mDNS repeater feature
Please bring mDNS repeater feature in Rosv7. It is a very important feature for home routers.
-

-
jvanhambelgium
Forum Guru

- Posts: 1086
- Joined:
- Location: Belgium
Re: mDNS repeater feature
This is only an issue if you start fiddling around with multiple LAN / VLAN'sPlease bring mDNS repeater feature in Rosv7. It is a very important feature for home routers.
Guess what, like 0.00001% or something of "home users" is actually toying around with that in their home setup.
Don't get your hopes up to see it integrated into RouterOS. I think similar requests are echoing through the dungeons of this forum for many years now...
-

-
memelchenkov
Member Candidate

- Posts: 204
- Joined:
- Contact:
Re: mDNS repeater feature
A pretty neat feature and often required here. It's usually good for sharing printers in work environment, rather than for home. However, for home could be useful too, people are just lazy now to make some complicated setups of their networks. But Mikrotik is a complicated device, it's strange they still ignore mDNS repeater. Who need "plug-and-play" device will not go Mikrotik way. Look at OpenWRT-enabled devices, there you could install any package you want. Or use your home NAS/RPi/etc. for this feature.
Re: mDNS repeater feature
OpenWrt has relayd and a dedicated interface type for this task. But relayd is limited to IPv4. I once had such a setup running.
Re: mDNS repeater feature
even the edgerouter has a mdns repeater..
Re: mDNS repeater feature
Ever home user needs mDNS. Don't know why mikrotik keeps ignoring this.even the edgerouter has a mdns repeater..
Re: mDNS repeater feature
I am a home user and do not need it.Ever home user needs mDNS.
Why is your assumption so absolute?
It is absolute-ly false.
My 4,000 contracts (home and business), corresponding to more than 16,000 people,
do not have it and no one has ever complained about it.
Please explain which critical part of the home network does not work without mDNS.
Thanks.
Re: mDNS repeater feature
I keep my IoT on a separate vlan, I have my smart tv and google home devices on the same IoT vlan. How do I connect the smart tv and google home from my Wifi that is on a separate vlan?I'm a home user, and I do not neet that.Ever home user needs mDNS.
Why you assumption is so absolute?
Is absolute false.
My 4000 contracts (home and business), corresponding to more than 16000 person do not have that, no one single complain about that.
Please explain what critical part of home network do not function without mDNS.
Thanks.
Re: mDNS repeater feature
(please do not quote on useless way, use "post reply" instead)
>>>I keep my IoT on a separate vlan = VLAN of IoT devices
>>>I have my smart tv and google home devices on the same IoT vlan = TV and Google Home on same VLAN of IoT devices
>>>How do I connect the smart tv and google home from my Wifi that is on a separate vlan?
But on previous description do not are already on same VLAN of IoT devices ???
The mDNS is not the tool for do that...
Solution is extremely simple:
Create one virual wlan for other IoT devices, TV and Google Home, than work on same VLAN of IoT devices...
Do not have any sense make separate VLAN of IoT devices and then set Google and Smart TV on "main" Wi-Fi
>>>I keep my IoT on a separate vlan = VLAN of IoT devices
>>>I have my smart tv and google home devices on the same IoT vlan = TV and Google Home on same VLAN of IoT devices
>>>How do I connect the smart tv and google home from my Wifi that is on a separate vlan?
But on previous description do not are already on same VLAN of IoT devices ???
The mDNS is not the tool for do that...
Solution is extremely simple:
Create one virual wlan for other IoT devices, TV and Google Home, than work on same VLAN of IoT devices...
Do not have any sense make separate VLAN of IoT devices and then set Google and Smart TV on "main" Wi-Fi
Last edited by rextended on Wed Jul 07, 2021 6:08 pm, edited 1 time in total.
Re: mDNS repeater feature
Hege muchechilen sokale? na orom bhabhei chole esheychen dalali korte?
Re: mDNS repeater feature
traduction:
You touch the wrong cable...
You touch the wrong cable...
Re: mDNS repeater feature
you may want to put your TV or your dishwasher on an IOT VLAN so it can access to internet but not other vlans, and still want make it discoverable for the familly vlan so they can start the dishwasher or lookt at the TV from their devices?(please do not quote on useless way, use "post reply" instead)
>>>I keep my IoT on a separate vlan = VLAN of IoT devices
>>>I have my smart tv and google home devices on the same IoT vlan = TV and Google Home on same VLAN of IoT devices
>>>How do I connect the smart tv and google home from my Wifi that is on a separate vlan?
But on previous description do not are already on same VLAN of IoT devices ???
The mDNS is not the tool for do that...
Solution is extremely simple:
Create one virual wlan for other IoT devices, TV and Google Home, than work on same VLAN of IoT devices...
Do not have any sense make separate VLAN of IoT devices and then set Google and Smart TV on "main" Wi-Fi
Another example is to put your printer on a vlan for the same reason, you want it upgradable/maintainable remotely . But you want also to make it discoverable easily.
Re: mDNS repeater feature
@benoitc why you write that quoting my post?
Re: mDNS repeater feature
to reply to your "Do not have any sense make separate VLAN of IoT devices and then set Google and Smart TV on "main" Wi-Fi" . I may have misunderstood. But as I understand the principle, devices were on IOT vlan but accessed from others. And then you need an MDNS repeater@benoitc why you write that quoting my post?
Re: mDNS repeater feature
To those people asking for mDNS, can you give examples where it will be useful?
Rextended provided solutions for the given examples. Maybe there are more examples?
Rextended provided solutions for the given examples. Maybe there are more examples?
-

-
memelchenkov
Member Candidate

- Posts: 204
- Joined:
- Contact:
Re: mDNS repeater feature
I.e. network printers in wired network shared with VLAN of wireless clients. Connections to printers are allowed by firewall, but mDNS are not routed so users must enter IP addresses rather than use auto-discovery feature.To those people asking for mDNS, can you give examples where it will be useful?
Re: mDNS repeater feature
Hello,
it would be useful because of apple.
One of our customers had the problem, that some of his hotspot users log in and close the status site.
After some time, they want to log out and they find it to complicated to use a url with an IP in it,
so I set up a static dns entry like 'router.customer.local' and it worked for all PCs and Laptops, but the iPhone couldn't resolve it.
After some sniffing I found only mDNS requests. Google found me an article that says, that Apple devices uses mDNS by local domains.
So mDNS would be helpful in his setting.
it would be useful because of apple.
One of our customers had the problem, that some of his hotspot users log in and close the status site.
After some time, they want to log out and they find it to complicated to use a url with an IP in it,
so I set up a static dns entry like 'router.customer.local' and it worked for all PCs and Laptops, but the iPhone couldn't resolve it.
After some sniffing I found only mDNS requests. Google found me an article that says, that Apple devices uses mDNS by local domains.
So mDNS would be helpful in his setting.
Re: mDNS repeater feature
Hello normis,To those people asking for mDNS, can you give examples where it will be useful?
Rextended provided solutions for the given examples. Maybe there are more examples?
Actually, he did not provide any solution.
mDNS repeater is needed in the case that you have an IoT vlan and you need to interact to those devices from your main vlan.
For e.g. A phone connected to the main vlan needs to "cast" content to a smart tv on the restricted IoT vlan. and just to avoid any "why you connect your phone to the IoT vlan?" because it is not the solution.
in 2021 mDNS Repeater is a must.
Re: mDNS repeater feature
You do not catch the point, (ignore mDNS) why make separate IoT VLAN if than must be continuosly on contact with "MAIN" VLAN?
True nonsense!!!
True nonsense!!!
Last edited by rextended on Thu Jul 08, 2021 2:26 pm, edited 2 times in total.
Re: mDNS repeater feature
Yes, the question is, why separate the IoT, if you don't really need to separate ?
Re: mDNS repeater feature
mDNS is not a NAT or Routing, it simply supplies an addressmDNS repeater is needed in the case that you have an IoT vlan and you need to interact to those devices from your main vlan.
for work already the two VLAN must communicate to eachother and...
why formerly separated VLAN, but effectively not?
The device also MUST be compatible whit mDNS
mDNS devices do not need any mDNS "proxy" if already are on same broadcast domain
All these devices are studied to be all on same wired/wireless network, not to different VLAN....A phone connected to the main vlan needs to "cast" content to a smart tv on the restricted IoT vlan....
Just some users on this forum or very advanced users use VLAN in house,
99,9% do not matter if are VLAN or not, 99,8% also do not know what ia a VLAN.
Re: mDNS repeater feature
It's not entire nonsense, sometimes it's not possible to do it differently.
Here's example: you have an IoT gadget. It might not need internet, so you want to block internet access for it. Fine, you can use IP firewall filter if you know gadget's IP address. The later part can be tricky with IPv6 and dynamic addresses (constructed with aide of SLAAC), but you can still filter that according to gadget's MAC address. But even that is not fail safe, Apple in particular (and others as well) started to "anonymize" MAC address ... good luck catching that.
But even if you successfully block access to internet: user might want to restrict access of device to LAN services. And that's not easy to do if all devices belong to same L2 network.
Having separate L2 network for IoT devices solves all above mentioned problems without too much fuss. But then there comes auto-discovery where many (probably most) vendors simply expect that everything attaches to same L2 network (hence need for mDNS proxying) unless gadget registers directly to some cloud. Which is probably how network looks like for 99% of home users, but those mostly are not interested in running Mikrotik gear.
Personally I couldn't care less about mDNS and all that automagical stuff. But I still find problematic attitude of Mikrotik about not implementing service, which is enforced by major players and used by home users more and more. If MT wants to stay alive in SOHO segment, then they'll have to implement those features whether they like them or not.
Here's example: you have an IoT gadget. It might not need internet, so you want to block internet access for it. Fine, you can use IP firewall filter if you know gadget's IP address. The later part can be tricky with IPv6 and dynamic addresses (constructed with aide of SLAAC), but you can still filter that according to gadget's MAC address. But even that is not fail safe, Apple in particular (and others as well) started to "anonymize" MAC address ... good luck catching that.
But even if you successfully block access to internet: user might want to restrict access of device to LAN services. And that's not easy to do if all devices belong to same L2 network.
Having separate L2 network for IoT devices solves all above mentioned problems without too much fuss. But then there comes auto-discovery where many (probably most) vendors simply expect that everything attaches to same L2 network (hence need for mDNS proxying) unless gadget registers directly to some cloud. Which is probably how network looks like for 99% of home users, but those mostly are not interested in running Mikrotik gear.
Personally I couldn't care less about mDNS and all that automagical stuff. But I still find problematic attitude of Mikrotik about not implementing service, which is enforced by major players and used by home users more and more. If MT wants to stay alive in SOHO segment, then they'll have to implement those features whether they like them or not.
Re: mDNS repeater feature
>>>you have an IoT gadget It might not need internet so you want to block internet access for it
Simply do not provide a gateway and DNS on lease
>>>you can use IP firewall filter if you know gadget's IP address
...no...
>>>The later part can be tricky with IPv6 and dynamic addresses...
...no... go out only know/allowed devices, if anonymize MAC, never go out
>>>but you can still filter that according to gadget's MAC address
...ok....
>>>But even that is not fail safe, Apple in particular (and others as well) started to "anonymize" MAC address...
do not buy Apple devices... or filter device with "2nd lower bit set" (000000!0) .. I do not know if is legal to change randomly the MAC (how much random?)
>>> good luck catching that.
...but on this way you still have MAC allowed to out, not a list of blocked MAC....
>>>user might want to restrict access of device to LAN services
why? what can do a device without internet to a light bulb, to a PC? etc.?.
>>>And that's not easy to do if all devices belong to same L2 network.
...really... is easy....
>>>Having separate L2 network for IoT devices solves all above mentioned problems
...yes but... still no see any problem with IoT devices on same L2 network of my PC...
Simply do not provide a gateway and DNS on lease
>>>you can use IP firewall filter if you know gadget's IP address
...no...
>>>The later part can be tricky with IPv6 and dynamic addresses...
...no... go out only know/allowed devices, if anonymize MAC, never go out
>>>but you can still filter that according to gadget's MAC address
...ok....
>>>But even that is not fail safe, Apple in particular (and others as well) started to "anonymize" MAC address...
do not buy Apple devices... or filter device with "2nd lower bit set" (000000!0) .. I do not know if is legal to change randomly the MAC (how much random?)
>>> good luck catching that.
...but on this way you still have MAC allowed to out, not a list of blocked MAC....
>>>user might want to restrict access of device to LAN services
why? what can do a device without internet to a light bulb, to a PC? etc.?.
>>>And that's not easy to do if all devices belong to same L2 network.
...really... is easy....
>>>Having separate L2 network for IoT devices solves all above mentioned problems
...yes but... still no see any problem with IoT devices on same L2 network of my PC...
Re: mDNS repeater feature
Why a separate IoT vlan? because I want it, and why have a Mikrotik router at home and use it as a stupid ISP HG(aka router)?
I want to have control of devices that I don't fully trust, those "black boxes", and having a vlan for it, I isolate it from the L2 domain.
The main reason that I have a Mikrotik at home is to do things that I cannot do using the ISP's Home Gateway, like having a separate, untrusted IoT vlan and a guest vlan.
mDNS Repeater is needed to make some services work across vlans, like printing, casting and etc.
I want to have control of devices that I don't fully trust, those "black boxes", and having a vlan for it, I isolate it from the L2 domain.
The main reason that I have a Mikrotik at home is to do things that I cannot do using the ISP's Home Gateway, like having a separate, untrusted IoT vlan and a guest vlan.
mDNS Repeater is needed to make some services work across vlans, like printing, casting and etc.
Re: mDNS repeater feature
In a business environment, wired printers can often be on their own VLAN, or one separate from Wireless devices. Without mDNS between the networks, the built in discovery tools for printing in a lot of mobile and wireless devices does not work. It prevents printing from some mobile devices to another network. Manual setup of DNS for this is long-winded and does not always work correctly (possibly wide-area bonjour).To those people asking for mDNS, can you give examples where it will be useful?
Rextended provided solutions for the given examples. Maybe there are more examples?
There is also streaming to projectors and smart tvs/sticks that rely on the devices being on the same network for discovery, which is not always true in a business environment.
That is what I have seen in my experience.
Re: mDNS repeater feature
You understand than mDNS do not do NAT, routing, firewall, etc. but just resolve address?mDNS Repeater is needed to make some services work across vlans, like printing, casting and etc.
If you can comunicate between VLANs... the VLANs for this do not have any sense!
Understand?
Re: mDNS repeater feature
nonsense is your posts, if you don't see a reason to use it, does not mean that no one can have a reason to need it.You do not catch the point, (ignore mDNS) why make separate IoT VLAN if than must be continuosly on contact with "MAIN" VLAN?
True nonsense!!!
Want a example? I want to all devices not be able to access/scan devices on my main "trusted" vlan, but still my devices on the trusted vlan be able to talk with those IoT, not backwards. Any connection started on trusted side is permitted, not the ones started on the untrusted that are not to the internet.
Ps. if you dont have a reason to post something useful, don't post, people here is just making a reasonable request for a thing that is used by all big players.
Re: mDNS repeater feature
>removed, useless, see post #41<
Last edited by rextended on Thu Jul 08, 2021 6:55 pm, edited 3 times in total.
Re: mDNS repeater feature
of course, I know that. I've FW rules to allow the connections in the way that I do.You understand than mDNS do not do NAT, routing, firewall, etc. but just resolve address?mDNS Repeater is needed to make some services work across vlans, like printing, casting and etc.
If you can comunicate between VLANs... the VLANs for this do not have any sense!
Understand?
Re: mDNS repeater feature
Ooooh, you understand now!
Re: mDNS repeater feature
@normis, basically some users, like me, want to isolate IoT devices by the L2 domain. but still allowing some connections to start from the trusted side.Yes, the question is, why separate the IoT, if you don't really need to separate ?
some times all this Ch***** crap you will never know...
Re: mDNS repeater feature
Ok, you deserve one solution until mDNS is officially supported?
Re: mDNS repeater feature
>removed, useless, see post #41<
Last edited by rextended on Thu Jul 08, 2021 6:47 pm, edited 3 times in total.
Re: mDNS repeater feature
Perfectly valid point.@normis, basically some users, like me, want to isolate IoT devices by the L2 domain. but still allowing some connections to start from the trusted side.
some times all this Ch***** crap you will never know...
Re: mDNS repeater feature
>removed, useless, see post #41<
Last edited by rextended on Thu Jul 08, 2021 6:48 pm, edited 1 time in total.
Re: mDNS repeater feature
not in the case of using a Routerboard without a switch chip or with a limited one (like RB4011).With that settings I give some clue & hint for someone...
Simply "copy" broadcasted mDNS/SSDP between VLANs.
No something named "mDNS proxy" required...
Re: mDNS repeater feature
I do not have one 4011 to do some test, sorry :(
Re: mDNS repeater feature
I think the real problem is Wireless: be always on another switch, not on RTL8367
Last edited by rextended on Thu Jul 08, 2021 6:47 pm, edited 1 time in total.
Re: mDNS repeater feature
I don't have the wireless version. the problem is the RTL8367, it does not support anything besides the same as a $10 switch. anyway, I don't use it, just the SFP+ port.
Re: mDNS repeater feature
Ok, "solved"
Install multicast separate package and configure PIM:
https://wiki.mikrotik.com/wiki/Manual:R ... _.28PIM.29
The Protocol independent multicast (PIM) can receive cast from one vlan and re-cast to another,
this forward mDNS (Apple) / SSDP (all the Others) multicast packet between VLANs and you do not need other things,
except for next step on firewall rules between VLANs connections.
mDNS: UDP packet with source as device IP, standard random port for source, destination multicast 224.0.0.251 port 5353
mDNS Query: UDP packet with source as device IP, port 10101, destination multicast 239.255.255.251 port 10101
SSDP / UPnP: UDP packet with source as device IP, standard random port for source, destination multicast 239.255.255.250 port 1900
WS-Discovery: UDP packet with source as device IP, standard random port for source, destination multicast 239.255.255.250 port 3702
All this do not change my disbelief on need separation from IoT and home private network.
(On home point of view, business/work is another thing...)
Install multicast separate package and configure PIM:
https://wiki.mikrotik.com/wiki/Manual:R ... _.28PIM.29
The Protocol independent multicast (PIM) can receive cast from one vlan and re-cast to another,
this forward mDNS (Apple) / SSDP (all the Others) multicast packet between VLANs and you do not need other things,
except for next step on firewall rules between VLANs connections.
mDNS: UDP packet with source as device IP, standard random port for source, destination multicast 224.0.0.251 port 5353
mDNS Query: UDP packet with source as device IP, port 10101, destination multicast 239.255.255.251 port 10101
SSDP / UPnP: UDP packet with source as device IP, standard random port for source, destination multicast 239.255.255.250 port 1900
WS-Discovery: UDP packet with source as device IP, standard random port for source, destination multicast 239.255.255.250 port 3702
All this do not change my disbelief on need separation from IoT and home private network.
(On home point of view, business/work is another thing...)
Re: mDNS repeater feature
I'm also in the same boat, having to get mDNS accross different interfaces (not just VLANs!).
In my use case I'm running Apple Airport as audio streaming receiver at a dance studio.
Audio needs to be sent from the wired devices that are inside the office VLAN (they need to be to get access to the internal systems) and also from the teacher devices that are joined into the network via wireless. At the moment both are in the same network, but I would prefer to move the teachers that are partly contractors into an isolated network where they can get internet and do streaming but cannot connect to the other internal systems.
As a bonus it would be great to be able to use AirPrint (mDNS) enabled Printers via the VPN connection from the home office site from the iPhone / iPad of the owner.
At the moment there is a linux VM connected to multiple VLANs and bridged to the remote site via EOIP running mDNS Repeater to get this functionality. Would be great if it could just be enabled on the MT Routers.
It's by no means a must feature, but as more and more devices are switched to mobile and automagical configuration it could keep some admins sane trying not to just put everything into one big network and hope for the best....
Also about PIM:
I tried setting it up, but mDNS requests are marked as not routable, so PIM simply ignores them....
If there is a simple workaround I would like to hear it, would save me a ton of work.
In my use case I'm running Apple Airport as audio streaming receiver at a dance studio.
Audio needs to be sent from the wired devices that are inside the office VLAN (they need to be to get access to the internal systems) and also from the teacher devices that are joined into the network via wireless. At the moment both are in the same network, but I would prefer to move the teachers that are partly contractors into an isolated network where they can get internet and do streaming but cannot connect to the other internal systems.
As a bonus it would be great to be able to use AirPrint (mDNS) enabled Printers via the VPN connection from the home office site from the iPhone / iPad of the owner.
At the moment there is a linux VM connected to multiple VLANs and bridged to the remote site via EOIP running mDNS Repeater to get this functionality. Would be great if it could just be enabled on the MT Routers.
It's by no means a must feature, but as more and more devices are switched to mobile and automagical configuration it could keep some admins sane trying not to just put everything into one big network and hope for the best....
Also about PIM:
I tried setting it up, but mDNS requests are marked as not routable, so PIM simply ignores them....
If there is a simple workaround I would like to hear it, would save me a ton of work.
Re: mDNS repeater feature
By the looks of it, L2 segregation for the mentioned above cases is an illusion of safety.
I understand the reason why you would want to put IoT devices under a separate VLAN. For instance, you bought a no-name smart light bulb on eBay and you don't want it to access your NAS and upload its content to the internet. But you want to be able to turn on/off the bulb from your PC/smartphone. Then why not put your PC/smartphone under both IoT and NAS VLANs? Then PC will be able to access both IoT and NAS devices, but IoT cannot access NAS.
What you are trying to do, is to segregate the network on L2 (via VLAN), but then combine it together on L3 (via inter-VLAN routing). Without a firewall, there is no safety here, only an illusion of it. Yes, IoT devices on one VLAN cannot do neighbor discovery, but with inter-VLAN routing, nobody prevents them to scan the routed network (unless a properly configured firewall). For example, your PC VLAN 10 IP 192.168.10.1/24 accesses a spyware light bulb on VLAN 20 IP 192.168.20.31/24, then the bulb scans the source network (e.g.), finds a NAS at 192.168.10.75 and does nasty things with that.
Of course, you can configure the firewall to allow traffic only from VLAN ID 10 to 20, but backward - only within the established connections (btw, it won't work in case of mDNS due to multicast), but IMHO that's overcomplicated.
It is much easier to assign PC to both VLANs with IP 192.168.10.1/24 and 192.168.20.1/24 for VLAN 10 and 20 respectively and to prevent (by simply not creating) routing between 192.168.10.0/24 and 192.168.20.0/24 networks.
I understand the reason why you would want to put IoT devices under a separate VLAN. For instance, you bought a no-name smart light bulb on eBay and you don't want it to access your NAS and upload its content to the internet. But you want to be able to turn on/off the bulb from your PC/smartphone. Then why not put your PC/smartphone under both IoT and NAS VLANs? Then PC will be able to access both IoT and NAS devices, but IoT cannot access NAS.
What you are trying to do, is to segregate the network on L2 (via VLAN), but then combine it together on L3 (via inter-VLAN routing). Without a firewall, there is no safety here, only an illusion of it. Yes, IoT devices on one VLAN cannot do neighbor discovery, but with inter-VLAN routing, nobody prevents them to scan the routed network (unless a properly configured firewall). For example, your PC VLAN 10 IP 192.168.10.1/24 accesses a spyware light bulb on VLAN 20 IP 192.168.20.31/24, then the bulb scans the source network (e.g.
Code: Select all
nmap -sn 192.168.10.0/24Of course, you can configure the firewall to allow traffic only from VLAN ID 10 to 20, but backward - only within the established connections (btw, it won't work in case of mDNS due to multicast), but IMHO that's overcomplicated.
It is much easier to assign PC to both VLANs with IP 192.168.10.1/24 and 192.168.20.1/24 for VLAN 10 and 20 respectively and to prevent (by simply not creating) routing between 192.168.10.0/24 and 192.168.20.0/24 networks.
Re: mDNS repeater feature
Surely that is one of the necessary precautions.Of course, you can configure the firewall to allow traffic only from VLAN ID 10 to 20, but backward - only within the established connections (btw, it won't work in case of mDNS due to multicast), but IMHO that's overcomplicated.
And that's where mDNS repeater would come in handy - so you can easily make the router transparent for mDNS, leaving router's firewall to work the usual way - allowing new connections only from trusted networks to untrusted, but not vice versa.
But now I wonder if the approach with PIM that @rextended suggested will do the trick...
Re: mDNS repeater feature
I have two VLANs one for LAN and one for WLAN. I want to cast my screen from the desktop in the LAN to my smart tv in WLAN. I use mikrotik because I need vlan segregation. Else would have gone with any other ASUS AC/AX router. Thats why I need MDNS.To those people asking for mDNS, can you give examples where it will be useful?
Rextended provided solutions for the given examples. Maybe there are more examples?
Re: mDNS repeater feature
@rextended Thanks for the workaround idea, but, for now, there is no multicast package for the ROS 7.x.
@raimondsp I don't understand the resistance against mDNS repeater, yes could be complicated to have all of them correctly configured, but still, I don't get it. Also, putting the phone in the untrusted vlan is not an option, as, in my case, I need to use some services on it. Also, it is not only phones using mDNS, laptops too.
@raimondsp I don't understand the resistance against mDNS repeater, yes could be complicated to have all of them correctly configured, but still, I don't get it. Also, putting the phone in the untrusted vlan is not an option, as, in my case, I need to use some services on it. Also, it is not only phones using mDNS, laptops too.
Re: mDNS repeater feature
I do not consider RouterOS 7 until at least first stable version coming out (except 7.0.3 for Chateau LTE12 than I do not have)
Re: mDNS repeater feature
You answer is a nonnse se as well. VLAN N allows different connections profile. Eg. You may not want to have IPV6 RA on a VLAN or use a different addressing for IOTs. You may want to only let 20Mbps throughtput to TVs. You also want IOT devices connected to the net but not allow them to discover other devices in the house. You may also want to only allows 2 VLAN to access to the same devices but let others vlans out.>>>you have an IoT gadget It might not need internet so you want to block internet access for it
Simply do not provide a gateway and DNS on lease
>>>you can use IP firewall filter if you know gadget's IP address
...no...
>>>The later part can be tricky with IPv6 and dynamic addresses...
...no... go out only know/allowed devices, if anonymize MAC, never go out
>>>but you can still filter that according to gadget's MAC address
...ok....
>>>But even that is not fail safe, Apple in particular (and others as well) started to "anonymize" MAC address...
do not buy Apple devices... or filter device with "2nd lower bit set" (000000!0) .. I do not know if is legal to change randomly the MAC (how much random?)
>>> good luck catching that.
...but on this way you still have MAC allowed to out, not a list of blocked MAC....
>>>user might want to restrict access of device to LAN services
why? what can do a device without internet to a light bulb, to a PC? etc.?.
>>>And that's not easy to do if all devices belong to same L2 network.
...really... is easy....
>>>Having separate L2 network for IoT devices solves all above mentioned problems
...yes but... still no see any problem with IoT devices on same L2 network of my PC...
There are plenty of uses cases afaik. You can't rely on mac addressing or even ips to make proper tules. In large networks this is near impossible.
As I understand you don't see any interrest to it and it may be useful you provide your own solutions to manages printers, some iot devices (like chromecast, apple tvs, ...) which can be useful for some. But afaik mDNS has some uses cases. A,nd it would be useful to have a package for it.
Re: mDNS repeater feature
I had to look, but this is apparently not something possible on an iPhone or an iPad :/
It is much easier to assign PC to both VLANs with IP 192.168.10.1/24 and 192.168.20.1/24 for VLAN 10 and 20 respectively and to prevent (by simply not creating) routing between 192.168.10.0/24 and 192.168.20.0/24 networks.
Re: mDNS repeater feature
@benoitc I think you misunderstood again.
That post is not addressed to you.
I don't want discuss about that.
I just try to help to find one alternative solution UNTIL mDNS is available.
That post is not addressed to you.
I don't want discuss about that.
I just try to help to find one alternative solution UNTIL mDNS is available.
Re: mDNS repeater feature
I was just describing the utility of segregating devices none vlan while wanting to access to them from others. (eg. controlling throughput or controlling who is there before anything).@benoitc I think you misunderstood again.
That post is not addressed to you.
I don't want discuss about that.
I just try to help to find one alternative solution UNTIL mDNS is available.
I will try your solution with PIM. The thing is that normally mDNS multicast is scoped to its subnet. so unsure how it will work when the ip is announced to the other subnet. mdns repeater are acting as proxy or such thing.
Re: mDNS repeater feature
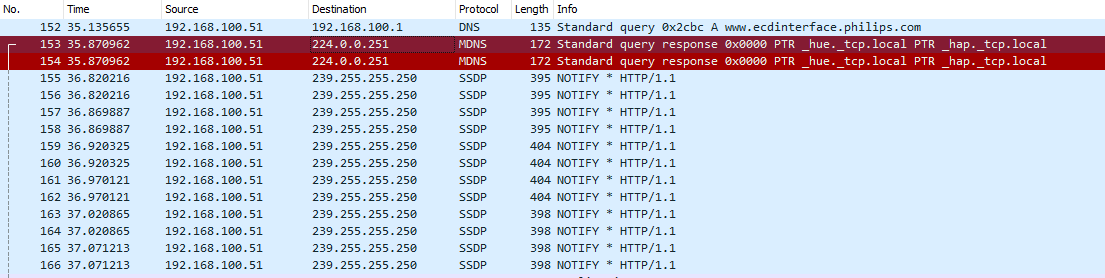
Hi Thanks for asking examples , I bought the MikroTik as extra router behind the router of my provider and defined 2 subnets on it. One for IOT and one for my Home PC's. I moved the IOT devices to the IOT subnet including the Philips HUE. This is not working anymore behind the MikroTIk router. I spend ours googling and wondering why it's traffic was not routed upstreams. Then I found HUE is generating MDNS traffic, I captured some of these packets. I tried to install the igmp-proxy package and see if that would help but no success. Hopfully there can be a solution for this.To those people asking for mDNS, can you give examples where it will be useful?
Rextended provided solutions for the given examples. Maybe there are more examples?
192.168.100.51 is the Hue, connected to Ether2 , Ether1 sits on the upstream router network 192.168.2.X, the upstream router 192.168.2.254 seems not to get the MDNS and Multicast packets so it cant futher route them to the internet.
(screenshot link will stop working after 14 days no view)
Re: mDNS repeater feature
On a hotspot network with 100 to 1000 or more devices on a network, one usually blocks multicast traffic, and adds client isolation. It would be handy to be able to reach AppleTV's or Chromecasts on a different VLAN, MDNS would be useful for this. This way we can still ensure proper efficiency and security on the main hotspot user VLAN, as well as give them access to the needed media services, without hotspot users being able to access each other.To those people asking for mDNS, can you give examples where it will be useful?
Rextended provided solutions for the given examples. Maybe there are more examples?
Re: mDNS repeater feature
Yes, mDNS is really a needed feature. Also, it's a VERY small and lightweight userland daemon. I run a VM with avahi and it doesn't really use any CPU while sitting in low single digits for memory usage. Additionally, it will literally need interfaces assignment and no other complex configuration.
Re: mDNS repeater feature
Allow inter-VLAN routing, allow multi-cast routing on LAN, don't block Multicast subnets. Problem solved.
https://en.wikipedia.org/wiki/Multicast_address
https://en.wikipedia.org/wiki/Multicast_address
Re: mDNS repeater feature
@DarkNate, if for some reason you read my posts, you can notice I never suggest to use "drop bogon", except for prevent IP spoofing on WAN,
but this forum, the web, and also some mikrotik guide put 224.0.0.0/4 as bad_ipv4, like must be dropped, IGNORING THE SOURCE, or someone dies...
https://help.mikrotik.com/docs/display/ ... d+Firewall
Toom much copy&paste without know what is doing
from ros guide:
But on page, you also linked:
224.0.0.251 Multicast DNS (mDNS) address, Routers must not forward these messages outside the subnet from which they originate
but this forum, the web, and also some mikrotik guide put 224.0.0.0/4 as bad_ipv4, like must be dropped, IGNORING THE SOURCE, or someone dies...
https://help.mikrotik.com/docs/display/ ... d+Firewall
Toom much copy&paste without know what is doing
from ros guide:
ROS HELP code
/ip firewall address-list [...] add address=224.0.0.0/4 comment="defconf: multicast" list=no_forward_ipv4 [...] /ip firewall filter [...] add action=drop chain=forward src-address-list=no_forward_ipv4 comment="defconf: drop bad forward IPs" add action=drop chain=forward dst-address-list=no_forward_ipv4 comment="defconf: drop bad forward IPs" [...]
But on page, you also linked:
224.0.0.251 Multicast DNS (mDNS) address, Routers must not forward these messages outside the subnet from which they originate
The IANA has reserved the range 224.0.0.0 to 224.0.0.255 for use by network protocols on a local network segment.
Packets with an address in this range are local in scope and are not forwarded by IP routers.
Packets with link local destination addresses are typically sent with a time-to-live (TTL) value of 1 and are not forwarded by a router.
Within this range, reserved link-local addresses provide network protocol functions for which they are reserved.
Network protocols use these addresses for automatic router discovery and to communicate important routing information.
For example, Open Shortest Path First (OSPF) uses the IP addresses 224.0.0.5 and 224.0.0.6 to exchange link-state information.
IANA assigns single multicast address requests for network protocols or network applications out of the 224.0.1.xxx address range.
Multicast routers forward these multicast addresses.
Re: mDNS repeater feature
224.0.0.0/4 should be dropped from WAN not LAN@DarkNate, if for some reason you read my posts, you can notice I never suggest to use "drop bogon", except for prevent IP spoofing on WAN,
but this forum, the web, and also some mikrotik guide put 224.0.0.0/4 as bad_ipv4, like must be dropped, IGNORING THE SOURCE, or someone dies...
https://help.mikrotik.com/docs/display/ ... d+Firewall
Toom much copy&paste without know what is doing
from ros guide:ROS HELP code
/ip firewall address-list [...] add address=224.0.0.0/4 comment="defconf: multicast" list=no_forward_ipv4 [...] /ip firewall filter [...] add action=drop chain=forward src-address-list=no_forward_ipv4 comment="defconf: drop bad forward IPs" add action=drop chain=forward dst-address-list=no_forward_ipv4 comment="defconf: drop bad forward IPs" [...]
But on page, you also linked:
224.0.0.251 Multicast DNS (mDNS) address, Routers must not forward these messages outside the subnet from which they originate
The IANA has reserved the range 224.0.0.0 to 224.0.0.255 for use by network protocols on a local network segment.
Packets with an address in this range are local in scope and are not forwarded by IP routers.
Packets with link local destination addresses are typically sent with a time-to-live (TTL) value of 1 and are not forwarded by a router.
Within this range, reserved link-local addresses provide network protocol functions for which they are reserved.
Network protocols use these addresses for automatic router discovery and to communicate important routing information.
For example, Open Shortest Path First (OSPF) uses the IP addresses 224.0.0.5 and 224.0.0.6 to exchange link-state information.
IANA assigns single multicast address requests for network protocols or network applications out of the 224.0.1.xxx address range.
Multicast routers forward these multicast addresses.
Re: mDNS repeater feature
That's the point: the MikroTik help and other "guides" incorrectly drop all regardless if are needed on LANs...
Re: mDNS repeater feature
Don't know, I review every rule/config line by line from guides, no blind copy/paste, so never had broken problems before.That's the point: the MikroTik help and other "guides" incorrectly drop all regardless if are needed on LANs...
Re: mDNS repeater feature
Have you actually tested it or just blindly linked the wikipedia page? mDNS traffic is marked to never cross the subnet and so that even if you forcefully forward it devices which support the protocol properly will simply ignore it. You need an mDNS proxy/router which is responsible for handling mDNS announcements between subnets.Allow inter-VLAN routing, allow multi-cast routing on LAN, don't block Multicast subnets. Problem solved.
https://en.wikipedia.org/wiki/Multicast_address
https://networkengineering.stackexchange.com/a/72933 see that for good summary
Even IETF had a document about the issue: https://tools.ietf.org/id/draft-bhandar ... ay-00.html
Re: mDNS repeater feature
Lets just remember that there is a open source implementation of it called avahi (that is actually what runs under the hood on EdgeMax routers for mDNS).
Most people here against, never used mDNS, so they didn't test it. also, there is no multicast package on 7.1 yet.
most people here for it, have used before and can't believe that this is not present on RouterOS.
Most people here against, never used mDNS, so they didn't test it. also, there is no multicast package on 7.1 yet.
most people here for it, have used before and can't believe that this is not present on RouterOS.
Re: mDNS repeater feature
I just wanted my guest network to be able to connect to the chromecast on the main network while being able to rate limit the whole guest network by simple queues, this might not be the right way but it was the easiest way for me to do it, I also wanted to setup a network only for IoT devices with no internet access, but further diving into this has only brought me across jank solutions.Yes, the question is, why separate the IoT, if you don't really need to separate ?
I am perplexed by the hesitation to have mDNS by mikrotik (just looking on the forums there are multiple threads of such discussions)
Frankly I can't comprehend the replies by the staff on this thread, and some of the replies are just fear-based rather than factual, and no examples given based on real-world scenarios.
FE;
How will having an mDNS server make these devices be able to access the internet? Unless your devices have already been compromised that doesn't sound right! Actually it sounds very paranoid, being scared of something on the small chance that it might happen? Then why connect to the internet at all?
And let's say even if the IoT devices were able to query local devices through mDNS how will they get internet access if the network they're on is unable to?
So far the only solution I could find was having to buy a pi just to be able to run an mDNS server, as chronicled here,
viewtopic.php?t=160966
This actually hurt reading, the poor guy spending months on what should be plug and play tbh.
Anyway, it has been a tiring day and I'm just more frustrated that the solution to such a simple problem has not been implemented despite so many threads on the forum about this very issue
Re: mDNS repeater feature
Yes, the question is, why separate the IoT, if you don't really need to separate ?
Because the IOT device might have more than one service that its broadcasting. And with a mDNS repeater function, you could chose which services to rebroadcast on another network. And then firewall to only allow the specific features you want. My device broadcasts file server, ssh server, vnc server functionality. It would be great to filter those.
I use mDNS repeaters a lot, for instance for guest access to internal apple-tv airmirror, for printer functions etc...
It is easier to separate the network functions IOT/printer/client/server etc. It is cleaner. It is easier creating firewall rules.
Also, you might want to deny internet access from the IOT LAN.
IOT might have different security policies compared to enterprise LAN...
Do I need to go on?
I dont understand why this needs to be "explained" to mikrotik staff... lol
Right now I do this in my Aerohive AP's instead.
-

-
archerious
Member Candidate

- Posts: 155
- Joined:
- Location: USA
- Contact:
Re: mDNS repeater feature
Couldn't agree more, the fact that Ubiquiti has had this feature for years is embarrassing. MikroTik is superior in routing, software,e and hardware, so I don't understand why they are allowing Ubiquiti to have an advantage over them. Mdns is extremely important for pro-sumers, the exact crowd that buys MikroTik for SOHO.Yes, the question is, why separate the IoT, if you don't really need to separate ?
Because the IOT device might have more than one service that its broadcasting. And with a mDNS repeater function, you could chose which services to rebroadcast on another network. And then firewall to only allow the specific features you want. My device broadcasts file server, ssh server, vnc server functionality. It would be great to filter those.
I use mDNS repeaters a lot, for instance for guest access to internal apple-tv airmirror, for printer functions etc...
It is easier to separate the network functions IOT/printer/client/server etc. It is cleaner. It is easier creating firewall rules.
Also, you might want to deny internet access from the IOT LAN.
IOT might have different security policies compared to enterprise LAN...
Do I need to go on?
I dont understand why this needs to be "explained" to mikrotik staff... lol
Right now I do this in my Aerohive AP's instead.
I've had several customers upset that their guest wifi cannot use airplay from the regular wifi, leading them to give their main wifi password to guests.....and regret it.
Stupid, stupid, stupid.
Just use Avahi or something else @MikroTik!
Re: mDNS repeater feature
But why do you not just put the printer to guest wifi instead? This is the recommended way to do it - according to discussion. No need to "hide" the printer in a "regular wifi". 
But just kidding. I do not get it either, why people argue so much against mdns repeater.
But just kidding. I do not get it either, why people argue so much against mdns repeater.
-

-
onnoossendrijver
Member

- Posts: 488
- Joined:
- Location: The Netherlands
Re: mDNS repeater feature
In a network where I need mDNS repeater I placed a small linux box running avahi (could be a Raspberry PI) with interfaces in both vlans.
This works really great.
Offcourse disable routing and/or configure the local firewall correctly...
This works really great.
Offcourse disable routing and/or configure the local firewall correctly...
Re: mDNS repeater feature
Another example is to put your printer on a vlan for the same reason, you want it upgradable/maintainable remotely . But you want also to make it discoverable easily.
Exactly my use case
Re: mDNS repeater feature
The biggest reason I can think of, is that you might have ethernet connected IoT devices in publicly accessible locations - you don't want your trusted network to be on the end of that cable. (CCTV is more likely than IoT, but the point is still the same)Yes, the question is, why separate the IoT, if you don't really need to separate ?
Re: mDNS repeater feature
A good practice for IOT on their own vlan is for limiting broadcasts.
You may want L3 connectivity to the devices but you may not like their "chatty" nature on L2.
With the rise of IOT devices it is easy to have 20+ devices on a network that broadcast constantly thus slowing down the network.
Gigabit ethernet and PCs will not feel this effect much but WiFi 5 and bellow or anything not as performant as a PC (ex TV, rpi) can exhibit slowdowns and strange behavior.
You may want L3 connectivity to the devices but you may not like their "chatty" nature on L2.
With the rise of IOT devices it is easy to have 20+ devices on a network that broadcast constantly thus slowing down the network.
Gigabit ethernet and PCs will not feel this effect much but WiFi 5 and bellow or anything not as performant as a PC (ex TV, rpi) can exhibit slowdowns and strange behavior.
Re: mDNS repeater feature
For the time being I will install avahi on a Raspberry Pi, however I would really like to have a mDNS proxy feature available in RouterOS. Some clients (seems like MacOS needs it for the scanner of my MFP) need mDNS in order function properly, so it's just nonsense to say that there is no use for it. And yes, I strongly disagree to say that we shouldn't put IoT devices in a separate VLAN: I want to control my network, i do not want those devices to control my network. Firewall rules for inter VLAN routing should of course be implemented.
Re: mDNS repeater feature
In v7.1 RC3 docker support is added so anyone who has/ will try implementing mDNS via container?
Re: mDNS repeater feature
Please keep all Container related questions and feedback to the specific topic: viewtopic.php?f=1&t=178342&p=878204
Re: mDNS repeater feature
It would need to be able to attach docker interfaces to each vlan on the existing bridge (as it needs to be on the same broadcast domain), if possible it could work, but, still not good as a native mDNS repeater / Avahi package for ROS.In v7.1 RC3 docker support is added so anyone who has/ will try implementing mDNS via container?
I don't think that docker / containers are the solution for the need discussed here.
Re: mDNS repeater feature
Glad to find this thread and I am having problems on this as well. Hope that there is a work around for being able to Airplay music to the different zones or even air print when we are on a different VLANs.
As more and more residentials and offices are getting more “Smarter” due to the huge increase of IoT products, it actually make sense to make sure they are on a different VLANs. Most Smart bulbs and other IoT devices are Wi-Fi based hence you do not want them to bog down that particular network when everything is on the same subnet.
In regards to multicast, I am still trying to figure out how to configure it correctly as I’ve a RB3011 with a UniFi 48 Pro POE switch and trying to configure to make sure the VLANs for Video Over IP works and properly configured but no luck.
As more and more residentials and offices are getting more “Smarter” due to the huge increase of IoT products, it actually make sense to make sure they are on a different VLANs. Most Smart bulbs and other IoT devices are Wi-Fi based hence you do not want them to bog down that particular network when everything is on the same subnet.
In regards to multicast, I am still trying to figure out how to configure it correctly as I’ve a RB3011 with a UniFi 48 Pro POE switch and trying to configure to make sure the VLANs for Video Over IP works and properly configured but no luck.
Re: mDNS repeater feature
For those who are interested, I have a simple mDNS reflector developed by myself and running in Docker. It is just hundreds lines of code in C, supporting both ipv4 and ipv6: https://github.com/vfreex/mdns-reflector
-

-
linedpaper
just joined
- Posts: 1
- Joined:
Re: mDNS repeater feature
Just got my first mikrotik and sad to see this is still not a feature. Second guessing my rb5009 purchase over the Ubiquiti option, hopefully it gets added soon.
Re: mDNS repeater feature
I haven't done any testing yet but this looks really useful. My workaround from this point has been a VLAN trunk to a raspberry pi with unnumbered interfaces running avahi in reflector mode. I'll report back after I've had a chance to dig into v7 and containers.For those who are interested, I have a simple mDNS reflector developed by myself and running in Docker. It is just hundreds lines of code in C, supporting both ipv4 and ipv6: https://github.com/vfreex/mdns-reflector
Regarding the need for mDNS reflectors, I figure I'll add my two cents in case staff makes another appearance on the thread. In theory, nobody should *need* an mDNS reflector. In fact, the aforementioned avahi didn't implement a reflector until later and you have to turn it on in the config. avahi's primary purpose was simply being an mDNS advertisement daemon for service discovery on Linux.
The previous posters talking about routable multicast have sort of the right idea. If you need link local multicast to leave the LAN, then maybe you shouldn't use link local multicast and instead a proper routable multicast group. Agreed! Unfortunately we all are stuck with the implementation decisions that Google (Chromecast/Home/etc), Apple (Airplay/Homekit/etc), and every other IoT vendor have made. They apparently cannot fathom why anyone would be using the devices on a network more complicated than a single Ethernet broadcast domain.
In a home environment, it's true that very few people actually need multiple VLANs and to put themselves in the situation where an mDNS reflector is required. However, a lot of these protocols are not limited to the home and there may be more business use cases than you think that could stand to benefit from this. In larger enterprise/campus networks, for example, it is often no longer acceptable to land wireless clients from controllerized wireless infrastructure directly onto the same LANs as the wall jacks. When there are BYOD users on wireless in a conference room that want to present to a wired AppleTV/Chromecast, you suddenly have a problem. This has been a problem in higher education for years and is becoming more and more common in any institutional environment that has conference rooms.
The solution to this is either proprietary full-stack replacements that speak Airplay/Chromecast and include their own mDNS replacement or for the networking vendors to support a native mDNS proxy. In the US, folks in higher ed have been grumpily lobbying Apple for almost a decade now [1] to just ditch the mechanism. Ultimately, vendors like Cisco saw the need and responded by implementing mDNS proxies in their wireless controllers [2]. Maybe Mikrotik can follow, too?
[1] https://www.cultofmac.com/182919/educat ... x-bonjour/
[2] https://www.cisco.com/c/en/us/td/docs/w ... ur-DG.html
Re: mDNS repeater feature
Cool, I installed this on a hap ac2, it seems to work ok, and appears to take up very little ram, and the executable is tiny.For those who are interested, I have a simple mDNS reflector developed by myself and running in Docker. It is just hundreds lines of code in C, supporting both ipv4 and ipv6: https://github.com/vfreex/mdns-reflector
Unfortunately, I needed to use a couple of VLans on the veth so need scripting to enable them first.
Ideally I would like no scripting, so could potentially remove all the other shell executables in the image.
Reducing likelihood of being owned (maybe).
Alternatively maybe Mikrotik could add this as a package...
Re: mDNS repeater feature
Can't PM you rplant. Mind explaining how you achieved this? Running openwrt / metarouter on 6.x?
Re: mDNS repeater feature
For those who are interested, I have a simple mDNS reflector developed by myself and running in Docker. It is just hundreds lines of code in C, supporting both ipv4 and ipv6: https://github.com/vfreex/mdns-reflector
which was forked into a docker (https://github.com/monstrenyatko/docker-mdns-repeater) container mentioned further down the same discussionFinally solved this!
So from Mikrotik perspective, everything was set up properly. You might need IGMP proxy for some devices, but no need for PIM (some suggested that IGMP is not enough, even though every guide says it uses IGMP), just a simple IGMP-Proxy setup will do.
I have switched from avahi to this mdns reflector:
https://github.com/kennylevinsen/mdns-repeater
With RouterOS 7.1rc3 .... would a docker image be usable?
https://github.com/monstrenyatko/docker-mdns-repeater
--------------
said in v7.1rc3 adds Docker (TM) compatible container supportWe will re-release container package soon. We wanted to improve security of the package, and make sure it does not have access to things it should not access. We will sandbox it more, re-evaluate all security aspects and will release it soon, when it is ready and completely secure.
Re: mDNS repeater feature
Ok, I read most of the topics above, even though I am still trying to make sense of everything has been written.
No networking expert here, and I even didn't know that such a mDNS was a thing until a couple of days ago, so please bear with me.
I have a Mikrotik hAP ac² at the top of my home LAN (in my room). I also have a Plex server installed on a little Windows notebook. There is also a not-VLAn capable switch/ap in my dining room for guest-wifi purpose. My smart tv with the Plex app is plugged to the switch as well. They are all on the same subnet now, and of course the Plex app can reach and read media contents on the Plex server.
I'm going to change a bit my private LAN in the next few days. Ubuntu server is going to be installed on the little notebook and a Plex server, as a docker container, will be installed on it.
I am going to separate an ethernet port ( the same ethernet port which the switch is plugged to) from my Mikrotik bridge and create a new subnet on it in order to set firewall rules to isolate the switch from my main LAN mostly because of the guest wifi running on it. However, I still want the Plex app on my TV to reach and read media contents of the plex server on my ubuntu server which will remain in my main LAN/subnet. Plex server is going to be the only service accessible from another subnet (by my smart TV). I know that the best solution would be that of setting up a vlan-capable switch and put the guest-wifi and my smart-tv on different VLANs in order to handle them with different firewall rules, but I'm not going to buy one..at the moment at least.
So, in your opinion, what would the best solution be in order to achieve my goal only with the devices I have at the moment? Thanks
No networking expert here, and I even didn't know that such a mDNS was a thing until a couple of days ago, so please bear with me.
I have a Mikrotik hAP ac² at the top of my home LAN (in my room). I also have a Plex server installed on a little Windows notebook. There is also a not-VLAn capable switch/ap in my dining room for guest-wifi purpose. My smart tv with the Plex app is plugged to the switch as well. They are all on the same subnet now, and of course the Plex app can reach and read media contents on the Plex server.
I'm going to change a bit my private LAN in the next few days. Ubuntu server is going to be installed on the little notebook and a Plex server, as a docker container, will be installed on it.
I am going to separate an ethernet port ( the same ethernet port which the switch is plugged to) from my Mikrotik bridge and create a new subnet on it in order to set firewall rules to isolate the switch from my main LAN mostly because of the guest wifi running on it. However, I still want the Plex app on my TV to reach and read media contents of the plex server on my ubuntu server which will remain in my main LAN/subnet. Plex server is going to be the only service accessible from another subnet (by my smart TV). I know that the best solution would be that of setting up a vlan-capable switch and put the guest-wifi and my smart-tv on different VLANs in order to handle them with different firewall rules, but I'm not going to buy one..at the moment at least.
So, in your opinion, what would the best solution be in order to achieve my goal only with the devices I have at the moment? Thanks
Last edited by broderick on Sun Jul 24, 2022 12:44 pm, edited 1 time in total.
-

-
brotherdust
Member Candidate

- Posts: 130
- Joined:
Re: mDNS repeater feature
Normis, as I'm sure you are aware, IOT devices have a notorious reputation for poor security practices. In order to limit the impact of these security problems, a conscientious network administrator will place these devices on separate VLAN. The VLAN provides an implicit context to apply additional security policies. The expectation that really _any_ IOT device is secure is foolish at best.Yes, the question is, why separate the IoT, if you don't really need to separate ?
Providing a native mDNS/SSDP repeater would allow administrators to follow the good practice of keeping these devices in a separate security context, whilst also making it possible for the more user-friendly functions to work across contexts.
Please consider adding this functionality to RouterOS 7. It is sorely needed and has been requested across the forum by your customers for years.
Thank you!
Edit:
If the answer is “no”: since RouterOS 7 lacks a PIM dense-mode implementation (for now), maybe the clever guys on your team could come up with a workaround using PIM-SM and post a working example config to the docs?
-

-
invader zog
Frequent Visitor

- Posts: 84
- Joined:
Re: mDNS repeater feature
I'd also like the feature.
All of my wireless, IOT, and entertainment devices are on one network (guest)
My servers and desktops are on another network (private)
I control and limit access from the guest to the private network
I'd like to be able to do a wireless sync of my iPhone from my desktop computer
If there are any suggestions/guides for how to accomplish this, I'd love to here. The only device I have that communicates on both networks is the MT, but I do have windows and linux servers running in my private network and could install a service there. I've been a MT user for decades now and am reasonably savvy with networking, but I don't know much about mDNS and forwarding broadcast traffic...
All of my wireless, IOT, and entertainment devices are on one network (guest)
My servers and desktops are on another network (private)
I control and limit access from the guest to the private network
I'd like to be able to do a wireless sync of my iPhone from my desktop computer
If there are any suggestions/guides for how to accomplish this, I'd love to here. The only device I have that communicates on both networks is the MT, but I do have windows and linux servers running in my private network and could install a service there. I've been a MT user for decades now and am reasonably savvy with networking, but I don't know much about mDNS and forwarding broadcast traffic...
Re: mDNS repeater feature
If this is implemented, some kind of way to filter which devices/services are repeated and to which interface would be handy. Sometimes you may not want everything advertised.
Re: mDNS repeater feature
I don't understand why RouterOS's PIM-SM was suggested in the thread: it requires devices to enter / leave multicast groups via IGMP.
mDNS (Apple Bonjour) does not use IGMP, PIM-SM and IGMP-Proxy are useless for it.
mDNS (Apple Bonjour) does not use IGMP, PIM-SM and IGMP-Proxy are useless for it.
Re: mDNS repeater feature
Avahi on your raspberry is reflecting mDNS, ROS does nothing here.
Re: mDNS repeater feature
Haha, I misread Till and TIL 
Re: mDNS repeater feature
Trust.Yes, the question is, why separate the IoT, if you don't really need to separate ?
The same reason is why you firewall your input chain from the world... You can't always trust that people won't do the right thing. This is the reason for a LOT of vlans.
However with IoT, there are service needs that have to be met. Easiest example: Chromecast. You need to have mDNS to be able to search from a home / production vlan to the Chromecast device discover the device and set up the initial communication. Once you choose to cast to a specific device... your mobile device is taken out of the loop and the data is pulled from the server / internet service. However, doesn't mean you should trust that Chromecast on your home network. Google and other entities have proven that they want data at nearly all costs. Similar goes with Chinese security cameras.
The design of Chromecast (and other google products) is to capture data (while providing a cool service). We want to limit what PERSONAL data google can capture.
Re: mDNS repeater feature
I spend a lot of time on the Ubiquiti EdgeMAX forums, and there are many noob questions related to getting things to work across vlans.Yes, the question is, why separate the IoT, if you don't really need to separate ?
In my opinion, many people use vlans without enough foundational understanding. They have just heard about how unsafe IoT devices are, and that the IoT devices should be kept separate, then find some recommendation for the ER-X, then come asking for help setting it up with vlans.
Then, soon after they get vlans working, they come back complaining that things don't work any more (chromecast, sonos, printer discovery, etc.)
I put mDNS repeater into the same class as UPnP. It is a bad idea from a security standpoint, but most home users are really more interested in ease of use than security, especially when it comes down to having to deal with family members' complaints about things that used to work no longer working.
These posts always remind me of the https://imgs.xkcd.com/comics/sandboxing_cycle.png cartoon.
If this does get added, it should not be the default. But I can understand why many people want it. It is a compromise between real security and no separation. Supporting mDNS repeater gives more separation than having everything in the same subnet/lan. It is the same argument for allowing a user to use https with "obsolete insecure ciphers" after making them make a manual exception vs. forcing them to use http with absolutely no protection.
FWIW, I don't use either UPnP or mDNS repeater. I just put the untrusted stuff on its own vlan with its own wifi SSID. That does mean I can't cast from my trusted PC, but I can live with that.
Re: mDNS repeater feature
I am just echoing my use case here.
I have 4 private vlans for 4 homes and 1 common guest vlan across all 4 homes.
The TVs in each home sit in their private vlan but sometimes when guests arrive, They want to be able to cast to the TV.
Internet traffic in guest vlan is routed over a vpn and I do not want guests using the private vlans _BUT_ I also want them to be able to cast to the TVs.
Google cast(& Presumably apple's casting tech) requires mdns for discovery and simply will not work if it can't see the TV. It'll be nice to be able to allow specific mdns traffic to be repeated across vlans. It's less safe than isolating the two vlans completely but that will not work in my case.
If I tell them that guests simply can not cast to the TVs, They'll most likely end up sharing the private vlan's password with them and I think that's just worse. :/
I have 4 private vlans for 4 homes and 1 common guest vlan across all 4 homes.
The TVs in each home sit in their private vlan but sometimes when guests arrive, They want to be able to cast to the TV.
Internet traffic in guest vlan is routed over a vpn and I do not want guests using the private vlans _BUT_ I also want them to be able to cast to the TVs.
Google cast(& Presumably apple's casting tech) requires mdns for discovery and simply will not work if it can't see the TV. It'll be nice to be able to allow specific mdns traffic to be repeated across vlans. It's less safe than isolating the two vlans completely but that will not work in my case.
If I tell them that guests simply can not cast to the TVs, They'll most likely end up sharing the private vlan's password with them and I think that's just worse. :/
Re: mDNS repeater feature
So you want your guest to be able to cast to another home? Isn't that what you are asking the ability to do, given you have "1 common guest vlan across all 4 homes."I have 4 private vlans for 4 homes and 1 common guest vlan across all 4 homes.
If I tell them that guests simply can not cast to the TVs, They'll most likely end up sharing the private vlan's password with them and I think that's just worse. :/
I won't go into it more, because this thread isn't the proper place, but I think there are better solutions to your problem than mdns to a common guest network.
-

-
MartyMcSly
just joined
- Posts: 1
- Joined:
Re: mDNS repeater feature
Anyone who's had their home network locked up by ransomware would see the value in separate VLANs.All this do not change my disbelief on need separation from IoT and home private network.
(On home point of view, business/work is another thing...)
Especially if they need their home network to access their work VPN. Say, hypothetically, they might be working from home because of a pandemic, perhaps?
Many IoT devices are built to a price, so security is skimped. They are notorious for being attack vectors.
An IoT VLAN is pretty much home internet security 101 these days.
Re: mDNS repeater feature
Yes, but this won't remain turned on _forever_. I'll only be turning on this repeater when I have some guests at home. (I am writing a wrapper for the mikrotik API and people in 4 homes will get a simple interface to turn this on/off)So you want your guest to be able to cast to another home? Isn't that what you are asking the ability to do, given you have "1 common guest vlan across all 4 homes."
-

-
vikinggeek
Frequent Visitor

- Posts: 54
- Joined:
Re: mDNS repeater feature
Care to share? Looking for something similar such the wife/kids can turn on/off a feature without having access to the router.I am writing a wrapper for the mikrotik API and people in 4 homes will get a simple interface to turn this on/off
Re: mDNS repeater feature
I too have a need for an mDNS repeater for the same reasons.
=> I segregate my networks
=> I have devices across multiple networks that i would like to see each others broadcasts (within limits)
=> I purchased a ton of mikrotik because i an not sheep and walk in a flock
=> i want and like to use the power of the equipment i purchased. Mikrotik is powerful like no other and mDNS is a valid feature request.
=> i am in a group of mikrotik user peers that respect each others opinion and collaborate not criticize
=> i choose to have a high degree of separation within my network
=> if you choose to dump all your equipment onto big flat networks then that's your choice and is totally ok. But not for me.
Adding this mDNS reflector feature would be appreciated. Thanks for your time.
=> I segregate my networks
=> I have devices across multiple networks that i would like to see each others broadcasts (within limits)
=> I purchased a ton of mikrotik because i an not sheep and walk in a flock
=> i want and like to use the power of the equipment i purchased. Mikrotik is powerful like no other and mDNS is a valid feature request.
=> i am in a group of mikrotik user peers that respect each others opinion and collaborate not criticize
=> i choose to have a high degree of separation within my network
=> if you choose to dump all your equipment onto big flat networks then that's your choice and is totally ok. But not for me.
Adding this mDNS reflector feature would be appreciated. Thanks for your time.
Re: mDNS repeater feature
Guessing your customers are not spoiled as othersI am a home user and do not need it.Ever home user needs mDNS.
Why is your assumption so absolute?
It is absolute-ly false.
My 4,000 contracts (home and business), corresponding to more than 16,000 people,
do not have it and no one has ever complained about it.
Please explain which critical part of the home network does not work without mDNS.
Thanks.
We have homestead with smarthome things implemented everywhere which have their own vlan. There is audiosystem around whole farm, which is connected to Loxone server( basically smarthome controller) but employee network is ofcourse on another vlan. And only way to control audioserver is via AirPlay where only mDNS or Bonjour or whatever apple bullshit works, you cannot manually add them so mDNS support would be our only solution. Now we have separate wi-fi for controlling the smarthome things but its kind of annoying for employees to need to switch wi-fi when they wanna change songs for example and then switch back if they wanna access company data. Its kinda specific problem but that doesnt mean there are none.
Re: mDNS repeater feature
Use Alexa devices...
From my Office I can control devices at my Home (different cities and networks) with vocal commands...
From my Office I can control devices at my Home (different cities and networks) with vocal commands...
Re: mDNS repeater feature
You will suggest everything else to prove that mikrotik doesn't need to implement mDNS. Such a simp!Use Alexa devices...
From my Office I can control devices at my Home (different cities and networks) with vocal commands...
Re: mDNS repeater feature
Zerotier?
If mDNS proxy is implemented, the RFC is broken because on RFC mDNS must not be forwarded outside local LAN...
If mDNS proxy is implemented, the RFC is broken because on RFC mDNS must not be forwarded outside local LAN...
Re: mDNS repeater feature
im gonna tell them to change system who cost them 20 000 euroUse Alexa devices...
From my Office I can control devices at my Home (different cities and networks) with vocal commands...
Re: mDNS repeater feature
I see mDNS proxy/repeater as valid feature request and understand why many people want such feature.
But do not understand why some people fight against it so dogged.
During decades networking evolved - we have switching (L2), routing (L3), VLANs, private VLANs, VRFs, VPNs etc. and all tends to separation/segmentation so recommending someone to
put everything to one L2 is strange.
@rextended
You fight mostly against mDNS here. But then you wrote:
"All this do not change my disbelief on need separation from IoT and home private network.
(On home point of view, business/work is another thing...)"
So if you see a value for business, why to deny the same value for home networks? If you do not want it, OK. But why to fight with people who want it.
@normis
Let me give you example of topology you may have at home:
- trusted wired LAN
- trusted (private) WLAN
- guest WLAN
- DMZ for NAS/servers etc,
- DMZ for IoT/media devices
So from 'trusted' LANs you have access to all DMZs, internet etc. And you need the option to cast to media devices in DMZ.
The guest WLAN has access only to internet, but ability cast to media devices. And of course DMZ devices are limited too.
So even if I need to allow some traffic and communication between trusted LANs and media devices, the media/IoT devices are still limited to access other parts of network.
Putting it to one flat L2 would give them more space than it is needed (and all devices are reachable mutually).
If I put media/IoT to separate L3 network, I can even isolate from each other and outside communicate is filtered by FW rules.
At the end it is Mikrotik's decision. It is not only about home networks, but too about small bushiness etc. Even big names can do mDNS repeater/forwarder in some products as in business it is expected to have separated networks. And it is Mikrotik's decision if they aim to business or not.
But do not understand why some people fight against it so dogged.
During decades networking evolved - we have switching (L2), routing (L3), VLANs, private VLANs, VRFs, VPNs etc. and all tends to separation/segmentation so recommending someone to
put everything to one L2 is strange.
@rextended
You fight mostly against mDNS here. But then you wrote:
"All this do not change my disbelief on need separation from IoT and home private network.
(On home point of view, business/work is another thing...)"
So if you see a value for business, why to deny the same value for home networks? If you do not want it, OK. But why to fight with people who want it.
@normis
Let me give you example of topology you may have at home:
- trusted wired LAN
- trusted (private) WLAN
- guest WLAN
- DMZ for NAS/servers etc,
- DMZ for IoT/media devices
So from 'trusted' LANs you have access to all DMZs, internet etc. And you need the option to cast to media devices in DMZ.
The guest WLAN has access only to internet, but ability cast to media devices. And of course DMZ devices are limited too.
So even if I need to allow some traffic and communication between trusted LANs and media devices, the media/IoT devices are still limited to access other parts of network.
Putting it to one flat L2 would give them more space than it is needed (and all devices are reachable mutually).
If I put media/IoT to separate L3 network, I can even isolate from each other and outside communicate is filtered by FW rules.
At the end it is Mikrotik's decision. It is not only about home networks, but too about small bushiness etc. Even big names can do mDNS repeater/forwarder in some products as in business it is expected to have separated networks. And it is Mikrotik's decision if they aim to business or not.
Re: mDNS repeater feature
Another vote here for the feature.
If I'm away from my network and I VPN in, services that rely on mDNS are unavailable. It would be nice to be able to have mDNS requests go across from the VPN subnet to my main subnet. If anyone knows how to do this without an mDNS repeater feature, let me know.
If I'm away from my network and I VPN in, services that rely on mDNS are unavailable. It would be nice to be able to have mDNS requests go across from the VPN subnet to my main subnet. If anyone knows how to do this without an mDNS repeater feature, let me know.
Re: mDNS repeater feature
I've seen this implemented on networks using Aruba APs, specifically with AirGroup. The most common deployment reason I've seen is for AirPrint or AirPlay, ChromeCast to allow these devices in another network to be discovered by guests on other networks. Obviously appropriate firewall is required between the networks, or the segmentation is not as useful.To those people asking for mDNS, can you give examples where it will be useful?
Rextended provided solutions for the given examples. Maybe there are more examples?
-

-
tcxelhyoqiqhmhelha
just joined
- Posts: 1
- Joined:
Re: mDNS repeater feature
FYI, this thread is the top google result for "multicast DNS mikrotik" and it's funny how this isn't implemented yet. I just wanna be able to plug a raspberry pi with a hostname "raspi" into my network and immediately access it by sshing "raspi.local" without having to figure out which 192.168.88.* it got assigned to.
Re: mDNS repeater feature
IoT devices lack security, has vulnerabilities etc. It's always wise to separate them with VLANs.Do not have any sense make separate VLAN of IoT devices and then set Google and Smart TV on "main" Wi-Fi
And with IPv6 you can firewall to accept, established, related, icmpv6 and drop the rest for the IoT VLAN without impacting the main VLAN where default firewall on macOS/Windows/iOS/Android is out of the box doing just that and hence should permit native end-to-end reachability without a middle box for the main VLAN to benefit from native IPv6 without the need for STUN/TURN/ICE/WebRTC and other bs.
Re: mDNS repeater feature
+1 for the mDNS feature also.
Landed here from google.
I am having my IoT devices in a separate VLAN and encounter difficulties managing those with Home Assistant software.
I am baffled that there are no real geeks on Mikrotik side to understand the need for mDNS.
Cheers!
Landed here from google.
I am having my IoT devices in a separate VLAN and encounter difficulties managing those with Home Assistant software.
I am baffled that there are no real geeks on Mikrotik side to understand the need for mDNS.
Cheers!
Re: mDNS repeater feature
The problem is there is no point separating trusted and untrusted vans when you allow the untrusted one inject an advertisement into the trusted one to get the trusted one to call into it not to mention allowing the untrusted one to see all that is advertised on the trusted one. Very helpful in its quest to pretend being one of them.
It would be nice to be able to copy mDNS entries in to static config on the trusted one though. Sort of like a static ip reservation flow. Pick it from list of what is on untrusted side to add static copy of it on the trusted side.
It would be nice to be able to copy mDNS entries in to static config on the trusted one though. Sort of like a static ip reservation flow. Pick it from list of what is on untrusted side to add static copy of it on the trusted side.
-

-
Valerio5000
Member Candidate

- Posts: 101
- Joined:
Re: mDNS repeater feature
I also happened to go to Google here, I use HAP AC2 which acts as a VPN server to other networks with other RBs. Same thing if through Windows or Android I enter the VPN directly .. well it would be fantastic to have the ability to search for a client on a remote network via DNS name. I have been trying to put a solution in ROS directly for months now I understand that it is useless, is it possible that the Mikrotik staff does not care about this convenient functionality?
+1 for me
+1 for me
Re: mDNS repeater feature
That's not true. It's called limiting access. For example, say you wanted to expose port 22 to another vlan, but not port 23, you can limit what can communicate.The problem is there is no point separating trusted and untrusted vans when you allow the untrusted one inject an advertisement into the trusted one to get the trusted one to call into it not to mention allowing the untrusted one to see all that is advertised on the trusted one. Very helpful in its quest to pretend being one of them.
It would be nice to be able to copy mDNS entries in to static config on the trusted one though. Sort of like a static ip reservation flow. Pick it from list of what is on untrusted side to add static copy of it on the trusted side.
Re: mDNS repeater feature
Exactly. Even Enterprise boxes from Cisco, Juniper and the usual suspects provide mDNS proxies to allow AppleTV based screen sharing among subnets so IThings can be used as sources for projectors and big screens in meeting rooms.That's not true. It's called limiting access. For example, say you wanted to expose port 22 to another vlan, but not port 23, you can limit what can communicate.
But it's not unsual in the forum here to have the crowd denying the need for features almost all other vendors have for good reasons. The MT community is a bit special in that regard.
Re: mDNS repeater feature
+1 vote
I'm facing problem with AirPlay (TV is in different VLAN then computer). Container is not solution for me, because TILE arch.
I'm facing problem with AirPlay (TV is in different VLAN then computer). Container is not solution for me, because TILE arch.
Re: mDNS repeater feature
+1 for this feature.
And while we're on the subject of IoT devices, I own several products that rely on UDP broadcast [^1] (Squeezebox to name one ubiquitous device).
I don't mean to hijack but merely want to add to the point: while I understand all the replies questioning the practices of creating such connections between VLANs and subnets, the reality is anyone who is mixing a home and business environment (i.e. SOHO) will somehow need the tools to work around devices that weren't designed in setups for multiple L2 segments, balancing usability and security.
The ability to selectively relay, block or allow these mDNS and UDP broadcasts in non-bridged settings, IMHO would immediately turn RouterOS into the swiss army knife for SOHO environments. Suggestions to run this in Docker on a MT-device from a management point of view to me still not ideal as for every change in the network I would need to recreate the container (i.e. with the changed interfaces - yes I understand that I could script this command) rather than just change a setting in RouterOS. At this point, using docker-compose on my Docker node would probably be simpler from a management point of view.
[^1]: According to some forum posts you're supposed to get this to work using dst-nat, but I was never able to get it working without running a Pi with https://github.com/nomeata/udp-broadcast-relay/ (incidently also running Avahi reflector) - but it's yet another to configure, update etc. This is why for now I've decided to merge the "trusted" access layer (managed phones, laptops etc.) and IoT segments into one untrusted L2 segment and require internal VPN to the business applications. From a security perspective this is arguably the cleanest solution, but from a usability perspective less so and it doesn't isolate the different devices as as much as I would like to.
And while we're on the subject of IoT devices, I own several products that rely on UDP broadcast [^1] (Squeezebox to name one ubiquitous device).
I don't mean to hijack but merely want to add to the point: while I understand all the replies questioning the practices of creating such connections between VLANs and subnets, the reality is anyone who is mixing a home and business environment (i.e. SOHO) will somehow need the tools to work around devices that weren't designed in setups for multiple L2 segments, balancing usability and security.
The ability to selectively relay, block or allow these mDNS and UDP broadcasts in non-bridged settings, IMHO would immediately turn RouterOS into the swiss army knife for SOHO environments. Suggestions to run this in Docker on a MT-device from a management point of view to me still not ideal as for every change in the network I would need to recreate the container (i.e. with the changed interfaces - yes I understand that I could script this command) rather than just change a setting in RouterOS. At this point, using docker-compose on my Docker node would probably be simpler from a management point of view.
[^1]: According to some forum posts you're supposed to get this to work using dst-nat, but I was never able to get it working without running a Pi with https://github.com/nomeata/udp-broadcast-relay/ (incidently also running Avahi reflector) - but it's yet another to configure, update etc. This is why for now I've decided to merge the "trusted" access layer (managed phones, laptops etc.) and IoT segments into one untrusted L2 segment and require internal VPN to the business applications. From a security perspective this is arguably the cleanest solution, but from a usability perspective less so and it doesn't isolate the different devices as as much as I would like to.
Re: mDNS repeater feature
My 2 cent:
Stop asking MT to do a non-RFC thing. MT will most likely not implement such a tool.
MT as a router manufacturer will always obey RFCs, and your wish is to forward/feflect/proxy local frames.
mDNS uses the follwing multicast address:
224.0.0.251 mDNS
But there is a good thing, you can build your own small mDNS-reflector with AVAHI.
All you have to do is setup a Raspberry, install AVAHI and connect this RPi with the desired VLANs.
E. g. you have VLAN10 and VLAN20, all you have to do is, to create a VLAN trunk, tagged VID10,20 and connect this to the RPi. Thats a step you can implment within a few minutes. So, stop waiting/asking for a feature that will never come and go on and do it your own!
Further references:
https://www.cisco.com/c/en/us/td/docs/s ... er_01.html
https://www.dell.com/support/kbdoc/de-d ... es?lang=en
Stop asking MT to do a non-RFC thing. MT will most likely not implement such a tool.
MT as a router manufacturer will always obey RFCs, and your wish is to forward/feflect/proxy local frames.
mDNS uses the follwing multicast address:
224.0.0.251 mDNS
https://www.iana.org/assignments/multic ... sses.xhtmlIPv4 Multicast Address Space Registry
The range of addresses between 224.0.0.0 and 224.0.0.255, inclusive,
is reserved for the use of routing protocols and other low-level
topology discovery or maintenance protocols, such as gateway discovery
and group membership reporting. Multicast routers should not forward
any multicast datagram with destination addresses in this range,
regardless of its TTL.
But there is a good thing, you can build your own small mDNS-reflector with AVAHI.
All you have to do is setup a Raspberry, install AVAHI and connect this RPi with the desired VLANs.
E. g. you have VLAN10 and VLAN20, all you have to do is, to create a VLAN trunk, tagged VID10,20 and connect this to the RPi. Thats a step you can implment within a few minutes. So, stop waiting/asking for a feature that will never come and go on and do it your own!
Further references:
https://www.cisco.com/c/en/us/td/docs/s ... er_01.html
https://www.dell.com/support/kbdoc/de-d ... es?lang=en
Re: mDNS repeater feature
Yes, 224.0.0.0/24 addresses shall not be and are not routed by normal routing.
That's why an additional mDNS reflector is required in the first place to propagate mDNS among subnets.
Technically, it is an odd thing to do. But practically there are many add-on implementations by Cisco et al to make AirPlay working so all the corporate iThings can use AirPlay to share to big screens using AppleTVs. Such setups are widely seen in coorp networks, because of the iThings management loves to use.
No one is asking to route mDNS violating RFCs. It is about having an optional service working as reflector among subnets, on top and independent of normal routing.
Similar to the multicast proxy allowing multicast traffic to pass the router, which normally would not be routed.
One of the Cisco flavors of mDSN reflector is called "Service Discovery Gateway" as described here:
https://www.cisco.com/en/US/docs/switch ... 10010.html
All other usual suspects like Juniper have similar addons.
Yes, it can be done using a Avahi on a raspi. Yes, on certain MT devices it can run as a docker container.
While I personally do not need it, I see it would be easier to have it as an (optional) package for ROS were required and it is a valid feature request.
I do not get the resistance here against a feature widely available on other brands and widely used in coorp networks.
There might be reasons for MT not to add it, but routing RFCs are not part of it. mDNS reflectors are not related to routing.
mDNS reflectors are a required evil to help with things initially designed for single subnet SOHO networks like Airplay. But creeped into coorp networks due to the popularity of iThings in management.
That's why an additional mDNS reflector is required in the first place to propagate mDNS among subnets.
Technically, it is an odd thing to do. But practically there are many add-on implementations by Cisco et al to make AirPlay working so all the corporate iThings can use AirPlay to share to big screens using AppleTVs. Such setups are widely seen in coorp networks, because of the iThings management loves to use.
No one is asking to route mDNS violating RFCs. It is about having an optional service working as reflector among subnets, on top and independent of normal routing.
Similar to the multicast proxy allowing multicast traffic to pass the router, which normally would not be routed.
One of the Cisco flavors of mDSN reflector is called "Service Discovery Gateway" as described here:
https://www.cisco.com/en/US/docs/switch ... 10010.html
All other usual suspects like Juniper have similar addons.
Yes, it can be done using a Avahi on a raspi. Yes, on certain MT devices it can run as a docker container.
While I personally do not need it, I see it would be easier to have it as an (optional) package for ROS were required and it is a valid feature request.
I do not get the resistance here against a feature widely available on other brands and widely used in coorp networks.
There might be reasons for MT not to add it, but routing RFCs are not part of it. mDNS reflectors are not related to routing.
mDNS reflectors are a required evil to help with things initially designed for single subnet SOHO networks like Airplay. But creeped into coorp networks due to the popularity of iThings in management.
Re: mDNS repeater feature
It do not say they have to ROUTE (IP-Routing at Layer3).
IANA says:
MT is a Multicast-Router, so MT will never FORWARD mDNS. This applies to "Proxy" or "Reflect" too.
Of course, MT could implement such a tool, but they will almost never do. Instead of asking for years, invest a few minutes and create your own solution.
I will not say the wish is totally obsolete and for a lot people a much easier solution, but as written, its a wish that will (most likely) never come true with the native MT ROS.
BTW: The right way to aks for the functionality would be: Not MT should create a workaround (mDNS forward over L2 boundaries is exactly this). Ask Apple to use a protocol which is up-to-date (VLANs are not a fancy stuff from year 2050 anymore). They (Apple) have chosen mDNS which is a Link-Local-Protocol. They know exactly what this means in regards of VLANs. Its not MTs fault, its Apple fault to use mDNS.
IANA says:
Multicast routers should not forward
any multicast datagram with destination addresses in this range,
regardless of its TTL.
MT is a Multicast-Router, so MT will never FORWARD mDNS. This applies to "Proxy" or "Reflect" too.
Of course, MT could implement such a tool, but they will almost never do. Instead of asking for years, invest a few minutes and create your own solution.
I will not say the wish is totally obsolete and for a lot people a much easier solution, but as written, its a wish that will (most likely) never come true with the native MT ROS.
BTW: The right way to aks for the functionality would be: Not MT should create a workaround (mDNS forward over L2 boundaries is exactly this). Ask Apple to use a protocol which is up-to-date (VLANs are not a fancy stuff from year 2050 anymore). They (Apple) have chosen mDNS which is a Link-Local-Protocol. They know exactly what this means in regards of VLANs. Its not MTs fault, its Apple fault to use mDNS.
Re: mDNS repeater feature
1. Yes, mDNS is an "rfc thing"I They know exactly what this means in regards of VLANs. Its not MTs fault, its Apple fault to use mDNS.
https://www.rfc-editor.org/rfc/rfc6762 (since 2013!)
2. every big vendor has some implementation
3. many people use it and it will probably get more and more important with IOT (people are generally lazy)
4. there are several useful open source implementations
So IMHO it would be nice to have.
Edit: something else comes to my mind, the Internet is full of workarounds, which were or are considered harmful & non standard, just to mention NAT, VLSM,
BR
Re: mDNS repeater feature
As a hobbyist, this might be a valid point.Its not MTs fault, its Apple fault to use mDNS.
As a professional:
Have you ever tried to sell gear not supporting the managements beloved iThings to a company?
Ever tried to explain to a "important" manager that his shiny new iPad Pro cannot connect to the screen in the meeting room because it's Apple's fault?
I bet not.
Re: mDNS repeater feature
It is not a valid point even for hobbyists. I was explaining to a colleague how proud I am using mikrotik products, and of the capsman network I have setup and the problem I have to "cast" video from my mobile phone connected to wifi, to my TV connected to the wired network (on different networks), and he replies: "oh, you have to configure mDNS". He is using products of another vendor, and it was implemented years ago....
Last edited by BartoszP on Sun Oct 30, 2022 1:00 am, edited 1 time in total.
Reason: Removed unneeded quote
Reason: Removed unneeded quote
Re: mDNS repeater feature
+1 for mDNS repearter.
I don't want to run an additional computer just for mDNS.
OpenWRT offers an mDNS package, you may use it.
I don't want to run an additional computer just for mDNS.
OpenWRT offers an mDNS package, you may use it.
Re: mDNS repeater feature
+1 to the mDNS reflector. It would be a nice feature to have.
Re: mDNS repeater feature
+1 to the mDNS reflector. It would be a nice feature to have that would help segmentation for IoT devices without additional hardware.
Re: mDNS repeater feature
+1 to the mDNS reflector. I would use this feature also...
Re: mDNS repeater feature
+1 for mDNS feature.
Last edited by kJpermol on Thu Nov 24, 2022 6:48 pm, edited 1 time in total.
Re: mDNS repeater feature
Hello, in the meantime we wait for the highly desired mDNS repeater/reflector, has someone tried any container package and is able to give some advice for the easiest one?
Those are the ones found:
- https://hub.docker.com/r/yuxzhu/mdns-reflector
- https://hub.docker.com/r/ydkn/avahi
- https://hub.docker.com/r/flungo/avahi
- https://hub.docker.com/r/angelnu/mdns_repeater
- https://hub.docker.com/r/monstrenyatko/mdns-repeater
Those are the ones found:
- https://hub.docker.com/r/yuxzhu/mdns-reflector
- https://hub.docker.com/r/ydkn/avahi
- https://hub.docker.com/r/flungo/avahi
- https://hub.docker.com/r/angelnu/mdns_repeater
- https://hub.docker.com/r/monstrenyatko/mdns-repeater
Re: mDNS repeater feature
Or, how about just a mDNS listener that shows up in /ip/neighbors to start?in the meantime we wait for the highly desired mDNS repeater/reflector
On reflection, and not saying Mikrotik shouldn't add Avanti-like features... but I still struggle that if you need mDNS to have a different scope than the existing Layer2 segment, something is wrong with your network design. If the only issue is printers/etc, SRV records in DNS, or using an LDAP sever, seems like a better approach to discovery needs by apps.
Re: mDNS repeater feature
Could agree with your statement, currently using DNS Static for printers, Chromecast etc... but for example mobile phones are not able to the printer using ip or name.
Re: mDNS repeater feature
My two cents on this matter. I still feel no need for such a mDNS feature actually. I have a few devices on a subnet; among them, a plex app runs on my smartTV which can connect to my Plex server laying on a different subnet; just a couple of firewall rules make the job done. However, I think that this mDNS is something better to have on our Mikrotik device than not, considering also that other competitors already have had it for a long time. If you don't use it you can just leave it turned off or disable it.
Re: mDNS repeater feature
Always the printers... Didn't mean sound that harsh. It's actually problem: you'd like still find things, like printers, on the entire network, even if you "segment stuff" (e.g. use VLANs/multiple bridges/switch chip).Could agree with your statement, currently using DNS Static for printers, Chromecast etc... but for example mobile phones are not able to the printer using ip or name.
To answer the question about the using mDNS containers, I'm just not sure any of them are "simple". You're kinda forced to wire up all the Mikrotik [v]LANs to the container on the RouterOS side (otherwise the container wouldn't have access to need networks to use multicast on). After that you have to have configure Avahi (or similar) to describe how you want to listen/reflect/redirect the provided VLAN. And for a pre-packaged container, you have to describe this in environment variables.
So to your question about "what container to use?", my advice is to start with your own Dockerfile that has the Avahi config file you want - to me that generally an easier approach, than un-winding how someone else mapped the actual mDNS configuration files USED to the potentially more limited environment variables wrapped up in a pre-packaged container (e.g. Docker Hub).
That being said, if you can't access something by IP address, not sure mDNS would help – at the end of mDNS process it's just an IP address to use (e.g.mDNS = same as DNS, just multicast instead unicast). So mDNS providing the same IP you're already trying (and not working) on the smartphones/etc. to your printers may not help.
Re: mDNS repeater feature
I could also use this feature. I have an Occulus Quest 2 and have setup wireguard to connect my house to a family member's house so I can easily backup important files to a remote site. We also often get together and I wanted to let my nieces and nephews enjoy some games that wouldn't be majorly impacted from some additional latency. But like apple and chromecast, the Airlink feature of the Occulus relies on mDNS.
I'm kind of perplexed by the argument that "the issue lies with apple for using mDNS". Why are we arguing against reality? Rather than complaining that company "X" shouldn't have used it, don't we just have to deal with the fact that Apple, Meta, and Alphabet, the biggest names out there ARE using it? Combining that with the fact that companies like Cisco and Juniper offer mDNS reflection packages there is a valid way to implement it that meets "RFC" specs, right?
In the meanwhile, I saw some people discussing using something like a raspberry pi running Avahi. How would one go about setting that up with the MT router itself being the wiregaurd host?
I'm kind of perplexed by the argument that "the issue lies with apple for using mDNS". Why are we arguing against reality? Rather than complaining that company "X" shouldn't have used it, don't we just have to deal with the fact that Apple, Meta, and Alphabet, the biggest names out there ARE using it? Combining that with the fact that companies like Cisco and Juniper offer mDNS reflection packages there is a valid way to implement it that meets "RFC" specs, right?
In the meanwhile, I saw some people discussing using something like a raspberry pi running Avahi. How would one go about setting that up with the MT router itself being the wiregaurd host?
Re: mDNS repeater feature
Why have a firewall if you are going to use port forwarding?Yes, the question is, why separate the IoT, if you don't really need to separate ?
Why support UPnP when you can use port forwarding instead with better control?
The reason is because there are many users that don't want complete isolation, but still want convenience more than absolute separation, and many don't even want to RTFM, they just want a simple "click this to make mDNS work".
The fact is, most other vendors selling into the home market segment support mDNS repeaters. Just like they support UPnP2 or UPnP.
MikroTik obviously doesn't plan to add support, even though there are many request for the feature, based on the age of this thread, the retorical question posted by @normis, followed by many posts, but then crickets from MikroTik.
So if this is an important feature for you, vote with your wallet and buy a router that does support it. They are not hard to find. Your only other option at this time is to add something like an unobtainable Raspberry Pi or to have a MikroTik router that supports containers (or OpenWrt see this for example).
I really don't understand MikroTik's stance on this. There is no need to make it the default, and I wouldn't want it to be. But what is the reason for not adding the functionality? Is it that it takes too much code space in the limited flash on many MikroTik routers?
I really don't care about it myself, but it seems like adding the functionality should be relatively easy, given that there are many opensource implementations available. But I do think that NIH (not invented here) syndrome is strong at MikroTik, for example their refusal to support rfc3021/31 subnet masks, because they invented their own proprietary /32 method that can work with /31 in certain circumstances, but not all.
And then MikroTik responds with posts like this that say their /32 subnets are superior to rfc3021, and that's the end of the discussion on their part. "RFCs? We don't need no stinking RFCs"
Re: mDNS repeater feature
I'm 100% with @Buckeye.
The TL;DR version is the RFC answer to dealing mDNS needing to span the local network/segment is actually RFC6763, https://www.rfc-editor.org/rfc/rfc6763#page-30 which is SD-DNS part of mDNS. Essentially if you add _whateverservice._tcp... in the "real" DNS, you can always have a device being able to be found. Most mDNS lookups will fall back to unicast (regular) DNS is how that all works. mDNS is really more about dynamically creating SRV records, but if you only have a handful of home things, a few the right static DNS entries save a container full of work.
In the most recent RFC in the mDNS line, RFC8766, the summary there actually covers most of the ground in this thread, and the agreed IETF reasoning. See below. The note about Wi-Fi was interesting...
I'll just point out reflection and repeaters are NOT in any IETF RFC (at least as AFAIK), for reasons explained below.there is a valid way to implement it that meets "RFC" specs, right?
The TL;DR version is the RFC answer to dealing mDNS needing to span the local network/segment is actually RFC6763, https://www.rfc-editor.org/rfc/rfc6763#page-30 which is SD-DNS part of mDNS. Essentially if you add _whateverservice._tcp... in the "real" DNS, you can always have a device being able to be found. Most mDNS lookups will fall back to unicast (regular) DNS is how that all works. mDNS is really more about dynamically creating SRV records, but if you only have a handful of home things, a few the right static DNS entries save a container full of work.
In the most recent RFC in the mDNS line, RFC8766, the summary there actually covers most of the ground in this thread, and the agreed IETF reasoning. See below. The note about Wi-Fi was interesting...
Multicast DNS [RFC6762] and its companion technology DNS-based
Service Discovery [RFC6763] were created to provide IP networking
with the ease of use and autoconfiguration for which AppleTalk was
well known [RFC6760] [ZC] [ROADMAP].
For a small home network consisting of just a single link (or a few
physical links bridged together to appear as a single logical link
from the point of view of IP), Multicast DNS [RFC6762] is sufficient
for client devices to look up the ".local" host names of peers on the
same home network, and to use Multicast DNS-based Service Discovery
(DNS-SD) [RFC6763] to discover services offered on that home network.
For a larger network consisting of multiple links that are
interconnected using IP-layer routing instead of link-layer bridging,
link-local Multicast DNS alone is insufficient because link-local
Multicast DNS packets, by design, are not propagated onto other
links.
Using link-local multicast packets for Multicast DNS was a conscious
design choice [RFC6762]. Even when limited to a single link,
multicast traffic is still generally considered to be more expensive
than unicast, because multicast traffic impacts many devices instead
of just a single recipient. In addition, with some technologies like
Wi-Fi [IEEE-11], multicast traffic is inherently less efficient and
less reliable than unicast, because Wi-Fi multicast traffic is sent
at lower data rates, and is not acknowledged [MCAST]. Increasing the
amount of expensive multicast traffic by flooding it across multiple
links would make the traffic load even worse.
Partitioning the network into many small links curtails the spread of
expensive multicast traffic but limits the discoverability of
services. At the opposite end of the spectrum, using a very large
local link with thousands of hosts enables better service discovery
but at the cost of larger amounts of multicast traffic.
Performing DNS-based Service Discovery using purely Unicast DNS is
more efficient and doesn't require large multicast domains but does
require that the relevant data be available in the Unicast DNS
namespace. The Unicast DNS namespace in question could fall within a
traditionally assigned globally unique domain name, or it could be
within a private local unicast domain name such as ".home.arpa"
[RFC8375].
In the DNS-SD specification [RFC6763], Section 10 ("Populating the
DNS with Information") discusses various possible ways that a
service's PTR, SRV, TXT, and address records can make their way into
the Unicast DNS namespace, including manual zone file configuration
[RFC1034] [RFC1035], DNS Update [RFC2136] [RFC3007], and proxies of
various kinds.
-

-
mattycourtney
just joined
- Posts: 6
- Joined:
Re: mDNS repeater feature
+1 to the request for an mDNS repeater! Without the mulicast package on ROS 7 it's not currently possible to use mDNS inter-VLAN; having an mDNS repeater would solve this
Re: mDNS repeater feature
One more request for mDNS repeater. Currently there is no way to use AirPrint-like features in corporate networks with printers and users on different VLANs without using VM with mDNS repeater.
Re: mDNS repeater feature
If you have a recent-enough router (one that supports containers) you can use https://github.com/mag1024/mikrotik-doc ... s-repeater to run the repeater directly on the router, without a VM.
That said, +1 for making this a built-in feature.
That said, +1 for making this a built-in feature.
Re: mDNS repeater feature
+1
First of all it story comes from bad Mikrotik DNS, that can not handle more then ~10k entries for spam filter. OK, replacing it by pi.hole with crazy performance gain. Then printserver that Mikrotik can not handle at all. Ok, installing cups and raspberry sharing printers by mDNS. Ok, trying to make normal VPN from Mikrotik and no way to establish connection to protonvpn (Mikrotik have tiny part of standard, that it VPN supports). Ok, installing OpenVPN on pi, successful connect to proton. Speed is better then on 16 core Mikrotik . OK, redirecting pefixes to raspberry and it does not work without hairpin NAT. Ok, moving raspberry to another subnet+vlan, now VPN works fine and Iam loosing printers. Damn...
First of all it story comes from bad Mikrotik DNS, that can not handle more then ~10k entries for spam filter. OK, replacing it by pi.hole with crazy performance gain. Then printserver that Mikrotik can not handle at all. Ok, installing cups and raspberry sharing printers by mDNS. Ok, trying to make normal VPN from Mikrotik and no way to establish connection to protonvpn (Mikrotik have tiny part of standard, that it VPN supports). Ok, installing OpenVPN on pi, successful connect to proton. Speed is better then on 16 core Mikrotik . OK, redirecting pefixes to raspberry and it does not work without hairpin NAT. Ok, moving raspberry to another subnet+vlan, now VPN works fine and Iam loosing printers. Damn...
Re: mDNS repeater feature
The veth interface has no firewalling (as far as I know on other systems). So how to make sure that only the requested ports go through the VM?If you have a recent-enough router (one that supports containers) you can use https://github.com/mag1024/mikrotik-doc ... s-repeater to run the repeater directly on the router, without a VM.
Re: mDNS repeater feature
So should I declare for a CUPS server? Should I listen to my printer with Wireshark?The TL;DR version is the RFC answer to dealing mDNS needing to span the local network/segment is actually RFC6763, https://www.rfc-editor.org/rfc/rfc6763#page-30 which is SD-DNS part of mDNS. Essentially if you add _whateverservice._tcp... in the "real" DNS, you can always have a device being able to be found. Most mDNS lookups will fall back to unicast (regular) DNS is how that all works. mDNS is really more about dynamically creating SRV records, but if you only have a handful of home things, a few the right static DNS entries save a container full of work.
Re: mDNS repeater feature
Just an idea, you could add a bridge's filter to restrict the container's veth to only allow multicast traffic I suppose.The veth interface has no firewalling (as far as I know on other systems). So how to make sure that only the requested ports go through the VM?If you have a recent-enough router (one that supports containers) you can use https://github.com/mag1024/mikrotik-doc ... s-repeater to run the repeater directly on the router, without a VM.
Re: mDNS repeater feature
On a Mac, there is a command "dns-sd -Z" that outputs the LAN's DNS records from mDNS broadcast, into a DNS zone file that can be use in a DNS server. I presume some similar tool exists for Win/Linux. Only issue is Mikrotik's DNS doesn't support one of the DNS type (PTR), so those records have to go into some other DNS server (perhaps Pi-Hole, but I haven't tested)So should I declare for a CUPS server? Should I listen to my printer with Wireshark?The TL;DR version... RFC6763, https://www.rfc-editor.org/rfc/rfc6763#page-30 which is SD-DNS part of mDNS. Essentially if you add _whateverservice._tcp... in the "real" DNS, you can always have a device being able to be found. Most mDNS lookups will fall back to unicast (regular) DNS is how that all works. mDNS is really more about dynamically creating SRV records, but if you only have a handful of home things, a few the right static DNS entries save a container full of work.
Re: mDNS repeater feature
I’m new here, just waiting on the arrival of my new Mikrotik router which I was really excited about… am I to understand that in (almost) 2023 mDNS is NOT a feature of Mikrotik routers?? I have a house full of IOT devices and use Home Assistant to bridge everything beautifully to homekit for me. All my IOT devices, cameras etc. My plan was to get a good router and actually segment everything into separate LANs. Im coming from pfsense, am I going to regret this decision?
Re: mDNS repeater feature
Did you buy something that you can run a container on? If not then yes you’re going to regret this purchase. It has been made clear certain things mdns, fixing ipv6 on their wireguard implementation etc are just not in the cards. You can of course do it yourself with a container on mikrotik for mdns or like so many things in this ecosystem. Get another device and do the lifting for the nice to have features you won’t find here.I’m new here, just waiting on the arrival of my new Mikrotik router which I was really excited about… am I to understand that in (almost) 2023 mDNS is NOT a feature of Mikrotik routers?? I have a house full of IOT devices and use Home Assistant to bridge everything beautifully to homekit for me. All my IOT devices, cameras etc. My plan was to get a good router and actually segment everything into separate LANs. Im coming from pfsense, am I going to regret this decision?
Re: mDNS repeater feature
Brooding it over, mDNS allows information to flow from on vlan to another.I’m new here, just waiting on the arrival of my new Mikrotik router which I was really excited about… am I to understand that in (almost) 2023 mDNS is NOT a feature of Mikrotik routers?? I have a house full of IOT devices and use Home Assistant to bridge everything beautifully to homekit for me. All my IOT devices, cameras etc. My plan was to get a good router and actually segment everything into separate LANs. Im coming from pfsense, am I going to regret this decision?
This may be not secure by design, this may be the explanation why Mikrotik does not plan to support it.
Re: mDNS repeater feature
Brooding it over, mDNS allows information to flow from on vlan to another.
This may be not secure by design, this may be the explanation why Mikrotik does not plan to support it.
[/quote]
I can also expose winbox ports to the internet, have no firewall. All terrible security choices but the decision is left to me. mDNS is a standard found everywhere else. Seems broken by design to say we won’t support this for security reasons. That’s a decision that the user must make just like having sane firewall rules for their environment
This may be not secure by design, this may be the explanation why Mikrotik does not plan to support it.
[/quote]
I can also expose winbox ports to the internet, have no firewall. All terrible security choices but the decision is left to me. mDNS is a standard found everywhere else. Seems broken by design to say we won’t support this for security reasons. That’s a decision that the user must make just like having sane firewall rules for their environment
Re: mDNS repeater feature
That didn't prevent MikroTik from supporting port forwarding or UPnP. And evidently MikroTik doesn't even support upnp2 (miniupnpd) which offers more secure options. see this thread UPnP security questionsSeems broken by design to say we won’t support this for security reasons.
So using the security card isn't a valid excuse for not allowing a user to choose to use an insecure "feature". I don't think anyone is requesting the option to be the default.
disclaimer: I don't use port forwarding, upnp, upnp2 or mdns repeater or reflector on my ER-X, but they are all options that are available.
This is a bit like the major broswers no longer supporting "weak" SSL/TLS options at all. And forcing users that have legacy equipment that does not support the newer versions to use http or an old version of the browser that will allow an exclusion for a specific site. When you look at the options of poor security or no security, which is better?
Re: mDNS repeater feature
using the security card isn't a valid excuse
I think I might be one of the most likely of this forum's members to go around waving the "security" flag, and even I will tell you that a flat refusal to support mDNS forwarding on security grounds is bogus.
mDNS forwarding is a routing decision made by the network's manager. Routing is what routers do, per the admin's instructions.
mDNS is no more a "security risk" than is PIM-SM. Yes, it should be off by default, but it should be available, left up to the admin to employ properly when enabled.
Re: mDNS repeater feature
Did you buy something that you can run a container on? If not then yes you’re going to regret this purchase.
I'm not certain about that. I still think this approach is worth trying.
If you're wondering why I don't try it and report back, it's because on the networks I manage that have mDNS devices, I don't (yet) use VLANs, so I don't run into the problem in the first place.
I believe coupling that switch rule with suitable inter-VLAN routing rules should allow mDNS based negotiations to transit VLANs. If not, I'd like to know why.
Re: mDNS repeater feature
I think @raimondsp point isn't that mDNS is insecure. Rather that folks overuse VLANs under "illusion of safety". Not quite the same thing.
My guess at MT's rational is that it's a lot of work, for what they think are "questionable" use cases.[...] you bought a no-name smart light bulb on eBay and you don't want it to access your NAS and upload its content to the internet. But you want to be able to turn on/off the bulb from your PC/smartphone. Then why not put your PC/smartphone under both IoT and NAS VLANs?
Re: mDNS repeater feature
it's a lot of work, for what they think are "questionable" use cases.
There are far better use cases.
Here's one: AirPrint in a corporate environment. It's convenient in BYOD shops to let people print from their iPhones or whatever, but if you think printers that haven't received firmware updates for 10 years belong on the employee WiFi LAN, you're either insane or not paying attention to security. Isolating the two with VLANs but allowing one-way print requests is entirely sensible.
Re: mDNS repeater feature
Here's another: screen-sharing to conference room displays. The plan to put a bad-ass LED wall in the boardroom might give the CEO a fuzzy, but if you tell him he can't have it because there's a Chinese ODM board at the heart of it that's as full of holes as a block of Jarlsberg, he's gonna buy the video wall anyway and then yell at IT when he can't show his charts and graphs at the next board meeting because someone with a clue put the video wall on a different VLAN than the WiFi.
Re: mDNS repeater feature
I understand the reason why you would want to put IoT devices under a separate VLAN. For instance, you bought a no-name smart light bulb on eBay and you don't want it to access your NAS and upload its content to the internet. But you want to be able to turn on/off the bulb from your PC/smartphone.
This is a very good example of the threat model I would like to protect against in my network setup. Most of us have an increasing number of (IoT) devices which run very obscure software stacks. A random bulb bought from eBay is a very example, but also, technically, there is nothing preventing Google to send a software update to my Chromecast and turn it into a spoofer. Having such a device completely free to roam in my network seems unnecessary and undesirable.
Then why not put your PC/smartphone under both IoT and NAS VLANs? Then PC will be able to access both IoT and NAS devices, but IoT cannot access NAS.
How would I do this? How do I setup my iPhone or Android phone to participate in more than one VLANs?
What you are trying to do, is to segregate the network on L2 (via VLAN), but then combine it together on L3 (via inter-VLAN routing). Without a firewall, there is no safety here, only an illusion of it. Yes, IoT devices on one VLAN cannot do neighbor discovery, but with inter-VLAN routing, nobody prevents them to scan the routed network (unless a properly configured firewall). For example, your PC VLAN 10 IP 192.168.10.1/24 accesses a spyware light bulb on VLAN 20 IP 192.168.20.31/24, then the bulb scans the source network (e.g.), finds a NAS at 192.168.10.75 and does nasty things with that.Code: Select allnmap -sn 192.168.10.0/24
Of course, you can configure the firewall to allow traffic only from VLAN ID 10 to 20, but backward - only within the established connections (btw, it won't work in case of mDNS due to multicast), but IMHO that's overcomplicated.
It is much easier to assign PC to both VLANs with IP 192.168.10.1/24 and 192.168.20.1/24 for VLAN 10 and 20 respectively and to prevent (by simply not creating) routing between 192.168.10.0/24 and 192.168.20.0/24 networks.
Indeed, ideally we want an IoT device to be segregated from everything else and allowed only the traffic that is expected from it. For example, an IoT device (e.g., a smart bulb) which uses MQTT should only be allowed to connect to the MQTT server via the relevant port. No other traffic needs to be allowed. In this example, RouterOS has sufficient support for me to implement this. The bulb is in the IoT vlan and the MQTT server is either in the IoT vlan and the firewall/routing rules allows me to access the MQTT server, or the MQTT server has access to both VLANs. Regardless of whether such an L3 segregation (via routing and firewall rules) is overly complicated or not, it is perfectly possible with features already supported by RouterOS (/ip/firewall and /ip/route).
Unfortunately, this is not as easy with devices that implement some form of autodiscovery via protocols such as mDNS, because these protocols assume that they are in the some broadcast domain.
L2 segregation is also possible in RouterOS but at the moment the way it is implemented (IEEE 802.1Q) makes it a binary decision (either no or complete segregation). Two devices either live in different VLANs and there is not broadcast between the two (e.g., mDNS, DHCP requests), or they live in the same VLAN and all broadcast messages are seen across the entire VLAN. I think the feature we're asking for here is a tool to repeat mDNS broadcasts across VLANs.
Last edited by relokin on Sun Jan 01, 2023 11:35 pm, edited 1 time in total.
Re: mDNS repeater feature
On a Mac, there is a command "dns-sd -Z" that outputs the LAN's DNS records from mDNS broadcast, into a DNS zone file that can be use in a DNS server. I presume some similar tool exists for Win/Linux. Only issue is Mikrotik's DNS doesn't support one of the DNS type (PTR), so those records have to go into some other DNS server (perhaps Pi-Hole, but I haven't tested)
Sorry for my late reply. On Debian installed "mdns-scan" package, which returns the PTR addresses, example:
avahi-resolve --name allows to map the hostname to its IP addresses.mdns-scan
...
XXXX._spotify-connect._tcp.local
Debian also offers "mdnsd" package:
embeddable Multicast DNS Daemon
This is a standalone mDNS-SD daemon for small systems. Although still
limited in functionality it can announce services like FTP, HTTP, and
SSH and respond to scanning (enumeration) requests from tools like
mdns-scan.
Re: mDNS repeater feature
https://github.com/vfreex/mdns-reflector
is also a good candidate and has Docker files.
There is a previous post about mdns-reflector.
is also a good candidate and has Docker files.
Anyhow I don't know the internal and security implications.docker pull yuxzhu/mdns-reflector:latest
There is a previous post about mdns-reflector.
Re: mDNS repeater feature
Can somebody make a simple tutorial to demonize any working docker mDNS reflector with two interfaces on ROS7?https://github.com/vfreex/mdns-reflector
is also a good candidate and has Docker files.
Thanks.
Re: mDNS repeater feature
Chromecasting and Casing (audio/ video / printer discovery )in general between the vlans, for example cast from the phone that is on the main network to Iot network etcTo those people asking for mDNS, can you give examples where it will be useful?
Rextended provided solutions for the given examples. Maybe there are more examples?
Re: mDNS repeater feature
This is my original post. Still no progress on mDNS Repeating.
Why do i own a ton of Mikrotik, because its complex technically capable gear and thats who I am. My house is full of segmented networks, VLANS and SSIDs. I run everything from Sat, LORA, WiFi and etherything I can bolt onto my home lab. Mikrotik is at the heart of it all.
If you run a big flat network that is your choice. no criticism here. I choose not to do that and I choose to use my tiks the way they can be used.
So why does Mikrotik, a company that makes such amazing kit continue to ignore this simple little feature request?
My house is full of Google and Apple and i want mDNS to repeat and propegate across my network segments.
Mikrotik Devs. Admins & Management - Does anyone from Mikrotik read our forums, do you have any interest in understaning your loyal communities feedback.
AGAIN - Humbly requesting an mDNS Repeater feature for these amazing product so we can use our tiks the way we want them.
Why do i own a ton of Mikrotik, because its complex technically capable gear and thats who I am. My house is full of segmented networks, VLANS and SSIDs. I run everything from Sat, LORA, WiFi and etherything I can bolt onto my home lab. Mikrotik is at the heart of it all.
If you run a big flat network that is your choice. no criticism here. I choose not to do that and I choose to use my tiks the way they can be used.
So why does Mikrotik, a company that makes such amazing kit continue to ignore this simple little feature request?
My house is full of Google and Apple and i want mDNS to repeat and propegate across my network segments.
Mikrotik Devs. Admins & Management - Does anyone from Mikrotik read our forums, do you have any interest in understaning your loyal communities feedback.
AGAIN - Humbly requesting an mDNS Repeater feature for these amazing product so we can use our tiks the way we want them.
Re: mDNS repeater feature
+1
While I currently don't need it myself, there are tons of valid use cases for a mDNS repeater. There are multiple ready-to-use open source implementations and required configuration is minimal, this really should be implemented as a feature in ROS.
While I currently don't need it myself, there are tons of valid use cases for a mDNS repeater. There are multiple ready-to-use open source implementations and required configuration is minimal, this really should be implemented as a feature in ROS.
Re: mDNS repeater feature
Just deploy IGMP Proxy correctly:
https://help.mikrotik.com/docs/display/ROS/IGMP+Proxy
Upstream interface will be loopback, “downstream” interface will be the L3 subinterface VLANs that sit on top of the bridge. Enable IGMP Snooping on the bridge, disable multicast querier.
I use it, and mDNS along with other multicast routing based apps works fine inter-VLAN.
https://help.mikrotik.com/docs/display/ROS/IGMP+Proxy
Upstream interface will be loopback, “downstream” interface will be the L3 subinterface VLANs that sit on top of the bridge. Enable IGMP Snooping on the bridge, disable multicast querier.
I use it, and mDNS along with other multicast routing based apps works fine inter-VLAN.
Re: mDNS repeater feature
@DarkNate, interesting, could you share an example of your configuration? igmp-snooping will disable bridge hardware offloading on many low-end devices, multicast-querier must be disabled on the router?
Thanks
Thanks
Re: mDNS repeater feature
I still can achieve 1Gig end-to-end routing performance inter-VLAN on RB450Gx4, hAP ax2 etc. I don't see what's the problem with losing hardware offloading. As long as you use single bridge per switch chip, bridge fast-foward/fast-path will work:igmp-snooping will disable bridge hardware offloading on many low-end devices, multicast-querier must be disabled on the router?
Thanks
https://help.mikrotik.com/docs/display/ ... plebridges
Yes multicast-querier must be disabled.
IMO, mDNS repeater is for lazy bums who refuse to learn PIM-SM and/or IGMP Proxy as evident in this group. Hardly any real network engineering efforts are made.@DarkNate, interesting, could you share an example of your configuration?
Thanks
I appreciate that MikroTik doesn't bend down to lazy-bums' demand for years. One of the few good vendors in that regard.
In my configuration example, I have one router and an L2 switch connected to it for Wi-Fi, keep that in mind:
Code: Select all
#Router side#
/interface bridge
add frame-types=admit-only-vlan-tagged igmp-snooping=yes igmp-version=3 mld-version=2 name=bridge priority=0x1000 vlan-filtering=yes
add arp=disabled name=loopback protocol-mode=none
/interface vlan
add interface=bridge mtu=9214 name="VLAN40" vlan-id=40
add interface=bridge mtu=9214 name="VLAN30" vlan-id=30
/interface bridge port
#This is the trunk port connected to the L2 switch#
add bridge=bridge edge=no frame-types=admit-only-vlan-tagged interface=ether1 point-to-point=yes
add bridge=bridge frame-types=admit-only-untagged-and-priority-tagged interface=ether2 pvid=40
add bridge=bridge frame-types=admit-only-untagged-and-priority-tagged interface=ether3 pvid=40
add bridge=bridge frame-types=admit-only-untagged-and-priority-tagged interface=ether4 pvid=40
add bridge=bridge frame-types=admit-only-untagged-and-priority-tagged interface=ether5 pvid=40
add bridge=bridge frame-types=admit-only-untagged-and-priority-tagged interface=ether6 pvid=40
add bridge=bridge frame-types=admit-only-untagged-and-priority-tagged interface=ether7 pvid=40
add bridge=bridge edge=yes frame-types=admit-only-untagged-and-priority-tagged interface=ether8 point-to-point=yes pvid=30
/interface bridge vlan
add bridge=bridge comment="VLAN40 + MGMT VLAN" tagged=bridge,ether1 vlan-ids=30,40
/ip address
add address=100.64.0.1/24 comment="VLAN40" interface="VLAN40" network=100.64.0.0
add address=30.0.0.0 comment="Loopback" interface=loopback network=10.0.0.0
add address=100.64.2.1/25 comment="VLAN30" interface="VLAN30" network=100.64.2.0
/routing igmp-proxy interface
add interface=loopback upstream=yes
add interface="VLAN40"
add interface="VLAN30"
#On L2 switch side#
/interface bridge
add frame-types=admit-only-vlan-tagged igmp-snooping=yes igmp-version=3 mld-version=2 name=bridge priority=0x2000 vlan-filtering=yes
/interface bridge port
#Ether1 is trunk port connected to router#
add bridge=bridge comment=defconf edge=no frame-types=admit-only-vlan-tagged interface=ether1 point-to-point=yes trusted=yes
add bridge=bridge comment=defconf edge=yes frame-types=admit-only-untagged-and-priority-tagged interface=ether2 pvid=40
add bridge=bridge comment=defconf edge=yes frame-types=admit-only-untagged-and-priority-tagged interface=ether3 pvid=40
add bridge=bridge comment=defconf edge=yes frame-types=admit-only-untagged-and-priority-tagged interface=ether4 pvid=40
add bridge=bridge comment=defconf edge=yes frame-types=admit-only-untagged-and-priority-tagged interface=5GHz_1 pvid=40
add bridge=bridge comment=defconf edge=yes frame-types=admit-only-untagged-and-priority-tagged interface=2GHz_1 pvid=40
add bridge=bridge comment=defconf edge=yes frame-types=admit-only-untagged-and-priority-tagged interface=ether5 pvid=30
/interface bridge vlan
add bridge=bridge tagged=ether1,bridge vlan-ids=30
add bridge=bridge tagged=ether1,bridge vlan-ids=40
Last edited by DarkNate on Mon Mar 27, 2023 10:15 pm, edited 2 times in total.
Re: mDNS repeater feature
That's one way to look at it. But why is MikroTik selling hAP ax lite into the home market? Most home users are not network engineers.IMO, mDNS repeater is for lazy bums who refuse to learn PIM-SM and/or IGMP Proxy as evident in this group. Hardly any real network engineering efforts are made.
I appreciate that MikroTik doesn't bend down to lazy-bums' demand for years. One of the few good vendors in that regard.
Your argument sounds similar to:
IMO, the nano editor is for lazy bums who refuse to learn vi. ...
Re: mDNS repeater feature
MikroTik sells hardware running a single version of RouterOS, the same thing found in ISPs, Telcos and Data Centres. Which vendor other than MikroTik sells an AP like ax lite supporting MPLS over IPv6 out of the box? None.That's one way to look at it. But why is MikroTik selling hAP ax lite into the home market? Most home users are not network engineers.
Your argument sounds similar to:
IMO, the nano editor is for lazy bums who refuse to learn vi. ...
Their target “home users” are power users. Not your grandma or grandpa who can't tell IPv4 from IPv6.
If your “home users” can't configure IGMP Proxy (like my example config or even the official docs), they should stick to TP-Link with OpenWRT.
Re: mDNS repeater feature
Well I'm not sure using OpenWRT is needed either. If you use just one LAN at a home, that solves the problem too.
And if you're are using VLANs, don't put stuff that needs multicast (e.g. mDNS [AirPrint, etc.]) on different subnets, also solve this. Since there are containers that support mDNS, that's an easy out here for Mikrotik when someone wants to do something non-standard. Or want to get more creative? DarkNate's complex world of multicast routing awaits – for those that just got the hang of VLANs...
But even after 50K views, no one has described how it work in practice, beyond "others vendors do it" or "add X package"... e.g. how would Mikrotik even define the needed mDNS "overlay network" in the RouterOS config? I don't think this is a trivial or easy thing to do.
While not a fan of @DarkNate's tone, have to agree I'm glad Mikrotik has NOT "caved in" to mob here. The standards/RFCs advise against repeating mDNS. And unicast DNS-SD is the RFC approved method for "mDNS" accross subnets/segments.
And if you're are using VLANs, don't put stuff that needs multicast (e.g. mDNS [AirPrint, etc.]) on different subnets, also solve this. Since there are containers that support mDNS, that's an easy out here for Mikrotik when someone wants to do something non-standard. Or want to get more creative? DarkNate's complex world of multicast routing awaits – for those that just got the hang of VLANs...
But even after 50K views, no one has described how it work in practice, beyond "others vendors do it" or "add X package"... e.g. how would Mikrotik even define the needed mDNS "overlay network" in the RouterOS config? I don't think this is a trivial or easy thing to do.
While not a fan of @DarkNate's tone, have to agree I'm glad Mikrotik has NOT "caved in" to mob here. The standards/RFCs advise against repeating mDNS. And unicast DNS-SD is the RFC approved method for "mDNS" accross subnets/segments.
Re: mDNS repeater feature
Use IGMP Proxy in simple VLAN segregated home networks and call it a day. iPhone in VLAN1 can talk to iPhone in VLAN2 for AirFuckKnowsWhat, no problem.Well I'm not sure using OpenWRT is needed either. If you use just one LAN at a home, that solves the problem too.
And if you're are using VLANs, don't put stuff that needs multicast (e.g. mDNS [AirPrint, etc.]) on different subnets, also solve this. Since there are containers that support mDNS, that's an easy out here for Mikrotik when someone wants to do something non-standard. Or want to get more creative? DarkNate's complex world of multicast routing awaits – for those that just got the hang of VLANs...
But even after 50K views, no one has described how it work in practice, beyond "others vendors do it" or "add X package"... e.g. how would Mikrotik even define the needed mDNS "overlay network" in the RouterOS config? I don't think this is a trivial or easy thing to do.
While not a fan of @DarkNate's tone, have to agree I'm glad Mikrotik has NOT "caved in" to mob here. The standards/RFCs advise against repeating mDNS. And unicast DNS-SD is the RFC approved method for "mDNS" accross subnets/segments.
Unicast DNS-SD defeats the whole purpose of multicast aka saving computing resources on L2 and L3.
Re: mDNS repeater feature
"Sorry bro" but unicast is way more efficient than multicast. Not saying don't use IGMP or a container to solve mDNS via milticast... but I can totally see why Mikrotik doesn't add this. e.g.
If mDNS proxy is implemented, the RFC is broken because on RFC mDNS must not be forwarded outside local LAN...
Re: mDNS repeater feature
What are you talking about? Multicast is superior for saving resources:"Sorry bro" but unicast is way more efficient than multicast. Not saying don't use IGMP or a container to solve mDNS via milticast... but I can totally see why Mikrotik doesn't add this. e.g.If mDNS proxy is implemented, the RFC is broken because on RFC mDNS must not be forwarded outside local LAN...
https://networkengineering.stackexchange.com/a/19587
https://www.researchgate.net/publicatio ... ing_Method
https://research.ijcaonline.org/volume6 ... 885611.pdf
https://citeseerx.ist.psu.edu/document? ... 48a684cc44
https://cims.nyu.edu/~eyal/papers/ngc.pdf
Why do you need mDNS proxy when IGMP Proxy for inter-VLAN multicast routing works fine, to begin with?
Re: mDNS repeater feature
I'll give that at some small scale multicast may be more efficient – but you can't IGMP proxy a large enterprise/campus/etc network – exactly where it breaks down is harder to predict. And compared to TTL-based caching of unicast DNS-SD results, I'm not sure even at smaller scales... But certainly multicast isn't friendly to Wi-Fi with duplicative mDNS data taking up airtime...Why do you need mDNS proxy when IGMP Proxy for inter-VLAN multicast routing works fine, to begin with?
But I think we're in agreement: Mikrotik shouldn't blindly ignore the RFCs WRT to how mDNS/DNS-SD works by promoting it to a mDNS redirection/reflection/etc into a built-in feature. If you want to expand the scope of all multicast (e.g. not just mDNS), then certainly PIM and IGMP proxy are valid ways to go. As would a container.
Re: mDNS repeater feature
It seems you aren't aware that multicast is used in large scale from stock trading which is nanosecond sensitive to TV networks where multicast serves hundreds of millions of users per second, that unicast simply cannot do without choking a 10G or even 100G link.I'll give that at some small scale multicast may be more efficient – but you can't IGMP proxy a large enterprise/campus/etc network – exactly where it breaks down is harder to predict. And compared to TTL-based caching of unicast DNS-SD results, I'm not sure even at smaller scales... But certainly multicast isn't friendly to Wi-Fi with duplicative mDNS data taking up airtime...
But I think we're in agreement: Mikrotik shouldn't blindly ignore the RFCs WRT to how mDNS/DNS-SD works by promoting it to a mDNS redirection/reflection/etc into a built-in feature. If you want to expand the scope of all multicast (e.g. not just mDNS), then certainly PIM and IGMP proxy are valid ways to go. As would a container.
I suggest you read this thread, where real network engineers who deploy multicast for a living discuss further:
https://twitter.com/danieldibswe/status ... 2540353540
And oh, duplicate multicast packets are eliminated or reduced when IGMP Snooping + IGMP Proxy or PIM is correctly deployed in a network, you can go even further with EVPN like DE-CIX did.
Re: mDNS repeater feature
@DarkNate
You are little bit arrogant, aren't you?
That you are expert in multicast routing does not mean that everyone else must be too. Good for you, but call anyone else lazy-bum?
Not everyone needs to know multicast routing even if they work in IT.
Mikrotik sells wireless APs on consumer market and with "wizard" for simple setup. Do you think that user who buys mikrotik and uses wizard should be able to setup multicast routing and IGMP proxy?
Mikrotik sells to consumers too and configuration should be simple.
And another point. I got briefly over "Multicast DNS" RFC6762 and on several places it counts with "Multicast DNS Proxy Servers" for example as with duplicate answer suppression.
So I do not see anything wrong or proxy/repeater.
Other vendors, even big names have such feature.
So if Mikrotik still plans to sell on consumer market they should consider this functionality. No consumer will do IGMP proxy, multicast etc.
You are little bit arrogant, aren't you?
That you are expert in multicast routing does not mean that everyone else must be too. Good for you, but call anyone else lazy-bum?
Not everyone needs to know multicast routing even if they work in IT.
Mikrotik sells wireless APs on consumer market and with "wizard" for simple setup. Do you think that user who buys mikrotik and uses wizard should be able to setup multicast routing and IGMP proxy?
Mikrotik sells to consumers too and configuration should be simple.
And another point. I got briefly over "Multicast DNS" RFC6762 and on several places it counts with "Multicast DNS Proxy Servers" for example as with duplicate answer suppression.
So I do not see anything wrong or proxy/repeater.
Other vendors, even big names have such feature.
So if Mikrotik still plans to sell on consumer market they should consider this functionality. No consumer will do IGMP proxy, multicast etc.
Re: mDNS repeater feature
I am not a multicast routing expert. But I work with those who are. None of them are in this thread.@DarkNate
You are little bit arrogant, aren't you?
That you are expert in multicast routing does not mean that everyone else must be too. Good for you, but call anyone else lazy-bum?
Not everyone needs to know multicast routing even if they work in IT.
Mikrotik sells wireless APs on consumer market and with "wizard" for simple setup. Do you think that user who buys mikrotik and uses wizard should be able to setup multicast routing and IGMP proxy?
Mikrotik sells to consumers too and configuration should be simple.
And another point. I got briefly over "Multicast DNS" RFC6762 and on several places it counts with "Multicast DNS Proxy Servers" for example as with duplicate answer suppression.
So I do not see anything wrong or proxy/repeater.
Other vendors, even big names have such feature.
So if Mikrotik still plans to sell on consumer market they should consider this functionality. No consumer will do IGMP proxy, multicast etc.
Re: mDNS repeater feature
@DarkNate, appreciated your help, followed suggestions on the previous post but not working, could be my fault.
Tried setting the bridge as upstream and then the VLAN2, printer was not visible on both cases, connected to VLAN1 and worked immediately.
I'm OK with IGMP Proxy, the MT complicated way instead of the more consumer repeater, I worked for a short time on huge CISCO campus network (but I'm not experienced as you), never had any problem printing or sharing contents on Apple devices between VLANs with the "repeater" function.
In my case I'm a low-end user, I can print with my computer using the static IP of the isolated device, using an iPhone is not possible to set the IP. How can you eventually build a network for a client with this missing feature?
Tried setting the bridge as upstream and then the VLAN2, printer was not visible on both cases, connected to VLAN1 and worked immediately.
I'm OK with IGMP Proxy, the MT complicated way instead of the more consumer repeater, I worked for a short time on huge CISCO campus network (but I'm not experienced as you), never had any problem printing or sharing contents on Apple devices between VLANs with the "repeater" function.
In my case I'm a low-end user, I can print with my computer using the static IP of the isolated device, using an iPhone is not possible to set the IP. How can you eventually build a network for a client with this missing feature?
Re: mDNS repeater feature
Why is the bridge upstream? Who told you to do that? I said the loopback needs to be upstream and then the L3 VLANs are separate downstream.@DarkNate, appreciated your help, followed suggestions on the previous post but not working, could be my fault.
Tried setting the bridge as upstream and then the VLAN2, printer was not visible on both cases, connected to VLAN1 and worked immediately.
I'm OK with IGMP Proxy, the MT complicated way instead of the more consumer repeater, I worked for a short time on huge CISCO campus network (but I'm not experienced as you), never had any problem printing or sharing contents on Apple devices between VLANs with the "repeater" function.
In my case I'm a low-end user, I can print with my computer using the static IP of the isolated device, using an iPhone is not possible to set the IP. How can you eventually build a network for a client with this missing feature?
Read it properly:
viewtopic.php?t=174354#p982771
viewtopic.php?t=174354#p982910
Re: mDNS repeater feature
I have mDNS repeating running over a Wireguard link. I had started the process of building this https://github.com/TheMickeyMike/docker ... r-mikrotik but then as the container system only allows one interface and the trick with this container is to feed in VLANs over it so things started to look messy or not possible this way with EoIP. I thought there might be another simpler method with bridge filters.
Wireguard is joining the subnets on L3 and each subnet is routed to the other with no filter rules.
EoIP is joining the bridges at each end using the same Wireguard link - no IPSEC used. The following filters are applied at each end as well to only let mDNS and SSDP (for UPnP) frames through on EoIP.
My iPad and CUPs on my PC can both discover and print to the printer at the other side. The LG Smart TV at the other house with the Photos and Videos App can discover (using SSDP) and play from my MythTV server.
Nothing seemed to work quite right until I reduced the MTU of the Wireguard interface to 1412 bytes as one end is using PPPoE. Also, the neighbour discovery service (dest. MAC FF:FF:FF:FF:FF:FF UDP:5678) seems to be out of the capture reach of the bridge filter so those frames get through. Mitigation would be to make sure that interface in question isn't included in the discovery process.
This method should work fine with VLANs or any other sets of bridge interfaces Mikrotik supports. No mDNS repeater software in containers, rPi's or IGMP snoopers needed; certainly not for small cases like this. I have tested using iPads at each site to discover and print to printers on the other site. So it works.
Here is a quick config I just knocked up on a hAPAC Lite to illustrate mDNS relaying between VLANs using bridge filtering and no IGMP snooping. IPv4 only.
* To be clear this mDNS relay config only relays mDNS traffic. It does not proxy any other data or do any IGMP or other multcast tasks.
* VLAN filtering is enabled using BridgeMain. Tagged VLANs 100 and 200 go to it for the VLANs interface to access.
* eth2 has PVID100, eth3 has PVID200.
* BridgeVLANs is the bridge that will straddle the 2 VLANs. It has the VLAN100 and VLAN200 ports attached as members. If left unfiltered all layer 2 broadcast traffic on both VLANs will pass between them.
* The bridge filter setup operates on each VLAN port only allowing mDNS to pass each way and blocking all other layer 2 traffic.
* Any actual data traffic that clients or servers use on either VLAN using addresses learned in the mDNS packets will pass via the routes on layer 3. You'll need add firewall rules to limit the traffic interaction but is out of the scope of this example.
* I would imagine this would work just fine on a CRS3xx switch as well but you might as well use the rolled gold standard of IGMP snooping.
Wireguard is joining the subnets on L3 and each subnet is routed to the other with no filter rules.
EoIP is joining the bridges at each end using the same Wireguard link - no IPSEC used. The following filters are applied at each end as well to only let mDNS and SSDP (for UPnP) frames through on EoIP.
Code: Select all
/interface bridge filter
add action=accept chain=forward dst-address=224.0.0.251/32 dst-mac-address=\
01:00:5E:00:00:FB/FF:FF:FF:FF:FF:FF dst-port=5353 ip-protocol=udp \
mac-protocol=ip out-interface=EoIP src-port=5353 comment=mDNS
add action=accept chain=forward comment=SSDP dst-address=239.255.255.250/32 \
dst-mac-address=01:00:5E:7F:FF:FA/FF:FF:FF:FF:FF:FF dst-port=1900 \
ip-protocol=udp log-prefix=SSDP mac-protocol=ip out-interface=EoIP
add action=drop chain=output out-interface=EoIP
add action=drop chain=forward out-interface=EoIPMy iPad and CUPs on my PC can both discover and print to the printer at the other side. The LG Smart TV at the other house with the Photos and Videos App can discover (using SSDP) and play from my MythTV server.
Nothing seemed to work quite right until I reduced the MTU of the Wireguard interface to 1412 bytes as one end is using PPPoE. Also, the neighbour discovery service (dest. MAC FF:FF:FF:FF:FF:FF UDP:5678) seems to be out of the capture reach of the bridge filter so those frames get through. Mitigation would be to make sure that interface in question isn't included in the discovery process.
This method should work fine with VLANs or any other sets of bridge interfaces Mikrotik supports. No mDNS repeater software in containers, rPi's or IGMP snoopers needed; certainly not for small cases like this. I have tested using iPads at each site to discover and print to printers on the other site. So it works.
Here is a quick config I just knocked up on a hAPAC Lite to illustrate mDNS relaying between VLANs using bridge filtering and no IGMP snooping. IPv4 only.
* To be clear this mDNS relay config only relays mDNS traffic. It does not proxy any other data or do any IGMP or other multcast tasks.
* VLAN filtering is enabled using BridgeMain. Tagged VLANs 100 and 200 go to it for the VLANs interface to access.
* eth2 has PVID100, eth3 has PVID200.
* BridgeVLANs is the bridge that will straddle the 2 VLANs. It has the VLAN100 and VLAN200 ports attached as members. If left unfiltered all layer 2 broadcast traffic on both VLANs will pass between them.
* The bridge filter setup operates on each VLAN port only allowing mDNS to pass each way and blocking all other layer 2 traffic.
* Any actual data traffic that clients or servers use on either VLAN using addresses learned in the mDNS packets will pass via the routes on layer 3. You'll need add firewall rules to limit the traffic interaction but is out of the scope of this example.
* I would imagine this would work just fine on a CRS3xx switch as well but you might as well use the rolled gold standard of IGMP snooping.
Code: Select all
/interface bridge
add comment="Main Bridge VLAN filtering runs on" frame-types=admit-only-vlan-tagged name=BridgeMain protocol-mode=none pvid=999 vlan-filtering=yes
add comment="Bridge for linking VLANs with filtering" name=BridgeVLANs protocol-mode=none
/interface ethernet
set [ find default-name=ether2 ] comment="Eth PVID100"
set [ find default-name=ether3 ] comment="Eth PVID200"
/interface vlan
add comment="VLAN100 on main bridge" interface=BridgeMain name=VLAN100 vlan-id=100
add comment="VLAN200 on main bridge" interface=BridgeMain name=VLAN200 vlan-id=200
/interface bridge filter
add action=accept chain=forward comment="Allow VLAN100 mDNS traffic out" dst-address=224.0.0.251/32 dst-mac-address=\
01:00:5E:00:00:FB/FF:FF:FF:FF:FF:FF dst-port=5353 out-interface=VLAN100 ip-protocol=udp mac-protocol=ip src-port=5353
add action=accept chain=forward comment="Allow VLAN200 mDNS traffic out" dst-address=224.0.0.251/32 dst-mac-address=\
01:00:5E:00:00:FB/FF:FF:FF:FF:FF:FF dst-port=5353 out-interface=VLAN200 ip-protocol=udp mac-protocol=ip src-port=5353
add action=drop chain=forward comment="VLAN100 drop all other forwarding" out-interface=VLAN100
add action=drop chain=output comment="VLAN100 drop all output" out-interface=VLAN100
add action=drop chain=forward comment="VLAN200 drop all other forwarding" out-interface=VLAN200
add action=drop chain=output comment="VLAN200 drop all output" out-interface=VLAN200
/interface bridge port
add bridge=BridgeVLANs comment="VLAN100 Port" interface=VLAN100
add bridge=BridgeVLANs comment="VLAN200 port" interface=VLAN200
add bridge=BridgeMain comment="Eth PVID100" frame-types=admit-only-untagged-and-priority-tagged interface=ether2 pvid=100
add bridge=BridgeMain comment="Eth PVID200" frame-types=admit-only-untagged-and-priority-tagged interface=ether3 pvid=200
/interface bridge settings
set use-ip-firewall=yes use-ip-firewall-for-vlan=yes
/interface bridge vlan
add bridge=BridgeMain comment="VLAN100 port definitions" tagged=BridgeMain vlan-ids=100
add bridge=BridgeMain comment="VLAN200 port definitions" tagged=BridgeMain vlan-ids=200
/ip address
add address=172.16.200.254/24 comment="VLAN200 interface address" interface=VLAN200 network=172.16.200.0
add address=172.16.100.254/24 comment="VLAN100 interface address" interface=VLAN100 network=172.16.100.0
Re: mDNS repeater feature
I attempted to run mDSN discovery over wireguard but at two DIFFERENT LOCATIONs..........
Feel free to test it, to make sure it works..............academic at this point.
viewtopic.php?p=990840#p990840
Feel free to test it, to make sure it works..............academic at this point.
viewtopic.php?p=990840#p990840
Re: mDNS repeater feature
Darknate is correct but let me add context.Just deploy IGMP Proxy correctly:
https://help.mikrotik.com/docs/display/ROS/IGMP+Proxy
mDNS as a standard is not meant to be reflected or repeated. Avahi is an implementation of the zeroconf standard that added mDNS reflection as a practical solution for those of us who have chosen to segment our networks due to concerns about the number of IoT devices from various vendors on our networks.
That being, neither IGMP Proxy nor mDNS reflection with Avahi is "correct". They're both "as bad as each other" in regards to the mDNS RFC. Pick one, make it work, and knock yourself out.
Mikrotik *could* add an mDNS reflector into ROS, just like they have added UPnP. However, it's not a network standard and that - to me - is why they have never done it. Currently I run an avahi daemon on a Raspberry Pi as I have segmented my network. I'll take a look at using an IGMP proxy but I'm more likely to use the mDNS reflector container on my RB5009.
Re: mDNS repeater feature
IGMP Proxy is closest to an internet standard than mDNS reflector/Avahi bullshit is. IGMP Proxy also handles stuff unrelated to mDNS, therefore allow ALL multicast traffic to work correctly across VLANs.That being, neither IGMP Proxy nor mDNS reflection with Avahi is "correct". They're both "as bad as each other" in regards to the mDNS RFC. Pick one, make it work, and knock yourself out.
https://www.rfc-editor.org/rfc/rfc4605
IGMP Proxy is so “standardized” that even Cisco supports it:
https://www.cisco.com/c/en/us/td/docs/s ... _proxy.pdf
Re: mDNS repeater feature
@Kaldek
> "mDNS as a standard is not meant to be reflected or repeated. ..."
If you check RFC for mDNS, you will see it counts with reflection, gateways even if it itself does not define proxying.
> "Mikrotik *could* add an mDNS reflector into ROS, just like they have added UPnP. However, it's not a network standard and that - to me - is why they have never done it. "
Just guessing, we do not have any word from Mikrotik.
@DarkNate
The more you fight against mDNS reflector/proxy the more it is ridiculous.
Maybe time to accept that this is valid feature request and many other vendors offer such feature, even Cisco. For example:
https://www.cisco.com/c/dam/en/us/td/do ... l-17-3.pdf
The IGMP proxy in theory could be more generic solution. But it is proxy and in fact will do the same as mDNS proxy if it works.
So takes mDNS packet from one subnet and puts it to another.
And if I got it right, then for IGMP proxy to work the devices has to use IGMP protocol and join to mDNS group so proxy can forward the mDNS packets.
But majority of IoT devices does not do that, just send mDNS packets.
For regular users/SMB the mDNS reflector/proxy (or call it as you want) should be part of ROS. No docker, no RPi etc. This is not for regular users and not easy to set up.
If I will recommend someone to buy Mikrotik and tell him that for mDNS he needs RPi to get it work and maintain, then there is no go.
Anyway other vendors do this (even Cisco) so it is just Mikrotik's decision.
> "mDNS as a standard is not meant to be reflected or repeated. ..."
If you check RFC for mDNS, you will see it counts with reflection, gateways even if it itself does not define proxying.
> "Mikrotik *could* add an mDNS reflector into ROS, just like they have added UPnP. However, it's not a network standard and that - to me - is why they have never done it. "
Just guessing, we do not have any word from Mikrotik.
@DarkNate
The more you fight against mDNS reflector/proxy the more it is ridiculous.
Maybe time to accept that this is valid feature request and many other vendors offer such feature, even Cisco. For example:
https://www.cisco.com/c/dam/en/us/td/do ... l-17-3.pdf
The IGMP proxy in theory could be more generic solution. But it is proxy and in fact will do the same as mDNS proxy if it works.
So takes mDNS packet from one subnet and puts it to another.
And if I got it right, then for IGMP proxy to work the devices has to use IGMP protocol and join to mDNS group so proxy can forward the mDNS packets.
But majority of IoT devices does not do that, just send mDNS packets.
For regular users/SMB the mDNS reflector/proxy (or call it as you want) should be part of ROS. No docker, no RPi etc. This is not for regular users and not easy to set up.
If I will recommend someone to buy Mikrotik and tell him that for mDNS he needs RPi to get it work and maintain, then there is no go.
Anyway other vendors do this (even Cisco) so it is just Mikrotik's decision.
Re: mDNS repeater feature
You've clearly never tested and configured IGMP Proxy correctly. If you did, you'd know it's only two-three lines of config to get it working:
viewtopic.php?t=174354#p982910
Like I said, it will handle all multicast/IGMP traffic.
viewtopic.php?t=174354#p982910
Like I said, it will handle all multicast/IGMP traffic.
Re: mDNS repeater feature
The more you fight against mDNS reflector/proxy the more it is ridiculous.
This is not for regular users and not easy to set up.
Not the only one disagree with this being promoted to a feature. "Regular users" don't have multiple LAN subnets, so how does this even come up in that case...
If you check RFC for mDNS, you will see it counts with reflection, gateways even if it itself does not define proxying.
Wrong. 239.0.0.0/8 are defined to be per interface in RFC2365, so there no need to look at mDNS RFCs.
And any reading of the mDNS/DNS-SD RFC series concludes with converting mDNS (multicast) into DNS-SD (unicast) at interface/subnet boundaries is the "proper" approach. How? In the standards, vendors offered a variety of approaches to do that like discovery proxy, dnsextd, etc.. But ignoring RFC2365 isn't one.
Anyway other vendors do this (even Cisco) so it is just Mikrotik's decision.
Why Mikrotik doesn't.... they've said the use cases don't make sense in the above. They never said anything about the rigorous standard compliance as the reasoning. I'd like to think so, perhaps @DarkNate too, but that's not what they said.
If you've gone done the road of subnetting your LAN, IGMP Proxy should not be a huge leap. And if it was, maybe you should re-think segmenting your network in the first place?
Re: mDNS repeater feature
VLANs + mDNS containers hacks takes like 10 minutes total for a noob.If you've gone done the road of subnetting your LAN, IGMP Proxy should not be a huge leap. And if it was, maybe you should re-think segmenting your network in the first place?
IGMP Proxy, takes 5 seconds to configure for all VLANs.
Not sure why these experts keep demanding MikroTik for mDNS repeater crap.
@MikroTik should continue as they are and never succumb to idiotic requests.
For the record, IoT devices work perfectly fine with IGMP Proxy in home use cases.
In production, we use PIM not IGMP Proxy or mDNS bs.
Re: mDNS repeater feature
Let's see if this second attempt will be the good one...it's only two-three lines of config to get it working:
viewtopic.php?t=174354#p982910
Code: Select all
/interface bridge add frame-types=admit-only-vlan-tagged igmp-snooping=yes igmp-version=3 mld-version=2 name=Bridge protocol-mode=mstp vlan-filtering=yes
/ip address add address=192.168.10.1/24 interface=LAN network=192.168.10.0
/ip address add address=192.168.20.1/26 interface=IoT network=192.168.20.0
/ip address add address=192.168.30.1/28 interface=NAS network=192.168.30.0
/routing igmp-proxy interface add alternative-subnets=192.168.20.1/26,192.168.30.1/28 interface=LAN upstream=yes
/routing igmp-proxy interface add interface=IoT
/routing igmp-proxy interface add interface=NAS
Re: mDNS repeater feature
Why do you keep insisting on doing the complete opposite of my config example here?Let's see if this second attempt will be the good one
Code: Select all/interface bridge add frame-types=admit-only-vlan-tagged igmp-snooping=yes igmp-version=3 mld-version=2 name=Bridge protocol-mode=mstp vlan-filtering=yes /ip address add address=192.168.10.1/24 interface=LAN network=192.168.10.0 /ip address add address=192.168.20.1/26 interface=IoT network=192.168.20.0 /ip address add address=192.168.30.1/28 interface=NAS network=192.168.30.0 /routing igmp-proxy interface add alternative-subnets=192.168.20.1/26,192.168.30.1/28 interface=LAN upstream=yes /routing igmp-proxy interface add interface=IoT /routing igmp-proxy interface add interface=NAS
viewtopic.php?t=174354#p982910
Why do you keep avoiding a loopback interface? Even though I provided the full configuration, you still actively decide to do it the wrong way, before and even now.
viewtopic.php?t=174354#p985159
What is the reason for your fear of loopback interface to correctly set the upstream interface?
Re: mDNS repeater feature
Wrong argument. The same you could say about IGMP proxy - so no need to look for IGMP RFCs.Wrong. 239.0.0.0/8 are defined to be per interface in RFC2365, so there no need to look at mDNS RFCs.
There are many other vendors (with Cisco too) providing such feature at some level. It maybe called differently, but do the same.
So at the end it is Mikrotik's pure business decision if they implement the same what other vendors already have.
Maybe time to stop denying reality and pretend it is something awful and accept this legitimate feature request already provided by other vendors.
Re: mDNS repeater feature
Wrong argument. The same you could say about IGMP proxy - so no need to look for IGMP RFCs.Wrong. 239.0.0.0/8 are defined to be per interface in RFC2365, so there no need to look at mDNS RFCs.
Yes. All that RFC means is that the packets in that IP range don't automatically flow from one network to another. When helped across via PIM or a proxy, that's a local administration matter, not subject to RFC restriction. There are no Internet cops gonna come running because you did this.
Re: mDNS repeater feature
Doesn't work. Used your specific example, including adding ipv6 GUA on the loopback, still no packets traverse the IGMP ProxyUse IGMP Proxy in simple VLAN segregated home networks and call it a day. iPhone in VLAN1 can talk to iPhone in VLAN2 for AirFuckKnowsWhat, no problem.
Unicast DNS-SD defeats the whole purpose of multicast aka saving computing resources on L2 and L3.
Re: mDNS repeater feature
without "idiotic" requests, you wouldn't have an easy to use interface like winbox.VLANs + mDNS containers hacks takes like 10 minutes total for a noob.If you've gone done the road of subnetting your LAN, IGMP Proxy should not be a huge leap. And if it was, maybe you should re-think segmenting your network in the first place?
IGMP Proxy, takes 5 seconds to configure for all VLANs.
Not sure why these experts keep demanding MikroTik for mDNS repeater crap.
@MikroTik should continue as they are and never succumb to idiotic requests.
For the record, IoT devices work perfectly fine with IGMP Proxy in home use cases.
In production, we use PIM not IGMP Proxy or mDNS bs.
without "idiotic" requests, you wouldn't have the ability to schedule things.
without "idiotic" requests, you wouldn't have the ability to use Zerotier with Tik.
without "idiotic" requests, you wouldn't have the ability to use containers on v7.
without "idiotic" requests, you wouldn't have the ability to use ROMON.
You don't need to be toxic to be helpful.
I've tested your solution for IGMP Proxy, and that doesn't work for mdns. No packets traverse the proxy. If I set the loopback as the upstream... 0 packets recieved / transmitted on either of the 3 interfaces.
If I set the vlan10 as the upstream, RX packets are seen on that interface, but not anywhere else.
Re: mDNS repeater feature
You didn't correctly configure it, and you are even hiding the config from the public in this forum just to make my solution look bad. And you need to be extra stupid to set a VLAN interface as upstream, unless a single multicast server like IPTV is running behind VLAN10.I've tested your solution for IGMP Proxy, and that doesn't work for mdns. No packets traverse the proxy. If I set the loopback as the upstream... 0 packets recieved / transmitted on either of the 3 interfaces.
If I set the vlan10 as the upstream, RX packets are seen on that interface, but not anywhere else.
Where is your config export?
0 packets received/transmitted is a bug in RouterOS, you being the expert that you are can confirm with official MikroTik support staff, they'll tell you to ignore packet count in IGMP Proxy. The proper way to verify IGMP Snooping + IGMP Proxy is working correctly is by printing the MDB table:
Code: Select all
interface bridge mdb printRe: mDNS repeater feature
As already explained, since you're expert I suggest you talk to official MikroTik support, packet count will be zero in IGMP Proxy when it is working correctly. Why? Ask them, you're the expert in this conversation clearly.Doesn't work. Used your specific example, including adding ipv6 GUA on the loopback, still no packets traverse the IGMP Proxy
Re: mDNS repeater feature
IGMP Proxy, takes 5 seconds to configure for all VLANs.
For the record, IoT devices work perfectly fine with IGMP Proxy in home use cases.
I'm interested into how this IGMP proxy works because it might fix my issue hopefully.
I have a server which runs on a subnet (192.168.3.0/24) and other devices on another one (10.10.10.0/24). No VLANs, just two subnets set up on two bridges.
I installed jellyfin on the server, and it happens now that a client (my smart TV) is on the subnet 10.10.10.0/24 and it should get access to the jellyfin app running on the server and its contents via DLNA I guess. I had already set a few firewall rules on my MK device to allow a couple of devices on 10.10.10.0/24 to acces my server, like my tv, and my laptop when I'm on the other subnet. They works. However, I didn't manage to make my tv see jellyfin contents on the server, I thought that IGMP or mDNS might have something to do with it.
I'm not a computer networking expert so I am aware that I might have said something stupid.
Could you help me figure it out?
Thanks
Re: mDNS repeater feature
All proposed solutions are for L2, but what if you have VPN connection between router and user device (smartphone, laptop...)?
mDNS repeater in container is also not an option since system in container can only get veth and tagged interfaces on its bridge, but l3 tunnel interfaces (wireguard, ovpn) cannot be bridged and tagged.
Only what I can see that can solve this is with mDNS repeater/reflector as ROS additional package which can be configured to select ROS interfaces to reflect mDNS between them. Something like: https://docs.paloaltonetworks.com/pan-o ... gmentation
Since Mikrotik is selling products for home users, it should be fair to cover needs for such consumers, even if some advanced skills are needed for configuration, but at least to be possible.
mDNS repeater in container is also not an option since system in container can only get veth and tagged interfaces on its bridge, but l3 tunnel interfaces (wireguard, ovpn) cannot be bridged and tagged.
Only what I can see that can solve this is with mDNS repeater/reflector as ROS additional package which can be configured to select ROS interfaces to reflect mDNS between them. Something like: https://docs.paloaltonetworks.com/pan-o ... gmentation
Since Mikrotik is selling products for home users, it should be fair to cover needs for such consumers, even if some advanced skills are needed for configuration, but at least to be possible.
Re: mDNS repeater feature
For posters here........... Do not mind Darknate's lack of personal communication skills (probably why he has more dates with large networks than real people  ) and of course the rampant narcissism.
) and of course the rampant narcissism.
He has a lot of experience with many large networks that is invaluable to other large network users!
How that translates to smaller home or SOHO setups is not always clear or necessarily possible.
Very pragmatic 'to the point' advice, (and expect some pushback if you keep ignoring the advice provided or keep applying it wrong after repeated attempts/time to help)
He has a lot of experience with many large networks that is invaluable to other large network users!
How that translates to smaller home or SOHO setups is not always clear or necessarily possible.
Very pragmatic 'to the point' advice, (and expect some pushback if you keep ignoring the advice provided or keep applying it wrong after repeated attempts/time to help)
Re: mDNS repeater feature
The guy is the toxic avenger. He may have some experience, but how he has been allowed to touch big networks with such a bad attitude is just horrible. These forums (and other places) are meant to help people with Mikrotik, not belittle others. I never claimed to be an expert, yet he starts with nasty attitude with everyone. Calling everyone lazy for wanting a convenience feature is such a bad attitude.For posters here........... Do not mind Darknate's lack of personal communication skills (probably why he has more dates with large networks than real people) and of course the rampant narcissism.
He has a lot of experience with many large networks that is invaluable to other large network users!
How that translates to smaller home or SOHO setups is not always clear or necessarily possible.
Very pragmatic 'to the point' advice, (and expect some pushback if you keep ignoring the advice provided or keep applying it wrong after repeated attempts/time to help)
He then goes on to say 'contact support'. There is virtually no support for anyone that doesn't have a contact at Mikrotik. Forums and other venues like reddit and my discord are one of the very few places people can get help on MIkrotik topics.
Re: mDNS repeater feature
why would someone need to have that? worse, why even relay such network noise?Ever home user needs mDNS. Don't know why mikrotik keeps ignoring this.even the edgerouter has a mdns repeater..
Re: mDNS repeater feature
That's the existential question here. Butwhy would someone need to have that? worse, why even relay such network noise?
And... it sounds like this could be resolved by better docs on IGMP Proxy for those that want to go this route. An example there would go a long way.[...] at the end it is Mikrotik's pure business decision [...]
But specific the troubles in making IGMP working may involve the firewall. Both the multicast discovery and the resulting unicast traffic once a device was discovered need to be allowed. If you block inter-VLAN forwarding, the IGMP proxy follows those rules too.
Re: mDNS repeater feature
If you know solution without mDNS repeater on ROS for case in my previous post I will be glad to try it. Case is that VPN is L3 tunnel between devices because client device (iOS) doesn't allow sandboxed VPN apps to create interfaces which can handle L2.why would someone need to have that? worse, why even relay such network noise?
Re: mDNS repeater feature
Maybe para 5 ( which at the bottom has a link to another solution ). - viewtopic.php?t=194646
Re: mDNS repeater feature
This solution is:Maybe para 5 ( which at the bottom has a link to another solution ). - viewtopic.php?t=194646
[ros]<---WAN(WG(EOIP/L2)/L3)--->[ros]<---(V)LAN--->[device]
EOIP is encapsulated, and can be handled on other side, in my case it can't:
[ros]<---WAN(WG/L3)--->[device]
I'm I right?
Re: mDNS repeater feature
IOT. This category of devices is now more prolific than every before. In homes, smb, and enterprises. We’re looking for tools to allow us to segregate these devices, yet interact the way that is convenient to those that are paying IT/Network support/engineers.why would someone need to have that? worse, why even relay such network noise?
Ever home user needs mDNS. Don't know why mikrotik keeps ignoring this.
With how much iPhone , bonjour, AirPlay,, chromecast has been made the norm, sometimes it’s not always possible to say ‘no’.
Re: mDNS repeater feature
Exactly. Give us a working example to get chromecast/airplay working using the IGMP Proxy and all of this noise goes away.That's the existential question here. Butwhy would someone need to have that? worse, why even relay such network noise?And... it sounds like this could be resolved by better docs on IGMP Proxy for those that want to go this route. An example there would go a long way.[...] at the end it is Mikrotik's pure business decision [...]
But specific the troubles in making IGMP working may involve the firewall. Both the multicast discovery and the resulting unicast traffic once a device was discovered need to be allowed. If you block inter-VLAN forwarding, the IGMP proxy follows those rules too.
Re: mDNS repeater feature
The fact is another, the problem is the absolute trust that is given to smartphones and computers,
which are seen as ultra-secure and without any espionage problems...
Instead the "IoT", which are products that come from exactly the same manufacturers, just from another brand, are the devil.
Well, it is precisely this blindness that causes most of the problems...
Don't want your Samsung TV (for example) to "see" your Samsung smartphone? What do you care for? Both devices are already full of Samsung spionage...
This situation is borderline comical, in own home separate the network because otherwise WHAT?
And I'm not talking about the "guest" who wants to print on our printer, since the latest printers already does it on their own without even using the Internet or home wlan...
All this effort for NOTHING. That's what the truth is for me.
I repeat, for me, then being an opinion, it is not said that it is an absolute truth that, only a few Than here on the forum Oven's truth,
it's like religious people, you're just an idiot, only they (religious people) know the truth and we can't tell it, we wouldn't understand it, we are inept...
which are seen as ultra-secure and without any espionage problems...
Instead the "IoT", which are products that come from exactly the same manufacturers, just from another brand, are the devil.
Well, it is precisely this blindness that causes most of the problems...
Don't want your Samsung TV (for example) to "see" your Samsung smartphone? What do you care for? Both devices are already full of Samsung spionage...
This situation is borderline comical, in own home separate the network because otherwise WHAT?
And I'm not talking about the "guest" who wants to print on our printer, since the latest printers already does it on their own without even using the Internet or home wlan...
All this effort for NOTHING. That's what the truth is for me.
I repeat, for me, then being an opinion, it is not said that it is an absolute truth that, only a few Than here on the forum Oven's truth,
it's like religious people, you're just an idiot, only they (religious people) know the truth and we can't tell it, we wouldn't understand it, we are inept...
Last edited by rextended on Sun Mar 26, 2023 6:03 pm, edited 5 times in total.
Re: mDNS repeater feature
I liked this quote from Mikrotik:
But...
If IGMP Proxy isn't working, Mikrotik has /tool/torch that might help with what's going on. See https://www.youtube.com/watch?v=45E2uwI3xhc and 224.0.0.251 as the dst-address and/or port 5353 to find mDNS (and you might want to change time out to 1:00 from 00:03).
Also, if one wanted limit IGMP proxy to limit to just mDNS etc. this should work
But didn't setup/test – I think rebroadcasting mDNS across subnets is a bad idea – but this would at least limit the scope of the IGMP proxy.
Also @DarkNate recommends a loopback, but the upstream could be the VLAN where you your doing the browsing from ("main"/base/mgmt/etc) and the "IoT VLANs" point to that "main VLAN" and that might be more friendly to the default firewall than adding a loopback bridge.
By the looks of it, L2 segregation for the mentioned above cases is an illusion of safety.
But...
So you want to cut-and-paste without understanding what it does? If you can't troubleshoot it, you shouldn't use it.Exactly. Give us a working example to get chromecast/airplay working using the IGMP Proxy and all of this noise goes away.
If IGMP Proxy isn't working, Mikrotik has /tool/torch that might help with what's going on. See https://www.youtube.com/watch?v=45E2uwI3xhc and 224.0.0.251 as the dst-address and/or port 5353 to find mDNS (and you might want to change time out to 1:00 from 00:03).
Also, if one wanted limit IGMP proxy to limit to just mDNS etc. this should work
Code: Select all
/interface bridge filter
add action=accept chain=forward comment="Allow mDNS" dst-address=224.0.0.251/32 mac-protocol=ip
add action=drop chain=forward comment="Drop all other multicast" dst-address=224.0.0.0/4 mac-protocol=ip
Also @DarkNate recommends a loopback, but the upstream could be the VLAN where you your doing the browsing from ("main"/base/mgmt/etc) and the "IoT VLANs" point to that "main VLAN" and that might be more friendly to the default firewall than adding a loopback bridge.
Re: mDNS repeater feature
If the device A is connecting to deivce B because see "mDSN", what stop other devices or service to do the same without notification?
If something can be leaked between the two networks....
Is not needed to be a Reliability Engineer to understand that...
If something can be leaked between the two networks....
Is not needed to be a Reliability Engineer to understand that...
Re: mDNS repeater feature
And if you want smartphone to see Samsung TV from WAN?Don't want your Samsung TV (for example) to "see" your Samsung smartphone? What do you care for? Both devices are already full of Samsung spionage...
Case, you are not at home and you want to collaborate/show something from smartphone/tablet screen to someone at home on TV over AirPlay/Chromecast? Using VPN to home router and mDNS discovery for such service is only what I think is possible here. iOS even doesn't allow apps to read screen buffer when it is not in foreground so only AirPlay system service can be used in this case (screen mirror), that's why collaboration/messenger apps on iOS doesn't have share screen feature because it will be useless.
Re: mDNS repeater feature
Are you really asking how to make a VPN that puts the remote device in the same L2 domain?
On that case the problem is not "mDNS or not", it's another one...
As in post #2 I would like to see how many people start doing this remotely...
Send the video via whatsapp, anyway the video must be transferred... and the person at home sees it on TV or smartphone as they like...
On that case the problem is not "mDNS or not", it's another one...
As in post #2 I would like to see how many people start doing this remotely...
Send the video via whatsapp, anyway the video must be transferred... and the person at home sees it on TV or smartphone as they like...
Last edited by rextended on Sun Mar 26, 2023 6:36 pm, edited 1 time in total.
Re: mDNS repeater feature
Yes, WG or OpenVPN (tun)Are you really asking how to make a VPN that puts the remote device in the same L2 domain?
On that case the problem is not "mDSN or not", it's another one...
Yeah, but this is not exact real time, and it involves additional actions while working, It is more convenient to have screen mirror...Send the video via whatsapp, anyway the video must be transferred... and the person at home sees it on TV or smartphone as they like...
Last edited by optio on Sun Mar 26, 2023 6:38 pm, edited 1 time in total.
Re: mDNS repeater feature
@anav already do that... (if I do not have rad bad...) search his topic...
(see here post #202)
This is the link:
viewtopic.php?p=990834#p990840
But please remain ontopic, for mDNS.
(see here post #202)
This is the link:
viewtopic.php?p=990834#p990840
But please remain ontopic, for mDNS.
Re: mDNS repeater feature
Working or at home?[…] involves additional actions while working […]
If you are working exist thousand of methoids to link two office on L2, if is just your vacation video, you can have a videocall during the proiection of already sended video...
Re: mDNS repeater feature
I did replied to him regarding that. viewtopic.php?p=992311#p992285@anav already do that... (if I do not have rad bad...) search his topic...
This solution doesn't work in my case if I'm understanded right.
Well this is in scope of mDNS discovery (AirPlay/Chromecast).But please remain ontopic, for mDNS.
Re: mDNS repeater feature
Working at any location...Working or at home?
No physical office exists in my case, home is only static physical location with ROS... Someone one can be at home and I want to share screen to that someone from any location.If you are working exist thousand of methoids to link two office on L2, if is just your vacation video, you can have a videocall during the proiection of already sended video...
Re: mDNS repeater feature
Send mDNS over WAN? (can happen...)
I think you solve with IPsec and L2TP on your case (or also by other VPN), but this is offtopic.
The intention of the main argument is to have mDNS to unnecessarily divide the home LAN into multiple VLANs,
and then allow the various devices to see each other as if they are in the same LAN/VLAN...
I think you solve with IPsec and L2TP on your case (or also by other VPN), but this is offtopic.
The intention of the main argument is to have mDNS to unnecessarily divide the home LAN into multiple VLANs,
and then allow the various devices to see each other as if they are in the same LAN/VLAN...
Last edited by rextended on Sun Mar 26, 2023 6:55 pm, edited 1 time in total.
Re: mDNS repeater feature
It's like ChatGPT, you can ask "why?" and you'll get some answer.
I think folks discount that once mDNS allows discovery the inter-VLAN unicast traffic still needs to be allowed by the firewall AFTER it's been discovered. Which in @pcunite-style VLAN config, it wouldn't. Which is why everyone goes "I want to keep things seperate!!!" does get silly since the firewall would have to allow the unicast traffic between VLAN anyway. Accomplishing what?
I'm all for DNS-SD support in /ip/dns - since I'd like avoid need mDNS entirely if /ip/dns supported DNS-SD, it be possible. And this work with WG since DNS-SD is unicast without the need for bridging.
But this avahi-style repeating/rebroadcasting feature is dated approach & crazy for RouterOS. If you want that functionality, then all it takes is figuring out IGMP Proxy (and likely bridge filtering and/or firewall rules).
And bridging WG is different than the "use cases" discussed here – seemingly "I want mDNS discovery spanning multiple VLANs on the same router"
I think folks discount that once mDNS allows discovery the inter-VLAN unicast traffic still needs to be allowed by the firewall AFTER it's been discovered. Which in @pcunite-style VLAN config, it wouldn't. Which is why everyone goes "I want to keep things seperate!!!" does get silly since the firewall would have to allow the unicast traffic between VLAN anyway. Accomplishing what?
I'm all for DNS-SD support in /ip/dns - since I'd like avoid need mDNS entirely if /ip/dns supported DNS-SD, it be possible. And this work with WG since DNS-SD is unicast without the need for bridging.
But this avahi-style repeating/rebroadcasting feature is dated approach & crazy for RouterOS. If you want that functionality, then all it takes is figuring out IGMP Proxy (and likely bridge filtering and/or firewall rules).
And bridging WG is different than the "use cases" discussed here – seemingly "I want mDNS discovery spanning multiple VLANs on the same router"
Re: mDNS repeater feature
Ok, I was seeking solutions for WG or tun ovpn.Send mDNS over WAN? (can happen...)
I think you solve with IPsec and L2TP on your case (or also by other VPN), but this is offtopic.
Actually OP is "Please bring mDNS repeater feature in Rosv7. It is a very important feature for home routers.", network topology is not specified.The intention of the main argument is to have mDNS to unnecessarily divide the home LAN into multiple VLANs,
and then allow the various devices to see each other as if they are in the same LAN/VLAN...
But ok I will drop this here since there is no exact solutions for wg/ovpn l3 peers.
Re: mDNS repeater feature
Yes, understand, he integrate it's need, and why, on successive post:Actually OP is "Please bring mDNS repeater feature in Rosv7. It is a very important feature for home routers.", network topology is not specified.
viewtopic.php?t=174354#p866278
I specify, however, that I am neither for, nor against the request.
I am against things made without sense, dividing everything and then having the needs to leave the devices communicate with each other again...
In a certain sense, what you asked for, even if it is resolved in another way, seems to me much more logical and useful....
Re: mDNS repeater feature
Security is done in layers.I liked this quote from Mikrotik:By the looks of it, L2 segregation for the mentioned above cases is an illusion of safety.
But...So you want to cut-and-paste without understanding what it does? If you can't troubleshoot it, you shouldn't use it.Exactly. Give us a working example to get chromecast/airplay working using the IGMP Proxy and all of this noise goes away.
If IGMP Proxy isn't working, Mikrotik has /tool/torch that might help with what's going on. See https://www.youtube.com/watch?v=45E2uwI3xhc and 224.0.0.251 as the dst-address and/or port 5353 to find mDNS (and you might want to change time out to 1:00 from 00:03).
Also, if one wanted limit IGMP proxy to limit to just mDNS etc. this should work
But didn't setup/test – I think rebroadcasting mDNS across subnets is a bad idea – but this would at least limit the scope of the IGMP proxy.Code: Select all/interface bridge filter add action=accept chain=forward comment="Allow mDNS" dst-address=224.0.0.251/32 mac-protocol=ip add action=drop chain=forward comment="Drop all other multicast" dst-address=224.0.0.0/4 mac-protocol=ip
Also @DarkNate recommends a loopback, but the upstream could be the VLAN where you your doing the browsing from ("main"/base/mgmt/etc) and the "IoT VLANs" point to that "main VLAN" and that might be more friendly to the default firewall than adding a loopback bridge.
Vlans segregation is just one of those.
Firewalls add another layer. So is endpoint security packages. And then traffic log analysis/UTM is another.
MikroTik has the ability to provide a convenience feature that would allow for more segregation, while only allowing certain services (mDns and related) to pass through.
It isn’t new precedence for MikroTik to add a convince feature. Capsman, user manager, hotspot, winbox, hell even the poorly designed quickset was made for convenience.
Aside that, I have tried Nate’s Loopback and without loopback example. I couldn’t get chromecast to work with IGMP proxy.
While others may learn with understand all of the concept and then build, my brain doesn’t work like that. I need to see it working, then work backwards on how I can build it better for the next time. Then I can know it.
Re: mDNS repeater feature
but he's not an assh–e like me,
if he answers you, he doesn't help you, he tells you that you are incompetent and that you have no graduation to understand...
I'm still waiting for someone to CONFIRM that it works... (and post a true export)...
if he answers you, he doesn't help you, he tells you that you are incompetent and that you have no graduation to understand...
I'm still waiting for someone to CONFIRM that it works... (and post a true export)...
Re: mDNS repeater feature
Glad that you understand, I will see if I will open another topic for issue with my case, need to investigate if this even possible on this network layer.I specify, however, that I am neither for, nor against the request.
I am against things made without sense, dividing everything and then having the needs to leave the devices communicate with each other again...
In a certain sense, what you asked for, even if it is resolved in another way, seems to me much more logical and useful....
Re: mDNS repeater feature
I really do not understand why someone is still fighting this with false or misleading arguments here.
If you do not see benefit or use for yourself then OK, do not use it.
But other users see some value in this feature.
mDNS works in local subnet and it can be fine for major home users or simple setups. But it hits wall with network segmentation what is mostly case for advanced users / SMB / Enteprises.
In such networks you want to achieve connectivity and keep segmentation due to security reasons and mDNS reflector/proxy is an option how to do it.
If you do not see benefit or use for yourself then OK, do not use it.
But other users see some value in this feature.
mDNS works in local subnet and it can be fine for major home users or simple setups. But it hits wall with network segmentation what is mostly case for advanced users / SMB / Enteprises.
In such networks you want to achieve connectivity and keep segmentation due to security reasons and mDNS reflector/proxy is an option how to do it.
Re: mDNS repeater feature
ok, put the mDNS proxy, and then what?
Proxy mDNS is not the method by which THEN the two devices send data to each other....
Proxy mDNS is not the method by which THEN the two devices send data to each other....
Re: mDNS repeater feature
Then you can get argument that putting security and mDNS reflector in same sentence is oxymoron since someone on another network can do mitm attack and send discovery responses to services on bogus device.In such networks you want to achieve connectivity and keep segmentation due to security reasons and mDNS reflector/proxy is an option how to do it.
Re: mDNS repeater feature
Just to then punch holes in those layers? And just ignoring the vendors advice (e.g. the "illusion of security") here, which be okay if you understood the underlying network protocols risks. But cut-and-paste other peoples configuration you don't understand doesn't seem very safe/secure to me. Just keeping the VLAN-as-security myth alive.keep segmentation due to security reasons
Use QuickSet, and then add any bridge filter drop rules you want. That actually give you all the fine-grain control between devices to implement whatever rules you want to block things... And to me seems like a better approach with your level of expertise here as that's pretty simple. No VLANs required. No IGMP Proxy. Just whatever "/interface/bridge/filter add action=drop" you want.
Re: mDNS repeater feature
@optio, Amm0
I guess you understand it wrong from my perspective.
It is not that you do segment network because of mDNS, but you already have segmented network and want to use mDNS now.
The network segmentation has it reason and in some aspects it increase security. Now you have new devices using mDNS and want to use it with your actual
design. Will you put everything to flat network?
My 1st comments in this thread are with example why it is needed. Shortly.
You have segmented network for: internal users, guests, dmz for nas/servers, IoT, cameras, printers etc. All separated, firewall rules in place etc. And with all this you want just some network segments to see mDNS to be able to discover devices and use it.
So the segmented network gives you some more security (in some aspects) even if you allow mDNS between it.
I guess you understand it wrong from my perspective.
It is not that you do segment network because of mDNS, but you already have segmented network and want to use mDNS now.
The network segmentation has it reason and in some aspects it increase security. Now you have new devices using mDNS and want to use it with your actual
design. Will you put everything to flat network?
My 1st comments in this thread are with example why it is needed. Shortly.
You have segmented network for: internal users, guests, dmz for nas/servers, IoT, cameras, printers etc. All separated, firewall rules in place etc. And with all this you want just some network segments to see mDNS to be able to discover devices and use it.
So the segmented network gives you some more security (in some aspects) even if you allow mDNS between it.
Re: mDNS repeater feature
Don't we punch holes into firewalls EVERYDAY with port forwarding? How about UPnP? GEOIP blocking? Content filtering? The OOTB experience with any CCR isn't 'secure'. It's what you make of it, and you have make compromises otherwise everything would be 0 trust and the world would be air gapped.Just to then punch holes in those layers? And just ignoring the vendors advice (e.g. the "illusion of security") here, which be okay if you understood the underlying network protocols risks. But cut-and-paste other peoples configuration you don't understand doesn't seem very safe/secure to me. Just keeping the VLAN-as-security myth alive.keep segmentation due to security reasons
Use QuickSet, and then add any bridge filter drop rules you want. That actually give you all the fine-grain control between devices to implement whatever rules you want to block things... And to me seems like a better approach with your level of expertise here as that's pretty simple. No VLANs required. No IGMP Proxy. Just whatever "/interface/bridge/filter add action=drop" you want.
What you considered secure may not be considered secure enough by someone else, and vice versa?
You're right, copy/paste other configs isn't safe, but it's a starting point. It's a risk that one has to choose to use or not use. The same goes with port forwarding, allowing management interface from the internet, or using a mac authentication for 802.1X.
Re: mDNS repeater feature
I do actually, from home user perspective, like myself, if you have complete control of your network clients and you don't expect elite hackers as your home guests, as I wrote at the end - no concern. My comment was that you can expect argument from someone related to enterprise/business network security perspective since you mentioned "Enteprises".@optio, Amm0
I guess you understand it wrong from my perspective.
Re: mDNS repeater feature
The concern may depend on a user.I do actually, from home user perspective, like myself, if you have complete control of your network clients and you don't expect elite hackers as your home guests, as I wrote at the end - no concern
You may have more trusted devices as PCs, phones, servers you maintain and regular update/upgrade.
But then other devices you do not have full control, sporadic upgrades if any, do not know how it communicates etc.
If such device has some well known vulnerability which can easily and widely used, then it can be compromised and no elite hacker is needed.
So my perspective is: why some devices should sniff around my network when not necessary? They in somehow isolated network and that's it.
Re: mDNS repeater feature
Here is my config for following Nate's suggestion. Both Airplay and Chromecast still don't work.
Topology
R1 > LAG to 2 MLAG connected CRS3X SWITCHES > LAG to POE Switch > CAP AC
I get it, I'm not skilled, experienced, smart as others that have done it all. I'm not afraid of being dumb. It allows me to ask questions and learn.
Topology
R1 > LAG to 2 MLAG connected CRS3X SWITCHES > LAG to POE Switch > CAP AC
I get it, I'm not skilled, experienced, smart as others that have done it all. I'm not afraid of being dumb. It allows me to ask questions and learn.
Code: Select all
---BOF---
###R1###
/interface bridge
add igmp-snooping=yes igmp-version=3 ingress-filtering=no mld-version=2 name=LANBridge priority=0x1000 vlan-filtering=yes
add arp=disabled name=loopback protocol-mode=none
#This is the trunk port connected to the a set of CRS Switches via MLAG#
/interface bridge port add bridge=LANBridge interface=LACPtoSwitches trusted=yes
/interface bridge port add bridge=LANBridge interface=ether5 pvid=69
#VLAN 69 is IOT Chromecast vlan - VLAN 75 is main vlan#
/interface bridge vlan add bridge=LANBridge tagged=LANBridge,LACPtoSwitches vlan-ids=75
/interface bridge vlan add bridge=LANBridge tagged=LANBridge,LACPtoSwitches vlan-ids=69
#IP ADDRESSES#
/ip address add address=10.69.69.1/24 comment="IOT" interface=v69 network=10.69.69.0
/ip address add address=10.69.75.1/24 comment="main network" interface=v75 network=10.69.75.0
/ip address add address=10.0.0.1 interface=loopback network=10.0.0.1
#DHCP SERVERS#
/ip pool add name=69pool ranges=10.69.69.51-10.69.69.200
/ip dhcp-server add address-pool=69pool dhcp-option-set=voice interface=v69 lease-time=5h55m name=v69_dhcp
/ip dhcp-server network add address=10.69.69.0/24 dns-server=10.69.69.1 gateway=10.69.69.1
/ip pool add name=75pool ranges=10.69.75.51-10.69.75.254
/ip dhcp-server add address-pool=75pool interface=v75 lease-time=1h10m name=v75_dhcp
/ip dhcp-server network add address=10.69.75.0/24 dns-server=10.69.75.1 gateway=10.69.75.1
#IGMP Proxy #
/routing igmp-proxy interface add interface=v75
/routing igmp-proxy interface add interface=v69
/routing igmp-proxy interface add interface=loopback upstream=yes
#On BOTH CRS3X Switches#
#SW1#
/interface bridge add dhcp-snooping=yes igmp-snooping=yes igmp-version=3 ingress-filtering=no mld-version=2 name=MLAG-BRIDGE vlan-filtering=yes
/interface ethernet set [ find default-name=ether23 ] comment="POE SW LACP LegA"
/interface ethernet set [ find default-name=ether24 ] comment="R1 LACP LegA"
/interface ethernet set [ find default-name=sfp-sfpplus1 ] comment="ICC LACP Leg1"
/interface ethernet set [ find default-name=sfp-sfpplus2 ] comment="ICC LACP Leg2"
#SW2#
/interface bridge add dhcp-snooping=yes igmp-snooping=yes igmp-version=3 ingress-filtering=no mld-version=2 name=MLAG-BRIDGE vlan-filtering=yes
/interface ethernet set [ find default-name=ether23 ] comment="POE SW LACP LegB"
/interface ethernet set [ find default-name=ether24 ] comment="R1 LACP LegB"
/interface ethernet set [ find default-name=sfp-sfpplus1 ] comment="ICC LACP Leg1"
/interface ethernet set [ find default-name=sfp-sfpplus2 ] comment="ICC LACP Leg2"
#Both Switches Match below#
/interface bridge mlag set bridge=MLAG-BRIDGE peer-port=ICC-BOND
/interface bridge port add bridge=MLAG-BRIDGE interface=ICC-BOND pvid=99 trusted=yes
/interface bridge port add bridge=MLAG-BRIDGE interface=POE-SW-BOND trusted=yes
/interface bridge port add bridge=MLAG-BRIDGE interface=R1-BOND trusted=yes
/interface bridge port add bridge=MLAG-BRIDGE interface=ether2 pvid=69
/interface bridge port add bridge=MLAG-BRIDGE interface=ether3 pvid=69
/interface bridge port add bridge=MLAG-BRIDGE interface=ether4 pvid=69
/interface bridge port add bridge=MLAG-BRIDGE interface=ether5 pvid=69
/interface bridge port add bridge=MLAG-BRIDGE interface=ether6 pvid=69
/interface bridge port add bridge=MLAG-BRIDGE interface=ether7 pvid=69
/interface bridge port add bridge=MLAG-BRIDGE interface=ether8 pvid=69
/interface bridge port add bridge=MLAG-BRIDGE interface=ether9 pvid=69
/interface bridge port add bridge=MLAG-BRIDGE interface=ether10 pvid=69
/interface bridge port add bridge=MLAG-BRIDGE interface=ether11 pvid=69
/interface bridge port add bridge=MLAG-BRIDGE interface=ether12 pvid=69
/interface bridge port add bridge=MLAG-BRIDGE interface=ether13 pvid=69
/interface bridge port add bridge=MLAG-BRIDGE interface=ether14 pvid=69
/interface bridge port add bridge=MLAG-BRIDGE interface=ether15 pvid=69
/interface bridge port add bridge=MLAG-BRIDGE interface=ether16 pvid=69
/interface bridge port add bridge=MLAG-BRIDGE interface=ether17 pvid=69
/interface bridge port add bridge=MLAG-BRIDGE interface=ether18 pvid=69
/interface bridge port add bridge=MLAG-BRIDGE interface=ether19 pvid=69
/interface bridge port add bridge=MLAG-BRIDGE interface=ether20 pvid=69
/interface bridge port add bridge=MLAG-BRIDGE interface=ether21 pvid=69
/interface bridge vlan add bridge=MLAG-BRIDGE tagged=ICC-BOND,R1-BOND,POE-SW-BOND,SERVER1-BOND vlan-ids=75
/interface bridge vlan add bridge=MLAG-BRIDGE tagged=ICC-BOND,POE-SW-BOND,R1-BOND,SERVER1-BOND vlan-ids=69
#HP2520G config#
HP2520G-SW1# show ip igmp config
IGMP Service Config
Control unknown multicast [Yes] : Yes
Forced fast leave timeout [0] : 4
Delayed flush timeout [0] : 0
VLAN ID VLAN Name IGMP Enabled Querier Allowed Querier Interval
------- ------------ ------------ --------------- ----------------
1 vlan1 No Yes 125
69 IOT Yes Yes 125
75 Main Yes Yes 125
##CAP AC AP - Connected to HP POE Switch##
/interface wireless set [ find default-name=TestIOT ] band=2ghz-g/n country="united states" disabled=no frequency=auto mode=ap-bridge multicast-helper=full radio-name=Cap2-2G security-profile=s2gwifipass ssid=TestIOT station-roaming=enabled vlan-id=69 vlan-mode=use-tag wps-mode=disabled
/interface wireless add disabled=no keepalive-frames=disabled mac-address=CE:2D:E0:47:9B:EA master-interface=TestIOT multicast-buffering=disabled multicast-helper=full name=Main security-profile=s2gwifipass ssid=s2gwifi vlan-id=75 vlan-mode=use-tag wds-cost-range=0 wds-default-cost=0 wps-mode=disabled
/interface bridge add comment=defconf igmp-snooping=yes igmp-version=3 mld-version=2 name=lanBridge
/interface bridge port add bridge=lanBridge comment=defconf ingress-filtering=no interface=ether1
/interface bridge port add bridge=lanBridge comment=defconf ingress-filtering=no interface=ether2
/interface bridge port add bridge=lanBridge interface=wlan1
/interface bridge port add bridge=lanBridge interface=TestIOT
---EOF---
Re: mDNS repeater feature
You can use the same config as mine, simply replace both VLANs from my example with your two bridges in IGMP Proxy, that's it. Each bridge is a separate broadcast domain, same thing as VLAN, only bridge is untagged traffic.I'm interested into how this IGMP proxy works because it might fix my issue hopefully.
I have a server which runs on a subnet (192.168.3.0/24) and other devices on another one (10.10.10.0/24). No VLANs, just two subnets set up on two bridges.
I installed jellyfin on the server, and it happens now that a client (my smart TV) is on the subnet 10.10.10.0/24 and it should get access to the jellyfin app running on the server and its contents via DLNA I guess. I had already set a few firewall rules on my MK device to allow a couple of devices on 10.10.10.0/24 to acces my server, like my tv, and my laptop when I'm on the other subnet. They works. However, I didn't manage to make my tv see jellyfin contents on the server, I thought that IGMP or mDNS might have something to do with it.
I'm not a computer networking expert so I am aware that I might have said something stupid.
Could you help me figure it out?
Thanks
Re: mDNS repeater feature
My dude, I work with MikroTik on daily basis, at home as well or in home use cases.The guy is the toxic avenger. He may have some experience, but how he has been allowed to touch big networks with such a bad attitude is just horrible. These forums (and other places) are meant to help people with Mikrotik, not belittle others. I never claimed to be an expert, yet he starts with nasty attitude with everyone. Calling everyone lazy for wanting a convenience feature is such a bad attitude.
He then goes on to say 'contact support'. There is virtually no support for anyone that doesn't have a contact at Mikrotik. Forums and other venues like reddit and my discord are one of the very few places people can get help on MIkrotik topics.
The packet count in IGMP Proxy is always zero, it is a bug, you are free to file bug report with MikroTik. Packet count doesn't impact functionality for your mDNS uses etc.
Re: mDNS repeater feature
People want it because they like flooding their networks at home with BUM. No clue why.why would someone need to have that? worse, why even relay such network noise?
Re: mDNS repeater feature
Advanced use case for IGMP Proxy is possible as long as you have RSTP handling L2 loops, otherwise you will need PIM, it simply needs better examples from MikroTik. For inter-VLAN firewalling, you'll need to be careful with firewalling of multicast groups, better to ensure you permit all multicast in firewall on all LAN interfaces (all VLANs etc).That's the existential question here. Butwhy would someone need to have that? worse, why even relay such network noise?And... it sounds like this could be resolved by better docs on IGMP Proxy for those that want to go this route. An example there would go a long way.[...] at the end it is Mikrotik's pure business decision [...]
But specific the troubles in making IGMP working may involve the firewall. Both the multicast discovery and the resulting unicast traffic once a device was discovered need to be allowed. If you block inter-VLAN forwarding, the IGMP proxy follows those rules too.
Re: mDNS repeater feature
I'm using iPhone etc, smart TVs etc on different VLANs. IGMP Proxy works fine, as per my example, nothing special is configured.IOT. This category of devices is now more prolific than every before. In homes, smb, and enterprises. We’re looking for tools to allow us to segregate these devices, yet interact the way that is convenient to those that are paying IT/Network support/engineers.
With how much iPhone , bonjour, AirPlay,, chromecast has been made the norm, sometimes it’s not always possible to say ‘no’.
Re: mDNS repeater feature
It's just L2/2.5 talk between Samsung TV and phone, instead of them relaying traffic over a TURN server, or downloading updates, one device can download and push via multicast to all devices.The fact is another, the problem is the absolute trust that is given to smartphones and computers,
which are seen as ultra-secure and without any espionage problems...
Instead the "IoT", which are products that come from exactly the same manufacturers, just from another brand, are the devil.
Well, it is precisely this blindness that causes most of the problems...
Don't want your Samsung TV (for example) to "see" your Samsung smartphone? What do you care for? Both devices are already full of Samsung spionage...
This situation is borderline comical, in own home separate the network because otherwise WHAT?
And I'm not talking about the "guest" who wants to print on our printer, since the latest printers already does it on their own without even using the Internet or home wlan...
All this effort for NOTHING. That's what the truth is for me.
I repeat, for me, then being an opinion, it is not said that it is an absolute truth that, only a few Than here on the forum Oven's truth,
it's like religious people, you're just an idiot, only they (religious people) know the truth and we can't tell it, we wouldn't understand it, we are inept...
You simply don't see this because of poor docs from the IoT OEMs. But PCAP does not lie, you can easily detect their multicast/IGMP use.
Re: mDNS repeater feature
Upstream can be a VLAN, only if you want that VLAN to serve multicast traffic, this means everything else like iPhone AirDrop on other VLANs or on the same VLANs will follow BUM flood everywhere on every port.Also @DarkNate recommends a loopback, but the upstream could be the VLAN where you your doing the browsing from ("main"/base/mgmt/etc) and the "IoT VLANs" point to that "main VLAN" and that might be more friendly to the default firewall than adding a loopback bridge.
The goal here is to reduce network noise with plain IGMP Proxy, hence upstream loopback.
But you can likely have more than one upstream.
Re: mDNS repeater feature
Config looks fine. But possibly, I could've missed something. Run a torch/packet sniffer and perform analysis on what happens when you try Chromecast. Something, somewhere is dropping the packet. Multicast-querier should remain disabled on the bridges/HP switch.Here is my config for following Nate's suggestion. Both Airplay and Chromecast still don't work.
If you're advanced enough to use MLAG and VLANs, you should be advanced enough to debug.
And unrelated but important, you should ensure bridge priority is correctly configured on all the network routers/switches to ensure RSTP/BPDUs work correctly. Refer to vendor docs on that, from MikroTik and HP.
Re: mDNS repeater feature
ok, is there something I can digest to better understand where Multicast-querier should be disabled? I currently see it querier enabled for those vlans on the AP switch. (I've now disabled those, tested, issue remains).Config looks fine. But possibly, I could've missed something. Run a torch/packet sniffer and perform analysis on what happens when you try Chromecast. Something, somewhere is dropping the packet. Multicast-querier should remain disabled on the bridges/HP switch.
I don't know how to debug mdns / IGMP Proxy.If you're advanced enough to use MLAG and VLANs, you should be advanced enough to debug.
When I torch the vlan75, and test ccast, I do see my iPhone trying to reach out to 224.0.0.251:5353 udp as expected. So mdns is traveling from my phone, AP, HP switch, CRS switch, and landing at the router...
When I torch the vlan69, and test ccast, i do not see any traffic for port 5353.
This is where I'm stuck. Somethings missing.
Thank you for the recommendation, I'll verify that the bridge priority is setup properly on all the switches/router.And unrelated but important, you should ensure bridge priority is correctly configured on all the network routers/switches to ensure RSTP/BPDUs work correctly. Refer to vendor docs on that, from MikroTik and HP.
Re: mDNS repeater feature
Doesn't Chromecast actually use SSDP? If so, same story, but 239.255.255.250 port 1900 is what you'd need to look at if it does use SSDP.When I torch the vlan69, and test ccast, i do not see any traffic for port 5353.
Also, didn't study the config very carefully, maybe covered...but "ingress-filtering=no" on your main bridge might allow those evil IoT device pass tagged traffic since the bridge won't enforce the VLAN tagging rules (except for PVID).
Re: mDNS repeater feature
Yep, ingress-filtering is already set to no.Doesn't Chromecast actually use SSDP? If so, same story, but 239.255.255.250 port 1900 is what you'd need to look at if it does use SSDP.When I torch the vlan69, and test ccast, i do not see any traffic for port 5353.
Also, didn't study the config very carefully, maybe covered...but "ingress-filtering=no" on your main bridge might allow those evil IoT device pass tagged traffic since the bridge won't enforce the VLAN tagging rules (except for PVID).
I'll check 1900 in a bit and report back.
I just don't know much about how the interaction works. If I remember correctly, mDNS is used for discovery for ccast.
Re: mDNS repeater feature
tested ccast, torched vlan69 for port 1900. Saw a kids pc trying to connect to 239.255.255.250:1900
Guessing Chrome is always looking for ccast devices. Still no joy on IGMP Proxy. I'm open to suggestions. I don't mind reading some digestible information about it.
Guessing Chrome is always looking for ccast devices. Still no joy on IGMP Proxy. I'm open to suggestions. I don't mind reading some digestible information about it.
Re: mDNS repeater feature
Very good. I'll try it. Thank you
You can use the same config as mine, simply replace both VLANs from my example with your two bridges in IGMP Proxy, that's it. Each bridge is a separate broadcast domain, same thing as VLAN, only bridge is untagged traffic.
Re: mDNS repeater feature
I did a PCAP on my end.
So IPv4 (IGMP) does get queried by the proxy/MikroTik. But IPv6 (MLD) does not. And this could impact apps that explicitly rely only on IPv6 Multicast or prefer IPv6, so of course you're not going to see it working.
The experts in this thread should demand for IPv6 MLD support in IGMP Proxy instead of mDNS repeater crap hacks.
So IPv4 (IGMP) does get queried by the proxy/MikroTik. But IPv6 (MLD) does not. And this could impact apps that explicitly rely only on IPv6 Multicast or prefer IPv6, so of course you're not going to see it working.
The experts in this thread should demand for IPv6 MLD support in IGMP Proxy instead of mDNS repeater crap hacks.
Re: mDNS repeater feature
Hello @DarkNate, apologies for not having followed your example, it was not clear that the "loopback" interface was the one that did the trick.What is the reason for your fear of loopback interface to correctly set the upstream interface?
This is what I tested without success, maybe due to a misconfig on my side:
Code: Select all
/interface bridge add arp=disabled name=loopback protocol-mode=none
/ip address add address=10.0.0.0 comment="Loopback" interface=loopback network=10.0.0.0
/routing igmp-proxy interface add interface=loopback upstream=yes ([i]then also added the LAN subnet + 192.168.1.0/24[/i])
/routing igmp-proxy interface add interface=LAN
Re: mDNS repeater feature
And your other bridge???
On DarkNathan post is present another bridge, with some settings.......
Also on igmp-proxy
Probably DarkNathan forget to export the VLANs and is why his config do not work for others that blindly copy & paste without understand what are doing...
On DarkNathan post is present another bridge, with some settings.......
Code: Select all
/interface bridge
# ok on your
add arp=disabled name=loopback protocol-mode=none
# not present on your, keeped relevant parts only
add […] igmp-snooping=yes igmp-version=3 mld-version=2 […]
Also on igmp-proxy
Code: Select all
/routing igmp-proxy interface
# this is present
add interface=loopback upstream=yes
# this are not LANs, are VLANs
add interface="Main VLAN"
add interface="Management VLAN"
Probably DarkNathan forget to export the VLANs and is why his config do not work for others that blindly copy & paste without understand what are doing...
Re: mDNS repeater feature
Adding missing settings and playng with config, this are jus the minimal config, the VLANs and the ports still be correctly configured.
For RouterOS v7.
On RouterOS v6, after install multicast extra package, remove mld-version=2 and set it on Winbox. For one bug the parameter can not be set on CLI.
For RouterOS v7.
On RouterOS v6, after install multicast extra package, remove mld-version=2 and set it on Winbox. For one bug the parameter can not be set on CLI.
revised but not verified code
/interface bridge # on RouterOS v6 remove mld-version=2 and set it on Winbox. For some reason the parameter can not be set on CLI. add igmp-snooping=yes igmp-version=3 mld-version=2 name=bridge protocol-mode=none add arp=disabled name=loopbridge protocol-mode=none # missing on DarkNathan example /interface vlan add interface=bridge name="VLAN 20" vlan-id=20 add interface=bridge name="VLAN 30" vlan-id=30 add interface=bridge name="VLAN 40" vlan-id=40 add interface=bridge name="MGMT VLAN" vlan-id=10 /interface bridge port add bridge=bridge interface=ether2 pvid=20 add bridge=bridge interface=ether3 pvid=30 add bridge=bridge interface=ether4 pvid=40 add bridge=bridge interface=ether5 pvid=10 /interface bridge vlan add bridge=bridge tagged=bridge vlan-ids=20,30,40,10 /ip address add address=10.0.0.0/32 interface=loopbridge add address=10.20.0.1/24 interface="VLAN 20" add address=10.30.0.1/24 interface="VLAN 30" add address=10.40.0.1/24 interface="VLAN 40" add address=10.10.0.1/24 interface="MGMT VLAN" /routing igmp-proxy interface add interface=loopbridge upstream=yes add interface="VLAN 20" add interface="VLAN 30" add interface="VLAN 40" add interface="MGMT VLAN"
Re: mDNS repeater feature
I didn't forget to add. This whole thread is about inter-VLAN routing, I expect people already configured the VLANs, wtf do I need to teach them basic VLAN config? It's already here:Probably DarkNathan forget to export the VLANs and is why his config do not work for others that blindly copy & paste without understand what are doing…
https://help.mikrotik.com/docs/display/ ... +switching
I've edited my post to make it a bit more clear, but like I said somewhere else, stupidity can only be cured by medical treatment, hopefully.
viewtopic.php?t=174354#p982910
Copy/Paste without understanding will obviously never work, ain't that common sense from grade 1 in school, maths class? 1+1=3 from your friend's notes?
Re: mDNS repeater feature
What is this? "(then also added the LAN subnet + 192.168.1.0/24)"Hello @DarkNate, apologies for not having followed your example, it was not clear that the "loopback" interface was the one that did the trick.
This is what I tested without success, maybe due to a misconfig on my side:Code: Select all/interface bridge add arp=disabled name=loopback protocol-mode=none /ip address add address=10.0.0.0 comment="Loopback" interface=loopback network=10.0.0.0 /routing igmp-proxy interface add interface=loopback upstream=yes ([i]then also added the LAN subnet + 192.168.1.0/24[/i]) /routing igmp-proxy interface add interface=LAN
Adding alternative subnets is only for advanced cases, where even I never need to use, and I have one of the most complex home labs you'll find on the DFZ.
If you built a network that requires alternative subnets, it means you need PIM not IGMP Proxy.
Re: mDNS repeater feature
But don't fool us all...I didn't forget to add. […] I've edited my post to make it a bit more clear
Will you stop offending forum users?[…]
but like I said somewhere else, stupidity can only be cured by medical treatment, hopefully.
[…]
ain't that common sense from grade 1 in school, maths class? 1+1=3 from your friend's notes?
[…]
Re: mDNS repeater feature
Not sure what you mean about fooling? Why should VLAN config be required for IGMP Proxy to work, if there's no VLANs on a network? If there are then the original post already made it clear.But don't fool us all...
Will you stop offending forum users?[…]
but like I said somewhere else, stupidity can only be cured by medical treatment, hopefully.
[…]
ain't that common sense from grade 1 in school, maths class? 1+1=3 from your friend's notes?
[…]
It's not offensive if it is a fact.
Re: mDNS repeater feature
I'm not the first to complain about how you answer and your know-it-all attitude "I studied, you are stupid and that's it"...It's not offensive if it is a fact.
Thank you, surely now in the eyes of other users I am a cute and kind little bobcat, compared to you...
I'd rather be ignorant than knowledgeable.
An ignoramus can always learn, the know-it-all cannot.
But this is a problem Than an Oven's truth
And I like "Los Gatos", sooner or later we meet there in person...
Re: mDNS repeater feature
he wanted to mark it ITALIC inside a
What is this? "(then also added the LAN subnet + 192.168.1.0/24)"
Code: Select all
code see:
Code: Select all
code block text with [i]italic fomating [/i]inside Re: mDNS repeater feature
maybe "metti ordine in casa tua" might be suitable here...Will you stop offending forum users?
seen your post where you also uncomprehendingly behave alike sometimes, so ... could you maybe stick to the topic? for the sake of users which might want/"need" mDNS aid
thanks
Re: mDNS repeater feature
No they can never learn. A newbie/curious person on the other hand can:An ignoramus can always learn, the know-it-all cannot.
The important thing is not to stop questioning. Curiosity has its own reason for existing. One cannot help but be in awe when one contemplates the mysteries of eternity, of life, of the marvellous structure of reality. It is enough if one tries to comprehend only a little of this mystery every day.
- Albert Einstein
Re: mDNS repeater feature
Focusing on the technical detail... IGMP works on interfaces/IP, so it's a fair point that it doesn't matter if VLAN.
Although guessing 90%+ of the +1's here have some "VLAN for safety" home configurations, with TV/etc separated from smartphones. The wisdom of that is well cataloged in this thread.
I do think @DarkNate's point here has been not been absorbed...
Also keep in mind, even if IGMP Proxy is working., the firewall would still need to allow the resulting traffic that's suggested in the discovery packets (e.g. mDNS does have return an DNS SRV someplace with ports/IP for a device to use to connect). The only simple firewall example be to allow the "IoT" VLAN full access to "MAIN" VLAN. Which defeats the whole purpose of "VLAN'ing your network".
So the next step after IGMP is your firewall needs to allow only resulting traffic you want (e.g. likely some music/video stream)...but that takes understand the ports used by the devices. Even then the mDNS SRV (or SSDP XML) can use dynamic/different port that may make that even more difficult to construct. And the discovered service might also use multicast, which should also flow through the IGMP, unless it suggest IPv6...
But all so complex for some very marginal security benefits from separating devices...based on a subjective opinion that threats are based on the device class (smartphones = safe, chrormecast = unsafe).
Although guessing 90%+ of the +1's here have some "VLAN for safety" home configurations, with TV/etc separated from smartphones. The wisdom of that is well cataloged in this thread.
I do think @DarkNate's point here has been not been absorbed...
Since IPv6 is enabled by default...easy to imagine Chromecast etc might very well prefer IPv6 if it find it on the network. I guess you might want to disable IPv6 as a result if you go down IGMP Proxy'ing.But IPv6 (MLD) does not. And this could impact apps that explicitly rely only on IPv6 Multicast or prefer IPv6, so of course you're not going to see it working.
The experts in this thread should demand for IPv6 MLD support in IGMP Proxy instead of mDNS repeater crap hacks.
Also keep in mind, even if IGMP Proxy is working., the firewall would still need to allow the resulting traffic that's suggested in the discovery packets (e.g. mDNS does have return an DNS SRV someplace with ports/IP for a device to use to connect). The only simple firewall example be to allow the "IoT" VLAN full access to "MAIN" VLAN. Which defeats the whole purpose of "VLAN'ing your network".
So the next step after IGMP is your firewall needs to allow only resulting traffic you want (e.g. likely some music/video stream)...but that takes understand the ports used by the devices. Even then the mDNS SRV (or SSDP XML) can use dynamic/different port that may make that even more difficult to construct. And the discovered service might also use multicast, which should also flow through the IGMP, unless it suggest IPv6...
But all so complex for some very marginal security benefits from separating devices...based on a subjective opinion that threats are based on the device class (smartphones = safe, chrormecast = unsafe).
Re: mDNS repeater feature
Unless you are an advanced networking user or engineer, I agree. Using VLANs at home makes no sense for the added complexity and bullshit hacks required.
For me personally, I don't use VLANs for “security”. I use it for labbing, there's main VLAN, guest VLAN and labbing VLAN. Each having different IP networking for logging reasons and PBR.
Can't have a home lab without labbing VLAN, the missus keeps complaining when the main VLAN used to go down because I'm doing some labbing on it in the past.
For me personally, I don't use VLANs for “security”. I use it for labbing, there's main VLAN, guest VLAN and labbing VLAN. Each having different IP networking for logging reasons and PBR.
Can't have a home lab without labbing VLAN, the missus keeps complaining when the main VLAN used to go down because I'm doing some labbing on it in the past.
Re: mDNS repeater feature
???could you maybe stick to the topic? for the sake of users which might want/"need" mDNS aid
And what is this?
viewtopic.php?t=174354#p992598
The only thing in the argument is "some way" to get mDNS to work between two (or more) VLANs.
Anything else is offtopc, if VLANs aren't involved, it's offtopic and @mafiosa's requirement is not met
Re: mDNS repeater feature
good advice
Re: mDNS repeater feature
To be clear, I ain't a VLAN hater – just pointing out moving a couple devices that need discovery to the "main" LAN would save a ton of learning, or containers, or waiting for a feature that may never come.
To answer @CTSsean on that point...
https://www.youtube.com/watch?v=8gbY9ScZJlQ
(won't help with SSDP, but covers the gambit of mDNS/DNS-SD discovery topics)
Re specifically IGMP Proxy. Exactly how is vendor-specific, why torch/sniffer are useful since some of this specific stuff just isn't documented.
But understanding what is documented by Mikrotik might be a good start. Here is a cheat sheet on those:
Bridge "Snooping" - https://help.mikrotik.com/docs/pages/vi ... d=59277403
https://help.mikrotik.com/docs/display/ ... t+Protocol
IGMP (general) - https://help.mikrotik.com/docs/display/ ... t+Protocol
IGMP Proxy - https://help.mikrotik.com/docs/display/ROS/IGMP+Proxy
(in some CRS this is hardware - https://help.mikrotik.com/docs/display/ ... LDSnooping ).
To answer @CTSsean on that point...
Well this might be helpful if you want to go off the deep end of understanding mDNS, this presentation is from the IETF "summarizing" (takes an ~1 hour) the various RFCs:I don't mind reading some digestible information about it.
https://www.youtube.com/watch?v=8gbY9ScZJlQ
(won't help with SSDP, but covers the gambit of mDNS/DNS-SD discovery topics)
Re specifically IGMP Proxy. Exactly how is vendor-specific, why torch/sniffer are useful since some of this specific stuff just isn't documented.
But understanding what is documented by Mikrotik might be a good start. Here is a cheat sheet on those:
Bridge "Snooping" - https://help.mikrotik.com/docs/pages/vi ... d=59277403
https://help.mikrotik.com/docs/display/ ... t+Protocol
IGMP (general) - https://help.mikrotik.com/docs/display/ ... t+Protocol
IGMP Proxy - https://help.mikrotik.com/docs/display/ROS/IGMP+Proxy
(in some CRS this is hardware - https://help.mikrotik.com/docs/display/ ... LDSnooping ).
Re: mDNS repeater feature
???And he still thinks he has some mod authority in the forums, when the whole world knows he was dishonourably stripped of his mod privilege by MikroTik staff. What a
Why do you invent these things? Isn't ChatGPT already enough to invent bulls–t?
It had almost become a full-time job, you have no idea...
Better as it is now.
You don't understand until you try it...
Don't worry, I know how to wait longer than you think on the river bank...
Re: mDNS repeater feature
@rextended, @DarkNate - your bickering may just cause Mikrotik to add this feature out of spite. And I think they have more important things to work than mDNS repeaters. 
Re: mDNS repeater feature
Oh... ok, that's fine, I'll abstain from answering him completely, except for technical questions that are relevant for everyone, all right?@rextended, @DarkNate - your bickering […]
And you know it's hard for me not to answer...

Re: mDNS repeater feature
Hello @DarkNate, I can not be smart like you Sir but I did my best to have the device config working at the best following all official guides (I mean Bridges, VLANs, etc...), waited some days after your initial answer just to make a couple of tests and not just answer "not working for me" and lose your time.What is this? "(then also added the LAN subnet + 192.168.1.0/24)"
My note was related to the additional setting of the subnet, just to make sure that was not working not due to this.
I would be happy to agree with you that we don't need mDNS repeater feature, maybe one day
Re: mDNS repeater feature
Any suggestions for my case?I did a PCAP on my end.
So IPv4 (IGMP) does get queried by the proxy/MikroTik. But IPv6 (MLD) does not. And this could impact apps that explicitly rely only on IPv6 Multicast or prefer IPv6, so of course you're not going to see it working.
The experts in this thread should demand for IPv6 MLD support in IGMP Proxy instead of mDNS repeater crap hacks.
I'm not sure what I'm missing.
Re: mDNS repeater feature
Reach out to MikroTik support. Give them the supout export file. This needs to be solved by them, not me.Any suggestions for my case?
I'm not sure what I'm missing.
Re: mDNS repeater feature
For those interested, i created an extended container image based on the github repo and a setup script which simplifies the mDNS repeating setup:
Mikrotik: mDNS Repeater as Docker-Container on the Router (ARM,ARM64,X86) (english version)
Mikrotik: mDNS Repeater als Docker-Container auf dem Router (ARM,ARM64,X86) (german version)
Regards @colinardo
Mikrotik: mDNS Repeater as Docker-Container on the Router (ARM,ARM64,X86) (english version)
Mikrotik: mDNS Repeater als Docker-Container auf dem Router (ARM,ARM64,X86) (german version)
Regards @colinardo
Last edited by colinardo on Tue Mar 28, 2023 2:58 pm, edited 1 time in total.
Re: mDNS repeater feature
Thanks for share!

"container", "simplifies" and "newbies" on same line....[…] container […] simplifies […] newbies […]
Re: mDNS repeater feature
i created an extended container image
That's a very fine contribution.
However, it looks like the upstream container could be trimmed down considerably:
- The run.sh script seems entirely superfluous. Look at the last line: all it does is pass its input parameters (given as CMD in the Dockerfile) to exec, replacing the shell script in memory. The setup steps it does above that shouldn't be necessary on RouterOS; the interfaces are already bound to the proper VLANs prior to starting the container, right?
- If you can get rid of this setup script, that removes the need for bash…
- …which was likely overkill anyway, since Alpine ships with a perfectly good shell interpreter already; if you really do need a run.sh, I don't see anything in that script that will require a major rewrite to make it run under the Almquist shell you get as /bin/sh in Alpine. It should port over easily enough.
- There's an apparent need for a shell in the chmod step in the second stage, but since Dockerfile version 1.3, you can say "COPY --chmod 700 …" instead.
- Since the CMD step uses the exec() form, you don't need a shell to run the command. That leaves only the "setcap" step as needing a shell and package manager, and if you can get rid of that, you should be able to pare this down to a single statically-linked binary. Reworking things so everything is hard-coded into the container rather than discovered on the fly is a worthwhile step here, because it'll save considerable space.
All this aside, it would be nice if you'd push those containers up to Docker Hub or similar.
I don't use mDNS across VLANs, so I can't help with practical testing. I'm replying out of academic interest in the topic.
Re: mDNS repeater feature
In addition, OT and just out of academic interest, a normal Alpine Linux starter instance is usually only around 8-10 meg and "mdns-repeater.c" should probably only add another few 100k.
Worth noting, besides being perfect for containers, Alpine Linux is a very lean and productive platform to use for mass production of Tailscale/Zerotier routers for OOB remote management using cheap low-end PIs. I just wish the ZT client was standard in all RoS platforms.
Worth noting, besides being perfect for containers, Alpine Linux is a very lean and productive platform to use for mass production of Tailscale/Zerotier routers for OOB remote management using cheap low-end PIs. I just wish the ZT client was standard in all RoS platforms.
Last edited by Larsa on Tue Mar 28, 2023 3:58 pm, edited 1 time in total.
Re: mDNS repeater feature
Alpine Linux is a very lean and productive platform
For the first (builder) stage, sure, but I think it's possible to get the second stage down to "FROM busybox" or, better, "FROM scratch", leaving only a single statically linked binary inside the container. Whether it's 100k as you estimate or 1MB (far limit of likelihood in my estimation) it's a lot better than the current 15MB.
If that means that the users of this method have to build their own containers from scratch to hard-code VLAN IDs in, I'm not seeing the problem. Docker Desktop is easy to install, and it's a few commands to build and push the container up to the router after that.
Last edited by tangent on Tue Mar 28, 2023 4:08 pm, edited 1 time in total.
Re: mDNS repeater feature
Perhaps I'm misunderstanding you but I don't see any contradictions here, but more of what fits best for the use case, i.e. each thing has its place, so to speak. If you want to run docker, there are several ready-made solutions to choose from that are not bloated with unnecessary stuff like https://www.docker.com/blog/how-to-use- ... ial-image/
Re: mDNS repeater feature
Perhaps I'm misunderstanding you
I'm saying use both: Alpine in the first stage to install the necessary build tools and run "gcc -static mdns_repeater.c -o mdns_repeater", then "FROM scratch" to copy that binary into the actual container, resulting in something more on the order of a meg, total.
I'm writing this as the current maintainer of the Fossil container which uses similar techniques to provide a distributed version control system, wiki-based web site, forum, chat system, bug tracker, etc. in about 4MB compressed, maybe 8MB on disk after instantiation. It uses a three-stage build system now so it can use BusyBox in the second stage, then get rid of it when it's done, another idea worth emulating in cases like this.
15MB is massively bloated for what this mDNS repeater does.
I'm half-tempted to dive in and rework the thing myself, only I'd then have to go and segment my LAN just to test it. My itch isn't that bad.
Re: mDNS repeater feature
MikroTik is working on mDNS repeater, but that will come together with a global DNS overhaul and it will be an improvement in all areas, not just this one. This is also why it takes some time to make.
Re: mDNS repeater feature
@normis
That is amazing to hear on both counts. Cannot wait for the new mDNS feature and more stable DNS function. The users whined and Mikrotik listened. Keep it up!
That is amazing to hear on both counts. Cannot wait for the new mDNS feature and more stable DNS function. The users whined and Mikrotik listened. Keep it up!
Re: mDNS repeater feature
Ok, I will reach out to Tik support and report back.Reach out to MikroTik support. Give them the supout export file. This needs to be solved by them, not me.
Re: mDNS repeater feature
I'm writing this as the current maintainer of the Fossil container which uses similar techniques to provide a distributed version control system...
Lean and mean, I like!
Re: mDNS repeater feature
Lean and mean, I like!
Yeah, especially since its closest competition is something like Gitlab CE, at 1.25 GB (gigabytes!) compressed, and something like 4 gigs when running. I get that it does more, but I dare say a whole lot of GitLab users could get by just fine with Fossil.
This thread inspired me to make another improvement to the container, which I just pushed. 3.28 MB on x86_64.
I realize I'm straying OT, but the point was, 15MB for an mDNS repeater is ludicrous.
Re: mDNS repeater feature
@Amm0
It worked sooooooo!!!!






@rextended, @DarkNate - your bickering may just cause Mikrotik to add this feature out of spite.
It worked sooooooo!!!!
MikroTik is working on mDNS repeater [...]
Re: mDNS repeater feature
This is actually great news:
Although the future stream of "is this done yet?" is going to be so much more boring than the "bickering".
Reading the tea leaves... that means discovery should work across BOTH WG/VPNs and VLANs, efficiently and without tricks. Looking forward to seeing how this comes out.[...] that will come together with a global DNS overhaul [...]
Although the future stream of "is this done yet?" is going to be so much more boring than the "bickering".
Re: mDNS repeater feature
I don't think that, if he announced it, we need to wait so long...
Re: mDNS repeater feature
I don't think that we need to wait so long...

Sorry ...
Re: mDNS repeater feature
With Mikrotik and CAPSMAN1 you can cordon off Wifi devices without using VLANs to their own bridge as long as you don't use local-forwarding for that SSID. This would be fine for many IOT cases which generally are low bandwidth. Multiple bridges combined with bridge firewall are really nice tools.Unless you are an advanced networking user or engineer, I agree. Using VLANs at home makes no sense for the added complexity and bullshit hacks required.
NORMIS ->>> It's a real shame CAPSMAN2 doesn't allow !local-forward. You've lost a powerful feature there.
<note> I didn't mean CAPSMAN2, I meant CAPSMAN in WifiWave2.
Last edited by UpRunTech on Wed Mar 29, 2023 7:46 am, edited 2 times in total.
Re: mDNS repeater feature
Ty. Keep it upIt worked sooooooo!!!!






Re: mDNS repeater feature
Capsman2 (the non wifiwave2) versions does allow known local forward. Under datapath. Capsman3 (wifi-wave2) is different.With Mikrotik and CAPSMAN1 you can cordon off Wifi devices without using VLANs to their own bridge as long as you don't use local-forwarding for that SSID. This would be fine for many IOT cases which generally are low bandwidth. Multiple bridges combined with bridge firewall are really nice tools.Unless you are an advanced networking user or engineer, I agree. Using VLANs at home makes no sense for the added complexity and bullshit hacks required.
NORMIS ->>> It's a real shame CAPSMAN2 doesn't allow !local-forward. You've lost a powerful feature there.
Re: mDNS repeater feature
Would be great if you fixed the IGMP Proxy problem with:MikroTik is working on mDNS repeater, but that will come together with a global DNS overhaul, and it will be an improvement in all areas, not just this one. This is also why it takes some time to make.
1. Documentation as users are not able to configure correctly due to poor documentation – Admittedly MikroTik in some or many cases have better docs than Juniper.
2. Lack of support for IPv6
mDNS repeater will not solve BUM traffic that's not related to mDNS. Home user devices makes use of other BUM for things that's not always mDNS. Meaning without IGMP Proxy properly supported at the least, BUM packets/frames will just flood the network.
Re: mDNS repeater feature
@colinardo
God/Buddha/Allah/ bless you,
finally I've manage to make that retard iPhone [wireless vlan300] to see my network printer [vlan 100]
God/Buddha/Allah/ bless you,
finally I've manage to make that retard iPhone [wireless vlan300] to see my network printer [vlan 100]
Re: mDNS repeater feature
Today, I've been able to get IGMP Proxy working with Chromecast cross vlans.
I'll get my documentation together and post a new thread so its easily findable.
Thank you to Nate for provided the basis of this solution. I don't understand quite how it works as the IGMP Proxy doesn't show much under the MFC, but it works.
I'll get my documentation together and post a new thread so its easily findable.
Thank you to Nate for provided the basis of this solution. I don't understand quite how it works as the IGMP Proxy doesn't show much under the MFC, but it works.
Re: mDNS repeater feature
looking forward to see
I'll get my documentation together and post a new thread so its easily findable.
Re: mDNS repeater feature
I'm surprised it didn't work and then started working. What changes in the config was made before/after?Today, I've been able to get IGMP Proxy working with Chromecast cross vlans.
I'll get my documentation together and post a new thread so its easily findable.
Thank you to Nate for provided the basis of this solution. I don't understand quite how it works as the IGMP Proxy doesn't show much under the MFC, but it works.
And nothing shows in packet counters/MFC because MikroTik didn't fix that bug yet.
And I told you from day 1, you don't need mDNS repeater bullshit. Was I ever wrong? Clearly not.
Re: mDNS repeater feature
me toolooking forward to see
I'll get my documentation together and post a new thread so its easily findable.
Re: mDNS repeater feature
@DarkNate: Thank you for sharing your IGMP Proxy expertise.
It works well in my setup for all IoT devices, making them visible in all “allowed” VLANs.
Also, thank you for hinting that the counters are broken.
And just like you mentioned, using Torch proved that it was working.
“Tip of the hat!”
It works well in my setup for all IoT devices, making them visible in all “allowed” VLANs.
Also, thank you for hinting that the counters are broken.
And just like you mentioned, using Torch proved that it was working.
“Tip of the hat!”
Re: mDNS repeater feature
please do shareToday, I've been able to get IGMP Proxy working with Chromecast cross vlans.
I'll get my documentation together and post a new thread so its easily findable.
Thank you to Nate for provided the basis of this solution. I don't understand quite how it works as the IGMP Proxy doesn't show much under the MFC, but it works.
Re: mDNS repeater feature
Anav, rextended and all the other experts in this thread have quietly disappeared after people started mentioning my IGMP Proxy approach works perfectly fine.@DarkNate: Thank you for sharing your IGMP Proxy expertise.
It works well in my setup for all IoT devices, making them visible in all “allowed” VLANs.
Also, thank you for hinting that the counters are broken.
And just like you mentioned, using Torch proved that it was working.
“Tip of the hat!”
This is why you should never trust people who lack computer science fundamentals education for best practices type approach in networking or tech in general.
Re: mDNS repeater feature
It seems to me that someone else has disappeared....Anav, rextended and all the other experts in this thread have quietly disappeared after people started mentioning my IGMP Proxy approach works perfectly fine.
This is why you should never trust people who lack computer science fundamentals education for best practices type approach in networking or tech in general.
It's not that I live here on the forum, I have a private life, you know?
And after MikroTik's announcement that it's implementing it, who cares about continuing to CORRECT YOU the things you forget?
Good evening everybody...
P.S.: I reply to you just because you write about me, else nothing:
viewtopic.php?p=993861#p992665
Re: mDNS repeater feature
I dont profess to be an expert, my purpose in posting is try and figure out what works most easily for the homeowner.
So when I dabble in other than home owner setups its because I want ascertain any thing that could possibly translate over.
I am not going away and luckily and am healthy as an elephant, so expect more of the same.
I have no idea what IGMP proxy is or does, I have spent the last little while trying to setup dns, and layer2 over wirguard, connecting separate networks
with same or different lan subnets across them for the purpose of discovery or unifi controller to ap etc....
However I am all llama ears if you think IGMP proxy is something that can translate well to the homeowner.
You seems prolific at proxy, so I have to wonder if its spills over to proxy gfs too.
On a serious note, I will endeavour to learn a bit about them before asking my usual 20 questions that will drive you bonkers.......
So when I dabble in other than home owner setups its because I want ascertain any thing that could possibly translate over.
I am not going away and luckily and am healthy as an elephant, so expect more of the same.
I have no idea what IGMP proxy is or does, I have spent the last little while trying to setup dns, and layer2 over wirguard, connecting separate networks
with same or different lan subnets across them for the purpose of discovery or unifi controller to ap etc....
However I am all llama ears if you think IGMP proxy is something that can translate well to the homeowner.
You seems prolific at proxy, so I have to wonder if its spills over to proxy gfs too.
On a serious note, I will endeavour to learn a bit about them before asking my usual 20 questions that will drive you bonkers.......
Re: mDNS repeater feature
Eh don't lower yourself by pandering to anyone's badgering. Given the total lack of documentation we don't know why IGMP proxy is working for some or what it's doing - no-one here wrote the code. It says *IGMP* proxy - why the hell would anyone assume it's going to relay mDNS or any other multicast frame without any context?On a serious note, I will endeavour to learn a bit about them before asking my usual 20 questions that will drive you bonkers.......
Re: mDNS repeater feature
most of the time IGMP traffic is multicast - so there comes the connection i guess ... still, as you wrote, the documentation is poor indeedEh don't lower yourself by pandering to anyone's badgering. Given the total lack of documentation we don't know why IGMP proxy is working for some or what it's doing - no-one here wrote the code. It says *IGMP* proxy - why the hell would anyone assume it's going to relay mDNS or any other multicast frame without any context?On a serious note, I will endeavour to learn a bit about them before asking my usual 20 questions that will drive you bonkers.......
Who is online
Users browsing this forum: No registered users and 3 guests



