I'm looking to set up a Backup LTE connection for my home network.
Primarily for getting in remotely, for example a LTE Enabled VPN server which I can connect to from outside over its public IP.
I already have a provider in my country identified which would give me a public not NATed un Firewalled public IP v4 on a pre payed LTE plan.
I would like the most a VPN which works from a windows client without any extra clients and which is not easily blocked, like SSTP.
The VPN server would need toe ability to detect its own IP and update a dyndns host accordingly.
To get the best reliability I think it should be one device that does the VPN server and LTE connectivity.
Alternatively I would like the option to set up the LTE box to bridge the obtained IP to a Ethernet port such that i can plug there in anything and its gets the IP assigned via DHCP and has full open network connectivity. Such that I can connect some other router and/or vpn server.
So what Miktorik hardware would be best for this job?
-

-
TraxXavier
just joined
- Posts: 21
- Joined:
LTE Backup Connection, configuration and setup
Last edited by TraxXavier on Thu Aug 29, 2024 10:37 am, edited 1 time in total.
Re: LTE Backup Connection, which hardware would be best?
Depends on the traffic requirements you have for that LTE link and how good/bad reception is in the area where you want to use it.
A simple AX Lite LTE may already be enough (I use it as road warrior device so not stationary installed, always have it with me in my backpack).
A simple AX Lite LTE may already be enough (I use it as road warrior device so not stationary installed, always have it with me in my backpack).
-

-
TraxXavier
just joined
- Posts: 21
- Joined:
Re: LTE Backup Connection, which hardware would be best?
I live in Vienna and the reception is quite good here.
Traffic, not much 4k remote desktop that's all.
I'm looking forward to use it with a 30GB/365-Days plan for only 40€/year.
btw: How easy is this Router OS to configure?
Traffic, not much 4k remote desktop that's all.
I'm looking forward to use it with a 30GB/365-Days plan for only 40€/year.
btw: How easy is this Router OS to configure?
Re: LTE Backup Connection, which hardware would be best?
Easy and RouterOS usually don't go in the same sentence 
The learning curve is quite steep but once you get how it works, it's amazing what you can do with these devices.
Only keeping that link alive via Wireguard towards my home was a couple of Gb per month, not doing anything. So be careful if you only have 30Gb/year.
And Wireguard is considered one of the least chatty VPN protocols, others consume a lot more.
Ofcourse if you only activate that VPN on dial-up basis, your LTE only needs to listen. It will not send that much.
So that will result in a lot less traffic.
The learning curve is quite steep but once you get how it works, it's amazing what you can do with these devices.
I used to have an SXT LTE in vacation house in South of France with remote access for management and control.I'm looking forward to use it with a 30GB/365-Days plan for only 40€/year.
Only keeping that link alive via Wireguard towards my home was a couple of Gb per month, not doing anything. So be careful if you only have 30Gb/year.
And Wireguard is considered one of the least chatty VPN protocols, others consume a lot more.
Ofcourse if you only activate that VPN on dial-up basis, your LTE only needs to listen. It will not send that much.
So that will result in a lot less traffic.
-

-
JohnTRIVOLTA
Member

- Posts: 417
- Joined:
- Location: BG/Sofia
Re: LTE Backup Connection, which hardware would be best?
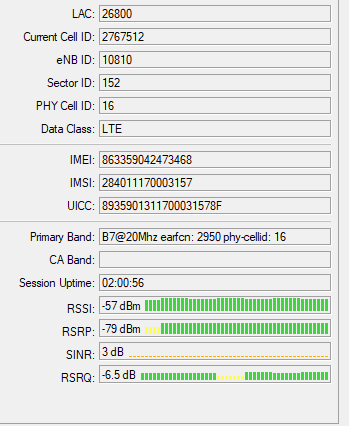
I use in my home network hAP AX Lite LTE /L41G-2axD&FG621-EA/.I have good cell signal coverage and this device meets my needs!

-

-
TraxXavier
just joined
- Posts: 21
- Joined:
Re: LTE Backup Connection, which hardware would be best?
Yea I have a proper fiber internet connection for the everyday use the LTE is only in case the main internet goes down or the modem needs power cycling, or something that cant be resolved remotely, BSOD on the home server which does the everyday Routing and VPN, etc....I used to have an SXT LTE in vacation house in South of France with remote access for management and control.
Only keeping that link alive via Wireguard towards my home was a couple of Gb per month, not doing anything. So be careful if you only have 30Gb/year.
And Wireguard is considered one of the least chatty VPN protocols, others consume a lot more.
Ofcourse if you only activate that VPN on dial-up basis, your LTE only needs to listen. It will not send that much.
So that will result in a lot less traffic.
So the traffic should be minimal normally.
-

-
TraxXavier
just joined
- Posts: 21
- Joined:
Re: LTE Backup Connection, which hardware would be best?
So I got the AX Lite LTE6 and set it up to use LTE for WAN, it has a LAN on ports 2,3,4 (192.168.x.x) and port 1 is connected to my regular network, excluded from the bridge, it gets a 10.x.x.x ip
when I setup port forwarding to the LAN it works fine but when i try to worward to a 10.x.x.x IP it does not.
How should I configure the port forwarding for the described use case such that it works?
The goal is to be able to RDP into PC's in the 10.x.x.x through the LTE connection but not to provide actual internet connectivity to this network as it has an own fast fiber connection, the RDP over LTE is needed in case the main internet goes down and some remote troubleshooting is required to get the main network back up and running.
when I setup port forwarding to the LAN it works fine but when i try to worward to a 10.x.x.x IP it does not.
How should I configure the port forwarding for the described use case such that it works?
The goal is to be able to RDP into PC's in the 10.x.x.x through the LTE connection but not to provide actual internet connectivity to this network as it has an own fast fiber connection, the RDP over LTE is needed in case the main internet goes down and some remote troubleshooting is required to get the main network back up and running.
Re: LTE Backup Connection, which hardware would be best?
By default ether1 is WAN on most Mikrotik devices, it is possible that you did not change its categorization to LAN?
If this is the case, likely you have some firewall rules that block the connection.
Follow the instructions in this post:
viewtopic.php?t=203686#p1051720
and post your configuration, so that some forum member may be able to give you some more accurate advice.
If this is the case, likely you have some firewall rules that block the connection.
Follow the instructions in this post:
viewtopic.php?t=203686#p1051720
and post your configuration, so that some forum member may be able to give you some more accurate advice.
-

-
TraxXavier
just joined
- Posts: 21
- Joined:
Re: LTE Backup Connection, which hardware would be best?
I have set it to be LAN as well, and here is the config
Code: Select all
# 2024-08-28 22:26:18 by RouterOS 7.12.2
# software id =
#
# model = L41G-2axD&FG621-EA
# serial number =
/interface bridge
add admin-mac=... auto-mac=no comment=defconf name=bridge
/interface wifiwave2
set [ find default-name=wifi1 ] channel.band=2ghz-ax .skip-dfs-channels=\
10min-cac .width=20/40mhz configuration.mode=ap .ssid=MikroTik-1E02AB \
security.authentication-types=wpa2-psk,wpa3-psk
/interface lte
set [ find default-name=lte1 ] allow-roaming=no band=""
/interface list
add comment=defconf name=WAN
add comment=defconf name=LAN
/interface lte apn
set [ find default=yes ] apn=webipaut use-network-apn=no
/ip pool
add name=default-dhcp ranges=192.168.88.10-192.168.88.254
/ip dhcp-server
add address-pool=default-dhcp interface=bridge lease-time=10m name=defconf
/interface bridge port
add bridge=bridge comment=defconf interface=ether2
add bridge=bridge comment=defconf interface=ether3
add bridge=bridge comment=defconf interface=ether4
add bridge=bridge comment=defconf interface=wifi1
/ip neighbor discovery-settings
set discover-interface-list=LAN
/interface list member
add comment=defconf interface=bridge list=LAN
add comment=defconf interface=lte1 list=WAN
add interface=ether1 list=LAN
/ip address
add address=192.168.88.1/24 comment=defconf interface=bridge network=\
192.168.88.0
/ip cloud
set ddns-enabled=yes
/ip dhcp-client
add interface=ether1
/ip dhcp-server network
add address=192.168.88.0/24 comment=defconf dns-server=192.168.88.1 gateway=\
192.168.88.1
/ip dns
set allow-remote-requests=yes
/ip dns static
add address=192.168.88.1 comment=defconf name=router.lan
/ip firewall filter
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=accept chain=input comment=\
"defconf: accept to local loopback (for CAPsMAN)" dst-address=127.0.0.1
add action=drop chain=input comment="defconf: drop all not coming from LAN" \
in-interface-list=!LAN
add action=accept chain=forward comment="defconf: accept in ipsec policy" \
ipsec-policy=in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" \
ipsec-policy=out,ipsec
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related hw-offload=yes
add action=accept chain=forward comment=\
"defconf: accept established,related, untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=drop chain=forward comment=\
"defconf: drop all from WAN not DSTNATed" connection-nat-state=!dstnat \
connection-state=new in-interface-list=WAN
/ip firewall nat
add action=masquerade chain=srcnat comment="defconf: masquerade" \
ipsec-policy=out,none out-interface-list=WAN
add action=dst-nat chain=dstnat dst-port=5900 in-interface=lte1 protocol=tcp \
to-addresses=10.70.10.41 to-ports=5900
/ip service
set www-ssl disabled=no
/ipv6 firewall address-list
add address=::/128 comment="defconf: unspecified address" list=bad_ipv6
add address=::1/128 comment="defconf: lo" list=bad_ipv6
add address=fec0::/10 comment="defconf: site-local" list=bad_ipv6
add address=::ffff:0.0.0.0/96 comment="defconf: ipv4-mapped" list=bad_ipv6
add address=::/96 comment="defconf: ipv4 compat" list=bad_ipv6
add address=100::/64 comment="defconf: discard only " list=bad_ipv6
add address=2001:db8::/32 comment="defconf: documentation" list=bad_ipv6
add address=2001:10::/28 comment="defconf: ORCHID" list=bad_ipv6
add address=3ffe::/16 comment="defconf: 6bone" list=bad_ipv6
/ipv6 firewall filter
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMPv6" protocol=\
icmpv6
add action=accept chain=input comment="defconf: accept UDP traceroute" port=\
33434-33534 protocol=udp
add action=accept chain=input comment=\
"defconf: accept DHCPv6-Client prefix delegation." dst-port=546 protocol=\
udp src-address=fe80::/10
add action=accept chain=input comment="defconf: accept IKE" dst-port=500,4500 \
protocol=udp
add action=accept chain=input comment="defconf: accept ipsec AH" protocol=\
ipsec-ah
add action=accept chain=input comment="defconf: accept ipsec ESP" protocol=\
ipsec-esp
add action=accept chain=input comment=\
"defconf: accept all that matches ipsec policy" ipsec-policy=in,ipsec
add action=drop chain=input comment=\
"defconf: drop everything else not coming from LAN" in-interface-list=\
!LAN
add action=accept chain=forward comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=drop chain=forward comment=\
"defconf: drop packets with bad src ipv6" src-address-list=bad_ipv6
add action=drop chain=forward comment=\
"defconf: drop packets with bad dst ipv6" dst-address-list=bad_ipv6
add action=drop chain=forward comment="defconf: rfc4890 drop hop-limit=1" \
hop-limit=equal:1 protocol=icmpv6
add action=accept chain=forward comment="defconf: accept ICMPv6" protocol=\
icmpv6
add action=accept chain=forward comment="defconf: accept HIP" protocol=139
add action=accept chain=forward comment="defconf: accept IKE" dst-port=\
500,4500 protocol=udp
add action=accept chain=forward comment="defconf: accept ipsec AH" protocol=\
ipsec-ah
add action=accept chain=forward comment="defconf: accept ipsec ESP" protocol=\
ipsec-esp
add action=accept chain=forward comment=\
"defconf: accept all that matches ipsec policy" ipsec-policy=in,ipsec
add action=drop chain=forward comment=\
"defconf: drop everything else not coming from LAN" in-interface-list=\
!LAN
/system clock
set time-zone-name=Europe/Vienna
/system note
set show-at-login=no
/tool mac-server
set allowed-interface-list=LAN
/tool mac-server mac-winbox
set allowed-interface-list=LAN
/tool sms
set port=lte1 receive-enabled=yes
/tool sniffer
set filter-dst-port=vnc-2 filter-ip-protocol=tcp
-

-
TraxXavier
just joined
- Posts: 21
- Joined:
Re: LTE Backup Connection, which hardware would be best?
I have narrowed down the issue, watching the traffic with wireshark on the target machine the incomming traffic is redirected properly, but it keeps its publilc IP and the target machine ofcause uses a different default gateway, so not sure how to fix that actually :/
Can this even be fixed? the microtik router would need to replace the public IP of the requesting client with some 10.70.x.x of its own so that the answer arrives and so on...
EDIT: its working its working i just needed to add a masquarade rule for the LAN list as well,
how i wonder should i create a separate list for the port 1 instead of keeping it in the LAN list?
Can this even be fixed? the microtik router would need to replace the public IP of the requesting client with some 10.70.x.x of its own so that the answer arrives and so on...
EDIT: its working its working i just needed to add a masquarade rule for the LAN list as well,
how i wonder should i create a separate list for the port 1 instead of keeping it in the LAN list?
-

-
TraxXavier
just joined
- Posts: 21
- Joined:
Re: LTE Backup Connection, which hardware would be best?
Next problem:
I have setup L2TP VPN, for it a created a new address pool 10.70.2.200/29
when i connect to the VPN from outside and attempt to connect to clients on the 10.x.x.x network the clients see the one router IP not the IP of the client, same as when using port forwarding with masquerade. When I disable the masquerade rule i cant connect to any 10.x.x.x from the VPN.
I have set up a new network bridge containing only the ethernet 1 port but that did not help eider.
the client sees the request comming from a VPN address 10.70.2.207 but it seams it can not answer i.e. the microtic router does not claim the 10.70.2.207 IP
how can i fix this issue?
EDIT: when i switch the VPN to use the regular lan pool 192.168.x.x where i woudl assume all should work normally i have the same issue
I have setup L2TP VPN, for it a created a new address pool 10.70.2.200/29
when i connect to the VPN from outside and attempt to connect to clients on the 10.x.x.x network the clients see the one router IP not the IP of the client, same as when using port forwarding with masquerade. When I disable the masquerade rule i cant connect to any 10.x.x.x from the VPN.
I have set up a new network bridge containing only the ethernet 1 port but that did not help eider.
the client sees the request comming from a VPN address 10.70.2.207 but it seams it can not answer i.e. the microtic router does not claim the 10.70.2.207 IP
how can i fix this issue?
EDIT: when i switch the VPN to use the regular lan pool 192.168.x.x where i woudl assume all should work normally i have the same issue
Code: Select all
# 2024-08-29 09:12:00 by RouterOS 7.12.2
# software id =
#
# model = L41G-2axD&FG621-EA
# serial number =
/interface bridge
add admin-mac=... auto-mac=no comment=defconf name=bridge
add name=vpn-bridge
/interface wifiwave2
set [ find default-name=wifi1 ] channel.band=2ghz-ax .skip-dfs-channels=\
10min-cac .width=20/40mhz configuration.mode=ap .ssid=MikroTik-1E02AB \
security.authentication-types=wpa2-psk,wpa3-psk
/interface lte
set [ find default-name=lte1 ] allow-roaming=no band=""
/interface list
add comment=defconf name=WAN
add comment=defconf name=LAN
/interface lte apn
set [ find default=yes ] apn=webipaut use-network-apn=no
/ip pool
add name=default-dhcp ranges=192.168.88.10-192.168.88.254
add name=vpn-pool ranges=10.70.2.200/29
/ip dhcp-server
add address-pool=default-dhcp interface=bridge lease-time=10m name=defconf
/ppp profile
set *FFFFFFFE bridge=vpn-bridge local-address=vpn-pool remote-address=\
vpn-pool
/interface bridge port
add bridge=bridge comment=defconf interface=ether2
add bridge=bridge comment=defconf interface=ether3
add bridge=bridge comment=defconf interface=ether4
add bridge=bridge comment=defconf interface=wifi1
add bridge=vpn-bridge comment=vpn-bridge interface=ether1
/ip neighbor discovery-settings
set discover-interface-list=LAN
/interface l2tp-server server
set enabled=yes use-ipsec=required
/interface list member
add comment=defconf interface=bridge list=LAN
add comment=defconf interface=lte1 list=WAN
add interface=vpn-bridge list=LAN
/interface sstp-server server
set enabled=yes
/ip address
add address=192.168.88.1/24 comment=defconf interface=bridge network=\
192.168.88.0
/ip cloud
set ddns-enabled=yes
/ip dhcp-client
# DHCP client can not run on slave or passthrough interface!
add interface=ether1
/ip dhcp-server network
add address=192.168.88.0/24 comment=defconf dns-server=192.168.88.1 gateway=\
192.168.88.1
/ip dns
set allow-remote-requests=yes
/ip dns static
add address=192.168.88.1 comment=defconf name=router.lan
/ip firewall filter
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=accept chain=input comment=SSTP-VPN dst-port=443 protocol=tcp
add action=accept chain=input comment=PPTP-VPN dst-port=1723 protocol=tcp
add action=accept chain=input comment=PPTP-VPN protocol=gre
add action=accept chain=input comment=L2TP-VPN dst-port=500,1701,4500 \
protocol=udp
add action=accept chain=input comment=L2TP-VPN protocol=ipsec-esp
add action=accept chain=input comment=\
"defconf: accept to local loopback (for CAPsMAN)" dst-address=127.0.0.1
add action=drop chain=input comment="defconf: drop all not coming from LAN" \
in-interface-list=!LAN
add action=accept chain=forward comment="defconf: accept in ipsec policy" \
ipsec-policy=in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" \
ipsec-policy=out,ipsec
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" \
connection-state=established,related hw-offload=yes
add action=accept chain=forward comment=\
"defconf: accept established,related, untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=drop chain=forward comment=\
"defconf: drop all from WAN not DSTNATed" connection-nat-state=!dstnat \
connection-state=new in-interface-list=WAN
/ip firewall nat
add action=masquerade chain=srcnat comment="defconf: masquerade" \
ipsec-policy=out,none out-interface-list=WAN
add action=dst-nat chain=dstnat disabled=yes dst-port=5900 in-interface=lte1 \
protocol=tcp to-addresses=10.70.0.1 to-ports=5900
add action=masquerade chain=srcnat disabled=yes out-interface-list=LAN
/ipv6 firewall address-list
add address=::/128 comment="defconf: unspecified address" list=bad_ipv6
add address=::1/128 comment="defconf: lo" list=bad_ipv6
add address=fec0::/10 comment="defconf: site-local" list=bad_ipv6
add address=::ffff:0.0.0.0/96 comment="defconf: ipv4-mapped" list=bad_ipv6
add address=::/96 comment="defconf: ipv4 compat" list=bad_ipv6
add address=100::/64 comment="defconf: discard only " list=bad_ipv6
add address=2001:db8::/32 comment="defconf: documentation" list=bad_ipv6
add address=2001:10::/28 comment="defconf: ORCHID" list=bad_ipv6
add address=3ffe::/16 comment="defconf: 6bone" list=bad_ipv6
/ipv6 firewall filter
add action=accept chain=input comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=\
invalid
add action=accept chain=input comment="defconf: accept ICMPv6" protocol=\
icmpv6
add action=accept chain=input comment="defconf: accept UDP traceroute" port=\
33434-33534 protocol=udp
add action=accept chain=input comment=\
"defconf: accept DHCPv6-Client prefix delegation." dst-port=546 protocol=\
udp src-address=fe80::/10
add action=accept chain=input comment="defconf: accept IKE" dst-port=500,4500 \
protocol=udp
add action=accept chain=input comment="defconf: accept ipsec AH" protocol=\
ipsec-ah
add action=accept chain=input comment="defconf: accept ipsec ESP" protocol=\
ipsec-esp
add action=accept chain=input comment=\
"defconf: accept all that matches ipsec policy" ipsec-policy=in,ipsec
add action=drop chain=input comment=\
"defconf: drop everything else not coming from LAN" in-interface-list=\
!LAN
add action=accept chain=forward comment=\
"defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" \
connection-state=invalid
add action=drop chain=forward comment=\
"defconf: drop packets with bad src ipv6" src-address-list=bad_ipv6
add action=drop chain=forward comment=\
"defconf: drop packets with bad dst ipv6" dst-address-list=bad_ipv6
add action=drop chain=forward comment="defconf: rfc4890 drop hop-limit=1" \
hop-limit=equal:1 protocol=icmpv6
add action=accept chain=forward comment="defconf: accept ICMPv6" protocol=\
icmpv6
add action=accept chain=forward comment="defconf: accept HIP" protocol=139
add action=accept chain=forward comment="defconf: accept IKE" dst-port=\
500,4500 protocol=udp
add action=accept chain=forward comment="defconf: accept ipsec AH" protocol=\
ipsec-ah
add action=accept chain=forward comment="defconf: accept ipsec ESP" protocol=\
ipsec-esp
add action=accept chain=forward comment=\
"defconf: accept all that matches ipsec policy" ipsec-policy=in,ipsec
add action=drop chain=forward comment=\
"defconf: drop everything else not coming from LAN" in-interface-list=\
!LAN
/ppp secret
add name=Trax profile=default-encryption
/system clock
set time-zone-name=Europe/Vienna
/system note
set show-at-login=no
/tool mac-server
set allowed-interface-list=LAN
/tool mac-server mac-winbox
set allowed-interface-list=LAN
/tool sms
set port=lte1 receive-enabled=yes
/tool sniffer
set filter-ip-protocol=tcp filter-port=vnc-2
Re: LTE Backup Connection, configuration and setup
Personally I believe that once something is working, the more "narrow" you can make the related rules/settings, the better, so, yes, I would check if the setup works with the masquerade rule attached to the single port you are interested to as opposed to an interface list.
i,e, try;
Ros is telling you that you have an error:
If the idea is that ether1 will get the IP from a DHCP server, either the interface is standalone or you have to attach the dhcp client to the bridge containing ether1 (but cannot say if it is connected to the issue you are now having.
If you do:
you should see a difference in the addresses assigned to ether1 (or to the bridge) when changing the settings.
i,e, try;
Code: Select all
add action=masquerade chain=srcnat out-interface=ether1
Code: Select all
/ip dhcp-client
# DHCP client can not run on slave or passthrough interface!
add interface=ether1
If you do:
Code: Select all
/ip address print-

-
TraxXavier
just joined
- Posts: 21
- Joined:
Re: LTE Backup Connection, configuration and setup
i have fixed the dhcp-client config, changing masquarade to out ether1 makes it no longer work
Re: LTE Backup Connection, configuration and setup
But if you have ether1 in a bridge, likely you have to add the masquerade to the bridge and not to ether1 (which is slave)?i have fixed the dhcp-client config, changing masquarade to out ether1 makes it no longer work
Or it means that you need interface-list=LAN because this way you are masquerading also on the original LAN bridge?
-

-
TraxXavier
just joined
- Posts: 21
- Joined:
Re: LTE Backup Connection, configuration and setup
My goal is to make it work without masquerade, that must be somehow doable

