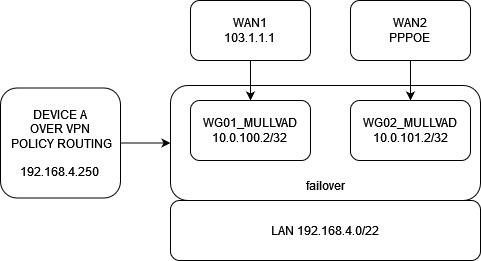
How do i get WG01_MULLVAD to use WAN1 using routing table? I tried many different combinations in Routing Rules with source set to wireguard interface ip, destination etc but it always used the default route.

# mar/07/2023 02:10:21 by RouterOS 7.6
# software id =
#
/interface ethernet
set [ find default-name=ether3 ] name=LAN
set [ find default-name=ether1 ] disable-running-check=no name=MANAGMENT_PORT
set [ find default-name=ether1 ] name=WAN1
set [ find default-name=ether2 ] mtu=1480 name=WAN2
/interface pppoe-client
add disabled=no interface=WAN1 name=WAN1_PPPOE user=user
/interface wireguard
add listen-port=13231 name=WIREGUARD_WAN1
add listen-port=13239 name=WIREGUARD_WAN2
/interface vlan
add interface=LAN name=FREEWIFI vlan-id=140
/interface wireless security-profiles
set [ find default=yes ] supplicant-identity=MikroTik
/ip pool
add name=dhcp_pool0 ranges=192.168.4.10-192.168.4.254
add name=dhcp_pool1 ranges=192.168.100.10-192.168.100.254
add name=dhcp_pool2 ranges=192.168.69.2-192.168.69.254
/ip dhcp-server
add address-pool=dhcp_pool0 interface=LAN lease-time=1h name=DHCP_LAN
add address-pool=dhcp_pool1 interface=MANAGMENT_PORT name=dhcp1
add address-pool=dhcp_pool2 interface=FREEWIFI lease-time=1h name=dhcp2
/routing table
add disabled=no fib name=WAN1_ROUTE
add disabled=no fib name=WAN1_ROUTE
add disabled=no fib name=WIREGUARD_GROUP
add disabled=no fib name=WAN1_ROUTE_WIREGUARD
add disabled=no fib name=WAN1_ROUTE_WIREGUARD
/ip neighbor discovery-settings
set discover-interface-list=all
/interface wireguard peers
add allowed-address=0.0.0.0/0,::/0 endpoint-address=138.1.1.1 endpoint-port=51820 interface=\
WIREGUARD_WAN1 persistent-keepalive=10s public-key=""
add allowed-address=0.0.0.0/0,::/0 endpoint-address=138.1.1.1 endpoint-port=51820 interface=\
WIREGUARD_WAN2 persistent-keepalive=10s public-key=""
/ip address
add address=103.1.1.1.1/24 interface=WAN2 network=103.1.1.0
add address=192.168.4.1/22 interface=LAN network=192.168.4.0
add address=192.168.100.235/24 interface=MANAGMENT_PORT network=192.168.100.0
add address=10.66.19.40 interface=WIREGUARD_WAN1 network=10.66.19.40
add address=192.168.69.1/24 interface=FREEWIFI network=192.168.69.0
add address=10.64.149.211 interface=WIREGUARD_WAN2 network=10.64.149.211
/ip dhcp-client
add interface=MANAGMENT_PORT
/ip dhcp-server network
add address=192.168.4.0/22 dns-server=192.168.100.230 gateway=192.168.4.1
add address=192.168.69.0/24 dns-server=192.168.100.235 gateway=192.168.69.1
add address=192.168.100.0/24 gateway=192.168.100.2
/ip dns
set allow-remote-requests=yes servers=1.1.1.1
/ip firewall filter
add action=drop chain=input comment="Block access to RouterOS services" dst-port=80,443,8291,8728,8729 \
protocol=tcp src-address=192.168.69.0/24
add action=accept chain=input connection-state=established,related
add action=drop chain=input connection-state=invalid
add action=drop chain=input in-interface=WAN2
/ip firewall mangle
add action=change-mss chain=forward new-mss=1500 out-interface=WIREGUARD_WAN1 passthrough=yes protocol=\
tcp tcp-flags=syn tcp-mss=1000-65535
add action=change-mss chain=forward new-mss=1500 out-interface=WIREGUARD_WAN2 passthrough=yes protocol=\
tcp tcp-flags=syn tcp-mss=1000-65535
/ip firewall nat
add action=masquerade chain=srcnat comment="DEFAULT NAT" out-interface=WAN1_PPPOE
add action=masquerade chain=srcnat comment="DEFAULT NAT" out-interface=WAN2
add action=masquerade chain=srcnat comment="DEFAULT NAT" out-interface=MANAGMENT_PORT
add action=masquerade chain=srcnat comment="DEFAULT NAT" out-interface=WIREGUARD_WAN1
add action=masquerade chain=srcnat comment="DEFAULT NAT" out-interface=WIREGUARD_WAN2
/ip route
add comment="MAIN ROUTE" disabled=no distance=1 dst-address=0.0.0.0/0 gateway=WAN1_PPPOE pref-src="" \
routing-table=main scope=30 suppress-hw-offload=no target-scope=10
add comment="POLICY ROUTE WAN1 " disabled=no distance=1 dst-address=0.0.0.0/0 gateway=WAN1_PPPOE \
pref-src="" routing-table=WAN1_ROUTE scope=30 suppress-hw-offload=no target-scope=10
add comment="POLICY ROUTE WAN1" disabled=no distance=2 dst-address=0.0.0.0/0 gateway=103.1.1.1.1 \
pref-src="" routing-table=WAN1_ROUTE scope=30 suppress-hw-offload=no target-scope=10
add comment="POLICY ROUTE PROXMOX" disabled=no distance=1 dst-address=192.168.100.0/24 gateway=\
192.168.100.2 pref-src="" routing-table=WIREGUARD_GROUP scope=30 suppress-hw-offload=no target-scope=\
10
add check-gateway=ping comment="MAIN ROUTE" disabled=no distance=1 dst-address=0.0.0.0/0 gateway=\
103.1.1.1.1 pref-src="" routing-table=main scope=30 suppress-hw-offload=no target-scope=10
add comment="CHECK ROUTE WAN1" disabled=no distance=1 dst-address=1.1.1.1/32 gateway=WAN1_PPPOE \
pref-src="" routing-table=main scope=11 suppress-hw-offload=no target-scope=10
add comment="CHECK ROUTE WAN2" disabled=no distance=1 dst-address=1.1.1.2/32 gateway=103.1.1.1.1 \
pref-src="" routing-table=main scope=11 suppress-hw-offload=no target-scope=10
add check-gateway=ping comment="RECURSIVE ROUTE WAN1" disabled=no distance=1 dst-address=0.0.0.0/0 \
gateway=1.1.1.1 pref-src="" routing-table=WAN1_ROUTE scope=30 suppress-hw-offload=no target-scope=\
11
add check-gateway=ping comment="RECURSIVE ROUTE WAN2" disabled=no distance=2 dst-address=0.0.0.0/0 \
gateway=1.1.1.2 pref-src="" routing-table=WAN1_ROUTE scope=30 suppress-hw-offload=no \
target-scope=11
add comment="ROUTE WIREGUARD PCS THROUGH TUNNEL" disabled=no distance=1 dst-address=0.0.0.0/0 gateway=\
WIREGUARD_WAN1 pref-src="" routing-table=WIREGUARD_GROUP scope=30 suppress-hw-offload=no \
target-scope=10
/ip service
set ftp disabled=yes
set www disabled=yes
set ssh disabled=yes
set api disabled=yes
set api-ssl disabled=yes
/ipv6 address
add address=fc00:-----/128 advertise=no interface=WIREGUARD_WAN1
/routing rule
add action=lookup-only-in-table comment="POLICY ROUTE WAN2 DEVICE OVER WAN2 GATEWAY" disabled=no interface=\
LAN src-address=192.168.4.243/32 table=WAN1_ROUTE
add action=lookup-only-in-table comment="POLICY ROUTE WAN1 DEVICE OVER WAN1 GATEWAY" disabled=no \
interface=LAN src-address=192.168.4.242/32 table=WAN1_ROUTE
add action=lookup-only-in-table disabled=no interface=LAN src-address=192.168.4.253/32 table=\
WIREGUARD_GROUP
add action=lookup-only-in-table disabled=no interface=LAN src-address=192.168.4.240/32 table=\
WIREGUARD_GROUP
add action=lookup-only-in-table disabled=no interface=LAN src-address=192.168.4.254/32 table=\
WIREGUARD_GROUP