500000c 011106a5 4a523b8
2 1500000c
15:16:09 ipsec,debug 01000000 c0a80527 0000000c 01000000 4a523b82 00000000 0000000
0 0000000c
15:16:09 ipsec,debug padding len=13
15:16:09 ipsec,debug skip to trim padding.
15:16:09 ipsec,debug decrypted.
15:16:09 ipsec,debug 0ca0ebeb 85ce3373 31876834 2374a315 08102001 9db55d38 0000013
c 01000018
15:16:09 ipsec,debug 2f34201e af427911 d056c48f ec0ee4be 46f17ceb 0a0000b8 0000000
1 00000001
15:16:09 ipsec,debug 000000ac 01030406 07e4e7bc 0300001c 010c0000 80010001 80020e1
0 80040004
15:16:09 ipsec,debug 80060100 80050002 0300001c 020c0000 80010001 80020e10 8004000
4 80060100
15:16:09 ipsec,debug 80050001 0300001c 030c0000 80010001 80020e10 80040004 8006008
0 80050002
15:16:09 ipsec,debug 0300001c 040c0000 80010001 80020e10 80040004 80060080 8005000
1 03000018
15:16:09 ipsec,debug 05030000 80010001 80020e10 80040004 80050002 00000018 0603000
0 80010001
15:16:09 ipsec,debug 80020e10 80040004 80050001 05000014 ce8baa1e 11d72d94 1ed1a35
d 2c9e825a
15:16:09 ipsec,debug 0500000c 0111cef5 c0a80527 1500000c 011106a5 4a523b82 1500000
c 01000000
15:16:09 ipsec,debug c0a80527 0000000c 01000000 4a523b82 00000000 00000000 0000000
c
15:16:09 ipsec,debug begin.
15:16:09 ipsec,debug seen nptype=8(hash) len=24
15:16:09 ipsec,debug seen nptype=1(sa) len=184
15:16:09 ipsec,debug seen nptype=10(nonce) len=20
15:16:09 ipsec,debug seen nptype=5(id) len=12
15:16:09 ipsec,debug seen nptype=5(id) len=12
15:16:09 ipsec,debug seen nptype=21(nat-oa) len=12
15:16:09 ipsec,debug seen nptype=21(nat-oa) len=12
15:16:09 ipsec,debug succeed.
15:16:09 ipsec,debug received IDci2:
15:16:09 ipsec,debug 0111cef5 c0a80527
15:16:09 ipsec,debug received IDcr2:
15:16:09 ipsec,debug 011106a5 4a523b82
15:16:09 ipsec,debug HASH(1) validate:
15:16:09 ipsec,debug 2f34201e af427911 d056c48f ec0ee4be 46f17ceb
15:16:09 ipsec,debug HASH with:
15:16:09 ipsec,debug 9db55d38 0a0000b8 00000001 00000001 000000ac 01030406 07e4e7b
c 0300001c
15:16:09 ipsec,debug 010c0000 80010001 80020e10 80040004 80060100 80050002 0300001
c 020c0000
15:16:09 ipsec,debug 80010001 80020e10 80040004 80060100 80050001 0300001c 030c000
0 80010001
15:16:09 ipsec,debug 80020e10 80040004 80060080 80050002 0300001c 040c0000 8001000
1 80020e10
15:16:09 ipsec,debug 80040004 80060080 80050001 03000018 05030000 80010001 80020e1
0 80040004
15:16:09 ipsec,debug 80050002 00000018 06030000 80010001 80020e10 80040004 8005000
1 05000014
15:16:09 ipsec,debug ce8baa1e 11d72d94 1ed1a35d 2c9e825a 0500000c 0111cef5 c0a8052
7 1500000c
15:16:09 ipsec,debug 011106a5 4a523b82 1500000c 01000000 c0a80527 0000000c 0100000
0 4a523b82
15:16:09 ipsec,debug hmac(hmac_sha1)
15:16:09 ipsec,debug HASH computed:
15:16:09 ipsec,debug 2f34201e af427911 d056c48f ec0ee4be 46f17ceb
15:16:09 ipsec,debug total SA len=180
15:16:09 ipsec,debug 00000001 00000001 000000ac 01030406 07e4e7bc 0300001c 010c000
0 80010001
15:16:09 ipsec,debug 80020e10 80040004 80060100 80050002 0300001c 020c0000 8001000
1 80020e10
15:16:09 ipsec,debug 80040004 80060100 80050001 0300001c 030c0000 80010001 80020e1
0 80040004
15:16:09 ipsec,debug 80060080 80050002 0300001c 040c0000 80010001 80020e10 8004000
4 80060080
15:16:09 ipsec,debug 80050001 03000018 05030000 80010001 80020e10 80040004 8005000
2 00000018
15:16:09 ipsec,debug 06030000 80010001 80020e10 80040004 80050001
15:16:09 ipsec,debug begin.
15:16:09 ipsec,debug seen nptype=2(prop) len=172
15:16:09 ipsec,debug succeed.
15:16:09 ipsec,debug proposal #1 len=172
15:16:09 ipsec,debug begin.
15:16:09 ipsec,debug seen nptype=3(trns) len=28
15:16:09 ipsec,debug seen nptype=3(trns) len=28
15:16:09 ipsec,debug seen nptype=3(trns) len=28
15:16:09 ipsec,debug seen nptype=3(trns) len=28
15:16:09 ipsec,debug seen nptype=3(trns) len=24
15:16:09 ipsec,debug seen nptype=3(trns) len=24
15:16:09 ipsec,debug succeed.
15:16:09 ipsec,debug transform #1 len=28
15:16:09 ipsec,debug type=SA Life Type, flag=0x8000, lorv=seconds
15:16:09 ipsec,debug type=SA Life Duration, flag=0x8000, lorv=3600
15:16:09 ipsec,debug life duration was in TLV.
15:16:09 ipsec,debug type=Encryption Mode, flag=0x8000, lorv=UDP-Transport
15:16:09 ipsec,debug UDP encapsulation requested
15:16:09 ipsec,debug type=Key Length, flag=0x8000, lorv=256
15:16:09 ipsec,debug type=Authentication Algorithm, flag=0x8000, lorv=hmac-sha1
15:16:09 ipsec,debug transform #2 len=28
15:16:09 ipsec,debug type=SA Life Type, flag=0x8000, lorv=seconds
15:16:09 ipsec,debug type=SA Life Duration, flag=0x8000, lorv=3600
15:16:09 ipsec,debug life duration was in TLV.
15:16:09 ipsec,debug type=Encryption Mode, flag=0x8000, lorv=UDP-Transport
15:16:09 ipsec,debug UDP encapsulation requested
15:16:09 ipsec,debug type=Key Length, flag=0x8000, lorv=256
15:16:09 ipsec,debug type=Authentication Algorithm, flag=0x8000, lorv=hmac-md5
15:16:09 ipsec,debug transform #3 len=28
15:16:09 ipsec,debug type=SA Life Type, flag=0x8000, lorv=seconds
15:16:09 ipsec,debug type=SA Life Duration, flag=0x8000, lorv=3600
15:16:09 ipsec,debug life duration was in TLV.
15:16:09 ipsec,debug type=Encryption Mode, flag=0x8000, lorv=UDP-Transport
15:16:09 ipsec,debug UDP encapsulation requested
15:16:09 ipsec,debug type=Key Length, flag=0x8000, lorv=128
15:16:09 ipsec,debug type=Authentication Algorithm, flag=0x8000, lorv=hmac-sha1
15:16:09 ipsec,debug transform #4 len=28
15:16:09 ipsec,debug type=SA Life Type, flag=0x8000, lorv=seconds
15:16:09 ipsec,debug type=SA Life Duration, flag=0x8000, lorv=3600
15:16:09 ipsec,debug life duration was in TLV.
15:16:09 ipsec,debug type=Encryption Mode, flag=0x8000, lorv=UDP-Transport
15:16:09 ipsec,debug UDP encapsulation requested
15:16:09 ipsec,debug type=Key Length, flag=0x8000, lorv=128
15:16:09 ipsec,debug type=Authentication Algorithm, flag=0x8000, lorv=hmac-md5
15:16:09 ipsec,debug transform #5 len=24
15:16:09 ipsec,debug type=SA Life Type, flag=0x8000, lorv=seconds
15:16:09 ipsec,debug type=SA Life Duration, flag=0x8000, lorv=3600
15:16:09 ipsec,debug life duration was in TLV.
15:16:09 ipsec,debug type=Encryption Mode, flag=0x8000, lorv=UDP-Transport
15:16:09 ipsec,debug UDP encapsulation requested
15:16:09 ipsec,debug type=Authentication Algorithm, flag=0x8000, lorv=hmac-sha1
15:16:09 ipsec,debug transform #6 len=24
15:16:09 ipsec,debug type=SA Life Type, flag=0x8000, lorv=seconds
15:16:09 ipsec,debug type=SA Life Duration, flag=0x8000, lorv=3600
15:16:09 ipsec,debug life duration was in TLV.
15:16:09 ipsec,debug type=Encryption Mode, flag=0x8000, lorv=UDP-Transport
15:16:09 ipsec,debug UDP encapsulation requested
15:16:09 ipsec,debug type=Authentication Algorithm, flag=0x8000, lorv=hmac-md5
15:16:09 ipsec,debug pair 1:
15:16:09 ipsec,debug 0x77c88: next=(nil) tnext=0x78d40
15:16:09 ipsec,debug 0x78d40: next=(nil) tnext=0x78d58
15:16:09 ipsec,debug 0x78d58: next=(nil) tnext=0x79ea8
15:16:09 ipsec,debug 0x79ea8: next=(nil) tnext=0x79ec0
15:16:09 ipsec,debug 0x79ec0: next=(nil) tnext=0x79ed8
15:16:09 ipsec,debug 0x79ed8: next=(nil) tnext=(nil)
15:16:09 ipsec,debug proposal #1: 6 transform
15:16:09 ipsec,debug got the local address from ID payload x.x.x.x[1701] pref
ixlen=32 ul_proto=17
15:16:09 ipsec,debug got the peer address from ID payload 192.168.5.39[52981] pref
ixlen=32 ul_proto=17
15:16:09 ipsec,debug updating policy address because of NAT in transport mode
15:16:09 ipsec,debug new peer address x.x.x.x[52981]
15:16:09 ipsec,debug (proto_id=ESP spisize=4 spi=00000000 spi_p=00000000 encmode=
UDP-Tunnel reqid=8:8)
15:16:09 ipsec,debug (trns_id=AES-CBC encklen=256 authtype=hmac-sha1)
15:16:09 ipsec,debug (trns_id=AES-CBC encklen=192 authtype=hmac-sha1)
15:16:09 ipsec,debug (trns_id=AES-CBC encklen=128 authtype=hmac-sha1)
15:16:09 ipsec,debug (trns_id=3DES encklen=0 authtype=hmac-sha1)
15:16:09 ipsec,debug begin compare proposals.
15:16:09 ipsec,debug pair[1]: 0x77c88
15:16:09 ipsec,debug 0x77c88: next=(nil) tnext=0x78d40
15:16:09 ipsec,debug 0x78d40: next=(nil) tnext=0x78d58
15:16:09 ipsec,debug 0x78d58: next=(nil) tnext=0x79ea8
15:16:09 ipsec,debug 0x79ea8: next=(nil) tnext=0x79ec0
15:16:09 ipsec,debug 0x79ec0: next=(nil) tnext=0x79ed8
15:16:09 ipsec,debug 0x79ed8: next=(nil) tnext=(nil)
15:16:09 ipsec,debug prop#=1 prot-id=ESP spi-size=4 #trns=6 trns#=1 trns-id=AES-CB
C
15:16:09 ipsec,debug type=SA Life Type, flag=0x8000, lorv=seconds
15:16:09 ipsec,debug type=SA Life Duration, flag=0x8000, lorv=3600
15:16:09 ipsec,debug type=Encryption Mode, flag=0x8000, lorv=UDP-Transport
15:16:09 ipsec,debug type=Key Length, flag=0x8000, lorv=256
15:16:09 ipsec,debug type=Authentication Algorithm, flag=0x8000, lorv=hmac-sha1
15:16:09 ipsec,debug prop#=1 prot-id=ESP spi-size=4 #trns=6 trns#=2 trns-id=AES-CB
C
15:16:09 ipsec,debug type=SA Life Type, flag=0x8000, lorv=seconds
15:16:09 ipsec,debug type=SA Life Duration, flag=0x8000, lorv=3600
15:16:09 ipsec,debug type=Encryption Mode, flag=0x8000, lorv=UDP-Transport
15:16:09 ipsec,debug type=Key Length, flag=0x8000, lorv=256
15:16:09 ipsec,debug type=Authentication Algorithm, flag=0x8000, lorv=hmac-md5
15:16:09 ipsec,debug prop#=1 prot-id=ESP spi-size=4 #trns=6 trns#=3 trns-id=AES-CB
C
15:16:09 ipsec,debug type=SA Life Type, flag=0x8000, lorv=seconds
15:16:09 ipsec,debug type=SA Life Duration, flag=0x8000, lorv=3600
15:16:09 ipsec,debug type=Encryption Mode, flag=0x8000, lorv=UDP-Transport
15:16:09 ipsec,debug type=Key Length, flag=0x8000, lorv=128
15:16:09 ipsec,debug type=Authentication Algorithm, flag=0x8000, lorv=hmac-sha1
15:16:09 ipsec,debug prop#=1 prot-id=ESP spi-size=4 #trns=6 trns#=4 trns-id=AES-CB
C
15:16:09 ipsec,debug type=SA Life Type, flag=0x8000, lorv=seconds
15:16:09 ipsec,debug type=SA Life Duration, flag=0x8000, lorv=3600
15:16:09 ipsec,debug type=Encryption Mode, flag=0x8000, lorv=UDP-Transport
15:16:09 ipsec,debug type=Key Length, flag=0x8000, lorv=128
15:16:09 ipsec,debug type=Authentication Algorithm, flag=0x8000, lorv=hmac-md5
15:16:09 ipsec,debug prop#=1 prot-id=ESP spi-size=4 #trns=6 trns#=5 trns-id=3DES
15:16:09 ipsec,debug type=SA Life Type, flag=0x8000, lorv=seconds
15:16:09 ipsec,debug type=SA Life Duration, flag=0x8000, lorv=3600
15:16:09 ipsec,debug type=Encryption Mode, flag=0x8000, lorv=UDP-Transport
15:16:09 ipsec,debug type=Authentication Algorithm, flag=0x8000, lorv=hmac-sha1
15:16:09 ipsec,debug prop#=1 prot-id=ESP spi-size=4 #trns=6 trns#=6 trns-id=3DES
15:16:09 ipsec,debug type=SA Life Type, flag=0x8000, lorv=seconds
15:16:09 ipsec,debug type=SA Life Duration, flag=0x8000, lorv=3600
15:16:09 ipsec,debug type=Encryption Mode, flag=0x8000, lorv=UDP-Transport
15:16:09 ipsec,debug type=Authentication Algorithm, flag=0x8000, lorv=hmac-md5
15:16:09 ipsec,debug peer's single bundle:
15:16:09 ipsec,debug (proto_id=ESP spisize=4 spi=07e4e7bc spi_p=00000000 encmode=
UDP-Transport reqid=0:0)
15:16:09 ipsec,debug (trns_id=AES-CBC encklen=256 authtype=hmac-sha1)
15:16:09 ipsec,debug (trns_id=AES-CBC encklen=256 authtype=hmac-md5)
15:16:09 ipsec,debug (trns_id=AES-CBC encklen=128 authtype=hmac-sha1)
15:16:09 ipsec,debug (trns_id=AES-CBC encklen=128 authtype=hmac-md5)
15:16:09 ipsec,debug (trns_id=3DES encklen=0 authtype=hmac-sha1)
15:16:09 ipsec,debug (trns_id=3DES encklen=0 authtype=hmac-md5)
15:16:09 ipsec,debug my single bundle:
15:16:09 ipsec,debug (proto_id=ESP spisize=4 spi=00000000 spi_p=00000000 encmode=
UDP-Tunnel reqid=8:8)
15:16:09 ipsec,debug (trns_id=AES-CBC encklen=256 authtype=hmac-sha1)
15:16:09 ipsec,debug (trns_id=AES-CBC encklen=192 authtype=hmac-sha1)
15:16:09 ipsec,debug (trns_id=AES-CBC encklen=128 authtype=hmac-sha1)
15:16:09 ipsec,debug (trns_id=3DES encklen=0 authtype=hmac-sha1)
15:16:09 ipsec,debug not matched
15:16:09 ipsec,error no suitable proposal found.
15:16:09 ipsec,error x.x.x.x failed to pre-process ph2 packet.
15:16:09 ipsec,debug compute IV for phase2
15:16:09 ipsec,debug phase1 last IV:
15:16:09 ipsec,debug bc0dbf76 f15e2a27 cc6e4816 46d4da83 c4575b73
15:16:09 ipsec,debug hash(sha1)
15:16:09 ipsec,debug encryption(aes)
15:16:09 ipsec,debug phase2 IV computed:
15:16:09 ipsec,debug 5569a0f7 88561e97 252f3a21 b481dd2d
15:16:09 ipsec,debug HASH with:
15:16:09 ipsec,debug c4575b73 0000000c 00000001 0100000e
15:16:09 ipsec,debug hmac(hmac_sha1)
15:16:09 ipsec,debug HASH computed:
15:16:09 ipsec,debug 3e72abbc 202592d7 b7969b08 0196a272 93c2cd4e
15:16:09 ipsec,debug begin encryption.
15:16:09 ipsec,debug encryption(aes)
15:16:09 ipsec,debug pad length = 12
15:16:09 ipsec,debug 0b000018 3e72abbc 202592d7 b7969b08 0196a272 93c2cd4e 0000000
c 00000001
15:16:09 ipsec,debug 0100000e b8f782ac 80af9e93 f8d5fc0b
15:16:09 ipsec,debug encryption(aes)
15:16:09 ipsec,debug with key:
15:16:09 ipsec,debug b1d7c185 aca220ff 96a3fc61 31155926 33cce459 861802b4 24e99c2
c 458d70b6
15:16:09 ipsec,debug encrypted payload by IV:
15:16:09 ipsec,debug 5569a0f7 88561e97 252f3a21 b481dd2d
15:16:09 ipsec,debug save IV for next:
15:16:09 ipsec,debug 82bc598e 5dbbab94 c60b2d8c 7e7e4553
15:16:09 ipsec,debug encrypted.
15:16:09 ipsec,debug 76 bytes from x.x.x.x[4500] to x.x.x.x[4500]
15:16:09 ipsec,debug 1 times of 80 bytes message will be sent to x.x.x.x[4500
]
15:16:09 ipsec,debug,packet 0ca0ebeb 85ce3373 31876834 2374a315 08100501 c4575b73
0000004c 732c6c8c
15:16:09 ipsec,debug,packet f569e1d2 31e90a9e 1d709017 eed72026 92798e27 e4ab679f
210c255f 82bc598e
15:16:09 ipsec,debug,packet 5dbbab94 c60b2d8c 7e7e4553
15:16:09 ipsec,debug sendto Information notify.
15:16:12 ipsec,debug ===== received 316 bytes from x.x.x.x[4500] to 74.82.59.
130[4500]
15:16:12 ipsec,debug,packet 0ca0ebeb 85ce3373 31876834 2374a315 08102001 9db55d38
0000013c 41118418
15:16:12 ipsec,debug,packet 64aed3df 721bb55e 9359905d 82d939a8 d9972f19 e01d2d25
b24c670c 510c746e
15:16:12 ipsec,debug,packet af9c9f41 4407b600 f39f2539 163279b9 6ad2130d 765c1f3b
af913ef4 c1f397f6
15:16:12 ipsec,debug,packet 7584524e 3cd4ce60 33a4e038 c54b343d d54ae1fb 666e5fb1
346f6f87 4adf9351
15:16:12 ipsec,debug,packet 96dac517 3d72cf0e beb8346d 690c9735 ee29d3ee d4b067e0
bdd8838b 9573150d
15:16:12 ipsec,debug,packet 54620d73 872861c4 98e15e8e 3c6d1144 7d7758c4 35b3fc81
a49d0aee f89aa7ba
15:16:12 ipsec,debug,packet d9915d1e 01700709 a2a5197f a5301dca 1669d9a3 e0f34882
569900a7 a53b6004
15:16:12 ipsec,debug,packet f2e14dd3 1f1211c0 1ac0c3b3 00af3220 9981ca6e f7c38662
530c487e 62f25637
15:16:12 ipsec,debug,packet 04dafd29 4eceb4f7 ce96259e 26eb9893 f633e93f 5cc4ca88
f59daccb 0ae0e17c
15:16:12 ipsec,debug,packet 28ca3552 ec8ffedc 60aa393d b1fbe1b7 4893cea9 19c1071f
1c36e19b
15:16:12 ipsec,error x.x.x.x peer sent packet for dead phase2
15:16:15 ipsec,debug ===== received 316 bytes from x.x.x.x[4500] to 74.82.59.
130[4500]
15:16:15 ipsec,debug,packet 0ca0ebeb 85ce3373 31876834 2374a315 08102001 9db55d38
0000013c 41118418
15:16:15 ipsec,debug,packet 64aed3df 721bb55e 9359905d 82d939a8 d9972f19 e01d2d25
b24c670c 510c746e
15:16:15 ipsec,debug,packet af9c9f41 4407b600 f39f2539 163279b9 6ad2130d 765c1f3b
af913ef4 c1f397f6
15:16:15 ipsec,debug,packet 7584524e 3cd4ce60 33a4e038 c54b343d d54ae1fb 666e5fb1
346f6f87 4adf9351
15:16:15 ipsec,debug,packet 96dac517 3d72cf0e beb8346d 690c9735 ee29d3ee d4b067e0
bdd8838b 9573150d
15:16:15 ipsec,debug,packet 54620d73 872861c4 98e15e8e 3c6d1144 7d7758c4 35b3fc81
a49d0aee f89aa7ba
15:16:15 ipsec,debug,packet d9915d1e 01700709 a2a5197f a5301dca 1669d9a3 e0f34882
569900a7 a53b6004
15:16:15 ipsec,debug,packet f2e14dd3 1f1211c0 1ac0c3b3 00af3220 9981ca6e f7c38662
530c487e 62f25637
15:16:15 ipsec,debug,packet 04dafd29 4eceb4f7 ce96259e 26eb9893 f633e93f 5cc4ca88
f59daccb 0ae0e17c
15:16:15 ipsec,debug,packet 28ca3552 ec8ffedc 60aa393d b1fbe1b7 4893cea9 19c1071f
1c36e19b
15:16:15 ipsec,error x.x.x.x peer sent packet for dead phase2
15:16:18 ipsec,debug ===== received 316 bytes from x.x.x.x[4500] to 74.82.59.
130[4500]
15:16:18 ipsec,debug,packet 0ca0ebeb 85ce3373 31876834 2374a315 08102001 9db55d38
0000013c 41118418
15:16:18 ipsec,debug,packet 64aed3df 721bb55e 9359905d 82d939a8 d9972f19 e01d2d25
b24c670c 510c746e
15:16:18 ipsec,debug,packet af9c9f41 4407b600 f39f2539 163279b9 6ad2130d 765c1f3b
af913ef4 c1f397f6
15:16:18 ipsec,debug,packet 7584524e 3cd4ce60 33a4e038 c54b343d d54ae1fb 666e5fb1
346f6f87 4adf9351
15:16:18 ipsec,debug,packet 96dac517 3d72cf0e beb8346d 690c9735 ee29d3ee d4b067e0
bdd8838b 9573150d
15:16:18 ipsec,debug,packet 54620d73 872861c4 98e15e8e 3c6d1144 7d7758c4 35b3fc81
a49d0aee f89aa7ba
15:16:18 ipsec,debug,packet d9915d1e 01700709 a2a5197f a5301dca 1669d9a3 e0f34882
569900a7 a53b6004
15:16:18 ipsec,debug,packet f2e14dd3 1f1211c0 1ac0c3b3 00af3220 9981ca6e f7c38662
530c487e 62f25637
15:16:18 ipsec,debug,packet 04dafd29 4eceb4f7 ce96259e 26eb9893 f633e93f 5cc4ca88
f59daccb 0ae0e17c
15:16:18 ipsec,debug,packet 28ca3552 ec8ffedc 60aa393d b1fbe1b7 4893cea9 19c1071f
1c36e19b
15:16:18 ipsec,error x.x.x.x peer sent packet for dead phase2
15:16:22 ipsec,debug ===== received 316 bytes from x.x.x.x[4500] to 74.82.59.
130[4500]
15:16:22 ipsec,debug,packet 0ca0ebeb 85ce3373 31876834 2374a315 08102001 9db55d38
0000013c 41118418
15:16:22 ipsec,debug,packet 64aed3df 721bb55e 9359905d 82d939a8 d9972f19 e01d2d25
b24c670c 510c746e
15:16:22 ipsec,debug,packet af9c9f41 4407b600 f39f2539 163279b9 6ad2130d 765c1f3b
af913ef4 c1f397f6
15:16:22 ipsec,debug,packet 7584524e 3cd4ce60 33a4e038 c54b343d d54ae1fb 666e5fb1
346f6f87 4adf9351
15:16:22 ipsec,debug,packet 96dac517 3d72cf0e beb8346d 690c9735 ee29d3ee d4b067e0
bdd8838b 9573150d
15:16:22 ipsec,debug,packet 54620d73 872861c4 98e15e8e 3c6d1144 7d7758c4 35b3fc81
a49d0aee f89aa7ba
15:16:22 ipsec,debug,packet d9915d1e 01700709 a2a5197f a5301dca 1669d9a3 e0f34882
569900a7 a53b6004
15:16:22 ipsec,debug,packet f2e14dd3 1f1211c0 1ac0c3b3 00af3220 9981ca6e f7c38662
530c487e 62f25637
15:16:22 ipsec,debug,packet 04dafd29 4eceb4f7 ce96259e 26eb9893 f633e93f 5cc4ca88
f59daccb 0ae0e17c
15:16:22 ipsec,debug,packet 28ca3552 ec8ffedc 60aa393d b1fbe1b7 4893cea9 19c1071f
1c36e19b
15:16:22 ipsec,error x.x.x.x peer sent packet for dead phase2
15:16:24 ipsec,debug KA: x.x.x.x[4500]->x.x.x.x[4500]
15:16:24 ipsec,debug 1 times of 1 bytes message will be sent to x.x.x.x[4500]
15:16:24 ipsec,debug,packet ff
[admin@FMT-ROUTER] >
tunnel=yes|no15:16:09 ipsec,debug peer's single bundle:
15:16:09 ipsec,debug (proto_id=ESP spisize=4 spi=07e4e7bc spi_p=00000000 encmode=UDP-Transport reqid=0:0) <--#####
15:16:09 ipsec,debug (trns_id=AES-CBC encklen=256 authtype=hmac-sha1)
15:16:09 ipsec,debug (trns_id=AES-CBC encklen=256 authtype=hmac-md5)
15:16:09 ipsec,debug (trns_id=AES-CBC encklen=128 authtype=hmac-sha1)
15:16:09 ipsec,debug (trns_id=AES-CBC encklen=128 authtype=hmac-md5)
15:16:09 ipsec,debug (trns_id=3DES encklen=0 authtype=hmac-sha1)
15:16:09 ipsec,debug (trns_id=3DES encklen=0 authtype=hmac-md5)
15:16:09 ipsec,debug my single bundle:
15:16:09 ipsec,debug (proto_id=ESP spisize=4 spi=00000000 spi_p=00000000 encmode=UDP-Tunnel reqid=8:8) <--#####
15:16:09 ipsec,debug (trns_id=AES-CBC encklen=256 authtype=hmac-sha1)
15:16:09 ipsec,debug (trns_id=AES-CBC encklen=192 authtype=hmac-sha1)
15:16:09 ipsec,debug (trns_id=AES-CBC encklen=128 authtype=hmac-sha1)
15:16:09 ipsec,debug (trns_id=3DES encklen=0 authtype=hmac-sha1)/ip ipsec policy print detail[admin@FMT-ROUTER] > /ip ipsec policy print detail
Flags: T - template, X - disabled, D - dynamic, I - invalid, A - active,
* - default
0 T * group=default src-address=::/0 dst-address=::/0 protocol=all
proposal=default template=yes
[admin@FMT-ROUTER] >
Please report that briefly to support@mikrotik.com with a link to this thread, including the version where it didn't work before you've upgraded to 6.42rc35.Ok, I just downgraded it to 6.41.3. Tried it again and it worked! It was definitely the version. Which is strange, because the previous version didn't work, so I updated to the RC, which gave the same issue. Now, I downgraded and it works.
which, however, doesn't appear in the changelog between 6.41.1 and 6.41.3.*) ike1 - fixed wildcard policy lookup on responder;
Well, to me it does not seem strange because before there was the conflicting manually added peer, wasn't it? So if you would try with the original version now, I assume it would eb working as well with that conflicting peer disabled or removed.Ok, I just downgraded it to 6.41.3. Tried it again and it worked! It was definitely the version. Which is strange, because the previous version didn't work, so I updated to the RC, which gave the same issue. Now, I downgraded and it works.