I played with it a little more and made a proof-of-concept of what I consider proper solution. Wireshark supports plugin interface called extcap. It's external executables or scripts that acquire data and feed them to Wireshark. And it's exactly what's needed here, something that receives TZSP packets on port 37008, unwraps original packets and passes them to Wireshark.
It's nowhere near to really be THE solution, it's minimalistic version without any error checks and with ugly shortcuts, but if you're not too unlucky, it works. It's made with PHP, which is probably quite unusual choice, but I really like PHP, especially for quick tests. It's tested with Wireshark 3.0.1 on Windows 7.
<Wireshark directory>\extcap\tzspdump.cmd:
@echo off
<path to php directory>\php.exe "<Wireshark directory>\tzspdump.php" %*
:
<?php
$options = getopt('', Array('extcap-interfaces', 'capture', 'extcap-interface:', 'fifo:', 'extcap-capture-filter:'));
if(empty($options)) {
echo 'Wireshark - tzspdump.php v0.0.1'.PHP_EOL;
} elseif(isset($options['extcap-interfaces'])) {
echo 'extcap {version=0.0.1}'.PHP_EOL;
echo 'interface {value=tzspdump}{display=TZSP Listener remote capture}'.PHP_EOL;
} elseif(isset($options['capture'])) {
if(isset($options['fifo'])) {
$pipe = str_replace('\\\\.\\pipe', '\\\\'.php_uname('n').'\\pipe', $options['fifo']);
$ph = fopen($pipe, 'a+');
fwrite($ph, "\xd4\xc3\xb2\xa1\x02\x00\x04\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x04\x00\x01\x00\x00\x00");
$sock = socket_create(AF_INET, SOCK_DGRAM, 0);
socket_bind($sock, '0.0.0.0' , 37008);
while(true) {
socket_recvfrom($sock, $buf, 10000, 0, $remote_ip, $remote_port);
$size = strlen($buf);
$t = explode(' ', microtime());
$size -= 5;
if(!fwrite($ph, pack('L', intval($t[1])).pack('L', intval(substr($t[0], 2))).pack('L', $size).pack('L', $size))) break;
if(!fwrite($ph, substr($buf, 5))) break;
}
socket_close($sock);
}
}
?>
Once installed, it will add another interface to Wireshark:
tzsp1.png
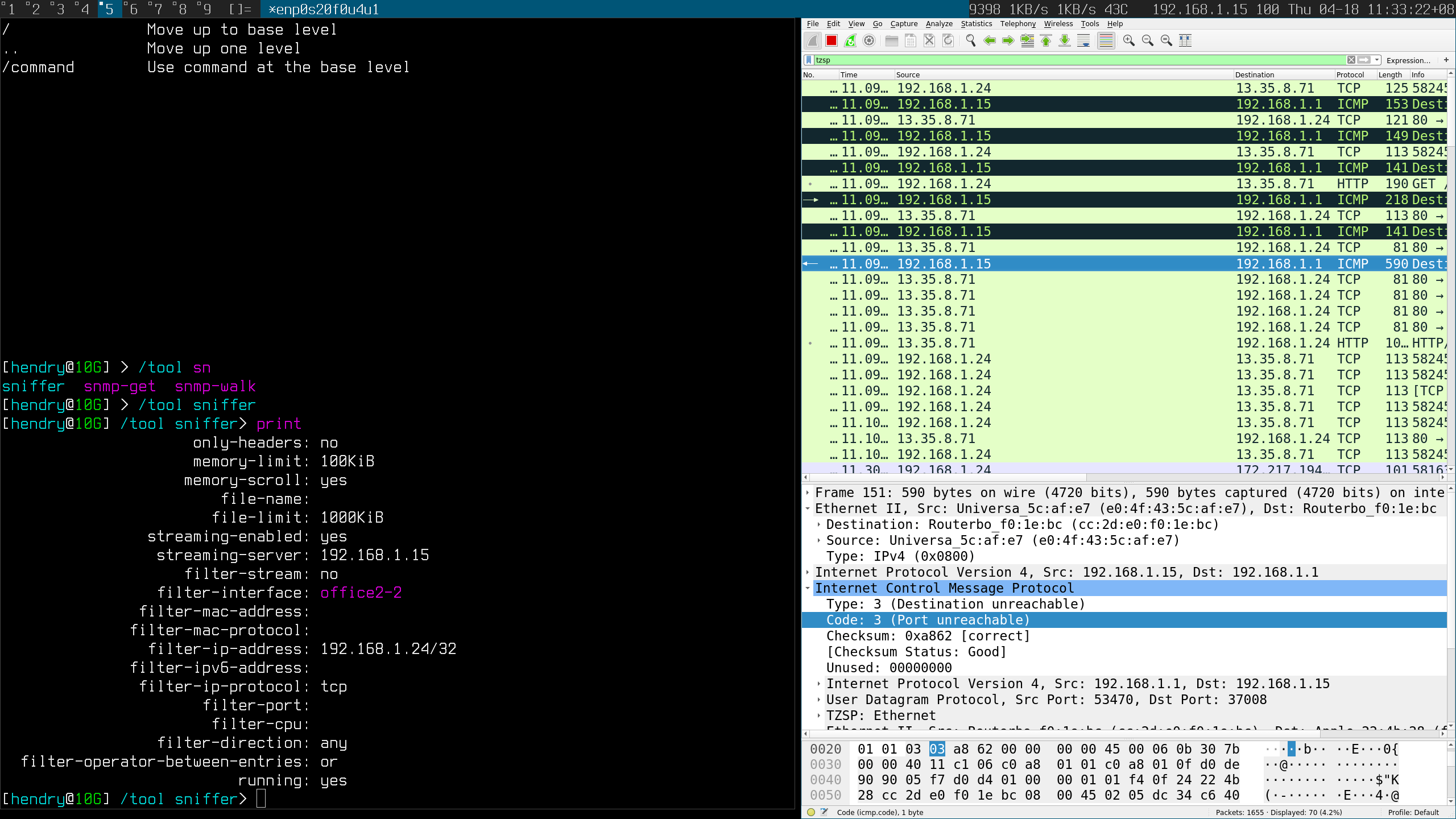
If you select it and start capture, Wireshark will start the script and it will listen on udp/37008 (you may need to allow it in firewall) and will pass all received packets to Wireshark. Here is an example of router sending CDP packet (notice that it's the original packet, as was on the router, no TZSP wrapping):
tzsp2.png
And that's all folks. I don't plan to develop this further, because PHP script is a dead end, regular people don't have PHP installed and to get it only for this is unreasonable. Best solution would be to convince Wireshark guys to properly implement this. Or someone else to do it and send them a patch. Feel free to do any of that, I'm not very good with convincing someone and too lazy to write proper code.

But that's not really all, there's one more thing. It seems that there might be a bug in RouterOS. The option to filter stream (to not capture TZSP packets sent by router) doesn't seem to always work. With small packets, everything is ok. But large packets don't fit in one TZSP packet and need to be sent fragmented. And then something like this happens, router captures own TZSP packets (it's captured using regular Wireshark capture on ethernet interface):
tzsp3.png