I have basic networking for my soho with 3 VLANss.
I'm using default firewall rules and need a filter/rules to prevent VLAN10 and VLAN20 from accessing other VLANs.
I have googled and add some rules but it seems not block the access. So, I restore the router to default cong and setup all the VLANs again w/o messing with any rules right now.
I need help, advice or suggestions on how to implement this in the firewall.
This is my setup: Hex mmips
WAN=ether1
Default local network is 192.168.88.0/24 using port ether2, ether3, ether4 on the mikrotik router.
VLAN4=192.168.4.0/24 (ether5)
VLAN10=192.168.10.0/24 (ether5)
VLAN20=10.0.20.0/24 (ether5)
I already setup my Netgear switch with trunk to eth5 on mikrotik hex and this setup is up and running.
Re: Need help with firewall rules to prevent VLAN access to LAN
In forward chain,
ensure your subnet has access to internet if required
ensure your vlans have access to internet if required
Then create last rule
chain=forward chain action=drop comment="drop all else"
Any traffic you didnt setup before this rule will be dropped including chatter between vlans etc.......
ensure your subnet has access to internet if required
ensure your vlans have access to internet if required
Then create last rule
chain=forward chain action=drop comment="drop all else"
Any traffic you didnt setup before this rule will be dropped including chatter between vlans etc.......
Re: Need help with firewall rules to prevent VLAN access to LAN
Something like this?
Be easy on the newbe, lol.
Be easy on the newbe, lol.
Code: Select all
add action=accept chain=forward comment="defconf: accept established,related" connection-state=established,related
add action=drop chain=forward comment="defconf: drop invalid" connection-state=invalid
add action=accept chain=input comment="defconf: accept established,related" connection-state=established,related
add action=drop chain=input comment="defconf: drop invalid" connection-state=invalid
add action=drop chain=input comment="defconf: drop all not coming from LAN" in-interface-list=!LAN
add action=drop chain=forward comment="Drop all else"Re: Need help with firewall rules to prevent VLAN access to LAN
I usually dont comment on snippets as the whole config tells the story
/export hide-sensitive file=anynameyouwish
So far so good (but without the rest a meaningless statement).
The order within a chain is critical and thus to make it read far easier most admins
put all the input rules first and then the forward chain rules so one doesnt have to bounce back and forth especially on complex firewall rules.
/export hide-sensitive file=anynameyouwish
So far so good (but without the rest a meaningless statement).
The order within a chain is critical and thus to make it read far easier most admins
put all the input rules first and then the forward chain rules so one doesnt have to bounce back and forth especially on complex firewall rules.
Re: Need help with firewall rules to prevent VLAN access to LAN
I usually dont comment on snippets as the whole config tells the story
/export hide-sensitive file=anynameyouwish
So far so good (but without the rest a meaningless statement).
The order within a chain is critical and thus to make it read far easier most admins
put all the input rules first and then the forward chain rules so one doesnt have to bounce back and forth especially on complex firewall rules.
Here it is.
I tested it but and can ping from any VLAN to another. So, as is it's not working.
All I'm trying is VLAN 10 and VLAN20 seperated and no access to LAN. I don't care if other from LAN has access to this two VLAN.
# jan/01/2002 18:00:38 by RouterOS 6.46.4
# software id = S1MG-NEED
# model = RouterBOARD 750G r3
# serial number = xxxxxxxxxx
/interface bridge
add admin-mac=xx:xx:xx:xx:xx auto-mac=no comment=defconf name=bridge
/interface vlan
add interface=ether5 name=VLAN4 vlan-id=4
add interface=ether5 name=VLAN10 vlan-id=10
add interface=ether5 name=VLAN20 vlan-id=20
/interface list
add comment=defconf name=WAN
add comment=defconf name=LAN
/ip pool
add name=dhcp ranges=192.168.88.100-192.168.88.150
add name=dhcp_pool1 ranges=192.168.4.10-192.168.4.200
add name=dhcp_pool2 ranges=192.168.10.10-192.168.10.50
add name=dhcp_pool3 ranges=10.0.20.2-10.0.20.100
/ip dhcp-server
add address-pool=dhcp disabled=no interface=bridge name=defconf
add address-pool=dhcp_pool1 disabled=no interface=VLAN4 name=dhcp1
add address-pool=dhcp_pool2 disabled=no interface=VLAN10 name=dhcp2
add address-pool=dhcp_pool3 disabled=no interface=VLAN20 name=dhcp3
/interface bridge port
add bridge=bridge comment=defconf interface=ether2
add bridge=bridge comment=defconf interface=ether3
add bridge=bridge comment=defconf interface=ether4
add bridge=bridge comment=defconf interface=ether5
/ip neighbor discovery-settings
set discover-interface-list=none
/interface list member
add comment=defconf interface=bridge list=LAN
add comment=defconf interface=ether1 list=WAN
/ip address
add address=192.168.88.1/24 comment=defconf interface=ether2 network=\
192.168.88.0
add address=192.168.4.1/24 interface=VLAN4 network=192.168.4.0
add address=192.168.10.1/24 interface=VLAN10 network=192.168.10.0
add address=10.0.20.1/24 interface=VLAN20 network=10.0.20.0
/ip dhcp-client
add comment=defconf disabled=no interface=ether1 use-peer-dns=no
/ip dhcp-server network
add address=10.0.20.0/24 dns-server=8.8.8.8,8.8.4.4 gateway=10.0.20.1
add address=192.168.4.0/24 dns-server=192.168.4.2,208.67.222.123 domain=\
clubamgg.com gateway=192.168.4.1
add address=192.168.10.0/24 dns-server=8.8.8.8,8.8.4.4 gateway=192.168.10.1
add address=192.168.88.0/24 comment=defconf dns-server=208.67.222.123,8.8.8.8 \
domain=clubamgg.com gateway=192.168.88.1
/ip dns
set allow-remote-requests=yes cache-size=5000KiB servers=8.8.8.8,8.8.4.4
/ip dns static
add address=192.168.88.1 comment=defconf name=router.lan
/ip firewall filter
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=accept chain=input comment=\
"defconf: accept to local loopback (for CAPsMAN)" dst-address=127.0.0.1
add action=drop chain=input comment="defconf: drop all not coming from LAN" \
in-interface-list=!LAN
add action=accept chain=forward comment="defconf: accept in ipsec policy" \
ipsec-policy=in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" \
ipsec-policy=out,ipsec
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related
add action=accept chain=forward comment=\
"defconf: accept established,related, untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=drop chain=forward comment=\
"defconf: drop all from WAN not DSTNATed" connection-nat-state=!dstnat \
connection-state=new in-interface-list=WAN
add action=accept chain=forward comment="defconf: accept established,related" \
connection-state=established,related
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=accept chain=input comment="defconf: accept established,related" \
connection-state=established,related
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=drop chain=input comment="defconf: drop all not coming from LAN" \
in-interface-list=!LAN
add action=drop chain=forward comment="Drop all else"
/ip firewall nat
add action=masquerade chain=srcnat comment="defconf: masquerade" \
ipsec-policy=out,none out-interface-list=WAN
add action=masquerade chain=srcnat
/ip service
set telnet disabled=yes
set ftp disabled=yes
set www disabled=yes
set ssh port=2200
set api disabled=yes
set api-ssl disabled=yes
/ipv6 firewall address-list
add address=::/128 comment="defconf: unspecified address" list=bad_ipv6
add address=::1/128 comment="defconf: lo" list=bad_ipv6
add address=fec0::/10 comment="defconf: site-local" list=bad_ipv6
add address=::ffff:0.0.0.0/96 comment="defconf: ipv4-mapped" list=bad_ipv6
add address=::/96 comment="defconf: ipv4 compat" list=bad_ipv6
add address=100::/64 comment="defconf: discard only " list=bad_ipv6
add address=2001:db8::/32 comment="defconf: documentation" list=bad_ipv6
add address=2001:10::/28 comment="defconf: ORCHID" list=bad_ipv6
add address=3ffe::/16 comment="defconf: 6bone" list=bad_ipv6
add address=::224.0.0.0/100 comment="defconf: other" list=bad_ipv6
add address=::127.0.0.0/104 comment="defconf: other" list=bad_ipv6
add address=::/104 comment="defconf: other" list=bad_ipv6
add address=::255.0.0.0/104 comment="defconf: other" list=bad_ipv6
/ipv6 firewall filter
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMPv6" protocol=\
icmpv6
add action=accept chain=input comment="defconf: accept UDP traceroute" port=\
33434-33534 protocol=udp
add action=accept chain=input comment=\
"defconf: accept DHCPv6-Client prefix delegation." dst-port=546 protocol=\
udp src-address=fe80::/10
add action=accept chain=input comment="defconf: accept IKE" dst-port=500,4500 \
protocol=udp
add action=accept chain=input comment="defconf: accept ipsec AH" protocol=\
ipsec-ah
add action=accept chain=input comment="defconf: accept ipsec ESP" protocol=\
ipsec-esp
add action=accept chain=input comment=\
"defconf: accept all that matches ipsec policy" ipsec-policy=in,ipsec
add action=drop chain=input comment=\
"defconf: drop everything else not coming from LAN" in-interface-list=\
!LAN
add action=accept chain=forward comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=drop chain=forward comment=\
"defconf: drop packets with bad src ipv6" src-address-list=bad_ipv6
add action=drop chain=forward comment=\
"defconf: drop packets with bad dst ipv6" dst-address-list=bad_ipv6
add action=drop chain=forward comment="defconf: rfc4890 drop hop-limit=1" \
hop-limit=equal:1 protocol=icmpv6
add action=accept chain=forward comment="defconf: accept ICMPv6" protocol=\
icmpv6
add action=accept chain=forward comment="defconf: accept HIP" protocol=139
add action=accept chain=forward comment="defconf: accept IKE" dst-port=\
500,4500 protocol=udp
add action=accept chain=forward comment="defconf: accept ipsec AH" protocol=\
ipsec-ah
add action=accept chain=forward comment="defconf: accept ipsec ESP" protocol=\
ipsec-esp
add action=accept chain=forward comment=\
"defconf: accept all that matches ipsec policy" ipsec-policy=in,ipsec
add action=drop chain=forward comment=\
"defconf: drop everything else not coming from LAN" in-interface-list=\
!LAN
/system clock
set time-zone-name=America/New_York
/system identity
set name=router
/system ntp client
set enabled=yes primary-ntp=38.229.71.7 secondary-ntp=199.180.133.100
/system ntp server
set broadcast=yes enabled=yes
/tool bandwidth-server
set enabled=no
/tool mac-server
set allowed-interface-list=none
/tool mac-server mac-winbox
set allowed-interface-list=none
Re: Need help with firewall rules to prevent VLAN access to LAN
Your configuration needs work...........
Ether5 is completely hosed and your mixing up use of bridges and vlans it looks like.
Would it be fair to say is that you are using the default LAN on ethernet 2-4 on the same bridge
Then you are using 3 vlans not on any bridge and all going out ether5?
I suppose that could work...........
One way to test would be to try and fix what you have created LOL
(1) remove eth5 from your bridge....... (remove this line in your config).
add bridge=bridge comment=defconf interface=ether5
(2) Change the interface to bridge (not ether2)
/ip address
add address=192.168.88.1/24 comment=defconf interface=ether2 network=\
192.168.88.0
Concur with Sindy, the FW rules are very non-standard looking, especially all the extra rules.
(3) Do not know the purpose of this input fw rule?
add action=accept chain=input comment="defconf: accept UDP traceroute" port=\
33434-33534 protocol=udp
(4) These rules I do not understand why there................. but perhaps they are fine...........
add action=accept chain=forward comment="defconf: accept ICMPv6" protocol=\
icmpv6
add action=accept chain=forward comment="defconf: accept HIP" protocol=139
add action=accept chain=forward comment="defconf: accept IKE" dst-port=\
500,4500 protocol=udp
add action=accept chain=forward comment="defconf: accept ipsec AH" protocol=\
ipsec-ah
add action=accept chain=forward comment="defconf: accept ipsec ESP" protocol=\
ipsec-esp
add action=accept chain=forward comment=\
"defconf: accept all that matches ipsec policy" ipsec-policy=in,ipsec
(5) Not sure I like this line......... (it looks like a default rule from the input chain subverted for use in the forward chain)
add action=drop chain=forward comment=\
"defconf: drop everything else not coming from LAN" in-interface-list=\
Simply change to.
add action=drop chain=input
(thus all traffic not approved by rules above this command will be blocked in the forward chain)
IN other words if you want to give folks access to the internet you will need to put it above this last rule.
bridge to wan
vlan to wan
etc.....
Ether5 is completely hosed and your mixing up use of bridges and vlans it looks like.
Would it be fair to say is that you are using the default LAN on ethernet 2-4 on the same bridge
Then you are using 3 vlans not on any bridge and all going out ether5?
I suppose that could work...........
One way to test would be to try and fix what you have created LOL
(1) remove eth5 from your bridge....... (remove this line in your config).
add bridge=bridge comment=defconf interface=ether5
(2) Change the interface to bridge (not ether2)
/ip address
add address=192.168.88.1/24 comment=defconf interface=ether2 network=\
192.168.88.0
Concur with Sindy, the FW rules are very non-standard looking, especially all the extra rules.
(3) Do not know the purpose of this input fw rule?
add action=accept chain=input comment="defconf: accept UDP traceroute" port=\
33434-33534 protocol=udp
(4) These rules I do not understand why there................. but perhaps they are fine...........
add action=accept chain=forward comment="defconf: accept ICMPv6" protocol=\
icmpv6
add action=accept chain=forward comment="defconf: accept HIP" protocol=139
add action=accept chain=forward comment="defconf: accept IKE" dst-port=\
500,4500 protocol=udp
add action=accept chain=forward comment="defconf: accept ipsec AH" protocol=\
ipsec-ah
add action=accept chain=forward comment="defconf: accept ipsec ESP" protocol=\
ipsec-esp
add action=accept chain=forward comment=\
"defconf: accept all that matches ipsec policy" ipsec-policy=in,ipsec
(5) Not sure I like this line......... (it looks like a default rule from the input chain subverted for use in the forward chain)
add action=drop chain=forward comment=\
"defconf: drop everything else not coming from LAN" in-interface-list=\
Simply change to.
add action=drop chain=input
(thus all traffic not approved by rules above this command will be blocked in the forward chain)
IN other words if you want to give folks access to the internet you will need to put it above this last rule.
bridge to wan
vlan to wan
etc.....
Last edited by anav on Fri May 15, 2020 10:14 pm, edited 4 times in total.
Re: Need help with firewall rules to prevent VLAN access to LAN
If those rules are your only ones, no host in LAN will be able to set up a connection anywhere else than to the Mikrotik itself, because the first rule in forward chain permit packets belonging to already established connections, but there is no rule which would permit packets capable of initiating a new connection. So e.g. if you want to allow all devices in LAN to set up connections to any server in the internet, modify the last action=drop rule in chain=forward to look the same like the action=drop rule in chain=input, i.e. add the same condition in-interface-list=!LAN to it.
Re: Need help with firewall rules to prevent VLAN access to LAN
Lots to fix before that Sindy, lets focus on the basics LOL but I am clueless on ipv6 rules LOL so will need help there!
Re: Need help with firewall rules to prevent VLAN access to LAN
Here is the latest and greatest config.
I have redone everything, all collected from different google search and my own understanding.
Again, my goal is to block VLAN 20 from talking to any other LAN device but only access to internet.
All firewall rules are default except this block rule.
Please advise.
Configuration below:
I have redone everything, all collected from different google search and my own understanding.
Again, my goal is to block VLAN 20 from talking to any other LAN device but only access to internet.
All firewall rules are default except this block rule.
After all the work from last couple of days I'm still failing to block VLAN20.#5.3 Block Secure/VLAN10 > VLAN20
add action=drop chain=forward in-interface=VLAN10-bridge out-interface=VLAN20-bridge
add action=drop chain=forward in-interface=VLAN4-bridge out-interface=VLAN20-bridge
#5.4 Block VLAN20 > VLAN4/VLAN20
add action=drop chain=forward in-interface=VLAN20-bridge out-interface=VLAN10-bridge
add action=drop chain=forward in-interface=VLAN20-bridge out-interface=VLAN4-bridge
#5.5 Block VLAN4 > VLAN10> VLAN4
add action=drop chain=forward in-interface=VLAN10-bridge out-interface=VLAN4-bridge
add action=drop chain=forward in-interface=VLAN4-bridge out-interface=VLAN10-bridge
Please advise.
Configuration below:
# may/16/2020 17:17:39 by RouterOS 6.46.6
# software id = S1MG-NEED
#
# model = RouterBOARD 750G r3
# serial number = XXXXXXXXXX
/interface bridge
add admin-mac=XXXXXXXXXX auto-mac=no comment=defconf name=\
1-default-bridge
add name=VLAN4-bridge
add name=VLAN10-bridge
add name=VLAN20-bridge
/interface ethernet
set [ find default-name=ether1 ] name=ether1-WAN
set [ find default-name=ether2 ] name=ether2-LAN-SWITCH
set [ find default-name=ether3 ] name=ether3-LAN
set [ find default-name=ether4 ] name=ether4-LAN
set [ find default-name=ether5 ] name=ether5-MGMT
/interface vlan
add interface=ether2-LAN-SWITCH name=VLAN4 vlan-id=4
add interface=ether2-LAN-SWITCH name=VLAN10 vlan-id=10
add interface=ether2-LAN-SWITCH name=VLAN20 vlan-id=20
/interface list
add comment=defconf name=WAN
add comment=defconf name=LAN
/ip pool
add name=dhcp ranges=192.168.88.10-192.168.88.200
add name=dhcp_pool4 ranges=192.168.4.2-192.168.4.200
add name=dhcp_pool5 ranges=192.168.10.10-192.168.10.100
add name=dhcp_pool6 ranges=10.0.20.10-10.0.20.200
/ip dhcp-server
add address-pool=dhcp disabled=no interface=1-default-bridge name=defconf
add address-pool=dhcp_pool4 disabled=no interface=VLAN4-bridge name=dhcp4
add address-pool=dhcp_pool5 disabled=no interface=VLAN10-bridge name=dhcp5
add address-pool=dhcp_pool6 disabled=no interface=VLAN20-bridge name=dhcp6
/user group
set full policy="local,telnet,ssh,ftp,reboot,read,write,policy,test,winbox,pas\
sword,web,sniff,sensitive,api,romon,dude,tikapp"
/interface bridge port
add bridge=1-default-bridge comment=defconf interface=ether2-LAN-SWITCH
add bridge=1-default-bridge comment=defconf interface=ether3-LAN
add bridge=1-default-bridge comment=defconf interface=ether4-LAN
add bridge=1-default-bridge comment=defconf interface=ether5-MGMT
add bridge=VLAN10-bridge interface=VLAN10
add bridge=VLAN20-bridge interface=VLAN20
add bridge=VLAN4-bridge interface=VLAN4
/ip neighbor discovery-settings
set discover-interface-list=none
/interface list member
add comment=defconf interface=1-default-bridge list=LAN
add comment=defconf interface=ether1-WAN list=WAN
/ip address
add address=192.168.88.1/24 comment=defconf interface=ether2-LAN-SWITCH \
network=192.168.88.0
add address=192.168.4.1/24 interface=VLAN4-bridge network=192.168.4.0
add address=192.168.10.1/24 interface=VLAN10-bridge network=192.168.10.0
add address=10.0.20.1/24 interface=VLAN20-bridge network=10.0.20.0
/ip cloud
set update-time=no
/ip dhcp-client
add comment=defconf disabled=no interface=ether1-WAN use-peer-dns=no
/ip dhcp-server network
add address=10.0.20.0/24 dns-server=8.8.8.8,8.8.4.4 gateway=10.0.20.1
add address=192.168.4.0/24 dns-server=192.168.4.2,208.67.222.123 gateway=\
192.168.4.1
add address=192.168.10.0/24 dns-server=8.8.8.8,8.8.4.4 gateway=192.168.10.1
add address=192.168.88.0/24 comment=defconf dns-server=8.8.8.8,8.8.4.4 \
gateway=192.168.88.1
/ip dns
set cache-size=3000KiB servers=8.8.8.8,208.67.222.123
/ip dns static
add address=192.168.88.1 comment=defconf name=router.lan
/ip firewall filter
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=accept chain=input comment=\
"defconf: accept to local loopback (for CAPsMAN)" dst-address=127.0.0.1
add action=drop chain=input comment="defconf: drop all not coming from LAN" \
in-interface-list=!LAN
add action=accept chain=forward comment="defconf: accept in ipsec policy" \
ipsec-policy=in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" \
ipsec-policy=out,ipsec
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related
add action=accept chain=forward comment=\
"defconf: accept established,related, untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=drop chain=forward comment=\
"defconf: drop all from WAN not DSTNATed" connection-nat-state=!dstnat \
connection-state=new in-interface-list=WAN
add action=drop chain=forward in-interface=VLAN10-bridge out-interface=\
VLAN20-bridge
add action=drop chain=forward in-interface=VLAN4-bridge out-interface=\
VLAN20-bridge
add action=drop chain=forward in-interface=VLAN20-bridge out-interface=\
VLAN10-bridge
add action=drop chain=forward in-interface=VLAN20-bridge out-interface=\
VLAN4-bridge
add action=drop chain=forward in-interface=VLAN10-bridge out-interface=\
VLAN4-bridge
add action=drop chain=forward in-interface=VLAN4-bridge out-interface=\
VLAN10-bridge
/ip firewall nat
add action=masquerade chain=srcnat comment="defconf: masquerade" \
ipsec-policy=out,none out-interface-list=WAN
add action=masquerade chain=srcnat
/ip service
set telnet disabled=yes
set ftp disabled=yes
set www disabled=yes
set ssh port=2200
set api disabled=yes
set winbox address=192.168.88.0/24
set api-ssl disabled=yes
/ipv6 firewall address-list
add address=::/128 comment="defconf: unspecified address" list=bad_ipv6
add address=::1/128 comment="defconf: lo" list=bad_ipv6
add address=fec0::/10 comment="defconf: site-local" list=bad_ipv6
add address=::ffff:0.0.0.0/96 comment="defconf: ipv4-mapped" list=bad_ipv6
add address=::/96 comment="defconf: ipv4 compat" list=bad_ipv6
add address=100::/64 comment="defconf: discard only " list=bad_ipv6
add address=2001:db8::/32 comment="defconf: documentation" list=bad_ipv6
add address=2001:10::/28 comment="defconf: ORCHID" list=bad_ipv6
add address=3ffe::/16 comment="defconf: 6bone" list=bad_ipv6
add address=::224.0.0.0/100 comment="defconf: other" list=bad_ipv6
add address=::127.0.0.0/104 comment="defconf: other" list=bad_ipv6
add address=::/104 comment="defconf: other" list=bad_ipv6
add address=::255.0.0.0/104 comment="defconf: other" list=bad_ipv6
/ipv6 firewall filter
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMPv6" protocol=\
icmpv6
add action=accept chain=input comment="defconf: accept UDP traceroute" port=\
33434-33534 protocol=udp
add action=accept chain=input comment=\
"defconf: accept DHCPv6-Client prefix delegation." dst-port=546 protocol=\
udp src-address=fe80::/10
add action=accept chain=input comment="defconf: accept IKE" dst-port=500,4500 \
protocol=udp
add action=accept chain=input comment="defconf: accept ipsec AH" protocol=\
ipsec-ah
add action=accept chain=input comment="defconf: accept ipsec ESP" protocol=\
ipsec-esp
add action=accept chain=input comment=\
"defconf: accept all that matches ipsec policy" ipsec-policy=in,ipsec
add action=drop chain=input comment=\
"defconf: drop everything else not coming from LAN" in-interface-list=\
!LAN
add action=accept chain=forward comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=drop chain=forward comment=\
"defconf: drop packets with bad src ipv6" src-address-list=bad_ipv6
add action=drop chain=forward comment=\
"defconf: drop packets with bad dst ipv6" dst-address-list=bad_ipv6
add action=drop chain=forward comment="defconf: rfc4890 drop hop-limit=1" \
hop-limit=equal:1 protocol=icmpv6
add action=accept chain=forward comment="defconf: accept ICMPv6" protocol=\
icmpv6
add action=accept chain=forward comment="defconf: accept HIP" protocol=139
add action=accept chain=forward comment="defconf: accept IKE" dst-port=\
500,4500 protocol=udp
add action=accept chain=forward comment="defconf: accept ipsec AH" protocol=\
ipsec-ah
add action=accept chain=forward comment="defconf: accept ipsec ESP" protocol=\
ipsec-esp
add action=accept chain=forward comment=\
"defconf: accept all that matches ipsec policy" ipsec-policy=in,ipsec
add action=drop chain=forward comment=\
"defconf: drop everything else not coming from LAN" in-interface-list=\
!LAN
/system clock
set time-zone-name=America/New_York
/system identity
set name=router
/system ntp client
set enabled=yes primary-ntp=38.229.71.1 secondary-ntp=199.180.133.100
/system ntp server
set broadcast=yes enabled=yes
/tool bandwidth-server
set enabled=no
/tool mac-server
set allowed-interface-list=none
/tool mac-server mac-winbox
set allowed-interface-list=none
/tool mac-server ping
set enabled=no
Re: Need help with firewall rules to prevent VLAN access to LAN
The reason is your setup is way more complicated that necessary and you have bridged within bridges and misconfigured vlans etc. In other words, nothing is going to work correctly.
USE ONE BRIDGE ONLY
Follow this reference, and you will be fine!
viewtopic.php?f=13&t=143620
USE ONE BRIDGE ONLY
Follow this reference, and you will be fine!
viewtopic.php?f=13&t=143620
Re: Need help with firewall rules to prevent VLAN access to LAN
SOMETHING LIKE>>>>>>>>>>>> Should get you started, much simplified. But only attempt this after reading the above linked article.
/interface bridge
add admin-mac=XXXXXXXXXX auto-mac=no comment=defconf name=\
1-default-bridge
/interface ethernet
set [ find default-name=ether1 ] name=ether1-WAN
set [ find default-name=ether2 ] name=ether2-LAN-SWITCH
set [ find default-name=ether3 ] name=ether3-LAN
set [ find default-name=ether4 ] name=ether4-LAN
set [ find default-name=ether5 ] name=ether5-MGMT
/interface vlan
add interface=1-default-bridge name=homeVLAN vlan-id=100
add interface=1-default-bridge name=VLANfour vlan-id=4
add interface=1-default-bridge name=VLANten vlan-id=10
add interface=1-default-bridge name=VLANtwenty vlan-id=20
/interface list
add comment=defconf name=WAN
add comment=defconf name=LAN
/ip pool
add name=dhcp_home ranges=192.168.88.10-192.168.88.200
add name=dhcp_pool4 ranges=192.168.4.2-192.168.4.200
add name=dhcp_pool10 ranges=192.168.10.10-192.168.10.100
add name=dhcp_pool20 ranges=10.0.20.10-10.0.20.200
/ip dhcp-server
add address-pool=dhcp_home disabled=no interface=homeVLAN name=dchphome
add address-pool=dhcp_pool4 disabled=no interface=VLANfour name=dhcp4
add address-pool=dhcp_pool5 disabled=no interface=VLANten name=dhcp5
add address-pool=dhcp_pool6 disabled=no interface=VLANtwenty name=dhcp6
IF port carries more than one VLAN its usually a trunk port (like ether2 for example to a smart switch or smart AP etc)
IF port carries a VLAN to a device that is unable to read vlan tags its an access port Will assume 3-4 are such ports)
/interface bridge port
add bridge=1-default-bridge comment=defconf interface=ether2-LAN-SWITCH ingress-filtering=yes (lets assume carrying 100,4,10,20)
add bridge=1-default-bridge comment=defconf interface=ether3-LAN pvid=100 admit-only-untagged-and-priority-tagged
add bridge=1-default-bridge comment=defconf interface=ether4-LAN pvid=100 admit-only-untagged-and-priority-tagged
add bridge=1-default-bridge comment=defconf interface=ether5-MGMT ingress-filtering=yes (lets assume carrying 100,20)
/interface bridge vlan
add bridge=1-default-bridge tagged=1-default-bridge, ether2-LAN-SWITCH,ether5-MGMT untagged=ether3-LAN,ether4-LAnN vlan-ids=100
add bridge=1-default-bridge tagged=1-default-bridge, ether2-LAN-SWITCH,ether5-MGMT vlan-ids=20
add bridge=1-default-bridge tagged=1-default-bridge, ether2-LAN-SWITCH vlan-ids=4
/interface list member
add comment=defconf interface=vlanhome list=LAN
add interface=VLANfour list=LAN
add interface=VLANten list=LAN
add interface=VLANtwenty list=LAN
add comment=defconf interface=ether1-WAN list=WAN
/ip address
add address=192.168.88.1/24 comment=defconf interface=homeVLAN \
network=192.168.88.0
add address=192.168.4.1/24 interface=VLANfour network=192.168.4.0
add address=192.168.10.1/24 interface=VLANten network=192.168.10.0
add address=10.0.20.1/24 interface=VLANtwenty network=10.0.20.0
/ip dhcp-server network
add address=10.0.20.0/24 dns-server=8.8.8.8,8.8.4.4 gateway=10.0.20.1
add address=192.168.4.0/24 dns-server=192.168.4.2,208.67.222.123 gateway=\
192.168.4.1
add address=192.168.10.0/24 dns-server=8.8.8.8,8.8.4.4 gateway=192.168.10.1
add address=192.168.88.0/24 comment=defconf dns-server=8.8.8.8,8.8.4.4 \
gateway=192.168.88.1
/ip firewall filter
{input chain}
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=accept chain=input comment=\
"defconf: accept to local loopback (for CAPsMAN)" dst-address=127.0.0.1
add action=drop chain=input comment="defconf: drop all not coming from LAN" \
in-interface-list=!LAN
{forward chain}
add action=accept chain=forward comment="defconf: accept in ipsec policy" \
ipsec-policy=in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" \
ipsec-policy=out,ipsec
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related
add action=accept chain=forward comment=\
"defconf: accept established,related, untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
USER DEFINED RULES
add action=accept chain=forward comment="Allow port forwarding" \
connection-state=new connection-nat-stat=dstnat in-interface-list=WAN
add action=accept chain=forward comment="Allow internet access" \
in-interface-list=LAN out-interface-list=WAN
add action=drop chain=forward comment="LastRule-Drop all else"
/ip firewall nat ( only need one masquerade rule the first(default) one! )
add action=masquerade chain=srcnat comment="defconf: masquerade" \
ipsec-policy=out,none out-interface-list=WAN
/interface bridge
add admin-mac=XXXXXXXXXX auto-mac=no comment=defconf name=\
1-default-bridge
/interface ethernet
set [ find default-name=ether1 ] name=ether1-WAN
set [ find default-name=ether2 ] name=ether2-LAN-SWITCH
set [ find default-name=ether3 ] name=ether3-LAN
set [ find default-name=ether4 ] name=ether4-LAN
set [ find default-name=ether5 ] name=ether5-MGMT
/interface vlan
add interface=1-default-bridge name=homeVLAN vlan-id=100
add interface=1-default-bridge name=VLANfour vlan-id=4
add interface=1-default-bridge name=VLANten vlan-id=10
add interface=1-default-bridge name=VLANtwenty vlan-id=20
/interface list
add comment=defconf name=WAN
add comment=defconf name=LAN
/ip pool
add name=dhcp_home ranges=192.168.88.10-192.168.88.200
add name=dhcp_pool4 ranges=192.168.4.2-192.168.4.200
add name=dhcp_pool10 ranges=192.168.10.10-192.168.10.100
add name=dhcp_pool20 ranges=10.0.20.10-10.0.20.200
/ip dhcp-server
add address-pool=dhcp_home disabled=no interface=homeVLAN name=dchphome
add address-pool=dhcp_pool4 disabled=no interface=VLANfour name=dhcp4
add address-pool=dhcp_pool5 disabled=no interface=VLANten name=dhcp5
add address-pool=dhcp_pool6 disabled=no interface=VLANtwenty name=dhcp6
IF port carries more than one VLAN its usually a trunk port (like ether2 for example to a smart switch or smart AP etc)
IF port carries a VLAN to a device that is unable to read vlan tags its an access port Will assume 3-4 are such ports)
/interface bridge port
add bridge=1-default-bridge comment=defconf interface=ether2-LAN-SWITCH ingress-filtering=yes (lets assume carrying 100,4,10,20)
add bridge=1-default-bridge comment=defconf interface=ether3-LAN pvid=100 admit-only-untagged-and-priority-tagged
add bridge=1-default-bridge comment=defconf interface=ether4-LAN pvid=100 admit-only-untagged-and-priority-tagged
add bridge=1-default-bridge comment=defconf interface=ether5-MGMT ingress-filtering=yes (lets assume carrying 100,20)
/interface bridge vlan
add bridge=1-default-bridge tagged=1-default-bridge, ether2-LAN-SWITCH,ether5-MGMT untagged=ether3-LAN,ether4-LAnN vlan-ids=100
add bridge=1-default-bridge tagged=1-default-bridge, ether2-LAN-SWITCH,ether5-MGMT vlan-ids=20
add bridge=1-default-bridge tagged=1-default-bridge, ether2-LAN-SWITCH vlan-ids=4
/interface list member
add comment=defconf interface=vlanhome list=LAN
add interface=VLANfour list=LAN
add interface=VLANten list=LAN
add interface=VLANtwenty list=LAN
add comment=defconf interface=ether1-WAN list=WAN
/ip address
add address=192.168.88.1/24 comment=defconf interface=homeVLAN \
network=192.168.88.0
add address=192.168.4.1/24 interface=VLANfour network=192.168.4.0
add address=192.168.10.1/24 interface=VLANten network=192.168.10.0
add address=10.0.20.1/24 interface=VLANtwenty network=10.0.20.0
/ip dhcp-server network
add address=10.0.20.0/24 dns-server=8.8.8.8,8.8.4.4 gateway=10.0.20.1
add address=192.168.4.0/24 dns-server=192.168.4.2,208.67.222.123 gateway=\
192.168.4.1
add address=192.168.10.0/24 dns-server=8.8.8.8,8.8.4.4 gateway=192.168.10.1
add address=192.168.88.0/24 comment=defconf dns-server=8.8.8.8,8.8.4.4 \
gateway=192.168.88.1
/ip firewall filter
{input chain}
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=accept chain=input comment=\
"defconf: accept to local loopback (for CAPsMAN)" dst-address=127.0.0.1
add action=drop chain=input comment="defconf: drop all not coming from LAN" \
in-interface-list=!LAN
{forward chain}
add action=accept chain=forward comment="defconf: accept in ipsec policy" \
ipsec-policy=in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" \
ipsec-policy=out,ipsec
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related
add action=accept chain=forward comment=\
"defconf: accept established,related, untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
USER DEFINED RULES
add action=accept chain=forward comment="Allow port forwarding" \
connection-state=new connection-nat-stat=dstnat in-interface-list=WAN
add action=accept chain=forward comment="Allow internet access" \
in-interface-list=LAN out-interface-list=WAN
add action=drop chain=forward comment="LastRule-Drop all else"
/ip firewall nat ( only need one masquerade rule the first(default) one! )
add action=masquerade chain=srcnat comment="defconf: masquerade" \
ipsec-policy=out,none out-interface-list=WAN
Re: Need help with firewall rules to prevent VLAN access to LAN
@anav
Thank you.
I played around with your configuration and got it up and running.
Before I dive deep into this I have a question.
Using a managed switch I 'm able to access all the VLAN. How do I supposed to access IP on the ether5 MGMT port on the router?
I really appreciate all the help you folks provide to "wanna bes" like me in this forum.
Thank you.
I played around with your configuration and got it up and running.
Before I dive deep into this I have a question.
Using a managed switch I 'm able to access all the VLAN. How do I supposed to access IP on the ether5 MGMT port on the router?
I really appreciate all the help you folks provide to "wanna bes" like me in this forum.
Re: Need help with firewall rules to prevent VLAN access to LAN
Now you are talking.
Your question is a USE CASE, but your description of it is poor.
In detail explain what your role is, in relation to the network, (what group of users do you belong to) and what is it that you need to accomplish.
Then we will look at how to do that most efficiently in the config.
The idea being that you identify all the use cases before starting a config............
In this case, also detail where you will be located (in which subnet or vlan) in attempting to reach port 5, and any vlans its holding...........
Your question is a USE CASE, but your description of it is poor.
In detail explain what your role is, in relation to the network, (what group of users do you belong to) and what is it that you need to accomplish.
Then we will look at how to do that most efficiently in the config.
The idea being that you identify all the use cases before starting a config............
In this case, also detail where you will be located (in which subnet or vlan) in attempting to reach port 5, and any vlans its holding...........
Re: Need help with firewall rules to prevent VLAN access to LAN
There is no IP address attached to the ether5-MGMT port as such, and in @anav's configuration suggestion, ether5's pvid is 1 like the bridge's own one, so calling the ether5 "MGMT" is slightly misleading. The idea is typically that one port of the router is dedicated to management and it is impossible to access the management services of the router from anywhere else, which is clearly not the case here.Using a managed switch I 'm able to access all the VLAN. How do I supposed to access IP on the ether5 MGMT port on the router?
Since your currently running configuration is likely some fusion of the original one and @anav's proposal (where no /interface vlan can be found), without posting it, you'll only get guesses.
So as always:
- post the anonymized configuration
- explain the particular goal you want to achieve
- describe what exactly does not work
Re: Need help with firewall rules to prevent VLAN access to LAN
Concur Sindy, one had to make a few assumptions based on incomplete information and my assumption was the following
a. the OP or admin has his pc located on etherport 5 and is on vlan 20 .
IF true then he simply needs two rules to add to his firewall rules to make it all work
input chain
rule to allow OP access to router for configuration purposes
add action=accept chain=input in-interface=VLANtwenty src-address-list=adminaccess *
forward chain
rule to allow OP access to all other vlans
add action=accept chain=forward in-interface=VLANtwenty src-address-list=adminaccess * out-interface-list=LAN
* where address list
add IP (ops deskstop - static) list=adminaccess
add IP (ops ipad - static) list=adminaccess
a. the OP or admin has his pc located on etherport 5 and is on vlan 20 .
IF true then he simply needs two rules to add to his firewall rules to make it all work
input chain
rule to allow OP access to router for configuration purposes
add action=accept chain=input in-interface=VLANtwenty src-address-list=adminaccess *
forward chain
rule to allow OP access to all other vlans
add action=accept chain=forward in-interface=VLANtwenty src-address-list=adminaccess * out-interface-list=LAN
* where address list
add IP (ops deskstop - static) list=adminaccess
add IP (ops ipad - static) list=adminaccess
Re: Need help with firewall rules to prevent VLAN access to LAN
In summary, agree that the managment vlan20 and port designation of mngmt for port 5 are probably not needed.
I would guess that the OP is really on the HOME user vlan10.
My two rules still work however to ensure that only the OP access the router for config purposes and only the OP can access the other VLANs.
just change in-interface from vlan20 to in-interface to vlan10 for example and the same is accomplished.
The management vlan is an entity for business that I dont quite understand...........
I would guess that the OP is really on the HOME user vlan10.
My two rules still work however to ensure that only the OP access the router for config purposes and only the OP can access the other VLANs.
just change in-interface from vlan20 to in-interface to vlan10 for example and the same is accomplished.
The management vlan is an entity for business that I dont quite understand...........
Re: Need help with firewall rules to prevent VLAN access to LAN
@anav @sindy
Thanks
here are some answers.
This is for my home use for 4 of us. I have an Unifi AP-AC lite with 3 ssid for each VLANs. My current router is an EdgerouterX. I want to replace this router with Mikrotik Hex.
My main lan is VLAN4. Most of my day to day stuff like PC, laptop, unifi ac-lite access point etc connected to it. Some of the devices in VLAN4 are using static ip like my printer, pi-hole, wireguard vpn etc. I have Pi-hole ad blocker setup to block ads in VLAN4 which brings me to my need for VLAN10. My daughter works from home now and some of her client sites are blocked by pi-hole. So, I'm using VLAN10 with google DNS and by-passing pi-hole DNS completely. So this VLAN10 is only used by her in her home office.
Everything else, like Roku, iptv, camera, IOT are using VLAN20.
Therefore, I really need only VLAV20 blocked from other VLANs.
Here is my config I have setup using @anav help.
Thanks
here are some answers.
This is for my home use for 4 of us. I have an Unifi AP-AC lite with 3 ssid for each VLANs. My current router is an EdgerouterX. I want to replace this router with Mikrotik Hex.
My main lan is VLAN4. Most of my day to day stuff like PC, laptop, unifi ac-lite access point etc connected to it. Some of the devices in VLAN4 are using static ip like my printer, pi-hole, wireguard vpn etc. I have Pi-hole ad blocker setup to block ads in VLAN4 which brings me to my need for VLAN10. My daughter works from home now and some of her client sites are blocked by pi-hole. So, I'm using VLAN10 with google DNS and by-passing pi-hole DNS completely. So this VLAN10 is only used by her in her home office.
Everything else, like Roku, iptv, camera, IOT are using VLAN20.
Therefore, I really need only VLAV20 blocked from other VLANs.
Here is my config I have setup using @anav help.
/interface bridge
add admin-mac=XXXXXXX auto-mac=no comment=defconf name=\
1-default-bridge
/interface ethernet
set [ find default-name=ether1 ] name=ether1-WAN
set [ find default-name=ether2 ] name=ether2-LAN-SWITCH
set [ find default-name=ether3 ] name=ether3-LAN
set [ find default-name=ether4 ] name=ether4-LAN
set [ find default-name=ether5 ] name=ether5-MGMT
/interface vlan
add interface=1-default-bridge name=HomeVLAN vlan-id=99
add interface=1-default-bridge name=VLAN4 vlan-id=4
add interface=1-default-bridge name=VLAN10 vlan-id=10
add interface=1-default-bridge name=VLAN20 vlan-id=20
/interface list
add comment=defconf name=WAN
add comment=defconf name=LAN
/ip pool
add name=dhcp_home ranges=192.168.99.10-192.168.99.100
add name=dhcp_pool4 ranges=192.168.4.10-192.168.4.200
add name=dhcp_pool10 ranges=192.168.10.10-192.168.10.100
add name=dhcp_pool20 ranges=10.0.20.2-10.0.20.10
/ip dhcp-server
add address-pool=dhcp_home disabled=no interface=HomeVLAN name=dhcphome
add address-pool=dhcp_pool4 disabled=no interface=VLAN4 name=dhcp4
add address-pool=dhcp_pool10 disabled=no interface=VLAN10 name=dhcp10
add address-pool=dhcp_pool20 disabled=no interface=VLAN20 name=dhcp20
/interface bridge port
add bridge=1-default-bridge comment=defconf ingress-filtering=yes interface=\
ether2-LAN-SWITCH
add bridge=1-default-bridge comment=defconf interface=ether3-LAN pvid=99
add bridge=1-default-bridge comment=defconf interface=ether4-LAN pvid=99
add bridge=1-default-bridge comment=defconf ingress-filtering=yes interface=\
ether5-MGMT
/interface bridge vlan
add bridge=1-default-bridge tagged=\
1-default-bridge,ether2-LAN-SWITCH,ether5-MGMT untagged=\
ether3-LAN,ether4-LAN vlan-ids=99
add bridge=1-default-bridge tagged=\
1-default-bridge,ether2-LAN-SWITCH,ether5-MGMT vlan-ids=20
add bridge=1-default-bridge tagged=1-default-bridge,ether2-LAN-SWITCH \
vlan-ids=4
/interface list member
add comment=defconf interface=HomeVLAN list=LAN
add interface=VLAN4 list=LAN
add interface=VLAN10 list=LAN
add interface=VLAN20 list=LAN
add comment=defconf interface=ether1-WAN list=WAN
add interface=1-default-bridge list=LAN
/ip address
add address=192.168.99.1/24 comment=defconf interface=HomeVLAN network=\
192.168.99.0
add address=192.168.4.1/24 interface=VLAN4 network=192.168.4.0
add address=192.168.10.1/24 interface=VLAN10 network=192.168.10.0
add address=10.0.20.1/24 interface=VLAN20 network=10.0.20.0
/ip dhcp-client
add disabled=no interface=ether1-WAN
/ip dhcp-server network
add address=10.0.20.0/24 dns-server=8.8.8.8,8.8.4.4 gateway=10.0.20.1
add address=192.168.4.0/24 dns-server=192.168.4.2,208.67.222.123 gateway=\
192.168.4.1
add address=192.168.10.0/24 dns-server=8.8.8.8,8.8.4.4 gateway=192.168.10.1
add address=192.168.99.0/24 comment=defconf dns-server=8.8.8.8,8.8.4.4 \
gateway=192.168.99.1
/ip dns
set servers=8.8.8.8,8.8.4.4
/ip firewall filter
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=accept chain=input comment=\
"defconf: accept to local loopback (for CAPsMAN)" dst-address=127.0.0.1
add action=drop chain=input comment="defconf: drop all not coming from LAN" \
in-interface-list=!LAN
add action=accept chain=forward comment="defconf: accept in ipsec policy" \
ipsec-policy=in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" \
ipsec-policy=out,ipsec
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related
add action=accept chain=forward comment=\
"defconf: accept established,related, untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=accept chain=forward comment="Allow port forwarding" \
connection-nat-state=dstnat connection-state=new in-interface-list=WAN
add action=accept chain=forward comment="Allow internet access" \
in-interface-list=LAN out-interface-list=WAN
add action=drop chain=forward comment="LastRule-Drop all else"
/ip firewall nat
add action=masquerade chain=srcnat comment="defconf: masquerade" \
ipsec-policy=out,none out-interface-list=WAN
Re: Need help with firewall rules to prevent VLAN access to LAN
Please provide a diagram to show what is hooked up to which port.
For example its not clear where the unifi is located? connected to smart switch on eth2?
Where is vlan10 connected to??
For example its not clear where the unifi is located? connected to smart switch on eth2?
Where is vlan10 connected to??
Re: Need help with firewall rules to prevent VLAN access to LAN
Here's a diagram.
All I need is VLAN20 not see any LAN resource.
Please ask if any confusion.
Eth5 is MGMT port.
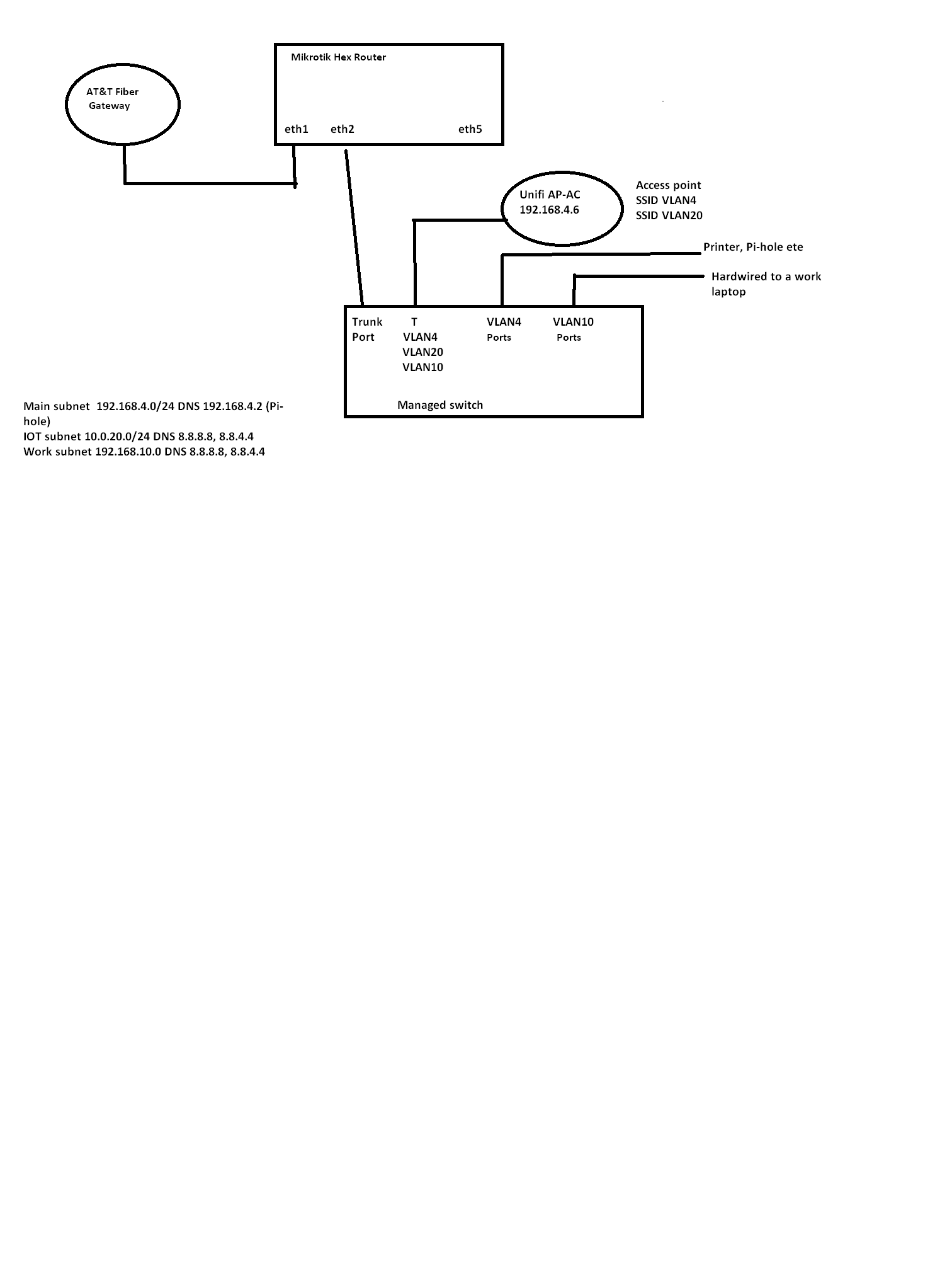
All I need is VLAN20 not see any LAN resource.
Please ask if any confusion.
Eth5 is MGMT port.
Re: Need help with firewall rules to prevent VLAN access to LAN
Okay with the assumptions from your diagram (vlan4 is your homeLAN) and there is nothing on eth3,4,5
Removed unnecessary stuff...........
So at this point, if vlans are talking to each other its because your managed switch is not configured properly.
The firewall rules prevent the router from allowing any user to attempt to reach the other vlan.
The fact that they are in VLANs prevents L2 crosstalk.
I have not seen your bridge rule that includes vlan filtering rule though ------- It is a last step in the config (ensure safe mode button is enabled as for some reason this step can cause the router to burp more than other changes LOL )
/interface bridge
add admin-mac= auto-mac=no comment=defconf name=1-default-bridge \
vlan-filtering=yes
/interface bridge
add admin-mac=XXXXXXX auto-mac=no comment=defconf name=\
1-default-bridge ??????????
/interface ethernet
set [ find default-name=ether1 ] name=ether1-WAN
set [ find default-name=ether2 ] name=ether2-LAN-SWITCH
/interface vlan
add interface=1-default-bridge name=VLAN4 vlan-id=4
add interface=1-default-bridge name=VLAN10 vlan-id=10
add interface=1-default-bridge name=VLAN20 vlan-id=20
/interface list
add comment=defconf name=WAN
add comment=defconf name=LAN
/ip pool
add name=dhcp_pool4 ranges=192.168.4.10-192.168.4.200
add name=dhcp_pool10 ranges=192.168.10.10-192.168.10.100
add name=dhcp_pool20 ranges=10.0.20.2-10.0.20.10
/ip dhcp-server
add address-pool=dhcp_pool4 disabled=no interface=VLAN4 name=dhcp4
add address-pool=dhcp_pool10 disabled=no interface=VLAN10 name=dhcp10
add address-pool=dhcp_pool20 disabled=no interface=VLAN20 name=dhcp20
/interface bridge port
add bridge=1-default-bridge comment=defconf ingress-filtering=yes interface=\
ether2-LAN-SWITCH
/interface bridge vlan
add bridge=1-default-bridge tagged=1-default-bridge,ether2-LAN-SWITCH vlan-ids=4,10,20
/interface list member
add interface=VLAN4 list=LAN
add interface=VLAN10 list=LAN
add interface=VLAN20 list=LAN
add comment=defconf interface=ether1-WAN list=WAN
/ip address
add address=192.168.4.1/24 interface=VLAN4 network=192.168.4.0
add address=192.168.10.1/24 interface=VLAN10 network=192.168.10.0
add address=10.0.20.1/24 interface=VLAN20 network=10.0.20.0
/ip dhcp-client
add disabled=no interface=ether1-WAN
/ip dhcp-server network
add address=10.0.20.0/24 dns-server=8.8.8.8,8.8.4.4 gateway=10.0.20.1
add address=192.168.4.0/24 dns-server=192.168.4.2,208.67.222.123 gateway=\
192.168.4.1
add address=192.168.10.0/24 dns-server=8.8.8.8,8.8.4.4 gateway=192.168.10.1
/ip dns
set servers=8.8.8.8,8.8.4.4
/ip firewall filter
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=accept chain=input comment=\
"defconf: accept to local loopback (for CAPsMAN)" dst-address=127.0.0.1
add action=drop chain=input comment="defconf: drop all not coming from LAN" \
in-interface-list=!LAN
add action=accept chain=forward comment="defconf: accept in ipsec policy" \
ipsec-policy=in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" \
ipsec-policy=out,ipsec
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related
add action=accept chain=forward comment=\
"defconf: accept established,related, untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=accept chain=forward comment="Allow port forwarding" \
connection-nat-state=dstnat connection-state=new in-interface-list=WAN
add action=accept chain=forward comment="Allow internet access" \
in-interface-list=LAN out-interface-list=WAN
add action=drop chain=forward comment="LastRule-Drop all else"
/ip firewall nat
add action=masquerade chain=srcnat comment="defconf: masquerade" \
ipsec-policy=out,none out-interface-list=WAN
Removed unnecessary stuff...........
So at this point, if vlans are talking to each other its because your managed switch is not configured properly.
The firewall rules prevent the router from allowing any user to attempt to reach the other vlan.
The fact that they are in VLANs prevents L2 crosstalk.
I have not seen your bridge rule that includes vlan filtering rule though ------- It is a last step in the config (ensure safe mode button is enabled as for some reason this step can cause the router to burp more than other changes LOL )
/interface bridge
add admin-mac= auto-mac=no comment=defconf name=1-default-bridge \
vlan-filtering=yes
/interface bridge
add admin-mac=XXXXXXX auto-mac=no comment=defconf name=\
1-default-bridge ??????????
/interface ethernet
set [ find default-name=ether1 ] name=ether1-WAN
set [ find default-name=ether2 ] name=ether2-LAN-SWITCH
/interface vlan
add interface=1-default-bridge name=VLAN4 vlan-id=4
add interface=1-default-bridge name=VLAN10 vlan-id=10
add interface=1-default-bridge name=VLAN20 vlan-id=20
/interface list
add comment=defconf name=WAN
add comment=defconf name=LAN
/ip pool
add name=dhcp_pool4 ranges=192.168.4.10-192.168.4.200
add name=dhcp_pool10 ranges=192.168.10.10-192.168.10.100
add name=dhcp_pool20 ranges=10.0.20.2-10.0.20.10
/ip dhcp-server
add address-pool=dhcp_pool4 disabled=no interface=VLAN4 name=dhcp4
add address-pool=dhcp_pool10 disabled=no interface=VLAN10 name=dhcp10
add address-pool=dhcp_pool20 disabled=no interface=VLAN20 name=dhcp20
/interface bridge port
add bridge=1-default-bridge comment=defconf ingress-filtering=yes interface=\
ether2-LAN-SWITCH
/interface bridge vlan
add bridge=1-default-bridge tagged=1-default-bridge,ether2-LAN-SWITCH vlan-ids=4,10,20
/interface list member
add interface=VLAN4 list=LAN
add interface=VLAN10 list=LAN
add interface=VLAN20 list=LAN
add comment=defconf interface=ether1-WAN list=WAN
/ip address
add address=192.168.4.1/24 interface=VLAN4 network=192.168.4.0
add address=192.168.10.1/24 interface=VLAN10 network=192.168.10.0
add address=10.0.20.1/24 interface=VLAN20 network=10.0.20.0
/ip dhcp-client
add disabled=no interface=ether1-WAN
/ip dhcp-server network
add address=10.0.20.0/24 dns-server=8.8.8.8,8.8.4.4 gateway=10.0.20.1
add address=192.168.4.0/24 dns-server=192.168.4.2,208.67.222.123 gateway=\
192.168.4.1
add address=192.168.10.0/24 dns-server=8.8.8.8,8.8.4.4 gateway=192.168.10.1
/ip dns
set servers=8.8.8.8,8.8.4.4
/ip firewall filter
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=accept chain=input comment=\
"defconf: accept to local loopback (for CAPsMAN)" dst-address=127.0.0.1
add action=drop chain=input comment="defconf: drop all not coming from LAN" \
in-interface-list=!LAN
add action=accept chain=forward comment="defconf: accept in ipsec policy" \
ipsec-policy=in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" \
ipsec-policy=out,ipsec
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related
add action=accept chain=forward comment=\
"defconf: accept established,related, untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=accept chain=forward comment="Allow port forwarding" \
connection-nat-state=dstnat connection-state=new in-interface-list=WAN
add action=accept chain=forward comment="Allow internet access" \
in-interface-list=LAN out-interface-list=WAN
add action=drop chain=forward comment="LastRule-Drop all else"
/ip firewall nat
add action=masquerade chain=srcnat comment="defconf: masquerade" \
ipsec-policy=out,none out-interface-list=WAN
Re: Need help with firewall rules to prevent VLAN access to LAN
Ok, I made some changes to my scripts and I think it's what I really want.
Only sticking points are, not sure if the firewall rules are correct, secondly, should I be able to enable on "1-default" vlan-filtering? I could not get the ether5 to communicate if I enabled filtering.
Only sticking points are, not sure if the firewall rules are correct, secondly, should I be able to enable on "1-default" vlan-filtering? I could not get the ether5 to communicate if I enabled filtering.
Code: Select all
/interface bridge
add admin-mac=00:00:00:82:05:00 auto-mac=no comment=defconf name=1-bridge
add ingress-filtering=yes name=MGMT vlan-filtering=yes
/interface vlan
add interface=1-bridge name=VLAN4 vlan-id=4
add interface=1-bridge name=VLAN10 vlan-id=10
add interface=1-bridge name=VLAN20 vlan-id=20
add interface=MGMT name=VLAN99 vlan-id=99
/interface list
add name=WAN
add name=LAN
/ip pool
add name=dhcp_pool0 ranges=192.168.4.10-192.168.4.200
add name=dhcp_pool1 ranges=192.168.10.10-192.168.10.100
add name=dhcp_pool2 ranges=10.0.20.10-10.0.20.200
add name=dhcp ranges=192.168.99.10-192.168.99.15
/ip dhcp-server
add address-pool=dhcp_pool0 disabled=no interface=VLAN4 name=dhcp1
add address-pool=dhcp_pool1 disabled=no interface=VLAN10 name=dhcp2
add address-pool=dhcp_pool2 disabled=no interface=VLAN20 name=dhcp3
add address-pool=dhcp disabled=no interface=MGMT name=dhcp4
/interface bridge port
add bridge=1-bridge interface=ether5
add bridge=MGMT interface=ether2
/ip neighbor discovery-settings
set discover-interface-list=none
/interface list member
add comment=defconf interface=ether1 list=WAN
add interface=MGMT list=LAN
add interface=VLAN4 list=LAN
add interface=VLAN10 list=LAN
add interface=VLAN20 list=LAN
add comment=defconf interface=1-bridge list=LAN
/ip address
add address=192.168.4.1/24 interface=VLAN4 network=192.168.4.0
add address=192.168.10.1/24 interface=VLAN10 network=192.168.10.0
add address=10.0.20.1/24 interface=VLAN20 network=10.0.20.0
add address=192.168.99.1/24 interface=ether2 network=192.168.99.0
/ip cloud
set update-time=no
/ip dhcp-client
add disabled=no interface=ether1
/ip dhcp-server network
add address=10.0.20.0/24 dns-server=8.8.8.8,8.8.4.4 gateway=10.0.20.1 \
netmask=24
add address=192.168.4.0/24 dns-server=192.168.4.2,208.67.222.123 gateway=\
192.168.4.1 netmask=24
add address=192.168.10.0/24 dns-server=8.8.8.8,8.8.4.4 gateway=192.168.10.1 \
netmask=24
add address=192.168.99.0/24 dns-server=192.168.4.2,8.8.8.8 gateway=\
192.168.99.1 netmask=24
/ip dns
set cache-size=3000KiB servers=192.168.4.2,208.67.222.12
/ip firewall address-list
add address=10.0.20.1-10.0.20.200 list="IoT Users"
/ip firewall filter
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=accept chain=input comment=\
"defconf: accept to local loopback (for CAPsMAN)" dst-address=127.0.0.1
add action=drop chain=input comment="defconf: drop all not coming from LAN" \
in-interface-list=!LAN
add action=accept chain=forward comment="defconf: accept in ipsec policy" \
ipsec-policy=in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" \
ipsec-policy=out,ipsec
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related
add action=accept chain=forward comment=\
"defconf: accept established,related, untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=accept chain=forward comment="Allow port forwarding" \
connection-nat-state=dstnat connection-state=new in-interface-list=WAN
add action=accept chain=forward comment="Allow internet access" \
in-interface-list=LAN out-interface-list=WAN
add action=drop chain=forward comment="LastRule-Drop all else"
add action=drop chain=input comment="Block IoT Local Ports" dst-address=\
192.168.99.1 dst-port=80,21,22,23,8291,2200 protocol=tcp \
src-address-list="IoT Users"
add action=drop chain=input comment="Block IoT VLAN4" dst-address=\
192.168.4.0/24 src-address-list="IoT Users"
add action=drop chain=input comment="Block Iot VLAN10" dst-address=\
192.168.10.0/24 src-address-list="IoT Users"
/ip firewall nat
add action=masquerade chain=srcnat comment="defconf: masquerade" \
ipsec-policy=out,none out-interface-list=WAN
add action=masquerade chain=srcnat
/ip service
set telnet disabled=yes
set ftp disabled=yes
set www disabled=yes
set ssh port=2200
set api disabled=yes
set winbox address=192.168.99.0/24
set api-ssl disabled=yes
/system clock
set time-zone-name=America/New_York
/system identity
set name=router
/system ntp client
set enabled=yes primary-ntp=38.229.71.1 secondary-ntp=199.180.133.100
/system ntp server
set broadcast=yes enabled=yes
/tool bandwidth-server
set enabled=no
/tool mac-server
set allowed-interface-list=none
/tool mac-server mac-winbox
set allowed-interface-list=none
/tool mac-server ping
set enabled=noRe: Need help with firewall rules to prevent VLAN access to LAN
Hmm, losing patience, why are you screwing around.
The instruction was as simple as this......
/interface bridge
add admin-mac= auto-mac=no comment=defconf name=1-default-bridge \
vlan-filtering=yes
and yet somehow you took it upon yourself to do this......
/interface bridge
add admin-mac=00:00:00:82:05:00 auto-mac=no comment=defconf name=1-bridge
add ingress-filtering=yes name=MGMT vlan-filtering=yes
You only need ONE BRIDGE,,,,,,,,,,
Should be
/interface bridge
add admin-mac=00:00:00:82:05:00 auto-mac=no comment=defconf name=1-bridge vlan-filtering=yes
/interface list member
add comment=defconf interface=ether1 list=WAN
add interface=vlan99 list=LAN
add interface=VLAN4 list=LAN
add interface=VLAN10 list=LAN
add interface=VLAN20 list=LAN
add interface=VLAN4 list=VLAN
add interface=VLAN10 list=VLAN
add interface=VLAN20 list=VLAN
/interface vlan
add interface=1-bridge name=VLAN4 vlan-id=4
add interface=1-bridge name=VLAN10 vlan-id=10
add interface=1-bridge name=VLAN20 vlan-id=20
add interface=1-bridge name=VLAN99 vlan-id=99
/ip dhcp-server
add address-pool=dhcp_pool0 disabled=no interface=VLAN4 name=dhcp1
add address-pool=dhcp_pool1 disabled=no interface=VLAN10 name=dhcp2
add address-pool=dhcp_pool2 disabled=no interface=VLAN20 name=dhcp3
add address-pool=dhcp disabled=no interface=VLAN99 name=dhcp4
/ip address
add address=192.168.4.1/24 interface=VLAN4 network=192.168.4.0
add address=192.168.10.1/24 interface=VLAN10 network=192.168.10.0
add address=10.0.20.1/24 interface=VLAN20 network=10.0.20.0
add address=192.168.99.1/24 interface=VLAN99 network=192.168.99.0
/interface bridge port
add bridge=1-bridge interface=ether5 pvid=99 frame-types=admit-only-untagged-and-priority-tagged (access port to your pc I assume)
add bridge=1-bridge interface=ether2 ingress-filtering=yes (trunk port to switch)
WHERE IS YOUR BRIDGE VLAN SETTINGS???
/interface bridge vlan
add bridge=1-bridge tagged=bridge,ether2 vlan-ids=4,10,20
add bridge=1-bridge untagged=ether5 vlan-ids=99
What are these rules for........... because these are all wrong!!!
add action=drop chain=input comment="Block IoT Local Ports" dst-address=\
192.168.99.1 dst-port=80,21,22,23,8291,2200 protocol=tcp \
src-address-list="IoT Users"
add action=drop chain=input comment="Block IoT VLAN4" dst-address=\
192.168.4.0/24 src-address-list="IoT Users"
add action=drop chain=input comment="Block Iot VLAN10" dst-address=\
192.168.10.0/24 src-address-list="IoT Users"
The instruction was as simple as this......
/interface bridge
add admin-mac= auto-mac=no comment=defconf name=1-default-bridge \
vlan-filtering=yes
and yet somehow you took it upon yourself to do this......
/interface bridge
add admin-mac=00:00:00:82:05:00 auto-mac=no comment=defconf name=1-bridge
add ingress-filtering=yes name=MGMT vlan-filtering=yes
You only need ONE BRIDGE,,,,,,,,,,
Should be
/interface bridge
add admin-mac=00:00:00:82:05:00 auto-mac=no comment=defconf name=1-bridge vlan-filtering=yes
/interface list member
add comment=defconf interface=ether1 list=WAN
add interface=vlan99 list=LAN
add interface=VLAN4 list=LAN
add interface=VLAN10 list=LAN
add interface=VLAN20 list=LAN
add interface=VLAN4 list=VLAN
add interface=VLAN10 list=VLAN
add interface=VLAN20 list=VLAN
/interface vlan
add interface=1-bridge name=VLAN4 vlan-id=4
add interface=1-bridge name=VLAN10 vlan-id=10
add interface=1-bridge name=VLAN20 vlan-id=20
add interface=1-bridge name=VLAN99 vlan-id=99
/ip dhcp-server
add address-pool=dhcp_pool0 disabled=no interface=VLAN4 name=dhcp1
add address-pool=dhcp_pool1 disabled=no interface=VLAN10 name=dhcp2
add address-pool=dhcp_pool2 disabled=no interface=VLAN20 name=dhcp3
add address-pool=dhcp disabled=no interface=VLAN99 name=dhcp4
/ip address
add address=192.168.4.1/24 interface=VLAN4 network=192.168.4.0
add address=192.168.10.1/24 interface=VLAN10 network=192.168.10.0
add address=10.0.20.1/24 interface=VLAN20 network=10.0.20.0
add address=192.168.99.1/24 interface=VLAN99 network=192.168.99.0
/interface bridge port
add bridge=1-bridge interface=ether5 pvid=99 frame-types=admit-only-untagged-and-priority-tagged (access port to your pc I assume)
add bridge=1-bridge interface=ether2 ingress-filtering=yes (trunk port to switch)
WHERE IS YOUR BRIDGE VLAN SETTINGS???
/interface bridge vlan
add bridge=1-bridge tagged=bridge,ether2 vlan-ids=4,10,20
add bridge=1-bridge untagged=ether5 vlan-ids=99
What are these rules for........... because these are all wrong!!!
add action=drop chain=input comment="Block IoT Local Ports" dst-address=\
192.168.99.1 dst-port=80,21,22,23,8291,2200 protocol=tcp \
src-address-list="IoT Users"
add action=drop chain=input comment="Block IoT VLAN4" dst-address=\
192.168.4.0/24 src-address-list="IoT Users"
add action=drop chain=input comment="Block Iot VLAN10" dst-address=\
192.168.10.0/24 src-address-list="IoT Users"
Who is online
Users browsing this forum: mansuramir and 163 guests


