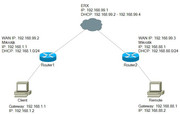
Hello all,
So I been sitting with this one for some time now. Reading the following
https://wiki.mikrotik.com/wiki/Manual:Interface/L2TP,
https://blog.johannfenech.com/mikrotik-l2tp-ipsec-vpn-server/,
https://www.cloudbrigade.com/mikrotik-l2tp-vpn-setup/,
https://jcutrer.com/howto/networking/mikrotik/l2tp-over-ipsec-troubleshooting
and watching videos to help me set this up.
This is not a Site-to-Site L2TP IPSec VPN but a Client to Site setup.
Router 1 will be the Site all Remote clients will connect to. I am currently sitting behind Router 2
Router 1 and Router 2 is Factory reset and both running firmware 6.44.5 LTS
Base setup of Router 1
# model = 750
/interface list
add comment=defconf name=WAN
add comment=defconf name=LAN
/interface wireless security-profiles
set [ find default=yes ] supplicant-identity=MikroTik
/ip pool
add name=dhcp ranges=192.168.1.2-192.168.1.5
/ip dhcp-server
add address-pool=dhcp disabled=no interface=bridge name=defconf
/interface bridge port
add bridge=bridge comment=defconf interface=ether2
add bridge=bridge comment=defconf interface=ether3
add bridge=bridge comment=defconf interface=ether4
add bridge=bridge comment=defconf interface=ether5
/ip neighbor discovery-settings
set discover-interface-list=LAN
/interface list member
add comment=defconf interface=bridge list=LAN
add comment=defconf interface=ether1 list=WAN
/ip address
add address=192.168.1.1/24 comment=defconf interface=ether2 network=192.168.1.0
/ip dhcp-client
add comment=defconf dhcp-options=hostname,clientid disabled=no interface=ether1
/ip dhcp-server network
add address=192.168.1.0/24 comment=defconf gateway=192.168.1.1 netmask=24
/ip dns
set allow-remote-requests=yes
/ip dns static
add address=192.168.1.1 name=router.lan
/ip firewall filter
add action=accept chain=input comment="defconf: accept established,related,untracked" connection-state=established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=invalid
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=drop chain=input comment="defconf: drop all not coming from LAN" in-interface-list=!LAN
add action=accept chain=forward comment="defconf: accept in ipsec policy" ipsec-policy=in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" ipsec-policy=out,ipsec
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" connection-state=established,related
add action=accept chain=forward comment="defconf: accept established,related, untracked" connection-state=established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" connection-state=invalid
add action=drop chain=forward comment="defconf: drop all from WAN not DSTNATed" connection-nat-state=!dstnat connection-state=new in-interface-list=WAN
/ip firewall nat
add action=masquerade chain=srcnat comment="defconf: masquerade" ipsec-policy=out,none out-interface-list=WA
/tool mac-server
set allowed-interface-list=LAN
/tool mac-server mac-winbox
set allowed-interface-list=LAN
The following, working from base setup above, is my attempts to make the L2TP IPSec VPN work.
Attempt 1
/interface l2tp-server server set enabled=yes use-ipsec=required ipsec-secret=Test
/ip pool add name=L2TP_pool ranges=192.168.1.10-192.168.1.15
/ppp profile add name=ipsec_vpn local-address=192.168.1.1 remote-address=L2TP_pool
/ppp secret add name=Test password=password service=l2tp profile=ipsec_vpn
/ip firewall filter add action=accept chain=input protocol=udp dst-port=500,1701,4500 in-interface=ether1 comment="Allow L2TP VPN (500,4500,1701/udp)"
Attempt 2
/ppp profile add name=ipsec_vpn local-address=192.168.1.1 dns-server=192.168.1.1
/interface l2tp-server server set enabled=yes default-profile=ipsec_vpn authentication=mschap1,mschap2,chap
/ip ipsec policy set [ find default=yes ] src-address=0.0.0.0/0 dst-address=0.0.0.0/0 protocol=all proposal=default template=yes
/ip ipsec peer add exchange-mode=main passive=yes name=l2tpserver
/ip ipsec identity add generate-policy=port-override auth-method=pre-shared-key secret=Test peer=l2tpserver
/ip ipsec proposal set default auth-algorithms=sha1 enc-algorithms=3des pfs-group=modp1024
/ppp secret add name=Test password=password service=l2tp profile=ipsec_vpn remote-address=192.168.1.15
/ip firewall filter add chain=input action=accept protocol=udp port=500,1701,4500 comment="Allow L2TP VPN (500,4500,1701/udp)"
/ip firewall filter add chain=input action=accept protocol=ipsec-esp comment="Allow L2TP VPN (ipsec-esp)"
Attempt 3
/interface l2tp-server server set enabled=yes authentication=mschap1,mschap2,chap use-ipsec=required ipsec-secret=Test
/ip pool add name=vpn_pool ranges=192.168.1.10-192.168.1.15 comment="L2TP VPN IP Pool"
/ppp profile add name=ipsec_vpn local-address=192.168.1.1 remote-address=vpn_pool
/ppp secret add name=Test password=password service=l2tp profile=ipsec_vpn
/ip firewall filter add action=accept chain=input protocol=udp dst-port=500,1701,4500 comment="Allow L2TP VPN (500,4500,1701/udp)"
/ip firewall filter add action=accept chain=input protocol=ipsec-esp comment="Allow L2TP VPN (ipsec-esp)"
The results are the same with all three attempts
- Connection is establish, Router 1 shows that the connection is made. Remote PCs VPN NIC gets an IP within Router 1s LOCAL range (192.168.1.0/24)
- Both Client and Remotes firewalls are off for testing of connection (normal Windows Firewall is used)
- I cannot ping any Client behind Router 1 nor can I access any Shared resources from Remote side.
Any suggestion ?