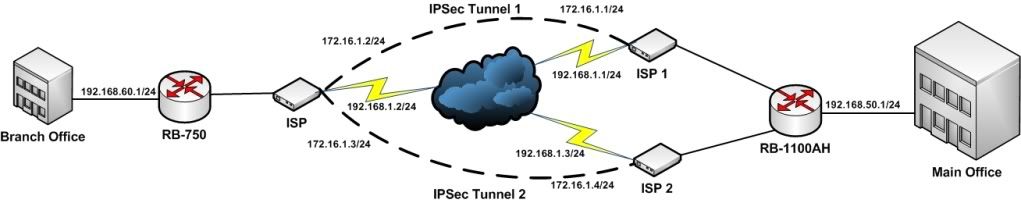
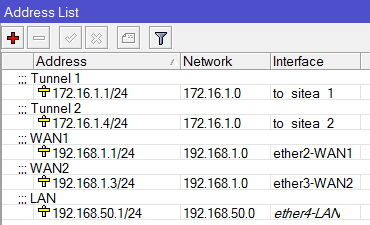
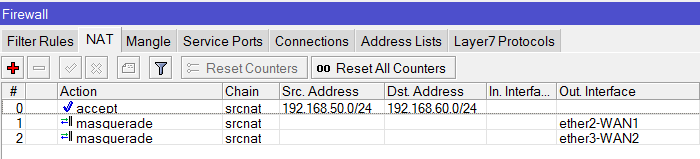
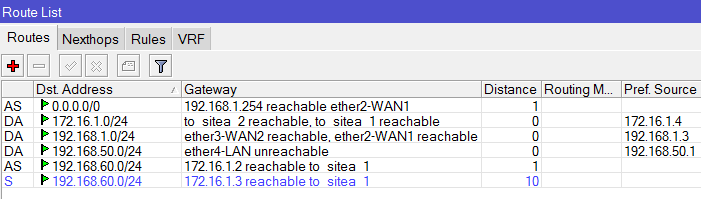
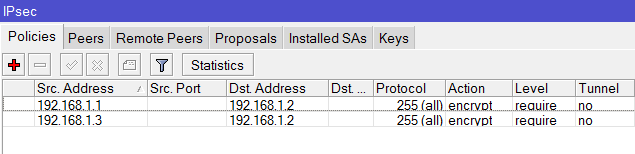
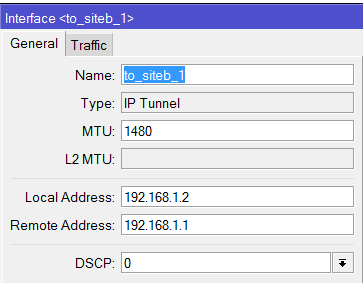
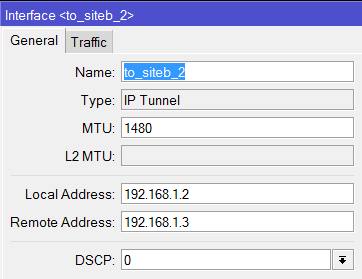
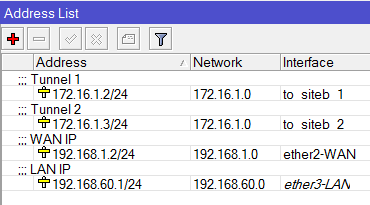
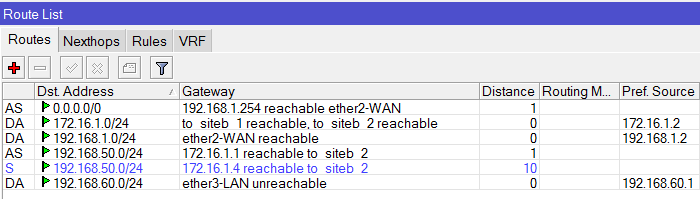
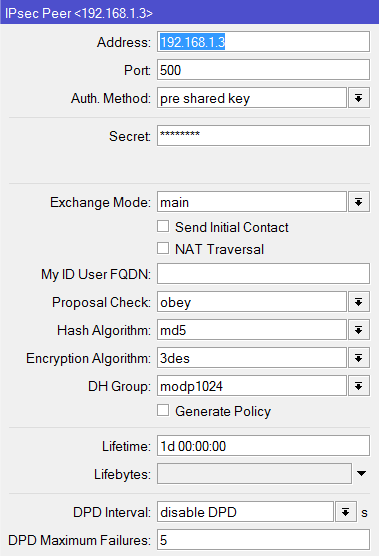
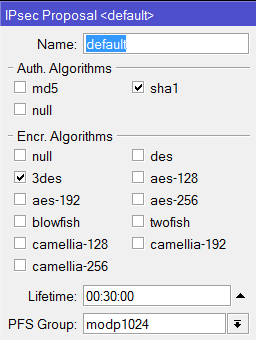
May I ask if it is possible to set-up a VPN connection via IPSec with Fail-over if your set-up is like the design below?
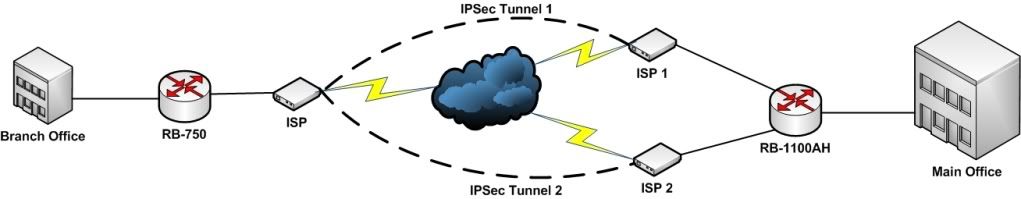
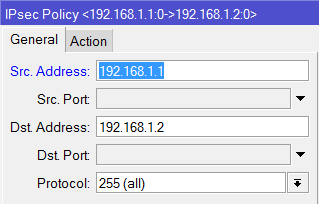
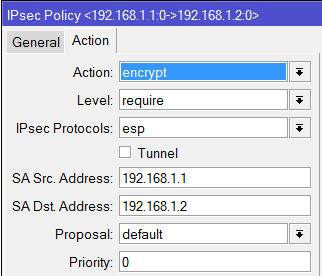
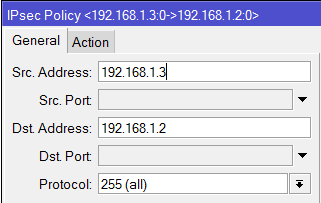
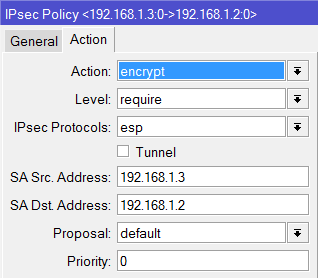
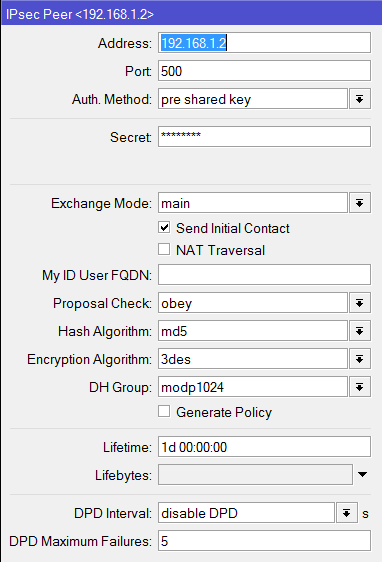
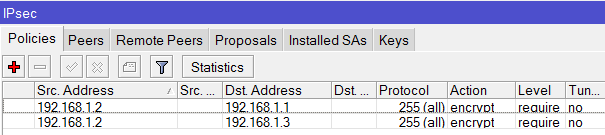
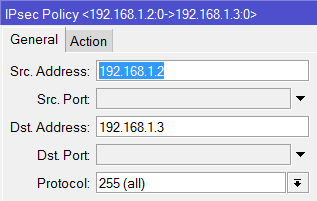
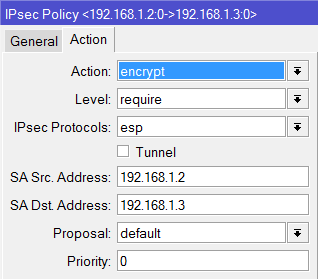
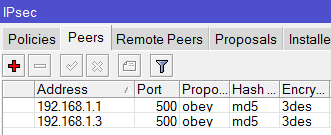
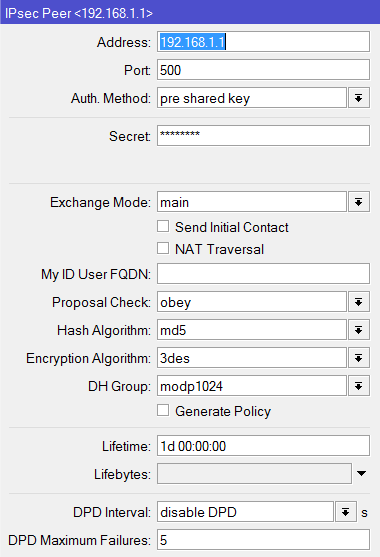
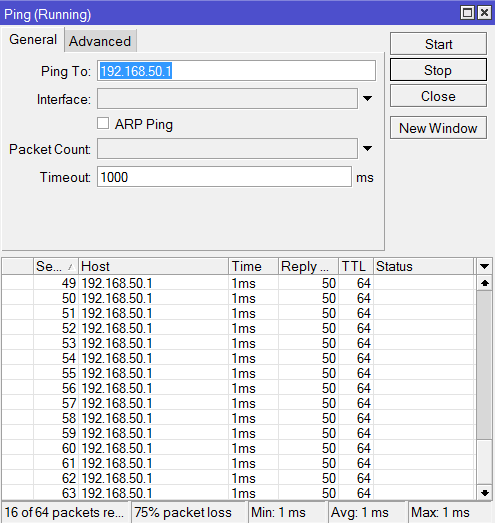
I tried and Set-up an IPSec Policy for ISP1 and ISP2 going to the Branch office and set-up an IPSec link to both ISP1 and ISP2 going to the main office.
Example:
/ip ipsec peer
add address=211.1.1.1/32 port=500 auth-method=pre-shared-key secret="test"
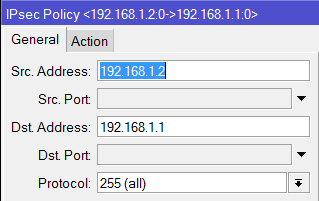
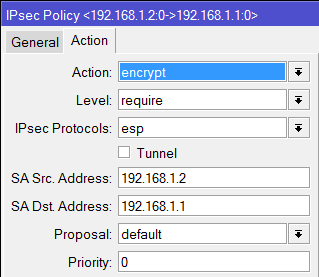
/ip ipsec policy
add src-address=10.1.1.0/24 src-port=any dst-address=10.1.101.0/24 dst-port=any \
sa-src-address=201.1.1.1 sa-dst-address=211.1.1.1 \
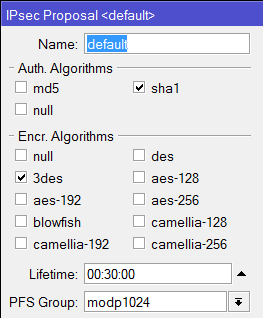
tunnel=yes action=encrypt proposal=default
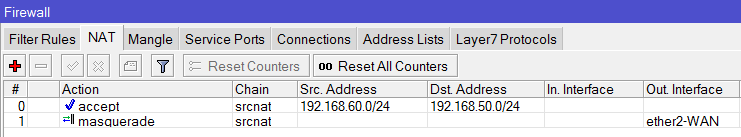
/ip firewall nat
add chain=srcnat action=accept place-before=0 \
src-address=10.1.1.0/24 dst-address=10.1.101.0/24
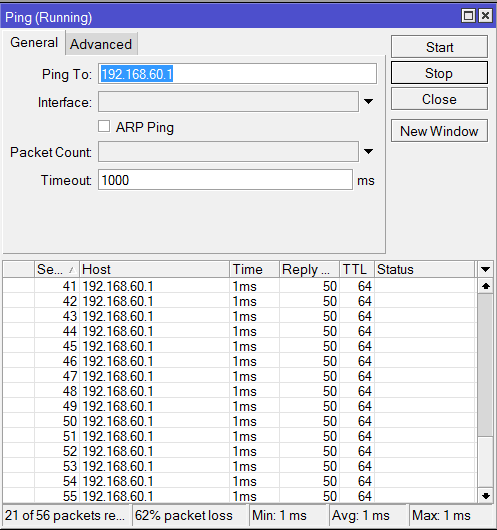
This set-up on one branch and vice-versa on the other. It's working if it's one to one VPN tunnel but if I added a new connection to my ISP 2 the fail-over no longer work.
Is there a way like bridging it and running Rapid Spanning Tree Protocol or Routing perhaps to implement this?
Thanks in advanced. I really need your help to implement something like this.