UPDATE: Majority of my devices working well with hAP ax². However, MBP keeps running on about a half of possible speed.
Couple of month ago I become a happy owner of hAP ax²
This is my first Mikrotik device.
After few weeks of juggling with it and digging through an enormous amount of various settings nothing helps.
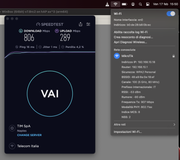
Here is my ISP speed (patch cord plugged into hAP ->> MacBook M1 PRO)

All I can get over WiFi a 1 meter away from the router is


I’ve been playing with, different versions of packages, WiFi channels, other things found on this forum, however nothing helps. The maximum I can get is 400Mb/s download speed out of 800Mb/s.
Dear Guru, I will infinitely appreciate it if you’ll point me to what is wrong with my settings
[admin@MikroTik] > export hide-sensitive
# feb/13/2023 22:32:50 by RouterOS 7.7
# software id = AHJZ-PQ1I
#
# model = C52iG-5HaxD2HaxD
# serial number = HERE_IS_MY_SERIAL
/interface bridge
add admin-mac=18:FD:74:BB:CB:C9 auto-mac=no comment=defconf name=bridge
/interface wifiwave2
set [ find default-name=wifi2 ] channel.band=2ghz-ax .frequency=2412 .skip-dfs-channels=10min-cac .width=20/40mhz \
configuration.country=Ukraine .mode=ap .ssid="AirPort Extreme Slow" disabled=no name=Private2GHz \
security.authentication-types=wpa2-psk,wpa3-psk .wps=push-button
set [ find default-name=wifi1 ] channel.band=5ghz-ax .frequency=5745-5805 .skip-dfs-channels=all .width=20/40/80mhz \
configuration.country=Ukraine .mode=ap .ssid="AirPort Extreme" disabled=no name=Private5GHz \
security.authentication-types=wpa2-psk,wpa3-psk
add configuration.chains="" .country=Ukraine .mode=ap .ssid="Glory to Ukraine app.191" disabled=no mac-address=\
1A:FD:74:BB:CB:CE master-interface=Private2GHz name=Guest2GHz security.authentication-types="" .ft=yes
add configuration.country=Ukraine .mode=ap .ssid="Glory to Ukraine app.191" disabled=no mac-address=1A:FD:74:BB:CB:CD \
master-interface=Private5GHz name=Guest5GHz security.ft=yes
/interface list
add comment=defconf name=WAN
add comment=defconf name=LAN
/ip pool
add name=dhcp ranges=192.168.88.10-192.168.88.254
/ip dhcp-server
add address-pool=dhcp interface=bridge lease-time=1w name=defconf
/port
set 0 name=serial0
/interface bridge filter
add action=drop chain=forward in-interface=Guest5GHz
add action=drop chain=forward out-interface=Guest5GHz
add action=drop chain=forward in-interface=Guest2GHz
add action=drop chain=forward out-interface=Guest2GHz
/interface bridge port
add bridge=bridge comment=defconf interface=ether2
add bridge=bridge comment=defconf interface=ether3
add bridge=bridge comment=defconf interface=ether4
add bridge=bridge comment=defconf interface=ether5
add bridge=bridge comment=defconf interface=Private5GHz
add bridge=bridge comment=defconf interface=Private2GHz
add bridge=bridge interface=Guest5GHz
add bridge=bridge interface=Guest2GHz
/ip neighbor discovery-settings
set discover-interface-list=LAN
/interface detect-internet
set detect-interface-list=all internet-interface-list=all lan-interface-list=all wan-interface-list=all
/interface list member
add comment=defconf interface=bridge list=LAN
add comment=defconf interface=ether1 list=WAN
/ip address
add address=192.168.88.1/24 comment=defconf interface=bridge network=192.168.88.0
/ip dhcp-client
add comment=defconf interface=ether1
/ip dhcp-server network
add address=192.168.88.0/24 comment=defconf dns-server=8.8.8.8,8.8.4.4,9.9.9.9 gateway=192.168.88.1
/ip dns
set allow-remote-requests=yes servers=8.8.8.8,8.8.8.4,9.9.9.9
/ip dns static
add address=192.168.88.1 comment=defconf name=router.lan
/ip firewall filter
add action=accept chain=input comment="defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=invalid
add action=accept chain=input comment="defconf: accept ICMP" protocol=icmp
add action=accept chain=input comment="defconf: accept to local loopback (for CAPsMAN)" dst-address=127.0.0.1
add action=drop chain=input comment="defconf: drop all not coming from LAN" in-interface-list=!LAN
add action=accept chain=forward comment="defconf: accept in ipsec policy" ipsec-policy=in,ipsec
add action=accept chain=forward comment="defconf: accept out ipsec policy" ipsec-policy=out,ipsec
add action=fasttrack-connection chain=forward comment="defconf: fasttrack" connection-state=established,related \
hw-offload=yes
add action=accept chain=forward comment="defconf: accept established,related, untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" connection-state=invalid
add action=drop chain=forward comment="defconf: drop all from WAN not DSTNATed" connection-nat-state=!dstnat \
connection-state=new in-interface-list=WAN
/ip firewall nat
add action=masquerade chain=srcnat comment="defconf: masquerade" ipsec-policy=out,none out-interface-list=WAN
/ip service
set www-ssl certificate=Webfig disabled=no
/ip upnp interfaces
add interface=bridge type=internal
add interface=ether1 type=external
/ipv6 firewall address-list
add address=::/128 comment="defconf: unspecified address" list=bad_ipv6
add address=::1/128 comment="defconf: lo" list=bad_ipv6
add address=fec0::/10 comment="defconf: site-local" list=bad_ipv6
add address=::ffff:0.0.0.0/96 comment="defconf: ipv4-mapped" list=bad_ipv6
add address=::/96 comment="defconf: ipv4 compat" list=bad_ipv6
add address=100::/64 comment="defconf: discard only " list=bad_ipv6
add address=2001:db8::/32 comment="defconf: documentation" list=bad_ipv6
add address=2001:10::/28 comment="defconf: ORCHID" list=bad_ipv6
add address=3ffe::/16 comment="defconf: 6bone" list=bad_ipv6
/ipv6 firewall filter
add action=accept chain=input comment="defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=input comment="defconf: drop invalid" connection-state=invalid
add action=accept chain=input comment="defconf: accept ICMPv6" protocol=icmpv6
add action=accept chain=input comment="defconf: accept UDP traceroute" port=33434-33534 protocol=udp
add action=accept chain=input comment="defconf: accept DHCPv6-Client prefix delegation." dst-port=546 protocol=udp \
src-address=fe80::/10
add action=accept chain=input comment="defconf: accept IKE" dst-port=500,4500 protocol=udp
add action=accept chain=input comment="defconf: accept ipsec AH" protocol=ipsec-ah
add action=accept chain=input comment="defconf: accept ipsec ESP" protocol=ipsec-esp
add action=accept chain=input comment="defconf: accept all that matches ipsec policy" ipsec-policy=in,ipsec
add action=drop chain=input comment="defconf: drop everything else not coming from LAN" in-interface-list=!LAN
add action=accept chain=forward comment="defconf: accept established,related,untracked" connection-state=\
established,related,untracked
add action=drop chain=forward comment="defconf: drop invalid" connection-state=invalid
add action=drop chain=forward comment="defconf: drop packets with bad src ipv6" src-address-list=bad_ipv6
add action=drop chain=forward comment="defconf: drop packets with bad dst ipv6" dst-address-list=bad_ipv6
add action=drop chain=forward comment="defconf: rfc4890 drop hop-limit=1" hop-limit=equal:1 protocol=icmpv6
add action=accept chain=forward comment="defconf: accept ICMPv6" protocol=icmpv6
add action=accept chain=forward comment="defconf: accept HIP" protocol=139
add action=accept chain=forward comment="defconf: accept IKE" dst-port=500,4500 protocol=udp
add action=accept chain=forward comment="defconf: accept ipsec AH" protocol=ipsec-ah
add action=accept chain=forward comment="defconf: accept ipsec ESP" protocol=ipsec-esp
add action=accept chain=forward comment="defconf: accept all that matches ipsec policy" ipsec-policy=in,ipsec
add action=drop chain=forward comment="defconf: drop everything else not coming from LAN" in-interface-list=!LAN
/system clock
set time-zone-name=Europe/Kiev
/system logging
add action=disk topics=critical
add action=disk topics=error
add action=disk topics=warning
/system watchdog
set automatic-supout=no watchdog-timer=no
/tool graphing interface
add
/tool graphing queue
add
/tool graphing resource
add
/tool mac-server
set allowed-interface-list=LAN
/tool mac-server mac-winbox
set allowed-interface-list=LAN