I am having a problem with the final configuration of the secondary MT(192.168.88.1 / WG 192.168.3.2) as a WireGuard client which will be in the studio in Paris and will be connecting to the studio in Rome(77.77.77.177 - temporary IP address) to the WireGuard server(192.168.3.1) to have access to LAN devices(192.168.2.0/24) (file server and remote desktop with workstations). I already arrived at the point where my main MT with the WG server(192.168.3.1) working well, from outside the studio I can connect to remote desktops in both directions and share the files - I can say that the base for Rome studio works well. Secondary MT(192.168.88.1 / WG 192.168.3.2) already appears in the ARP on the main MT, but I can not ping anything or use a remote desktop. My understanding is that if my direct clients to the WG server(192.168.3.1) are correct and pass the firewall and have access to the LAN(192.168.2.0/24) that means on the side of the server is all ok because what I think is that all connections from the MT client will be visible as just MT. So, the setup of the MT client(192.168.88.1 / WG 192.168.3.2) is missing something, I have already marked the packages and connections and mangled it, and I see the packages for addresses in the main LAN(192.168.2.0/24) are cached and marked properly, but it seems like that's the end for them and are not going into WG(192.168.3.2) and then to WG server(192.168.3.1).
Network map
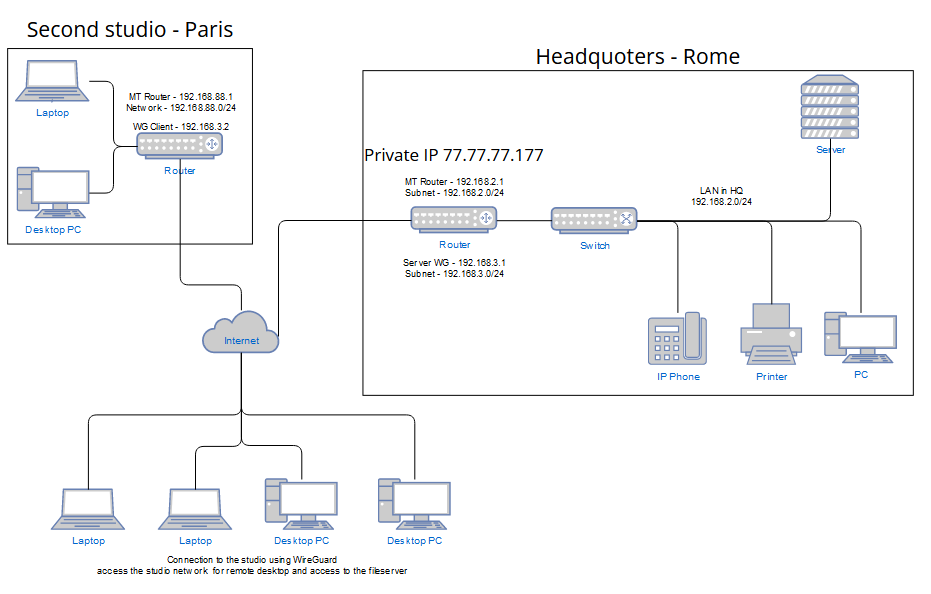
Config of main MT(192.168.2.1 / WG 192.168.3.1) updated with anav sugestions
Code: Select all
# 2023-09-28 00:48:11 by RouterOS 7.10
# software id = AAD3-KLSA
/interface bridge
add admin-mac=48:A9:8A:BA:F3:5D arp=proxy-arp auto-mac=no comment=defconf \
name=bridge
/interface wifiwave2
set [ find default-name=wifi1 ] channel.skip-dfs-channels=10min-cac \
configuration.mode=ap .ssid=MikroTik-BAF361 disabled=no \
security.authentication-types=wpa2-psk,wpa3-psk
set [ find default-name=wifi2 ] channel.skip-dfs-channels=10min-cac \
configuration.mode=ap .ssid=MikroTik-BAF362 disabled=no \
security.authentication-types=wpa2-psk,wpa3-psk
/interface wireguard
add listen-port=13231 mtu=1420 name=wireguard1
/interface list
add comment=defconf name=WAN
add comment=defconf name=LAN
/ip pool
add name=default-dhcp ranges=192.168.2.100-192.168.2.250
/ip dhcp-server
add address-pool=default-dhcp interface=bridge lease-time=10m name=defconf
/interface bridge port
add bridge=bridge comment=defconf interface=ether2
add bridge=bridge comment=defconf interface=ether3
add bridge=bridge comment=defconf interface=ether4
add bridge=bridge comment=defconf interface=ether5
add bridge=bridge comment=defconf interface=wifi1
add bridge=bridge comment=defconf interface=wifi2
/ip neighbor discovery-settings
set discover-interface-list=LAN
/ipv6 settings
set disable-ipv6=yes
/interface list member
add comment=defconf interface=bridge list=LAN
add comment=defconf interface=ether1 list=WAN
add interface=wireguard1 list=LAN
add interface=wifi1 list=LAN
add interface=wifi2 list=LAN
/interface wireguard peers
add allowed-address=192.168.3.0/24 comment="Admin - personal" endpoint-address=\
77.77.77.177 endpoint-port=13231 interface=wireguard1 \
persistent-keepalive=35s public-key=\
"/*****************************************************/"
add allowed-address=192.168.3.2/32,192.168.88.0/24 comment=\
"MT Paris" endpoint-address=77.77.77.177 endpoint-port=13231 interface=\
wireguard1 persistent-keepalive=35s public-key=\
"/*****************************************************/"
/ip address
add address=192.168.2.1/24 comment=defconf interface=bridge network=\
192.168.2.0
add address=77.77.77.177/29 interface=ether1 network=77.77.77.136
add address=192.168.3.1/24 comment=WireGuard interface=wireguard1 network=\
192.168.3.0
/ip dhcp-client
add comment=defconf disabled=yes interface=ether1
/ip dhcp-server network
add address=192.168.88.0/24 comment=defconf dns-server=192.168.88.1 gateway=\
192.168.88.1
/ip dns
set allow-remote-requests=yes servers=8.8.8.8,1.1.1.1
/ip dns static
add address=192.168.2.1 comment=defconf name=router.lan
/ip firewall address-list
add address=192.168.88.0/24 comment="local admin desktop/laptop wired" \
disabled=yes list=Authorized
add address=192.168.2.0/24 comment="Remote admin desktop/laptop wired" list=\
Authorized
add address=192.168.3.10 comment="Remote admin laptop - MR" list=Authorized
add address=192.168.3.0/24 comment="Remote admin ipad/smartphone" list=\
Authorized
/ip firewall filter
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=accept chain=input comment=\
"defconf: accept to local loopback (for CAPsMAN)" dst-address=127.0.0.1
add action=accept chain=input comment=wireguard dst-port=13231 log=yes \
log-prefix=WireGuard protocol=udp
add action=accept chain=input src-address-list=Authorized
add action=accept chain=input comment="Allow LAN DNS queries-UDP" dst-port=53 \
in-interface-list=LAN protocol=udp
add action=accept chain=input comment="Allow LAN DNS queries - TCP" dst-port=\
53 in-interface-list=LAN protocol=tcp
add action=drop chain=input comment="drop all else"
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related hw-offload=yes
add action=accept chain=forward comment=\
"defconf: accept established,related, untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=accept chain=forward comment="allow internet traffic" \
in-interface-list=LAN out-interface-list=WAN
add action=accept chain=forward comment=\
"Incoming remote traffic from WireGuard to local lan" in-interface=\
wireguard1
add action=accept chain=forward comment="Outgoing local traffic to WireGuard" \
out-interface=wireguard1
add action=drop chain=forward comment="drop all else"
/ip firewall nat
add action=masquerade chain=srcnat comment="defconf: masquerade" \
ipsec-policy=out,none out-interface-list=WAN
/ip firewall raw
add action=accept chain=prerouting comment=\
"defconf: enable for transparent firewall" disabled=yes
add action=accept chain=prerouting comment="defconf: accept DHCP discover" \
dst-address=255.255.255.255 dst-port=67 in-interface-list=LAN protocol=\
udp src-address=0.0.0.0 src-port=68
add action=drop chain=prerouting comment="defconf: drop bad UDP" port=0 \
protocol=udp
add action=jump chain=prerouting comment="defconf: jump to ICMP chain" \
jump-target=icmp4 protocol=icmp
add action=jump chain=prerouting comment="defconf: jump to TCP chain" \
jump-target=bad_tcp protocol=tcp
add action=accept chain=prerouting comment=\
"defconf: accept everything else from LAN" in-interface-list=LAN
add action=accept chain=prerouting comment=\
"defconf: accept everything else from WAN" in-interface-list=WAN
add action=drop chain=prerouting comment="defconf: drop the rest"
add action=drop chain=bad_tcp comment="defconf: TCP flag filter" protocol=tcp \
tcp-flags=!fin,!syn,!rst,!ack
add action=drop chain=bad_tcp comment=defconf protocol=tcp tcp-flags=fin,syn
add action=drop chain=bad_tcp comment=defconf protocol=tcp tcp-flags=fin,rst
add action=drop chain=bad_tcp comment=defconf protocol=tcp tcp-flags=fin,!ack
add action=drop chain=bad_tcp comment=defconf protocol=tcp tcp-flags=fin,urg
add action=drop chain=bad_tcp comment=defconf protocol=tcp tcp-flags=syn,rst
add action=drop chain=bad_tcp comment=defconf protocol=tcp tcp-flags=rst,urg
add action=drop chain=bad_tcp comment="defconf: TCP port 0 drop" port=0 \
protocol=tcp
/ip route
add disabled=no distance=1 dst-address=0.0.0.0/0 gateway=77.77.77.137 \
pref-src="" routing-table=main scope=30 suppress-hw-offload=no \
target-scope=10
add disabled=no dst-address=192.168.2.0/24 gateway=wireguard1 routing-table=\
main suppress-hw-offload=no
/ip service
set telnet disabled=yes
set ftp disabled=yes
set ssh disabled=yes
set api disabled=yes
set api-ssl disabled=yes
/system clock
set time-zone-name=Europe/Rome
/system note
set show-at-login=no
/tool mac-server
set allowed-interface-list=LAN
/tool mac-server mac-winbox
set allowed-interface-list=LAN
Config of MT-2 (192.168.88.1 / WG 192.168.3.2) updated with anav sugestions
Code: Select all
# sep/28/2023 01:03:05 by RouterOS 7.6
# software id = PVSB-VYKC
#
/interface bridge
add admin-mac=48:A9:8A:51:BB:63 arp=proxy-arp auto-mac=no comment=defconf \
name=bridge
/interface ethernet
set [ find default-name=ether1 ] comment=WAN
set [ find default-name=ether2 ] comment=LAN2
set [ find default-name=ether3 ] comment=LAN3
set [ find default-name=ether4 ] comment=LAN4
set [ find default-name=ether5 ] comment=LAN5
/interface wifiwave2
set [ find default-name=wifi1 ] channel.skip-dfs-channels=10min-cac comment=\
"WiFi 5GHz" configuration.country=Italy .mode=ap .ssid=MikroTik-51BB67 \
disabled=no security.authentication-types=wpa2-psk,wpa3-psk
set [ find default-name=wifi2 ] channel.skip-dfs-channels=10min-cac comment=\
"WiFi 2.4GHz" configuration.country=Italy .mode=ap .ssid=MikroTik-51BB68 \
disabled=no security.authentication-types=wpa2-psk,wpa3-psk
/interface wireguard
add comment=wireguard listen-port=13231 mtu=1420 name=wireguard-client
/interface list
add comment=defconf name=WAN
add comment=defconf name=LAN
/ip pool
add name=dhcp ranges=192.168.88.10-192.168.88.254
/ip dhcp-server
add address-pool=dhcp interface=bridge name=defconf
/port
set 0 name=serial0
/routing table
add comment=WireGuard disabled=no fib name=wg
/interface bridge port
add bridge=bridge comment=defconf interface=ether2
add bridge=bridge comment=defconf interface=ether3
add bridge=bridge comment=defconf interface=ether4
add bridge=bridge comment=defconf interface=ether5
add bridge=bridge comment=defconf interface=wifi1
add bridge=bridge comment=defconf interface=wifi2
/ip neighbor discovery-settings
set discover-interface-list=LAN
/ipv6 settings
set accept-redirects=no accept-router-advertisements=no disable-ipv6=yes \
forward=no
/interface list member
add comment=defconf interface=bridge list=LAN
add comment=defconf interface=ether1 list=WAN
add interface=wireguard-client list=LAN
add interface=wifi1 list=LAN
add interface=wifi2 list=LAN
/interface wireguard peers
add allowed-address=192.168.2.0/24,192.168.3.0/24 comment=\
"wg-client to wg-server" endpoint-address=77.77.77.177 endpoint-port=13231 \
interface=wireguard-client persistent-keepalive=35s public-key=\
"/***************************************/"
/ip address
add address=192.168.88.1/24 comment=defconf interface=bridge network=\
192.168.88.0
add address=192.168.3.2/24 comment=wireguard-client interface=\
wireguard-client network=192.168.3.0
/ip dhcp-client
add comment=defconf interface=ether1 use-peer-dns=no
/ip dhcp-server network
add address=192.168.88.0/24 comment=defconf dns-server=192.168.88.1 gateway=\
192.168.88.1
/ip dns
set allow-remote-requests=yes servers=192.168.1.254,8.8.8.8,1.1.1.1
/ip dns static
add address=192.168.88.1 comment=defconf name=router.lan
/ip firewall address-list
add address=192.168.3.0/24 list=wg-dest
add address=192.168.2.0/24 list=wg-dest
add address=192.168.88.0/24 comment="local admin desktop/laptop wired" list=\
Authorized
add address=192.168.2.0/24 comment="Remote admin desktop/laptop wired" list=\
Authorized
add address=192.168.3.10 comment="Remote admin laptop - MR" list=Authorized
add address=192.168.3.0/24 comment="Remote admin ipad/smartphone" list=\
Authorized
/ip firewall filter
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=accept chain=input comment=\
"defconf: accept to local loopback (for CAPsMAN)" dst-address=127.0.0.1
add action=accept chain=input comment=wireguard dst-port=13231 log=yes \
log-prefix=WireGuard protocol=udp
add action=accept chain=input src-address-list=Authorized
add action=accept chain=forward comment=\
"Incoming remote traffic from WireGuard to local lan" in-interface=\
wireguard-client
add action=accept chain=forward comment="Outgoing local traffic to WireGuard" \
out-interface=wireguard-client
add action=accept chain=input comment="Allow LAN DNS queries-UDP" dst-port=53 \
in-interface-list=LAN protocol=udp
add action=accept chain=input comment="Allow LAN DNS queries - TCP" dst-port=\
53 in-interface-list=LAN protocol=tcp
add action=drop chain=input comment="drop all else"
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related hw-offload=yes
add action=accept chain=forward comment=\
"defconf: accept established,related, untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=accept chain=forward comment="allow internet traffic" \
in-interface-list=LAN out-interface-list=WAN
add action=drop chain=forward comment="drop all else"
/ip firewall mangle
add action=mark-connection chain=prerouting comment=WireGuard \
connection-state=new dst-address-list=wg-dest in-interface=bridge \
new-connection-mark=wg-con passthrough=yes
add action=mark-routing chain=prerouting comment=WireGuard connection-mark=\
wg-con in-interface=bridge new-routing-mark=wg passthrough=yes
/ip firewall nat
add action=masquerade chain=srcnat comment="defconf: masquerade" \
ipsec-policy=out,none out-interface-list=WAN
add action=masquerade chain=srcnat comment="WireGuard: masquarade" \
out-interface=wireguard-client
/ip route
add disabled=no dst-address=192.168.88.0/24 gateway=wireguard-client \
routing-table=main suppress-hw-offload=no
/ip service
set telnet disabled=yes
set ftp disabled=yes
set ssh disabled=yes
set api disabled=yes
set api-ssl disabled=yes
/system clock
set time-zone-name=Europe/Rome
/tool mac-server
set allowed-interface-list=LAN
/tool mac-server mac-winbox
set allowed-interface-list=LAN
In MT(192.168.88.1 / WG 192.168.3.2) where I do WG clients I disabled all firewalls to be sure that nothing is blocking my outgoing connections. Also, I removed from the config of the main MT (192.168.2.1) the country filter list because it is 120000 addresses, but for testing, I am disabling that rule for a moment to be sure that is not the problem.
That is my first post here on this forum, I have tried my best, let me know that I put all the info needed and thanks in advance for any suggestions.


