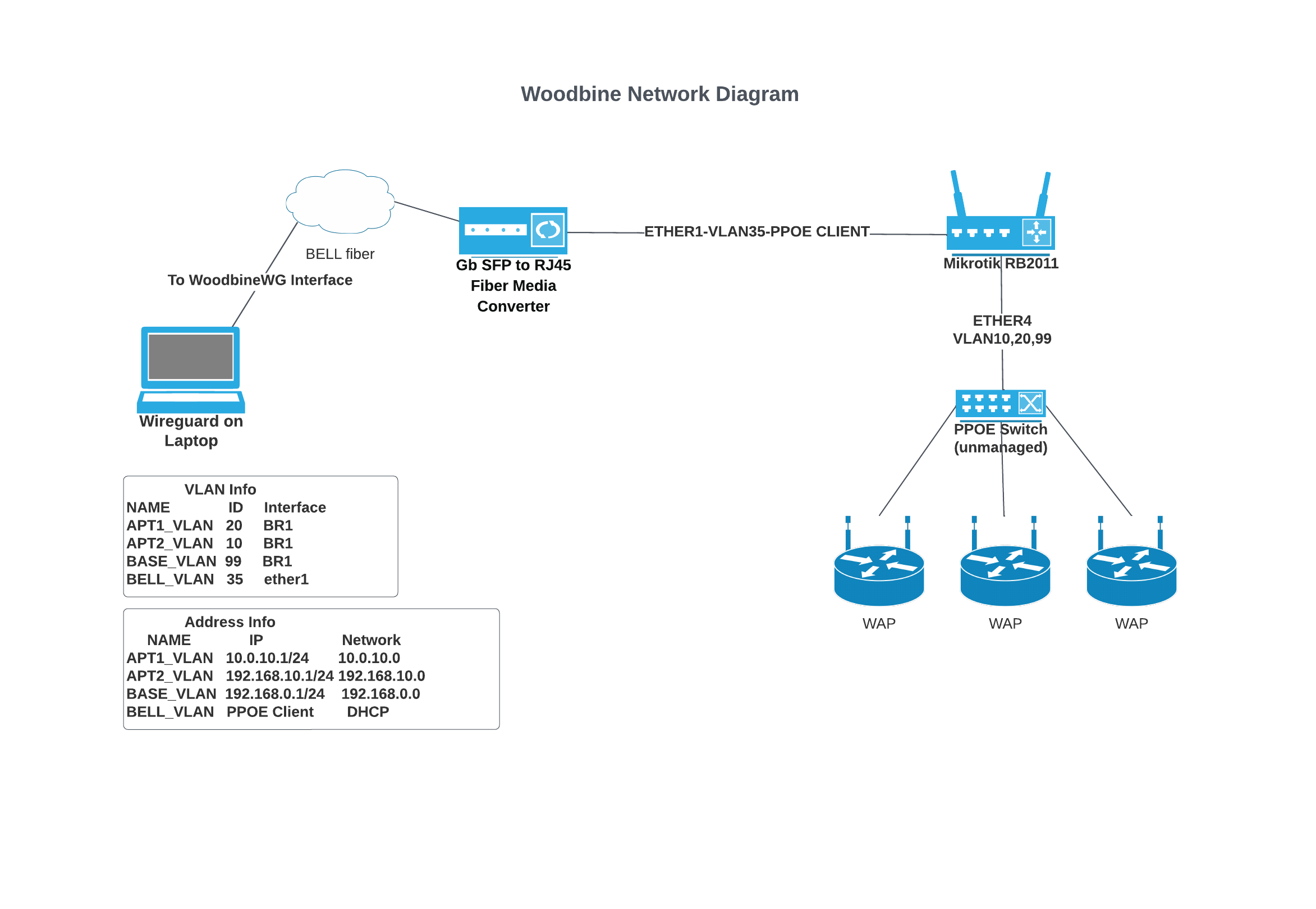
Here is my current config:
Code: Select all
# mar/31/2023 08:15:09 by RouterOS 7.8
# software id = 5MCY-99KG
#
# model = RB2011UiAS-2HnD
# serial number = XXX
/interface bridge
add name=BR1 protocol-mode=none vlan-filtering=yes
/interface ethernet
set [ find default-name=ether1 ] mtu=1508
/interface wireless
set [ find default-name=wlan1 ] frequency=auto mode=ap-bridge ssid=BLUE
/interface wireguard
add listen-port=13231 mtu=1392 name=WoodbineWG
/interface vlan
add interface=BR1 name=APT1_VLAN vlan-id=20
add interface=BR1 name=APT2_VLAN vlan-id=10
add interface=BR1 name=BASE_VLAN vlan-id=99
add interface=ether1 name=BELL_VLAN vlan-id=35
/interface pppoe-client
add add-default-route=yes interface=ether1 name=Virgin user=\
xxx@virginmobile.ca
/interface list
add name=WAN
add name=VLAN
add name=BASE
/interface wireless security-profiles
set [ find default=yes ] authentication-types=wpa2-psk mode=dynamic-keys \
supplicant-identity=MikroTik
add authentication-types=wpa2-psk mode=dynamic-keys name=guest \
supplicant-identity=MikroTik
/interface wireless
add mac-address=E6:8D:8C:36:5C:C7 master-interface=wlan1 name=wlan2 \
security-profile=guest ssid=GREEN
/ip pool
add name=APT1_POOL ranges=10.0.10.2-10.0.10.254
add name=APT2_POOL ranges=192.168.10.50-192.168.10.254
add name=BASE_POOL ranges=192.168.0.50-192.168.0.254
/ip dhcp-server
add address-pool=APT1_POOL interface=APT1_VLAN name=APT1_DHCP
add address-pool=APT2_POOL interface=APT2_VLAN name=APT2_DHCP
add address-pool=BASE_POOL interface=BASE_VLAN name=BASE_DHCP
/port
set 0 name=serial0
/interface bridge port
add bridge=BR1 frame-types=admit-only-untagged-and-priority-tagged interface=\
ether2 pvid=20
add bridge=BR1 frame-types=admit-only-untagged-and-priority-tagged interface=\
ether3 pvid=20
add bridge=BR1 frame-types=admit-only-untagged-and-priority-tagged interface=\
wlan1 pvid=20
add bridge=BR1 frame-types=admit-only-untagged-and-priority-tagged interface=\
wlan2 pvid=10
add bridge=BR1 comment="Admin Access" frame-types=\
admit-only-untagged-and-priority-tagged interface=ether5 pvid=99
add bridge=BR1 frame-types=admit-only-vlan-tagged interface=ether4
/ip neighbor discovery-settings
set discover-interface-list=BASE
/interface bridge vlan
add bridge=BR1 tagged=BR1,ether4 untagged=wlan2 vlan-ids=10
add bridge=BR1 tagged=BR1,ether4 untagged=ether2,ether3,wlan1 vlan-ids=20
add bridge=BR1 tagged=BR1,ether4 untagged=ether5 vlan-ids=99
/interface list member
add interface=ether1 list=WAN
add interface=BASE_VLAN list=VLAN
add interface=APT1_VLAN list=VLAN
add interface=APT2_VLAN list=VLAN
add interface=BASE_VLAN list=BASE
/interface wireguard peers
add allowed-address=10.10.105.3/32 interface=WoodbineWG public-key=\
"FTg+d2M/fWtPA/re9G9gUfZPt+qwsasfsfaUDm2obgJLDCc="
/ip address
add address=192.168.0.1/24 interface=BASE_VLAN network=192.168.0.0
add address=10.0.10.1/24 interface=APT1_VLAN network=10.0.10.0
add address=192.168.10.1/24 interface=APT2_VLAN network=192.168.10.0
add address=10.10.105.1/24 interface=WoodbineWG network=10.10.105.0
/ip dhcp-client
add interface=ether1
/ip dhcp-server network
add address=10.0.10.0/24 dns-server=192.168.0.1 gateway=10.0.10.1
add address=192.168.0.0/24 dns-server=192.168.0.1 gateway=192.168.0.1
add address=192.168.10.0/24 dns-server=192.168.10.1 gateway=192.168.10.1
/ip dns
set allow-remote-requests=yes servers=1.1.1.1
/ip firewall filter
add action=accept chain=input dst-port=51820 protocol=udp
add action=accept chain=input comment="Allow Estab & Related" \
connection-state=established,related
add action=accept chain=forward in-interface=WoodbineWG
add action=accept chain=input comment="Allow VLAN" in-interface-list=VLAN
add action=accept chain=input comment="Allow Base_Vlan Full Access" \
in-interface=BASE_VLAN
add action=accept chain=forward comment="Allow Estab & Related" \
connection-state=established,related
add action=accept chain=forward comment="VLAN Internet Access only" \
connection-state=new in-interface-list=VLAN out-interface-list=WAN
add action=accept chain=input dst-port=51820 in-interface=WoodbineWG \
protocol=tcp
add action=accept chain=input comment="Allow Subnet and WG to internet" \
in-interface=WoodbineWG
add action=accept chain=input comment="allow all from LAN" in-interface=\
ether1
add action=accept chain=input dst-port=443 protocol=udp
add action=drop chain=input comment=Drop
add action=drop chain=forward comment=Drop
/ip firewall nat
add action=masquerade chain=srcnat comment="Default masquerade" \
out-interface-list=WAN
add action=masquerade chain=srcnat out-interface=ether1 src-address=\
192.168.0.0/24
/ip service
set www-ssl disabled=no
/lcd interface pages
set 0 interfaces="sfp1,ether1,ether2,ether3,ether4,ether5,ether6,ether7,ether8\
,ether9,ether10"
/system clock
set time-zone-name=America/Toronto
/system identity
set name=RouterSwitchAP
/system script
add dont-require-permissions=no name=script1 owner=admin policy=\
ftp,reboot,read,write,policy,test,password,sniff,sensitive,romon source="#\
##########################################################################\
####\r\
\n# Topic:\t\tUsing RouterOS to VLAN your network\r\
\n# Example:\t\tRouter-Switch-AP all in one device\r\
\n# Web:\t\t\thttps://forum.mikrotik.com/viewtopic.php\?t=143620\r\
\n# RouterOS:\t\t6.47.10\r\
\n# Date:\t\t\tFebruary 17, 2023\r\
\n# Notes:\t\tStart with a reset (/system reset-configuration)\r\
\n# Thanks:\t\tmkx, sindy\r\
\n########################################################################\
#######\r\
\n\r\
\n#######################################\r\
\n# Naming\r\
\n#######################################\r\
\n\r\
\n# name the device being configured\r\
\n/system identity set name=\"RouterSwitchAP\"\r\
\n\r\
\n\r\
\n#######################################\r\
\n# VLAN Overview\r\
\n#######################################\r\
\n\r\
\n# 10 = BLUE\r\
\n# 20 = GREEN\r\
\n# 99 = BASE (MGMT) VLAN\r\
\n\r\
\n\r\
\n#######################################\r\
\n# WIFI Setup\r\
\n#\r\
\n# Example wireless settings only. Do\r\
\n# NOT use in production!\r\
\n#######################################\r\
\n\r\
\n# Blue SSID\r\
\n/interface wireless security-profiles set [ find default=yes ] authentic\
ation-types=wpa2-psk mode=dynamic-keys wpa2-pre-shared-key=\"password\"\r\
\n/interface wireless set [ find default-name=wlan1 ] ssid=BLUE frequency=\
auto mode=ap-bridge disabled=no\r\
\n\r\
\n# Green SSID\r\
\n/interface wireless security-profiles add name=guest authentication-type\
s=wpa2-psk mode=dynamic-keys wpa2-pre-shared-key=\"password\"\r\
\n/interface wireless add name=wlan2 ssid=GREEN master-interface=wlan1 sec\
urity-profile=guest disabled=no\r\
\n\r\
\n\r\
\n#######################################\r\
\n# Bridge\r\
\n#######################################\r\
\n\r\
\n# create one bridge, set VLAN mode off while we configure\r\
\n/interface bridge add name=BR1 protocol-mode=none vlan-filtering=no\r\
\n\r\
\n\r\
\n#######################################\r\
\n#\r\
\n# -- Access Ports --\r\
\n#\r\
\n#######################################\r\
\n\r\
\n# ingress behavior\r\
\n/interface bridge port\r\
\n\r\
\n# Blue VLAN 20\r\
\nadd bridge=BR1 interface=ether2 pvid=20\r\
\nadd bridge=BR1 interface=ether3 pvid=20\r\
\nadd bridge=BR1 interface=wlan1 pvid=20\r\
\n\r\
\n# Green VLAN 10\r\
\nadd bridge=BR1 interface=ether4 pvid=10\r\
\nadd bridge=BR1 interface=wlan2 pvid=10\r\
\n\r\
\n# BASE_VLAN, set aside a port for admin access to Winbox the device.\r\
\nadd bridge=BR1 interface=ether5 pvid=99\r\
\n\r\
\n# egress behavior, handled automatically\r\
\n\r\
\n# L3 switching so Bridge must be a tagged member\r\
\n/interface bridge vlan\r\
\nadd bridge=BR1 tagged=BR1 vlan-ids=10\r\
\nadd bridge=BR1 tagged=BR1 vlan-ids=20\r\
\nadd bridge=BR1 tagged=BR1 vlan-ids=99\r\
\n\r\
\n\r\
\n#######################################\r\
\n# IP Addressing & Routing\r\
\n#######################################\r\
\n\r\
\n# LAN facing router's IP address on the BASE_VLAN\r\
\n/interface vlan add interface=BR1 name=BASE_VLAN vlan-id=99\r\
\n/ip address add address=192.168.0.1/24 interface=BASE_VLAN\r\
\n\r\
\n# DNS server, set to cache for LAN\r\
\n/ip dns set allow-remote-requests=yes servers=\"9.9.9.9\"\r\
\n\r\
\n# Yellow WAN facing port with IP Address and route provided by ISP\r\
\n/ip address add interface=ether1 address=a.a.a.a/aa network=a.a.a.0\r\
\n/ip route add distance=1 gateway=b.b.b.b\r\
\n\r\
\n\r\
\n#######################################\r\
\n# IP Services\r\
\n#######################################\r\
\n\r\
\n# Blue VLAN interface creation, IP assignment, and DHCP service\r\
\n/interface vlan add interface=BR1 name=BLUE_VLAN vlan-id=20\r\
\n/ip address add interface=BLUE_VLAN address=10.0.10.1/24\r\
\n/ip pool add name=BLUE_POOL ranges=10.0.10.2-10.0.10.254\r\
\n/ip dhcp-server add address-pool=BLUE_POOL interface=BLUE_VLAN name=BLUE\
_DHCP disabled=no\r\
\n/ip dhcp-server network add address=10.0.10.0/24 dns-server=192.168.0.1 \
gateway=10.0.10.1\r\
\n\r\
\n# Green VLAN interface creation, IP assignment, and DHCP service\r\
\n/interface vlan add interface=BR1 name=GREEN_VLAN vlan-id=10\r\
\n/ip address add interface=GREEN_VLAN address=192.168.10.1/24\r\
\n/ip pool add name=GREEN_POOL ranges=192.168.10.50-192.168.10.254\r\
\n/ip dhcp-server add address-pool=GREEN_POOL interface=GREEN_VLAN name=GR\
EEN_DHCP disabled=no\r\
\n/ip dhcp-server network add address=192.168.10.0/24 dns-server=192.168.1\
0.1 gateway=192.168.10.1\r\
\n\r\
\n# Optional: Create a DHCP instance for BASE_VLAN. Convenience feature fo\
r an admin.\r\
\n /ip pool add name=BASE_POOL ranges=192.168.88.10-192.168.0.254\r\
\n /ip dhcp-server add address-pool=BASE_POOL interface=BASE_VLAN name=BAS\
E_DHCP disabled=no\r\
\n /ip dhcp-server network add address=192.168.88.0/24 dns-server=192.168.\
88.1 gateway=192.168.88.1\r\
\n\r\
\n\r\
\n#######################################\r\
\n# Firewalling & NAT\r\
\n# A good firewall for WAN. Up to you\r\
\n# about how you want LAN to behave.\r\
\n#######################################\r\
\n\r\
\n# Use MikroTik's \"list\" feature for easy rule matchmaking.\r\
\n\r\
\n/interface list add name=WAN\r\
\n/interface list add name=VLAN\r\
\n/interface list add name=BASE\r\
\n\r\
\n/interface list member\r\
\nadd interface=ether1 list=WAN\r\
\nadd interface=BASE_VLAN list=VLAN\r\
\nadd interface=BLUE_VLAN list=VLAN\r\
\nadd interface=GREEN_VLAN list=VLAN\r\
\nadd interface=BASE_VLAN list=BASE\r\
\n\r\
\n# VLAN aware firewall. Order is important.\r\
\n/ip firewall filter\r\
\n\r\
\n\r\
\n##################\r\
\n# INPUT CHAIN\r\
\n##################\r\
\nadd chain=input action=accept connection-state=established,related comme\
nt=\"Allow Estab & Related\"\r\
\n\r\
\n# Allow VLANs to access router services like DNS, Winbox. Naturally, you\
\_SHOULD make it more granular.\r\
\nadd chain=input action=accept in-interface-list=VLAN comment=\"Allow VLA\
N\"\r\
\n\r\
\n# Allow BASE_VLAN full access to the device for Winbox, etc.\r\
\nadd chain=input action=accept in-interface=BASE_VLAN comment=\"Allow Bas\
e_Vlan Full Access\"\r\
\n\r\
\nadd chain=input action=drop comment=\"Drop\"\r\
\n\r\
\n##################\r\
\n# FORWARD CHAIN\r\
\n##################\r\
\nadd chain=forward action=accept connection-state=established,related com\
ment=\"Allow Estab & Related\"\r\
\n\r\
\n# Allow all VLANs to access the Internet only, NOT each other\r\
\nadd chain=forward action=accept connection-state=new in-interface-list=V\
LAN out-interface-list=WAN comment=\"VLAN Internet Access only\"\r\
\n\r\
\nadd chain=forward action=drop comment=\"Drop\"\r\
\n\r\
\n##################\r\
\n# NAT\r\
\n##################\r\
\n/ip firewall nat add chain=srcnat action=masquerade out-interface-list=W\
AN comment=\"Default masquerade\"\r\
\n\r\
\n\r\
\n#######################################\r\
\n# VLAN Security\r\
\n#######################################\r\
\n\r\
\n# Only allow ingress packets without tags on Access Ports\r\
\n/interface bridge port\r\
\nset bridge=BR1 ingress-filtering=yes frame-types=admit-only-untagged-and\
-priority-tagged [find interface=ether2]\r\
\nset bridge=BR1 ingress-filtering=yes frame-types=admit-only-untagged-and\
-priority-tagged [find interface=ether3]\r\
\nset bridge=BR1 ingress-filtering=yes frame-types=admit-only-untagged-and\
-priority-tagged [find interface=ether4]\r\
\nset bridge=BR1 ingress-filtering=yes frame-types=admit-only-untagged-and\
-priority-tagged [find interface=ether5]\r\
\nset bridge=BR1 ingress-filtering=yes frame-types=admit-only-untagged-and\
-priority-tagged [find interface=wlan1]\r\
\nset bridge=BR1 ingress-filtering=yes frame-types=admit-only-untagged-and\
-priority-tagged [find interface=wlan2]\r\
\n\r\
\n\r\
\n#######################################\r\
\n# MAC Server settings\r\
\n#######################################\r\
\n\r\
\n# Ensure only visibility and availability from BASE_VLAN, the MGMT netwo\
rk\r\
\n/ip neighbor discovery-settings set discover-interface-list=BASE\r\
\n/tool mac-server mac-winbox set allowed-interface-list=BASE\r\
\n/tool mac-server set allowed-interface-list=BASE\r\
\n\r\
\n\r\
\n#######################################\r\
\n# Turn on VLAN mode\r\
\n#######################################\r\
\n/interface bridge set BR1 vlan-filtering=yes\r\
\n\r\
\n"
add dont-require-permissions=no name=script2 owner=admin policy=\
ftp,reboot,read,write,policy,test,password,sniff,sensitive,romon source="#\
\_Blue VLAN interface creation, IP assignment, and DHCP service\r\
\n/interface vlan add interface=BR1 name=BLUE_VLAN vlan-id=20\r\
\n/ip address add interface=BLUE_VLAN address=10.0.10.1/24\r\
\n/ip pool add name=BLUE_POOL ranges=10.0.10.2-10.0.10.254\r\
\n/ip dhcp-server add address-pool=BLUE_POOL interface=BLUE_VLAN name=BLUE\
_DHCP disabled=no\r\
\n/ip dhcp-server network add address=10.0.10.0/24 dns-server=192.168.0.1 \
gateway=10.0.10.1\r\
\n\r\
\n# Green VLAN interface creation, IP assignment, and DHCP service\r\
\n/interface vlan add interface=BR1 name=GREEN_VLAN vlan-id=10\r\
\n/ip address add interface=GREEN_VLAN address=192.168.10.1/24\r\
\n/ip pool add name=GREEN_POOL ranges=192.168.10.50-192.168.10.254\r\
\n/ip dhcp-server add address-pool=GREEN_POOL interface=GREEN_VLAN name=GR\
EEN_DHCP disabled=no\r\
\n/ip dhcp-server network add address=192.168.10.0/24 dns-server=192.168.1\
0.1 gateway=192.168.10.1\r\
\n\r\
\n# Optional: Create a DHCP instance for BASE_VLAN. Convenience feature fo\
r an admin.\r\
\n /ip pool add name=BASE_POOL ranges=192.168.88.10-192.168.0.254\r\
\n /ip dhcp-server add address-pool=BASE_POOL interface=BASE_VLAN name=BAS\
E_DHCP disabled=no\r\
\n /ip dhcp-server network add address=192.168.88.0/24 dns-server=192.168.\
88.1 gateway=192.168.88.1\r\
\n\r\
\n\r\
\n#######################################\r\
\n# Firewalling & NAT\r\
\n# A good firewall for WAN. Up to you\r\
\n# about how you want LAN to behave.\r\
\n#######################################\r\
\n\r\
\n# Use MikroTik's \"list\" feature for easy rule matchmaking.\r\
\n\r\
\n/interface list add name=WAN\r\
\n/interface list add name=VLAN\r\
\n/interface list add name=BASE\r\
\n\r\
\n/interface list member\r\
\nadd interface=ether1 list=WAN\r\
\nadd interface=BASE_VLAN list=VLAN\r\
\nadd interface=BLUE_VLAN list=VLAN\r\
\nadd interface=GREEN_VLAN list=VLAN\r\
\nadd interface=BASE_VLAN list=BASE\r\
\n\r\
\n# VLAN aware firewall. Order is important.\r\
\n/ip firewall filter\r\
\n\r\
\n\r\
\n##################\r\
\n# INPUT CHAIN\r\
\n##################\r\
\nadd chain=input action=accept connection-state=established,related comme\
nt=\"Allow Estab & Related\"\r\
\n\r\
\n# Allow VLANs to access router services like DNS, Winbox. Naturally, you\
\_SHOULD make it more granular.\r\
\nadd chain=input action=accept in-interface-list=VLAN comment=\"Allow VLA\
N\"\r\
\n\r\
\n# Allow BASE_VLAN full access to the device for Winbox, etc.\r\
\nadd chain=input action=accept in-interface=BASE_VLAN comment=\"Allow Bas\
e_Vlan Full Access\"\r\
\n\r\
\nadd chain=input action=drop comment=\"Drop\"\r\
\n\r\
\n##################\r\
\n# FORWARD CHAIN\r\
\n##################\r\
\nadd chain=forward action=accept connection-state=established,related com\
ment=\"Allow Estab & Related\"\r\
\n\r\
\n# Allow all VLANs to access the Internet only, NOT each other\r\
\nadd chain=forward action=accept connection-state=new in-interface-list=V\
LAN out-interface-list=WAN comment=\"VLAN Internet Access only\"\r\
\n\r\
\nadd chain=forward action=drop comment=\"Drop\"\r\
\n\r\
\n##################\r\
\n# NAT\r\
\n##################\r\
\n/ip firewall nat add chain=srcnat action=masquerade out-interface-list=W\
AN comment=\"Default masquerade\"\r\
\n\r\
\n\r\
\n#######################################\r\
\n# VLAN Security\r\
\n#######################################\r\
\n\r\
\n# Only allow ingress packets without tags on Access Ports\r\
\n/interface bridge port\r\
\nset bridge=BR1 ingress-filtering=yes frame-types=admit-only-untagged-and\
-priority-tagged [find interface=ether2]\r\
\nset bridge=BR1 ingress-filtering=yes frame-types=admit-only-untagged-and\
-priority-tagged [find interface=ether3]\r\
\nset bridge=BR1 ingress-filtering=yes frame-types=admit-only-untagged-and\
-priority-tagged [find interface=ether4]\r\
\nset bridge=BR1 ingress-filtering=yes frame-types=admit-only-untagged-and\
-priority-tagged [find interface=ether5]\r\
\nset bridge=BR1 ingress-filtering=yes frame-types=admit-only-untagged-and\
-priority-tagged [find interface=wlan1]\r\
\nset bridge=BR1 ingress-filtering=yes frame-types=admit-only-untagged-and\
-priority-tagged [find interface=wlan2]\r\
\n\r\
\n\r\
\n#######################################\r\
\n# MAC Server settings\r\
\n#######################################\r\
\n\r\
\n# Ensure only visibility and availability from BASE_VLAN, the MGMT netwo\
rk\r\
\n/ip neighbor discovery-settings set discover-interface-list=BASE\r\
\n/tool mac-server mac-winbox set allowed-interface-list=BASE\r\
\n/tool mac-server set allowed-interface-list=BASE\r\
\n\r\
\n\r\
\n#######################################\r\
\n# Turn on VLAN mode\r\
\n#######################################\r\
\n/interface bridge set BR1 vlan-filtering=yes\r\
\n"
/tool mac-server
set allowed-interface-list=BASE
/tool mac-server mac-winbox
set allowed-interface-list=BASE
One other thing: I started this config using an example found in another thread and it seems that much of the original config still seems to be there, though in a commented out form (\n). Any idea how I can clean up this config file?

