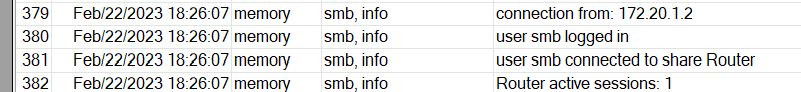
Once connected with Wireguard I can access to the entire hAP ax3 network, but not to the active sharing in the router.
Have I forgotten something in firewall?
Thanks for your help.
Code: Select all
# feb/22/2023 16:19:38 by RouterOS 7.8rc3
# software id = BH9H-NUQS
#
# model = C53UiG+5HPaxD2HPaxD
# serial number = HDG08XXXXXX
/container mounts
add dst=/minidlna name=DLNA src=/usb1/containers/minidlna-data
add dst=/Film name="DLNA Media" src=/usb1/Dati/Film
/interface bridge
add admin-mac=48:A9:8A:0E:18:EB auto-mac=no comment=defconf name=bridge
/interface wifiwave2
set [ find default-name=wifi1 ] channel.band=5ghz-ax .frequency=5180-5500 \
.skip-dfs-channels=10min-cac .width=20/40/80mhz configuration.country=\
Italy .mode=ap .ssid=MikroTik disabled=no security.authentication-types=\
wpa2-psk .management-protection=disabled .wps=disable
set [ find default-name=wifi2 ] channel.band=2ghz-ax .skip-dfs-channels=\
10min-cac .width=20/40mhz configuration.country=Italy .mode=ap .ssid=\
MikroTik disabled=no security.authentication-types=wpa2-psk \
.management-protection=disabled .wps=disable
/interface veth
add address=192.168.10.3/24 gateway=192.168.10.1 name=veth1
/interface wireguard
add listen-port=31077 mtu=1420 name=wireguard1
/interface vlan
add interface=ether1 name=vlan835 vlan-id=835
/interface pppoe-client
add add-default-route=yes disabled=no interface=vlan835 name=pppoe-out1 \
use-peer-dns=yes user=user
/interface list
add comment=defconf name=WAN
add comment=defconf name=LAN
/ip pool
add name=default-dhcp ranges=192.168.10.10-192.168.10.254
/ip dhcp-server
add add-arp=yes address-pool=default-dhcp interface=bridge name=defconf
/port
set 0 name=serial0
/queue type
add kind=fq-codel name="fq codel"
/queue tree
add max-limit=295M name="FTTH Upload" packet-mark=no-mark parent=pppoe-out1 \
queue="fq codel"
/container
add envlist=DLNA interface=veth1 mounts="DLNA,DLNA Media" root-dir=\
usb1/containers/minidlna start-on-boot=yes
/container config
set registry-url=https://registry-1.docker.io tmpdir=/usb1/containers/tmp
/container envs
add key=MINIDLNA_MEDIA_DIR name=DLNA value=/Film
add key=MINIDLNA_FRIENDLY_NAME name=DLNA value="Router MikroTik"
add key=MINIDLNA_ROOT_CONTAINER name=DLNA value=B
/interface bridge port
add bridge=bridge comment=defconf interface=ether2
add bridge=bridge comment=defconf interface=ether3
add bridge=bridge comment=defconf interface=ether4
add bridge=bridge comment=defconf interface=ether5
add bridge=bridge comment=defconf interface=wifi1
add bridge=bridge comment=defconf interface=wifi2
add bridge=bridge comment="minidlna container" interface=veth1
/ip neighbor discovery-settings
set discover-interface-list=LAN
/interface list member
add comment=defconf interface=bridge list=LAN
add comment=defconf interface=ether1 list=WAN
add comment="FTTH" interface=pppoe-out1 list=WAN
/interface wireguard peers
add allowed-address=172.20.1.2/32 interface=wireguard1 public-key=\
"cut"
/ip address
add address=192.168.10.1/24 comment=defconf interface=bridge network=\
192.168.10.0
add address=172.20.1.1/24 comment=WireGuard interface=wireguard1 network=\
172.20.1.0
/ip cloud
set ddns-enabled=yes
/ip dhcp-client
add comment=defconf disabled=yes interface=ether1
/ip dhcp-server lease
add address=192.168.10.10 client-id=1:70:85:c2:62:34:b2 comment="PC" \
mac-address=70:85:C2:62:34:B2 server=defconf
/ip dhcp-server network
add address=192.168.10.0/24 comment=defconf dns-server=192.168.10.1 gateway=\
192.168.10.1
/ip dns
set allow-remote-requests=yes
/ip dns static
add address=192.168.10.1 comment=defconf name=router.lan
/ip firewall filter
add action=accept chain=input comment="allow WireGuard" dst-port=31077 \
protocol=udp
add action=accept chain=input comment="allow WireGuard traffic" src-address=\
172.20.1.0/24
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=accept chain=input comment=\
"defconf: accept to local loopback (for CAPsMAN)" dst-address=127.0.0.1
add action=drop chain=input comment="defconf: drop all not coming from LAN" \
in-interface-list=!LAN
add action=accept chain=forward comment="defconf: accept in ipsec policy" \
ipsec-policy=in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" \
ipsec-policy=out,ipsec
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related hw-offload=yes
add action=accept chain=forward comment=\
"defconf: accept established,related, untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=drop chain=forward comment=\
"defconf: drop all from WAN not DSTNATed" connection-nat-state=!dstnat \
connection-state=new in-interface-list=WAN
/ip firewall nat
add action=masquerade chain=srcnat comment="defconf: masquerade" \
ipsec-policy=out,none out-interface-list=WAN
/ip service
set telnet disabled=yes
set ftp disabled=yes
set ssh disabled=yes
set api disabled=yes
set api-ssl disabled=yes
/ip smb
set allow-guests=no domain=WORKGROUP enabled=yes interfaces=bridge,wireguard1
/ip smb shares
set [ find default=yes ] disabled=yes
add directory=usb1/Dati name=Router
/ip smb users
add name=smb read-only=no
/ip upnp
set enabled=yes
/ip upnp interfaces
add interface=bridge type=internal
add interface=pppoe-out1 type=external
/ipv6 firewall address-list
add address=::/128 comment="defconf: unspecified address" list=bad_ipv6
add address=::1/128 comment="defconf: lo" list=bad_ipv6
add address=fec0::/10 comment="defconf: site-local" list=bad_ipv6
add address=::ffff:0.0.0.0/96 comment="defconf: ipv4-mapped" list=bad_ipv6
add address=::/96 comment="defconf: ipv4 compat" list=bad_ipv6
add address=100::/64 comment="defconf: discard only " list=bad_ipv6
add address=2001:db8::/32 comment="defconf: documentation" list=bad_ipv6
add address=2001:10::/28 comment="defconf: ORCHID" list=bad_ipv6
add address=3ffe::/16 comment="defconf: 6bone" list=bad_ipv6
/ipv6 firewall filter
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMPv6" protocol=\
icmpv6
add action=accept chain=input comment="defconf: accept UDP traceroute" port=\
33434-33534 protocol=udp
add action=accept chain=input comment=\
"defconf: accept DHCPv6-Client prefix delegation." dst-port=546 protocol=\
udp src-address=fe80::/10
add action=accept chain=input comment="defconf: accept IKE" dst-port=500,4500 \
protocol=udp
add action=accept chain=input comment="defconf: accept ipsec AH" protocol=\
ipsec-ah
add action=accept chain=input comment="defconf: accept ipsec ESP" protocol=\
ipsec-esp
add action=accept chain=input comment=\
"defconf: accept all that matches ipsec policy" ipsec-policy=in,ipsec
add action=drop chain=input comment=\
"defconf: drop everything else not coming from LAN" in-interface-list=\
!LAN
add action=accept chain=forward comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=drop chain=forward comment=\
"defconf: drop packets with bad src ipv6" src-address-list=bad_ipv6
add action=drop chain=forward comment=\
"defconf: drop packets with bad dst ipv6" dst-address-list=bad_ipv6
add action=drop chain=forward comment="defconf: rfc4890 drop hop-limit=1" \
hop-limit=equal:1 protocol=icmpv6
add action=accept chain=forward comment="defconf: accept ICMPv6" protocol=\
icmpv6
add action=accept chain=forward comment="defconf: accept HIP" protocol=139
add action=accept chain=forward comment="defconf: accept IKE" dst-port=\
500,4500 protocol=udp
add action=accept chain=forward comment="defconf: accept ipsec AH" protocol=\
ipsec-ah
add action=accept chain=forward comment="defconf: accept ipsec ESP" protocol=\
ipsec-esp
add action=accept chain=forward comment=\
"defconf: accept all that matches ipsec policy" ipsec-policy=in,ipsec
add action=drop chain=forward comment=\
"defconf: drop everything else not coming from LAN" in-interface-list=\
!LAN
/system clock
set time-zone-name=Europe/Rome
/system package update
set channel=testing
/tool e-mail
/tool mac-server
set allowed-interface-list=LAN
/tool mac-server mac-winbox
set allowed-interface-list=LAN