Hi people, I need to redesign our network following the attached diagram as we have 2 transit ISPs connected respectively to 2 CCR cloud cores.
I would like to ask two things:
Can the IPs of the OSFP area be private or do they have to be public? We have to announce a subnet / 24 via our ASN and I would be sorry to lose several for the OSFP area
For loopback IPs we will use public addresses
I wonder why doing some tests in the laboratory with the private OSFP area IPs by disconnecting a carrier on Router 1 it is no longer reachable from the Router 2 Transit. This is because in the Router the NAT is disabled so R1 contacts R2 from the natted IP. R2 doesn't have NAT and can't manage it ...
The second point is the Route Reflector .. I have activated 2 peers, one on Router1 and one on Router2. On the Route Reflector there is an IGBP that goes to the loopbacks of the respective routers. The session goes up correctly but the PC connected to the Reflector router has an additional HOP when it browses.
Example:
Router 1: 1.1.1.1
Router 2: 1.1.1.2
Router Reflector: 1.1.1.3
If I do a traceroute from the PC connected to the reflector I see
1.1.1.3> 1.1.1.1> IP OF PTP ISP>
Is there any way to skip 1.1.1.1 and go directly to the ISP Transit PTP? On the peer of router1 and router2 I have activated the Route Reflect and the Next Hop but it doesn't work anyway ...
Thank you all
-

-
connectlife
Member Candidate

- Posts: 100
- Joined:
2 ISP + 2 Router with BGP and OSFP
You do not have the required permissions to view the files attached to this post.
-

-
StubArea51
Trainer

- Posts: 1739
- Joined:
- Location: stubarea51.net
- Contact:
Re: 2 ISP + 2 Router with BGP and OSFP
The first question I would have is - what kind of network are you running - ISP, Data Center, Enterprise or other?
The short answer is, yes, you don't need the links between routers inside of an ASN to be public. You can always assign a single /32 IPv4 public address as a loopback if needed.
An IPv4 range that we commonly use for PTP and transit link between routers is 100.64.0.0/10 - while it's not strictly outlined for that purpose (it's defined for CGNAT in RFC 6598 - https://datatracker.ietf.org/doc/html/rfc6598)
When the RFC was developed/written (10+ years ago),it was assumed that IPv6 would gain significant momentum and become the dominant version of IP within 3 to 5 years. Obviously that hasn't happened yet, so people tend to use some of the more obscure ranges when IPv4 is needed. Notable examples that use 100.64.0.0/10 are: Google corporate, Lumen L3 VPNs, Taliscale VPNs). We've used it in 1000+ client networks over the last decade and it works without issue.
Using 100.64.0.0/10 addressing for links between routers keeps you completely out of RFC1918 private space.
Here is an example of what that addressing would look like:
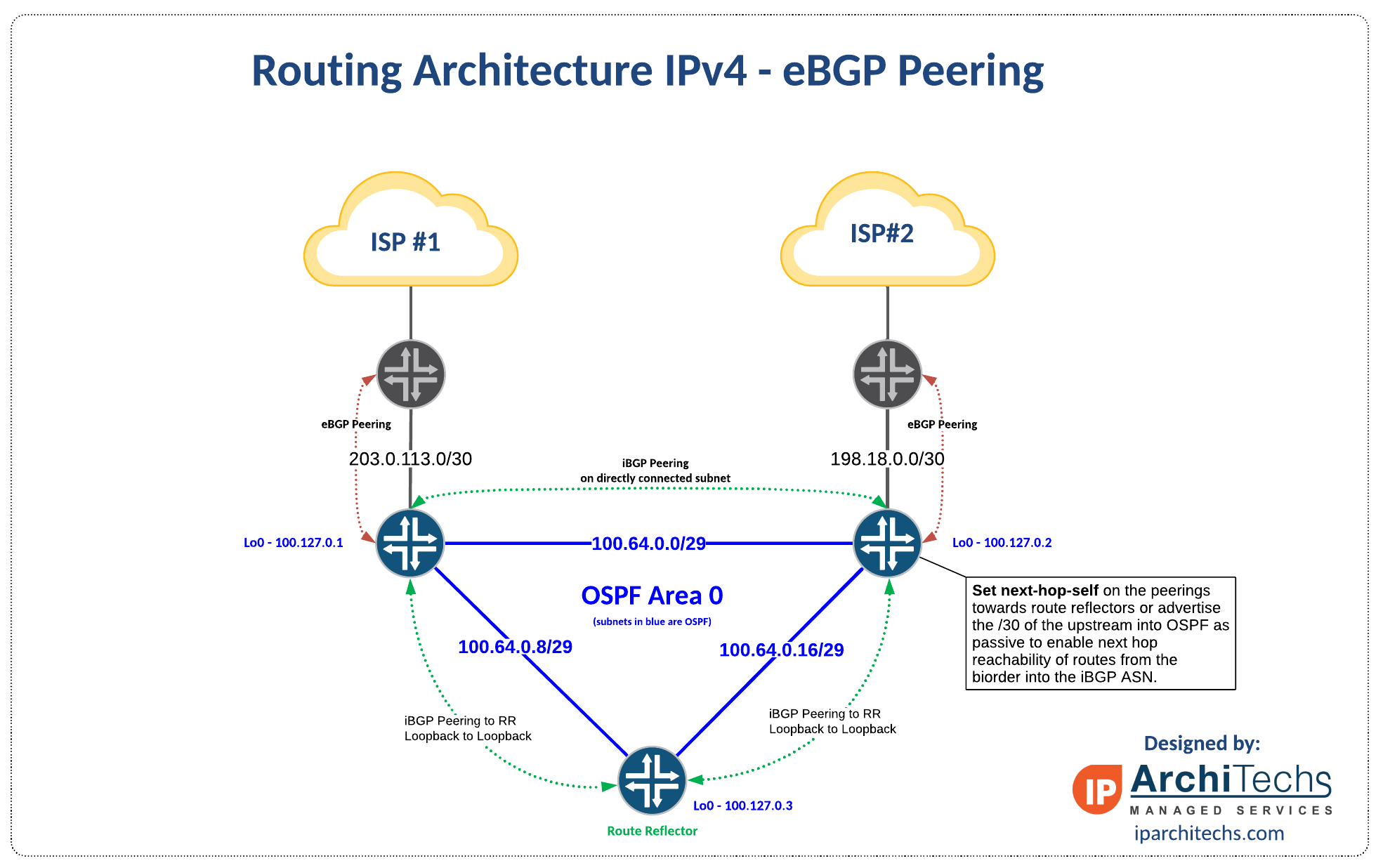
EDIT: I didn't see that you already referenced the drawing I did
There are two ways to deal with this - use mangle to try and set the ICMP source to a public loopback (haven't tied so i'm not sure this is doable) or use mangle/firewall filter to just drop ICMP replies for the hops you don't want to respond
The short answer is, yes, you don't need the links between routers inside of an ASN to be public. You can always assign a single /32 IPv4 public address as a loopback if needed.
An IPv4 range that we commonly use for PTP and transit link between routers is 100.64.0.0/10 - while it's not strictly outlined for that purpose (it's defined for CGNAT in RFC 6598 - https://datatracker.ietf.org/doc/html/rfc6598)
When the RFC was developed/written (10+ years ago),it was assumed that IPv6 would gain significant momentum and become the dominant version of IP within 3 to 5 years. Obviously that hasn't happened yet, so people tend to use some of the more obscure ranges when IPv4 is needed. Notable examples that use 100.64.0.0/10 are: Google corporate, Lumen L3 VPNs, Taliscale VPNs). We've used it in 1000+ client networks over the last decade and it works without issue.
Using 100.64.0.0/10 addressing for links between routers keeps you completely out of RFC1918 private space.
Here is an example of what that addressing would look like:

EDIT: I didn't see that you already referenced the drawing I did
There are two ways to deal with this - use mangle to try and set the ICMP source to a public loopback (haven't tied so i'm not sure this is doable) or use mangle/firewall filter to just drop ICMP replies for the hops you don't want to respond
Last edited by StubArea51 on Thu Nov 11, 2021 5:53 pm, edited 1 time in total.
-

-
connectlife
Member Candidate

- Posts: 100
- Joined:
Re: 2 ISP + 2 Router with BGP and OSFP
Hi, we are an ISP
we are currently set up like this:
Loopback IP Router 1: 5.133.xx.252
Loopback IP Router 2: 5.133.xx.253
R1 IP to R2: 100.64.0.1/29 (ether2)
R2 IP to R1: 100.64.0.2/29 (ether2)
The iGP session between R1 and R2 is ok
On the R2 routing table I have a situation like this:
----------------------------------------------------------------------------
0 ADb 0.0.0.0/0 100.64.0.1 200
1 Db 0.0.0.0/0 2.2.2.1 20
2 ADo 1.1.1.0/30 100.64.0.1 110
3 ADC 2.2.2.0/30 2.2.2.2 ether1 0
----------------------------------------------------------------------------
if the peer at the BGP transit is OK the traffic switches to 2.2.2.1, everything is ok
If the BGP peer drops the traffic goes to 100.64.0.1 (IP of the ether2 of R1)
Here the traffic does not pass because on R1 the NAT is off .. If I turn on the NAT and activate a Masquerade rule the traffic passes ...
If instead of 100.64.0.1 I put an IP of the public class eg 5.133.xx.240 (R1) and 5.133.xx.241 (R2) the traffic passes because it does not NAT ..
Why this behavior?
Thanks friend
we are currently set up like this:
Loopback IP Router 1: 5.133.xx.252
Loopback IP Router 2: 5.133.xx.253
R1 IP to R2: 100.64.0.1/29 (ether2)
R2 IP to R1: 100.64.0.2/29 (ether2)
The iGP session between R1 and R2 is ok
On the R2 routing table I have a situation like this:
----------------------------------------------------------------------------
0 ADb 0.0.0.0/0 100.64.0.1 200
1 Db 0.0.0.0/0 2.2.2.1 20
2 ADo 1.1.1.0/30 100.64.0.1 110
3 ADC 2.2.2.0/30 2.2.2.2 ether1 0
----------------------------------------------------------------------------
if the peer at the BGP transit is OK the traffic switches to 2.2.2.1, everything is ok
If the BGP peer drops the traffic goes to 100.64.0.1 (IP of the ether2 of R1)
Here the traffic does not pass because on R1 the NAT is off .. If I turn on the NAT and activate a Masquerade rule the traffic passes ...
If instead of 100.64.0.1 I put an IP of the public class eg 5.133.xx.240 (R1) and 5.133.xx.241 (R2) the traffic passes because it does not NAT ..
Why this behavior?
Thanks friend
Who is online
Users browsing this forum: No registered users and 10 guests
