Hello everyone!
I mention that I have a network in the company with Ubiquiti products, both the USG PRO 4 Router, Switches and APs.
In the Router, I have my two Internet providers connected to both WAN cards doing LB.
A few days ago the company bought a Fortigate to configure the internet restrictions in the different clients, VPN for some employees to access Client to Site from their homes and add security.
And a Mikrotik CCR1009 was also bought to be the border router to the two internet providers, connecting them in the following way:
Internet
--
--
--
Mikrotik CCR1009-7G-1C-1S+: Details: https://mikrotik.com/product/CCR1009-7G-1C-1Splus
--
--
--
Fortigate 100F: Details: https://www.fortinet.com/content/dam/fo ... series.pdf
--
--
--
Ubiquiti UniFi USG-PRO-4: Details: https://www.ui.com/unifi-routing/unifi- ... way-pro-4/
--
--
--
Internal Network
In this way, only use the Ubiquiti Unifi USG for VLAN management.
How do you recommend connecting both physically and the configurations between the equipment? Physically I do not even realize how to configure them, for example the USG would have to stop connecting the WAN plates to not swim .. since the only NAT would be those of the Mikrotik .. with what if they help me graphically show the connections between I really appreciate the equipment and configurations of recommendation, since many networking things I am beginning to understand in the last time.
I know that this forum only sees Mikrotik topics, but maybe there are people with experience in other products that I comment and that connect to Ubiquiti equipment.
From already thank you very much!!
-

-
StubArea51
Trainer

- Posts: 1739
- Joined:
- Location: stubarea51.net
- Contact:
Re: Mikrotik physical connection recommendations to other products.
I've done this quite a bit with MikroTik and Fortigate for Enterprise and Data Center networks.
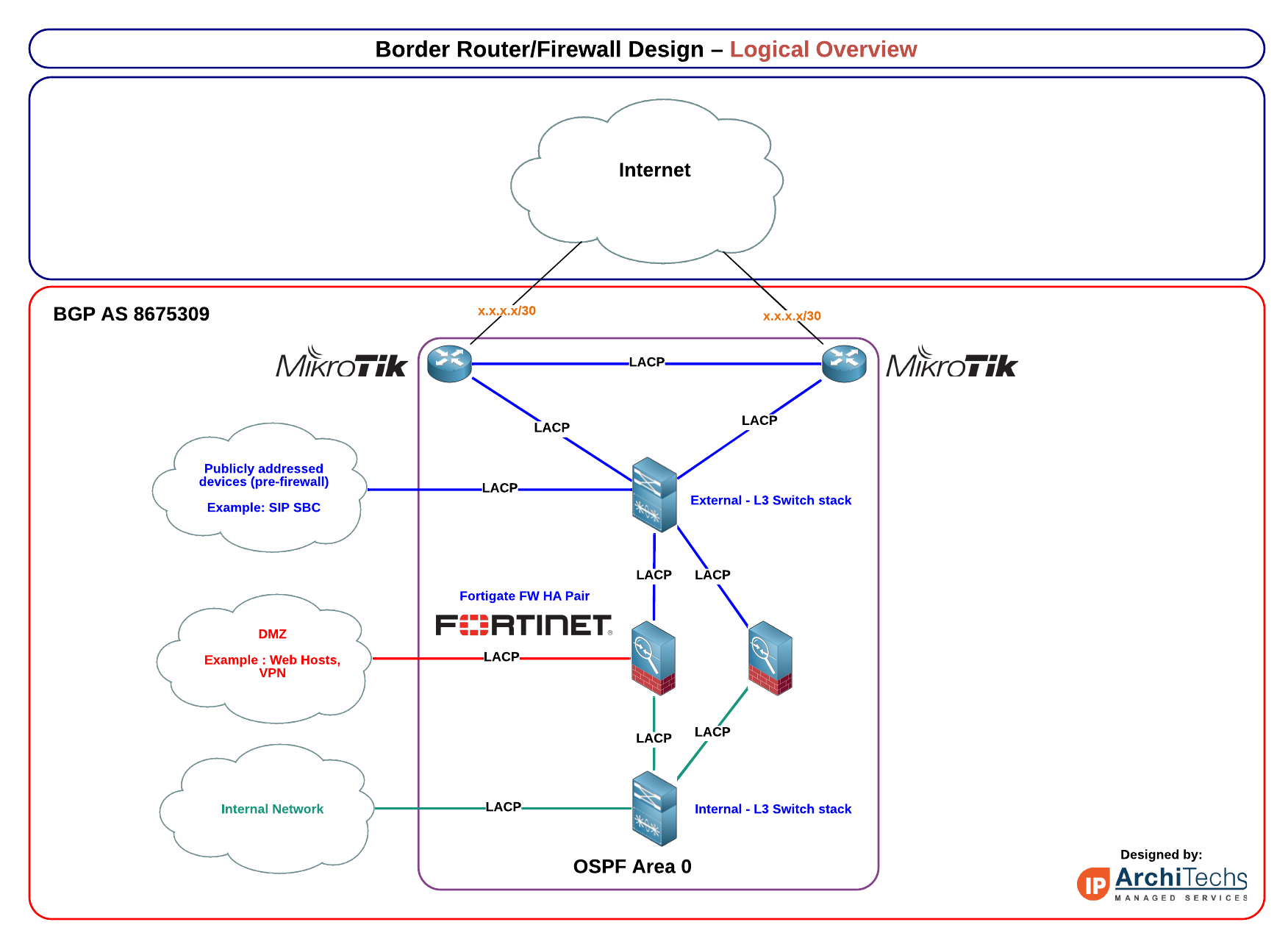
Typically I use a design that employs dynamic routing and L3 switch stacks for a few reasons
1) Failover isolation - the border routers can failover independently of the firewall pair if there is an internet outage or device outage. The same is true of the firewalls, if a firewall fails, it doesn't affect the state of the Internet edge
2) Simplified FW policy - in this design, there is only one logical "WAN" interface because the Internet failover is handled at a different tier, so policy management is easier
3) Flexibility - L3 switch stacks for internal and external allow for new devices to be added in the zone that makes the most sense - outside the FW and publicly addressed. In the DMZ with NAT or as publicly addressed and inside the internal network with RFC 1918 addressing.
4) Dynamic routing using iBGP/OSPF is a little more work to setup but it makes failover of the entire system much cleaner and injecting routes from VPNs or into the interior of the network **much** easier and less prone to traffic blackholes like static routing can cause. If you don't need BGP on the border routers, OSPF by itself is also an option.
Here is an overview that I modified from a production design.
Typically I use a design that employs dynamic routing and L3 switch stacks for a few reasons
1) Failover isolation - the border routers can failover independently of the firewall pair if there is an internet outage or device outage. The same is true of the firewalls, if a firewall fails, it doesn't affect the state of the Internet edge
2) Simplified FW policy - in this design, there is only one logical "WAN" interface because the Internet failover is handled at a different tier, so policy management is easier
3) Flexibility - L3 switch stacks for internal and external allow for new devices to be added in the zone that makes the most sense - outside the FW and publicly addressed. In the DMZ with NAT or as publicly addressed and inside the internal network with RFC 1918 addressing.
4) Dynamic routing using iBGP/OSPF is a little more work to setup but it makes failover of the entire system much cleaner and injecting routes from VPNs or into the interior of the network **much** easier and less prone to traffic blackholes like static routing can cause. If you don't need BGP on the border routers, OSPF by itself is also an option.
Here is an overview that I modified from a production design.

Re: Mikrotik physical connection recommendations to other products.
So how does a company buy equipment when they dont have any clue of how to incorporate the equipment into their IT infrastructure.
It sounds bass ackwards to me...............
It sounds bass ackwards to me...............
Who is online
Users browsing this forum: Google [Bot] and 76 guests

