IPS1(ppoe) => LAN1
ISP2(ppoe2) => LAN2
LAN1 clients go through ISP1 only and LAN2 through ISP2
But when i try to ping lan1 client from lan2 or vice versa, nothing works.
Can you help me figure it out?
Code: Select all
# jan/02/1970 09:49:11 by RouterOS 6.49
# software id = 342Z-DE8Y
#
# model = RB760iGS
# serial number = E1F10D0B5C2B
/interface ethernet
set [ find default-name=ether1 ] name=ether1-wan1
set [ find default-name=ether2 ] name=ether2-wan2
/interface pppoe-client
add disabled=no interface=ether1-wan1 name=pppoe-amigo
add disabled=no interface=ether2-wan2 name=pppoe-byfly
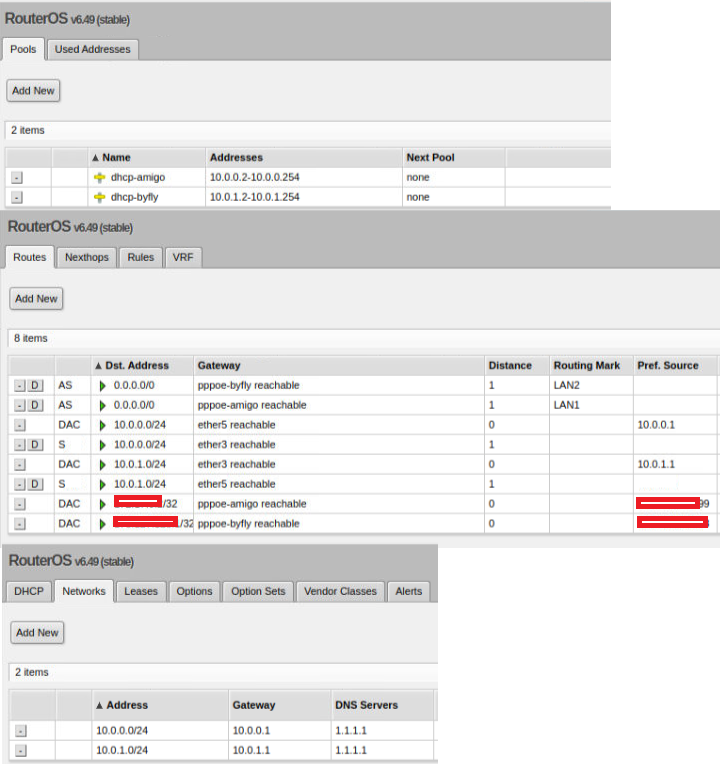
/ip pool
add name=dhcp-amigo ranges=10.0.0.2-10.0.0.254
add name=dhcp-byfly ranges=10.0.1.2-10.0.1.254
/ip dhcp-server
add address-pool=dhcp-byfly disabled=no interface=ether3 name=dhcp-byfly
add address-pool=dhcp-amigo disabled=no interface=ether5 name=dhcp-amigo
/interface bridge settings
set use-ip-firewall=yes use-ip-firewall-for-pppoe=yes use-ip-firewall-for-vlan=yes
/ip address
add address=10.0.0.1/24 interface=ether5 network=10.0.0.0
add address=10.0.1.1/24 interface=ether3 network=10.0.1.0
/ip dhcp-server lease
add address=10.0.1.242 client-id=1:52:3e:aa:f1:41:14 mac-address=52:3E:AA:F1:41:14 server=dhcp-byfly
add address=10.0.1.241 client-id=1:52:3e:aa:f2:ea:3d mac-address=52:3E:AA:F2:EA:3D server=dhcp-byfly
add address=10.0.0.2 client-id=1:50:3e:aa:6:df:a7 mac-address=50:3E:AA:06:DF:A7 server=dhcp-amigo
add address=10.0.1.9 client-id=1:50:3e:aa:6:df:a7 mac-address=50:3E:AA:06:DF:A7 server=dhcp-byfly
add address=10.0.0.4 client-id=1:52:3e:aa:f1:41:14 mac-address=52:3E:AA:F1:41:14 server=dhcp-amigo
add address=10.0.0.5 client-id=1:52:3e:aa:f2:ea:3d mac-address=52:3E:AA:F2:EA:3D server=dhcp-amigo
/ip dhcp-server network
add address=10.0.0.0/24 dns-server=1.1.1.1 gateway=10.0.0.1
add address=10.0.1.0/24 dns-server=1.1.1.1 gateway=10.0.1.1
/ip firewall filter
add action=accept chain=forward dst-address=10.0.1.0/24 src-address=10.0.0.0/24
add action=accept chain=forward dst-address=10.0.0.0/24 src-address=10.0.1.0/24
/ip firewall mangle
add action=mark-routing chain=prerouting new-routing-mark=LAN1 passthrough=yes src-address=10.0.0.0/24
add action=mark-routing chain=prerouting new-routing-mark=LAN2 passthrough=yes src-address=10.0.1.0/24
/ip firewall nat
add action=masquerade chain=srcnat out-interface=ether3
add action=masquerade chain=srcnat out-interface=ether5
add action=masquerade chain=srcnat out-interface=pppoe-amigo protocol=tcp
add action=masquerade chain=srcnat out-interface=pppoe-byfly
add action=dst-nat chain=dstnat in-interface=pppoe-byfly protocol=tcp to-addresses=10.0.1.241 to-ports=36100
/ip route
add distance=1 gateway=pppoe-amigo routing-mark=LAN1
add distance=1 gateway=pppoe-byfly routing-mark=LAN2
add distance=1 dst-address=10.0.0.0/24 gateway=ether3
add distance=1 dst-address=10.0.1.0/24 gateway=ether5
/system routerboard settings
set auto-upgrade=yes silent-boot=yes